Available Functions
Available functions
The module firmware automatically detects which algorithms it can support. These algorithms are advertised when the provider first starts up. The provider conservatively advertises only those mechanisms that are supported by all installed modules in the system.
| Certain algorithms are not supported by older versions of firmware. We recommend that you ensure that your module is upgraded to the most recent version of firmware appropriate for your environment. |
The following table indicates the cipher modes available for each cipher.
| Cipher | CBC | CFB | CTR | ECB | OFB | GCM |
|---|---|---|---|---|---|---|
AESWrap |
X |
|||||
ArcFour |
||||||
CAST256 |
X |
X |
X |
X |
X |
|
DES2 |
X |
X |
X |
X |
X |
|
DES |
X |
X |
X |
X |
X |
|
DESede |
X |
X |
X |
X |
X |
|
DESedeWrap |
X |
|||||
ECIES1 |
||||||
Rijndael |
X |
X |
X |
X |
X |
X |
RSA |
X |
In the table above, annotations with the following numbers indicate:
1 These ciphers support key wrap and unwrap only.
The following table indicates the padding types available for each cipher.
| Cipher | ANSI X9.23 | ISO 10126 | ISO 7816 | None | OAEP | PKCS #1 | PKCS #5 | Zero byte |
|---|---|---|---|---|---|---|---|---|
AESWrap |
X |
|||||||
ArcFour |
||||||||
CAST256 |
X |
X |
X |
X |
X |
X |
||
DES2 |
X |
X |
X |
X |
X |
X |
||
DES |
X |
X |
X |
X |
X |
X |
||
DESede |
X |
X |
X |
X |
X |
X |
||
DESedeWrap |
X |
|||||||
ECIES1 |
||||||||
Rijndael |
X |
X |
X |
X |
X |
X |
||
RSA |
X |
X |
In the table above, annotations with the following numbers indicate:
1 These ciphers support key wrap and unwrap only.
| Algorithm | Key length in bits for generation or signing |  |
 |
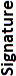 |
 |
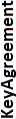 |
 |
 |
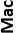 |
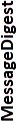 |
 |
|---|---|---|---|---|---|---|---|---|---|---|---|
AESWrap |
Y |
||||||||||
Arcfour |
8, 16 to 2048 |
Y1 |
Y1 |
||||||||
CAST256 |
128, 192, 256 |
Y1 |
Y1 |
||||||||
DES |
64 |
Y1 |
Y1 |
||||||||
DESede |
192 |
Y |
Y |
||||||||
DES2 |
128 |
Y |
Y |
||||||||
DESedeWrap |
Y |
||||||||||
DH |
Y |
Y |
Y |
||||||||
DSA |
1024 |
Y |
Y |
||||||||
ECDH |
Y |
Y |
Y |
||||||||
ECDHwithSHA1KDF |
Y |
||||||||||
ECDHwithSHA224KDF |
Y |
||||||||||
ECDHwithSHA256KDF |
Y |
||||||||||
ECDHwithSHA384KDF |
Y |
||||||||||
ECDHwithSHA512KDF |
Y |
||||||||||
ECDSA |
Y |
Y |
|||||||||
EdDSA |
256 |
Y1 |
Y1 |
||||||||
Ed25519 |
256 |
Y1 |
Y1 |
||||||||
Ed25519ph |
Y1 |
||||||||||
HmacMD5 |
Y1 |
Y1 |
|||||||||
HmacRIPEMD160 |
8, 16 to 2048 |
Y1 |
Y1 |
||||||||
HmacSHA1 |
8, 16 to 2048 |
Y |
Y |
||||||||
HmacSHA224 |
8, 16 to 2048 |
Y |
Y |
||||||||
HmacSHA256 |
8, 16 to 2048 |
Y |
Y |
||||||||
HmacSHA384 |
8, 16 to 2048 |
Y |
Y |
||||||||
HmacSHA512 |
8, 16 to 2048 |
Y |
Y |
||||||||
HmacTiger |
8, 16 to 2048 |
Y1 |
Y1 |
||||||||
MD5 |
Y1 |
||||||||||
MD5andSHA1withRSA |
Y |
||||||||||
MD5withRSA |
Y |
||||||||||
nCipher.sworld |
Y |
||||||||||
Rijndael |
Y |
Y |
|||||||||
RawRSA |
Y |
||||||||||
RIPEMD160 |
Y1 |
||||||||||
RIPEMD160withRSA |
Y1 |
||||||||||
RIPEMD160withRSAandMGF1 |
322+ |
Y1 |
|||||||||
RNG |
Y |
||||||||||
RSA |
512+ |
Y |
Y |
Y |
|||||||
SHA1 |
Y |
||||||||||
SHA1withDSA |
Y |
||||||||||
SHA1withECDSA |
Y |
||||||||||
SHA1withRSA |
Y |
||||||||||
SHA1withRSAandMGF1 |
322+ |
Y |
|||||||||
SHA224 |
Y |
||||||||||
SHA224withDSA |
Y |
||||||||||
SHA224withECDSA |
Y |
||||||||||
SHA224withRSA |
Y |
||||||||||
SHA224withRSAandMGF1 |
450+ |
Y |
|||||||||
SHA256 |
Y |
||||||||||
SHA256withDSA |
Y |
||||||||||
SHA256withECDSA |
Y |
||||||||||
SHA256withRSA |
Y |
||||||||||
SHA256withRSAandMGF1 |
514+ |
Y |
|||||||||
SHA384 |
Y |
||||||||||
SHA384withDSA |
Y |
||||||||||
SHA384withECDSA |
Y |
||||||||||
SHA384withRSA |
Y |
||||||||||
SHA384withRSAandMGF1 |
770+ |
Y |
|||||||||
SHA512 |
Y |
||||||||||
SHA512withDSA |
Y |
||||||||||
SHA512withECDSA |
Y |
||||||||||
SHA512withRSA |
Y |
||||||||||
SHA512withRSAand MGF1 |
1026+ |
Y |
|||||||||
Tiger |
8, 16 to 256 |
Y |
Y |
Y1 |
In the table above, annotations with the following numbers indicate:
1 These algorithms are not supported in FIPS 140 Level 3 Security Worlds.