Introduction
This guide explains how to configure a Red Hat Certificate System (RHCS) installation with an Entrust nShield Hardware Security Module (HSM). The integration between the HSM and Red Hat Certificate System uses the PKCS #11 cryptographic API.
The basic architecture of an RHCS deployment is shown in the diagram below:
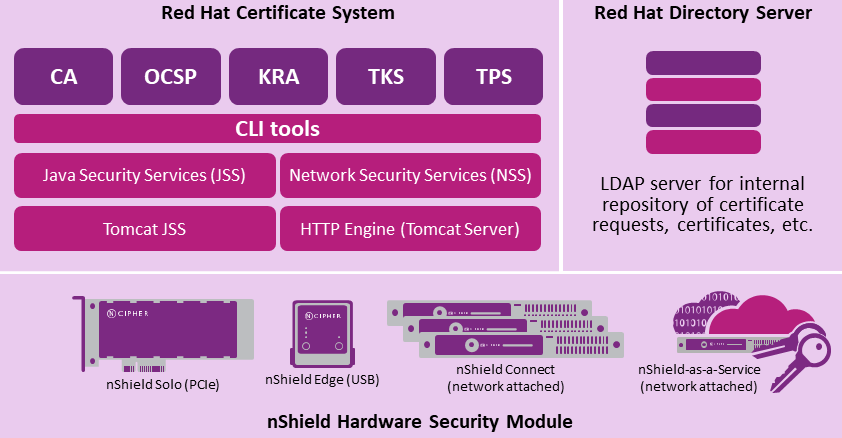
| This guide does not cover every step in the process of setting up all software. Some packages require that other packages are already configured, initialized, and running before they can be installed successfully. |
Requirements
For an RHCS installation, you need to set up a Red Hat Enterprise Linux system. Conceptually, a CentOS platform will work in an identical manner, however the core RHCS packages may not be as up-to-date as those provided by Red Hat.
This guide does not cover the installation and configuration of the nShield Security World client software. For those instructions, see the Installation Guide for your HSM.
Requirements for the Red Hat Enterprise Linux server:
| Component | Minimum Requirements | Recommended Requirements |
|---|---|---|
Memory |
2 GB |
4 GB or more |
Processor |
1 CPU |
1 CPU or more |
Processor Cores |
2 |
4 or more, AES-NI support |
Hard Disk |
20 GB |
80 GB or more |
CD/DVD |
Optional |
Optional |
Network Adapter |
1 |
1 |
USB Controller |
Only required for nShield Remote Administration |
|
Display |
Standard configuration |
|
Components required for installation:
-
Security World software v13.6.12.
-
Red Hat Enterprise Linux v8.10.
-
Linux firewall (
firewalld). -
Static IP address.
-
Mozilla Firefox.
Versions of Mozilla Firefox after v31.6.0 do not support client-side (web browser) initiated key generation functions. -
OpenJDK 64-bit.
-
Red Hat Directory Server (RHDS) v11.
Any LDAP-compliant database should be compatible with the integration.
-
Red Hat Certificate System (RHCS) v10.
Licensing
There is no licensing that is imported into the product after installation. Contact Red Hat for appropriate licensing to purchase RHCS product support and RHN channel access.
Product configurations
RHCS v10.8 has been tested with the following nShield HSM configurations:
| nShield HSM | Software | Firmware | Netimage | Security World | Ciphersuite |
|---|---|---|---|---|---|
Connect XC |
13.6.12 |
13.6.11 |
FIPS-140 Level 3 |
DLf3072s256mAEScSP800131Ar1 |
|
nShield 5C |
13.6.12 |
13.6.12 |
FIPS-140 Level 3 |
DLf3072s256mAEScSP800131Ar1 |
The Common Criteria edition has been tested with the following settings:
| nShield HSM | Software | Firmware | Netimage | Security World | Ciphersuite |
|---|---|---|---|---|---|
Connect XC |
13.6.12 |
12.60.15 |
13.3.2 |
Common Criteria |
DLf3072s256mAEScSP800131Ar1 |
nShield 5C |
13.6.12 |
13.5.1 |
13.6.12 |
Common Criteria |
DLf3072s256mAEScSP800131Ar1 |
Supported nShield functionality
| Red Hat Certificate System does not support module-protected keys. When you are enabling the use of an HSM, RHCS requires a token name, for which module protected keys have none. Using "accelerator" does not work. |
| Feature | Support | Feature | Support |
|---|---|---|---|
Key Generation |
Yes |
Module-only keys |
No |
Key Management |
Yes |
FIPS 140 Level 3 mode support |
Yes |
1-of-N Operator Card Set |
Yes |
Common Criteria mode support |
Yes |
K-of-N Operator Card Set |
Yes |
Load Sharing |
Yes |
Softcards |
Yes |
Failover |
Yes |
Policy requirements
Entrust recommends that your organization operates its PKI using an approved organizational Certificate Policy, Certificate Practices Statement, and any other policy/procedure guidance necessary to govern the administration of the PKI and associated HSM(s). In particular, these documents should specify the following aspects of HSM administration:
-
The number and quorum of Administrator Cards in the Administrator Card Set (ACS), and the policy for managing these cards.
Common Criteria firmware requires a minimum quorum of two Administrator Cards. -
Whether application keys are to be protected by Operator Card Set (OCS) or Softcard protection mechanisms. Module key protection mechanism is not supported.
-
The number and quorum of Operator Cards in the OCS (if OCS key protection is used), and the policy for managing these cards.
-
Whether the security world should be compliant with FIPS 140 Level 3, FIPS 140 Level 2, or Common Criteria.
Entrust recommends that you allow only unprivileged connections unless you are performing administrative tasks. See the User Guide for your HSM and the nShield Security Manual for more recommendations, or contact your local Entrust nShield Account Manager to arrange a technical discussion on architecture and best practices specific to your environment.
Compliance with US government security standards
It may be important for your organization to configure your RHEL OS in compliance with applicable standards such as FIPS.
-
US Government Security Standards for Red Hat products, see https://access.redhat.com/articles/2918071.
-
Information on enabling FIPS mode for RHEL v8, see https://docs.redhat.com/en/documentation/red_hat_enterprise_linux/8/html/security_hardening/using-the-system-wide-cryptographic-policies_security-hardening