Deploy Entrust KeyControl
In order to provide uninterrupted access to the keys, in production deploy a cluster of at least 2 KeyControl Vault instances behind a load balancer. Use the load balancer FQDN when specifying the URL of the DKE key in the compliance label, and when registering the Azure application that provides authentication for the service.
If you use a single KeyControl instance you can access it directly, and use its FQDN directly. We will use the term ‘Service FQDN’ for the address used to access the service whether it is a load balancer or KeyControl instance.
You will need to include the Service FQDN in the SSL certificate on the cluster. In order to register the Azure App, the Service FQDN needs to be in a domain verified with the Azure account, see Add your custom domain name to your tenant.
The following steps summarize the deployment of the Entrust KeyControl.
Deploy an Entrust KeyControl cluster
For the purpose of this integration, a single-node Entrust KeyControl cluster was deployed in Azure. This cluster can be reached at the load balancer hostname.
-
Deploy the Entrust KeyControl node per Deploying a KeyControl Vault Node in Azure.
-
Bookmark the public IP.
-
Configure the node per Configuring the First KeyControl Vault Node.
-
If deploying two-nodes, configure the second node per Configuring Additional KeyControl Vault Nodes.
Following is an example of the WEB GUI of a two-node Entrust KeyControl cluster deployed on-premises.
Install certificate authority (CA) certificate
The Entrust KeyControl cluster needs a certificate from your private root CA, or a trusted public CA, per your organization policies.
-
Create a certificate signing request (CSR) per Creating a Certificate Signing Request.
-
Have your private root CA, or a trusted public CA, sign the CSR.
-
Install the signed certificate per Installing External Certificates for Internal and External Webservers.
Create a Cloud Key Management Vault in Entrust KeyControl
The Entrust KeyControl Vault appliance supports different type of vaults that can be used by all type of applications. This section describes how to create a Cloud Key Management vault in the Entrust KeyControl vault server.
-
Create a vault per Creating a Vault. The vault Type is Cloud Key Management.
Once the vault is created successfully, the new vault’s URL and sign-in credentials will be emailed to the administrator’s email address entered above. In closed gap environments where email is not available, the URL and sign-in credentials are displayed at this time. -
Bookmark the Vault URL. Copy the User Name and Temporary Password.
-
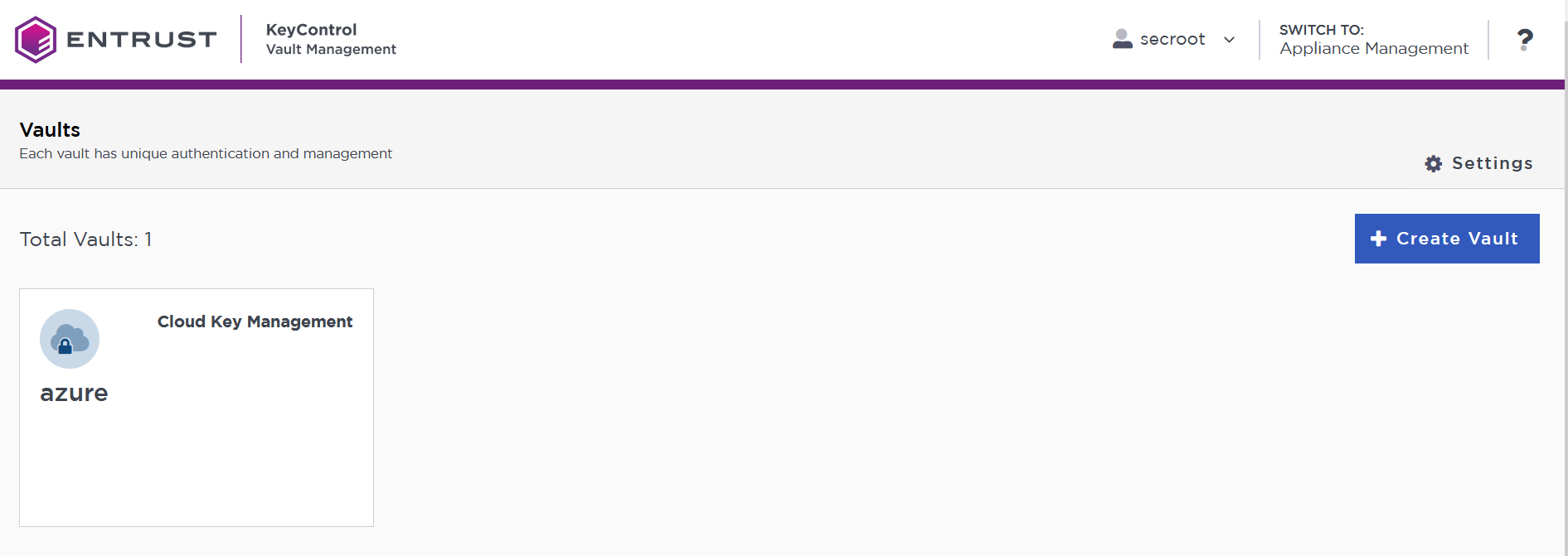
The newly created Vault is added to the Vault Management dashboard.
For example:
-
Sign in to the URL provided above with the temporary password. Change the initial password when prompted. Sign in again to verify.
-
Notice the new vault.
For example: