nShield architecture
This chapter provides a brief overview of the Security World Software architecture. The following diagram provides a visual representation of nShield architecture and the documentation that relates to it.
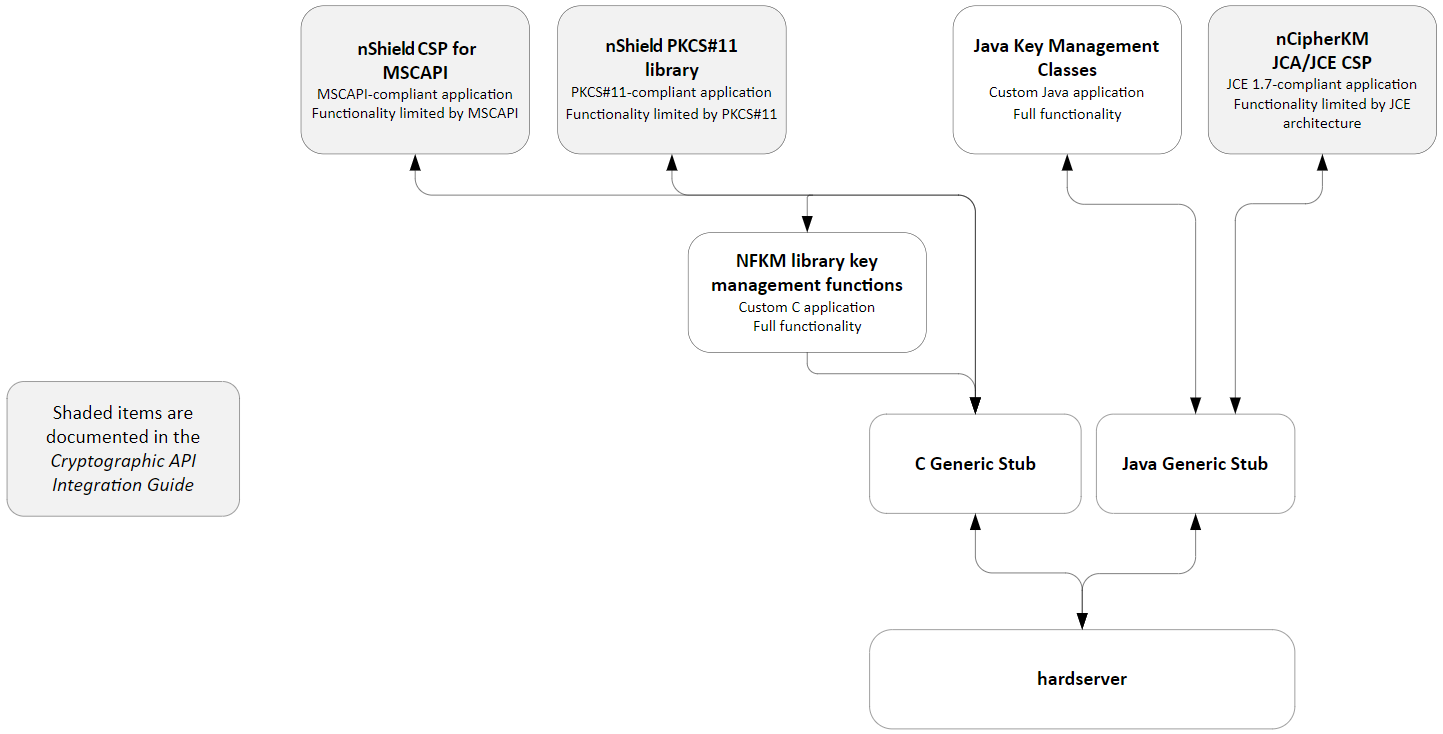
Security World Software modules
nShield modules provide a secure environment to perform cryptographic functions. Key-management modules are fitted with a smart card interface that enables keys to be stored on removable tokens for extra security. nShield modules are available for PCI buses and also as network attached Ethernet modules (nShield Connect).
Security World Software server
The Security World Software server, often referred to as the hardserver, accepts requests by means of an interprocess communication facility (for example, a domain socket on Linux or named pipes or TCP/IP sockets on Windows).
The Security World Software server receives requests from applications and passes these to the nShield module(s). The module handles these requests and returns them to the server. The server ensures that the results are returned to the correct calling program.
You only need a single Security World Software server running on your host computer. This server can communicate with multiple applications and multiple nShield modules.
Stubs and interface libraries
An application can either handle its own cryptographic functions or it can use a cryptographic library:
-
If the application uses a cryptographic library that is already able to communicate with the Security World Software server, then no further modification is necessary. The application can automatically make use of the nShield module.
-
If the application uses a cryptographic library that has not been modified to be able to communicate with the Security World Software server, then either Entrust or the cryptographic library supplier need to create adaption function(s) and compile them into the cryptographic library. The application users then must relink their applications using the updated cryptographic library.
If the application performs its own cryptographic functions, you must create adaption function(s) that pass the cryptographic functions to the Security World Software server. You must identify each cryptographic function within the application and change it to call the nShield adaption function, which in turn calls the generic stub. If the cryptographic functions are provided by means of a DLL or shared library, the library file can be changed. Otherwise, the application itself must be recompiled.
Using an interface library
Entrust supplies the following interface libraries:
-
Microsoft CryptoAPI
-
PKCS #11
-
nCipherKM JCA/JCE CSP
Third-party vendors may supply nShield-aware versions of their cryptographic libraries.
The functionality provided by these libraries is the intersection of the functionality provided by the nCore API and the functionality provided by the standard for that library.
Most standard libraries offer fewer key-management options than are available in the nCore API. However, the nShield libraries do not include any extensions to their standards. If you want to make use of features of the nCore API that are not offered in the standard, you should convert your application to work directly with the generic stub.
On the other hand, many standard libraries include functions that are not supported on the nShield module, such as support for IDEA or Skipjack. If you require a feature that is not supported on the nShield module, contact Support because it may be possible to add the feature in a future release. However, in many cases, features are not present on the module for licensing reasons, as opposed to technical reasons, and Entrust cannot offer them in the interface library.
Writing a custom application
If you choose not to use one of the interface libraries, you must write a custom application. This gives you access to all the features of the nCore API. For this purpose, Entrust provides generic stub libraries for C and Java. If you want to use a language other than C orJava, you must write your own wrapper functions in your chosen programming language that call the C generic stub functions.
Entrust supplies several utility functions to help you write your application.
Acceleration-only or key management
You must also decide whether you want to use key management or whether you are writing an acceleration-only application.
Acceleration-only applications are much simpler to write but do not offer any security benefits.
The Microsoft CryptoAPI, Java JCE, PKCS #11, as well as the application plug-ins, use the Security World paradigm for key storage.
If you are writing a custom application, you have the option of using the Security World mechanisms, in which case your users can use either KeySafe or the command-line utilities supplied with the module for many key-management operations. This means you do not have to write these functions yourself.
The NFKM library gives you access to all the Security World functionality.