Install and configure client
This installation must be performed on the client using the <domain_name>\Administrator account.
Installation steps:
Select the protection method
OCS or Module protection can be used to authorize access to the keys protected by the HSM. Follow your organization’s security policy to select which one.
Install the Security World software and create a Security World
-
Install the Security World software. For instructions, see the Installation Guide and the User Guide for the HSM.
-
Install Hotfix TAC-996 if multiple Windows user accounts need access to the same data. Contact nShield support to download the Hotfix. To perform the installation:
-
Open a command window as Administrator and uninstall the CNG:
C:\Users\Administrator.EXAMPLE>cnginstall32 --uninstall nckspsw.dll removed. ncpp.dll removed. C:\Users\Administrator.EXAMPLE>cnginstall --uninstall nckspsw.dll removed. ncpp.dll removed. -
Reboot the server.
-
Copy files as per the installation instructions in the Hotfix package:
C:\Users\Administrator.EXAMPLE>copy C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\* "C:\Program Files\nCipher\nfast\c\caping\vs2017-32\lib\." C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\nckspsw.dll Overwrite C:\Program Files\nCipher\nfast\c\caping\vs2017-32\lib\.\nckspsw.dll? (Yes/No/All): All C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\nckspsw.lib C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\nckspsw.map C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\nckspsw.pdb C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\ncpp.dll C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\ncpp.lib C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\ncpp.map C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-32\lib\ncpp.pdb 8 file(s) copied. C:\Users\Administrator.EXAMPLE>copy C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\* "C:\Program Files\nCipher\nfast\c\caping\vs2017-64\lib\." C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\nckspsw.dll Overwrite C:\Program Files\nCipher\nfast\c\caping\vs2017-64\lib\.\nckspsw.dll? (Yes/No/All): All C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\nckspsw.lib C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\nckspsw.map C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\nckspsw.pdb C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\ncpp.dll C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\ncpp.lib C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\ncpp.map C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\c\caping\vs2017-64\lib\ncpp.pdb 8 file(s) copied. C:\Users\Administrator.EXAMPLE>copy C:\Users\Administrator.EXAMPLE\Downloads\hotfix-Z155163-TAC996\hotfix-Z155163-TAC996\nfast\lib\versions\caping-atv.txt "C:\Program Files\nCipher\nfast\lib\versions\." Overwrite C:\Program Files\nCipher\nfast\lib\versions\.\caping-atv.txt? (Yes/No/All): All 1 file(s) copied. -
Open a command window as Administrator and install the CNG:
C:\Users\Administrator.EXAMPLE>cnginstall32 --install nckspsw.dll installed. ncpp.dll installed. C:\Users\Administrator.EXAMPLE>cnginstall --install nckspsw.dll installed. ncpp.dll installed. -
Reboot the server.
-
-
Add the Security World utilities path
C:\Program Files\nCipher\nfast\binto the Windows system path. -
Open the firewall port 9004 for the HSM connections.
-
Install the nShield Connect HSM locally, remotely, or remotely via the serial console. See the following nShield Support articles and the Installation Guide for the HSM:
Access to the Entrust nShield Support Portal is available to customers under maintenance. To request an account, contact nshield.support@entrust.com. -
Open a command window and run the following to confirm that the HSM is
operational:C:\Users\Administrator.EXAMPLE>enquiry Server: enquiry reply flags none enquiry reply level Six serial number 5F08-02E0-D947 6A74-1261-7843 mode operational version 12.80.4 ... Module #1: enquiry reply flags none enquiry reply level Six serial number 5F08-02E0-D947 mode operational version 12.72.1 ... -
Create your Security World if one does not already exist, or copy an existing one. Follow your organization’s security policy for this.
-
Confirm that the Security World is
usable:C:\Users\Administrator.EXAMPLE>nfkminfo World generation 2 state 0x3737000c Initialised Usable ... ... Module #1 generation 2 state 0x2 Usable ...
Create the OCS or Softcard
If using OCS protection, create the OCS now. Follow your organization’s security policy for the value N of K/N. As required, create extra OCS cards, one for each person with access privilege, plus spares.
| Administrator Card Set (ACS) authorization is required to create an OCS in FIPS 140 level 3. |
| After an OCS card set has been created, the cards cannot be duplicated. |
-
If using remote administration, ensure the
C:\ProgramData\nCipher\Key Management Data\config\cardlistfile contains the serial number of the card(s) to be presented. -
Open a command window as Administrator.
