Physical security of the nShield Connect
This chapter provides a brief overview of the physical security measures that have been implemented to protect your Connect. You are also shown how to:
-
Check the physical security of your Connect
-
Disable and re-enable tamper detection functionality on your Connect.
The tamper detection functionality on the Connect provides additional physical security, over and above that provided by the holographic security seal, and alerts you to tampering in an operational environment. There is a removable lid on top of the Connect, protected by the security seal and tamper switches. To prevent the insertion of objects into the Connect, baffles are placed behind vents.
To optimize their effectiveness, use the physical security measures implemented on the Connect in association with your security policies and procedures. For more information about creating and managing security policies, see the Security Policy Guide on the NIST CMVP website.
| Currently, the FIPS 140-2 Level 3 boundary is at the internal module. Future software releases may move the FIPS boundary so that it includes the entire Connect chassis. |
| For more information about FIPS 140-2, see http://csrc.nist.gov/publications/fips/fips140- 2/fips1402.pdf. |
Tamper event
The Connect offers several layers of tamper protection. The outer boundary of the box is tamper‑responsive. When tampered, the unit ceases to provide cryptographic functionality, alerts the operator of the event, and ultimately forces the operator to reset the unit to factory defaults. Movements/vibrations, or replacing the fan tray module or a PSU, does not activate the tamper detection functionality. Tamper‑responsiveness can be disabled, if desired. If a tamper event does occur, you can use the Security World data stored on the RFS and the Administrator Card Set to recover the keys and cryptographic data.
Connect lid is closed
If the Connect is powered, a tamper event has occurred, and the lid is closed, the following message is displayed onscreen:
** TAMPER DETECTED ** Consult User Guide. Check physical seals. Reset to factory state or disable tamper detection first? RESET DISABLE
When you see this message, examine your unit for physical signs of tampering (see Physical security checks).
If you discover signs of tampering do not attempt to put the unit back into operation. The date and time of the tamper event are recorded in the log (see Logging, debugging, and diagnostics).
| The tamper-responsiveness circuitry has a Real Time Clock that is synchronised to the system time of the Connect, however the times associated with events in the tamper log may still have slight offsets to times recorded in other log files. |
If there are signs of tampering, and the tamper event occurred:
-
During transit from Entrust, contact Support.
-
After installation, refer to your security policies and procedures. For more information about creating and managing security policies, see the Security Policy Guide.
If there are no signs of tampering, you can either:
-
Reset the Connect to a factory state
Or:
-
Disable the tamper detection functionality and then reset the Connect to a factory state.
Do not disable tamper detection unless asked to do so by Support
You require a quorum of the Administrator Card Set (ACS) to restore the key data and reconnect the Connect to the network. If you chose to disable the tamper protection circuitry when you reset the Connect to a factory state, a cautionary warning is displayed prior to the request for card authorization. For information about re-enabling disabled tamper detection functionality, see Disabling tamper detection functionality.
Connect lid is open
If the Connect is powered, a tamper event has occurred, and the lid is open, the following message is displayed onscreen:
** TAMPER DETECTED **
Unit lid is open
Replace lid or disable
tamper detection.
DISABLE
An open lid indicates that the physical security of the unit is compromised. You may want to examine your unit for other physical signs of tampering (see Physical security checks). Do not attempt to put the unit back into operation.
The date and time of the tamper event are recorded in the log files (see Logging, debugging, and diagnostics). If the tamper event occurred:
-
During transit from Entrust, contact Support.
-
After installation, refer to your security policies and procedures. For more information about creating and managing security policies, see the Security Policy Guide on the NIST CMVP website.
If you choose to replace the lid of the Connect, the onscreen message changes to the tamper alert message that is given when the lid is closed. Closing the lid provides you with the option to reset the unit to a factory state without disabling tamper detection functionality. If the lid remains open, all button presses other than those made using the right-hand navigation button are ignored. Pressing the right-hand navigation button disables tamper responsiveness and resets the Connect to a factory state.
Physical security checks
Check the physical security of your Connect before installation and at regular intervals afterwards. For an alternative presentation of the physical security checks described here, see the Physical Security Checklist. For more information about tamper events, and what actions to take if you discover signs of tampering, see Tamper event.
To determine if the security of the Connect is compromised:
-
Check that the physical security seal is authentic and intact. Look for the holographic foil bearing the nCipher logo. Look for cuts, tears and voiding of the seal. The seal is located on the top of the Connect chassis.
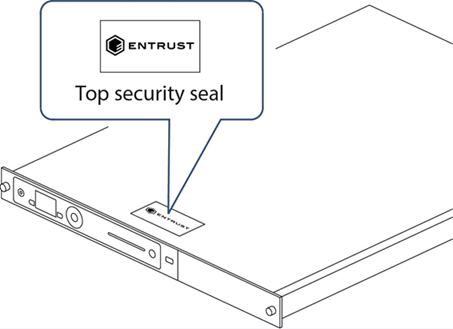
For information about the appearance of intact and damaged security seals, see the Physical Security Checklist.
-
Check that the metal lid remains flush with the Connect chassis.


-
Check all surfaces — the top, bottom and sides of the Connect — for signs of physical damage.
