Introduction
The Entrust Validation Authority (EVA) Server is an Online Certificate Status Protocol (OCSP) server for distribution of certificate revocation information for certificates issued by any certification authority (CA). The EVA Server provides integrity and validity for online transactions by validating, in real-time, digital certificates issued by a CA. The Entrust nShield Hardware Security Module (HSM) integrates with the Entrust Validation Authority server through the nShield PKCS #11 cryptography API to securely generate and store the OCSP response signing keys. To respond to OCSP requests, Entrust Validation Authority connects with different components.
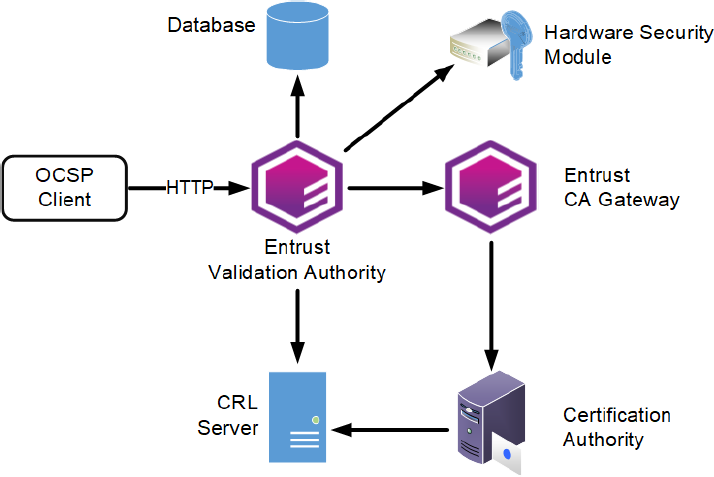
In this architecture:
-
Multiple clients send OCSP requests to the OCSP Responder service of Entrust Validation Authority.
-
Multiple Certification Authorities (CAs) issue certificates.
-
A Hardware Security Module (HSMs) managing one or several OCSP signing keys.
-
One database stores the status of the certificates. For each CA, Entrust Validation Authority obtains the certificate status from either:
-
An Entrust CA Gateway instance.
-
A full or "combined" CRL published in an LDAP or HTTP server. Entrust Validation Authority does not support partitioned CRLs.
-
In this guide, the CA GW was not used and instead Entrust Validation Authority was configured using a Certificate Revocation List (CRL) published on a HTTP server.
Post‑Quantum Ready
This integration brings together the power of Entrust’s next‑generation nShield HSM platform and Entrust Validation Authority technology to deliver security built for the quantum era. With support for NIST‑selected post‑quantum algorithms, the combined solution gives organizations a confident, future‑proof path to quantum‑safe cryptography. By enabling seamless adoption of hybrid and quantum‑resistant protection today, Entrust empowers customers to stay ahead of evolving threats and safeguard mission‑critical keys and operations.
Requirements
The Entrust Validation Authority requires the following software:
-
Entrust Deployment Manager 2.0.2
-
Database
-
Entrust CA Gateway or a CRL Server hosted on a HTTP server.
-
Serial Number server (Not used in this integration)
-
Certification Authority (CA)
Reference the Entrust Validation Authority Deployment Guide for product specific requirements.
Before starting this integration, review:
-
The documentation for the nShield Connect HSM.
-
The documentation and configuration process for Entrust Deployment Manager.
-
The documentation and configuration process for Entrust Validation Authority.
Before using nShield products:
-
When creating a Security World, identify custodians of the administrator card set (ACS).
-
Obtain enough blank smart cards to create the ACS.
-
Define the Security World parameters. For details of the security implications of the choices, see the nShield Security Manual.
| Entrust recommends that you allow only unprivileged connections unless you are performing administrative tasks. |
Licensing
Configuring Entrust Validation Authority requires importing a license text file into the Entrust Deployment Manager server administration web UI. Obtain the license file to configure Entrust Validation Authority in the Entrust Deployment Manager web UI. Also reference the Entrust Validation Authority Deployment Guide for product specific license requirements.
Product configurations
Entrust tested nShield HSM integration with Entrust Validation Authority in the following configurations:
| Product | Version |
|---|---|
Entrust Validation Authority |
2.4.7 |
PKCS11 Library used in EVA |
13.9.0-139-015f0 |
Entrust Deployment Management |
2.0.2 |
Postgres Database |
16 |
easy-rsa CA |
3.1.7 |
Security World |
13.9.3 |
HSM Hardware |
Connect XC, nShield 5C |
Supported features
Entrust tested nShield HSM integration with the following features:
| Softcard | Module | OCS | nSaaS |
|---|---|---|---|
Yes |
Yes |
Yes |
Not Tested |