nCore architecture
This section describes the interaction between your application and an nShield module that occurs when performing the following cryptographic tasks:
-
generating a key
-
loading a key
-
transacting a command on a module
Programming environment architecture
The following diagram illustrates typical architecture in which one would use the nCore API:
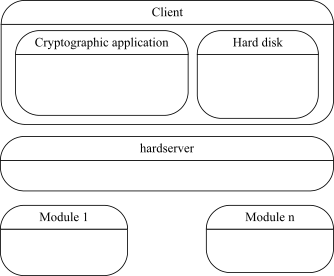
In the typical programming environment architecture diagram:
-
Client: The computer on which your cryptographic application runs.
-
hardserver: An intermediary between applications and module. The hardserver is responsible for routing commands to modules, and returning the reply from the module to the calling application.
-
Module: The hardware that performs cryptographic tasks.
Generating a key
Keys generated using the nCore API are generally stored in encrypted form on the hard disk of the computer running the cryptographic application. The key blob that contains the encrypted key information is generated by a module when an application uses the module to generate a key.
The following diagram illustrates the interaction between your cryptographic application and the Security World that occurs during the key-generation process:
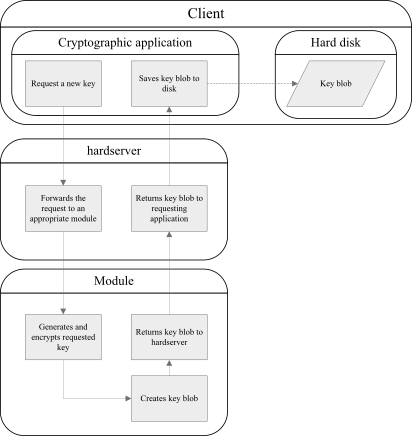
A key blob can only be decrypted by a module that has a record of the key that was used to encrypt the information in the key blob. A key blob contains key information and an Access Control List (ACL) which defines who can use the key and what operations the key can be used for.
Loading a key
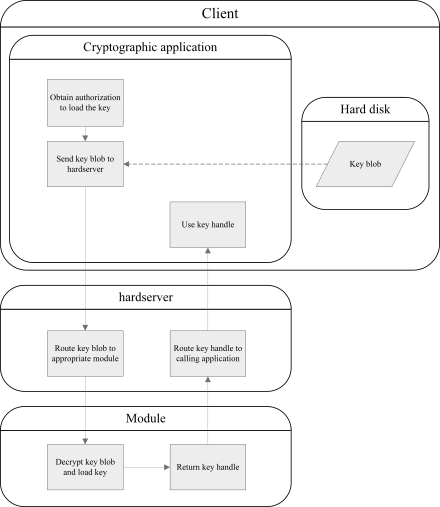
Because key information is encrypted in a key blob, the key itself cannot be used to perform a cryptographic operation until it is decrypted. To use a key, you first need to load the encrypted key blob into a module. The key blob is decrypted using a key stored on the module, and a handle or object reference to the key is returned to your application.
In most cases it is necessary to provide authentication in the form of a smart card and/or a pass phrase before using a key. The user interaction that prompts for authentication to be provided is handled by the nCore API.
The following diagram illustrates the key loading process:
Transacting a command
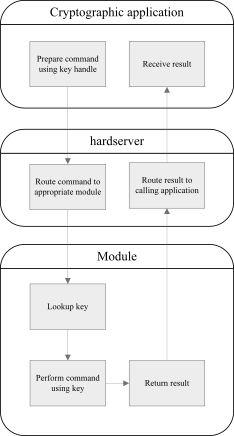
After an application has loaded a key, it can instruct a module to use the key to perform cryptographic operations such as encryption, decryption, signing and verification. The following diagram illustrates the process of transacting a command.
C tutorial explains how to write a C application that:
-
creates a connection to the hardserver
-
generates a key
-
loads a key onto a module
-
transacts a command with the module to use the key to encrypt a file.
Java tutorial explains how to write a similar Java application which signs a file.