nShield Security World v13.3 Security Manual
Introduction
Good security practice requires procedural as well as technical measures to provide a comprehensive security environment for the protection of your cryptographic keys and data.
This guide provides advice to you on the secure operation of the product. It identifies procedural measures that should be deployed to support the secure operation of the nShield. The guidance should be used in the development of your Security Operating Procedures for your systems incorporating the nShield.
Who should read this document?
The guide should be used by the following people:
-
Those responsible for the security policy and procedures for your systems incorporating the nShield
-
Those responsible for commissioning the nShield
-
Those responsible for administering the nShield
-
Those responsible for auditing the nShield.
Products covered by this manual
The guide covers the following product variants:
-
nShield Edge
-
nShield Solo+
-
nShield Solo XC
-
nShield 5s
-
nShield Connect+
-
nShield Connect XC
-
nShield 5c
| In this manual, guidance given for nShield Solo applies to the Solo+, Solo XC, and nShield 5s product variants. Similarly, guidance given for nShield Connect applies to the Connect+, Connect XC, and nShield 5c product variants. |
Product security objective
The nShield range of products provide protection against technical and physical attacks on keys used to protect your data in use, in motion and at rest. This provides confidentiality, integrity and availability* of user data up to FIPS 140 Level 3 and Common Criteria version 3.1 revision 5 EAL 4+ (platform and version dependent) when deployed in accordance with the technical and procedural controls identified in the User Guide and Security Manual.
*Some availability threats can be mitigated by hosting a Security World across multiple Hardware Security Modules (HSMs).
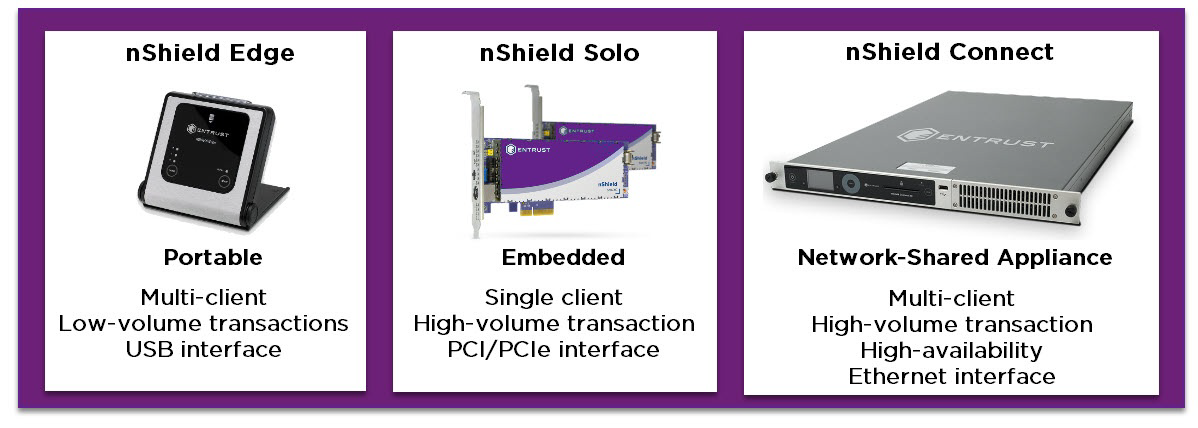
Product selection
As part of the security product selection process, you must determine that the functionality delivered by any candidate product meets your requirements.
| In this manual the terms module and HSM are both used to generically describe the nShield range of products. |
Security manual authority and scope
The guide is advisory and its scope is limited to identifying good procedural practices for the secure operation of the product within your environment.
If there is any contradiction between the guidance that occurs in this manual and that found in either the Installation guides or User Guides then the guidance found here takes precedence.
The scope of this manual is limited to security procedural guidance. The Installation guides and User Guides documents provide guidance on how to implement the controls discussed in this Manual.
Related documents
-
nShield Solo, nShield Solo XC and nShield Edge User Guide (specific to the operating environment: Linux and Windows)
-
nShield 5s User Guide (specific to the operating environment: Linux and Windows)
-
nShield Connect User Guide (specific to the operating environment: Linux and Windows)
-
nShield 5c User Guide (specific to the operating environment: Linux and Windows)
-
CodeSafe Developer Guide
-
nShield Connect Physical Security Checklist
-
nShield nToken Installation Guide
-
nShield Edge Installation Guide
-
nShield Solo and nShield Solo XC Installation Guide
-
nShield 5s Installation Guide
-
nShield Connect Installation Guide
-
nShield 5c Installation Guide