-
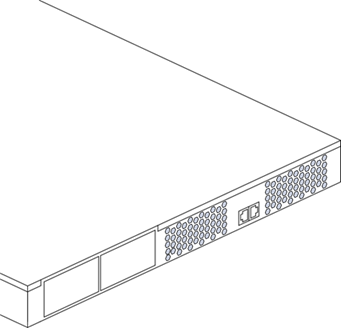
Check that there are no signs of physical damage to the vents, including attempts to insert objects into the vents.

Replacing the fan tray module and PSU
You can replace the fan tray module or a power supply unit (PSU) without activating a tamper event as both are outside the security boundary. You can access:
-
The PSU(s) from the rear of the Connect.
-
The fan tray module through the removable front vent.
Should a problem occur with the fan tray module or a PSU, contact Support before taking further action. For more information about replacing the fan tray module or a PSU, see the Fan Tray Module Installation Sheet or the Power Supply Unit Installation Sheet.
| The fan tray module contains back‑up batteries providing reserve capacity (a guaranteed minimum of 3 years) for tamper detection functionality even when the Connect is in an unpowered state. |
The tamper protection circuitry remains fully operational if the Connect is placed on standby while a replacement operation is performed (whether you are replacing the fan tray module or one of the two PSUs, in the case of dual PSU units).
| Provided that the Connect is connected to the mains power supply, the Connect displays an onscreen error message when back‑up battery power is low. The Status LED also displays a low power warning. For more information, see the Installation Guide. |
Replacing the fan tray module
It is not necessary to remove mains power to replace a fan tray module (we recommend that you power down the unit into standby state using the front panel power button). However, if mains power is removed then a replacement fan tray module must be installed within an hour to ensure that a tamper event is not activated. If put in standby state the time required to change fan tray module is unlimited. For more information about replacing the fan tray module, see the Fan Tray Module Installation Sheet.
Fan tray module error messages
If you receive any of the following error messages on the Connect display, accompanied by the orange warning LED, follow the related action in the table below:
| Error message | Action |
|---|---|
Single fan fail |
Contact Support |
Many fans fail |
Replace fan tray |
Battery power low |
Consider replacing fan tray during the next scheduled service/maintenance period. |
System Shutdown Both fans in a pair had failed |
Replace fan tray |
If the error message is Single fan fail, the Connect can continue operating under the specified operating environment. Although you are advised to contact Support, the limited nature of such a failure means you can replace the fan tray module at your convenience.
If the error message is Many fans fail, you must replace the fan tray module immediately.
If the error message is Battery Power low, this indicates that one or both of the backup batteries located on the fan tray module (required only when the Connect is removed from mains power) is running low.
The Battery Power low indication has no detrimental affect on the Connect performance whilst the unit remains powered. Entrust recommend customers should consider replacing the fan tray module during the next service/maintenance.
If two fans fail from a redundant pair, the Connect will display the error message Many fans have failed for a few seconds and it will then shutdown. On reboot, the Connect will then display the error messages System Shutdown and Both fans in a pair had failed. In this situation the fan tray module must be replaced immediately.
Replacing the PSU
If you have a dual PSU Connect, you do not have to remove power to the functioning PSU while replacing a faulty PSU. Tamper detection functionality will operate normally throughout the PSU replacement process. If you decide to remove power from both PSUs, tamper detection functionality will continue to operate normally for at least 3 years, as the fan tray module provides back‑up capacity for this circuitry. For more information about replacing the PSU, see the Power Supply Unit Installation Sheet.
PSU error messages
If a PSU fails, an orange warning LED comes on and an error message is displayed on the Connect display. Although you are advised to contact Support, the unit can continue to operate normally and you can replace the failed PSU at your convenience. There is no need to power down the unit when you replace the failed PSU.
In addition to the orange warning LED, an audible warning is given when a PSU fails on an Connect. The audible warning is turned off when you navigate to the Critical errors screen.
Battery life when storing the Connect
If a Connect has been in storage for an extended period of time the fan tray module may need replacement.
Entrust guarantees a minimum battery life of three years, even if the Connect remains in storage and is not connected to the mains power supply during this time.
Disabling tamper detection functionality
We do not recommend disabling tamper detection functionality. However, there may be circumstances in which disabling this functionality is required. For example, you may want to:
-
Bring the management of the Connect into line with your existing operational procedures
-
Standardize the management task, if you are managing a mixture of older and newer units.
To disable tamper responsiveness on your Connect:
-
From the main menu select System > System configuration > Tamper config.
You are shown the following dialog:
Tamper responsiveness is currently enabled. This matches nCipher's recommendation. Do you want to disable tamper responsiveness? -
Press the right-hand navigation button to disable tamper responsiveness.
-
You are asked to confirm the change. Press the right-hand navigation button again.
Tamper responsiveness is disabled and the unit is reset to a factory state. To restore the key data and reconnect the Connect to the network you must present a quorum of the ACS.
Reactivating disabled tamper functionality
If your circumstances change, for example, your operational procedures are updated, you may want to re-enable tamper responsiveness.
To re-enable tamper responsiveness on your Connect:
-
From the main menu select System > System configuration > Tamper config.
-
You are shown the following dialog:
Tamper responsiveness is currently DISABLED. nCipher recommends that tamper should be enabled. Re-anble tamper responsiveness? -
Press the right-hand navigation button to enable tamper responsiveness.
-
You are asked to confirm the change. Press the right-hand navigation button again.
Tamper responsiveness is enabled and the unit is reset to a factory state. To restore the key data and reconnect the Connect to the network you must present a quorum of the ACS. Tamper events are logged and never erased.