-
Run the following command. Follow your organization’s security policy for the values K/N. The OCS cards cannot be duplicated after created. Enter a passphrase or password at the prompt. Notice that
slot 2, remote via a Trusted Verification Device (TVD), is used to present the card. In this example, K=1 and N=1.>createocs -m1 -s2 -N testOCS -Q 1/1 FIPS 140-2 level 3 auth obtained. Creating Cardset: Module 1: 0 cards of 1 written Module 1 slot 0: Admin Card #1 Module 1 slot 2: empty Module 1 slot 3: empty Module 1 slot 2: blank card Module 1 slot 2:- passphrase specified - writing card Card writing complete. cardset created; hkltu = a165a26f929841fe9ff2acdf4bb6141c1f1a2eedAdd the
-p(persistent) option to the command above to retain authentication after the OCS card has been removed from the HSM front panel slot, or from the TVD. If using OCS card protection and the non-persistent card configuration, OCS cards need to be inserted in the nShield front panel or always present in the TVD. The authentication provided by the OCS as shown in the command line above is non-persistent and only available for K=1 and while the OCS card is present in the HSM front panel slot or TVD. -
Verify the OCS created:
nfkminfo -c Cardset list - 1 cardsets: (P)ersistent/(N)ot, (R)emoteable/(L)ocal-only Operator logical token hash k/n timeout name a165a26f929841fe9ff2acdf4bb6141c1f1a2eed 1/1 none-NL testOCSThe
rocsutility also shows the OCS created:>rocs `rocs' key recovery tool Useful commands: `help', `help intro', `quit'. rocs> list cardset No. Name Keys (recov) Sharing 1 testOCS 0 (0) 1 of 1 rocs> quit
If using Softcard protection, create the Softcard now.
-
Ensure the
C:\Program Files\nCipher\nfast\cknfastrcfile exists with the following content. Otherwise create it.> type "C:\Program Files\nCipher\nfast\cknfastrc" CKNFAST_LOADSHARING=1 -
Run the following command and enter a passphrase/password at the prompt:
>ppmk -n testSC Enter new pass phrase: Enter new pass phrase again: New softcard created: HKLTU d9414ed688c6405aab675471d3722f8c70f5d864 -
Verify the Softcard was created:
>nfkminfo -s SoftCard summary - 1 softcards: Operator logical token hash name d9414ed688c6405aab675471d3722f8c70f5d864 testSCThe
rocsutility also shows the OCS and Softcard created.>rocs `rocs' key recovery tool Useful commands: `help', `help intro', `quit'. rocs> list cardset No. Name Keys (recov) Sharing 1 testOCS 0 (0) 1 of 1 2 testSC 0 (0) (softcard) rocs>quit
Install and register the CNG provider
To install and register the CNG provider:
-
Select Start > Entrust > CNG configuration wizard.
-
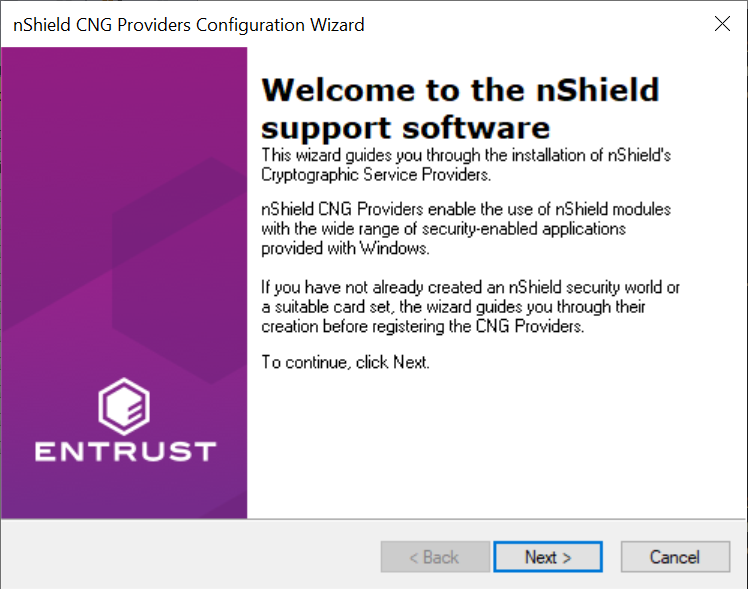
Select Next on the Welcome window.
-
Select Next on the Enable HSM Pool Mode window, leaving Enable HSM Mode for CNG Providers un-checked.
If you intend to use multiple HSMs in a failover and load-sharing capacity, select Enable HSM Pool Mode for CNG Providers. If you do, you can only use module protected keys. Module protection does not provide conventional 1 or 2 factor authentication. Instead, the keys are encrypted and stored as an application key token, also referred to as a Binary Large Object (blob), in the kmdata/localdirectory. -
Select Use existing security world on the Initial setup window. Then select Next.
-
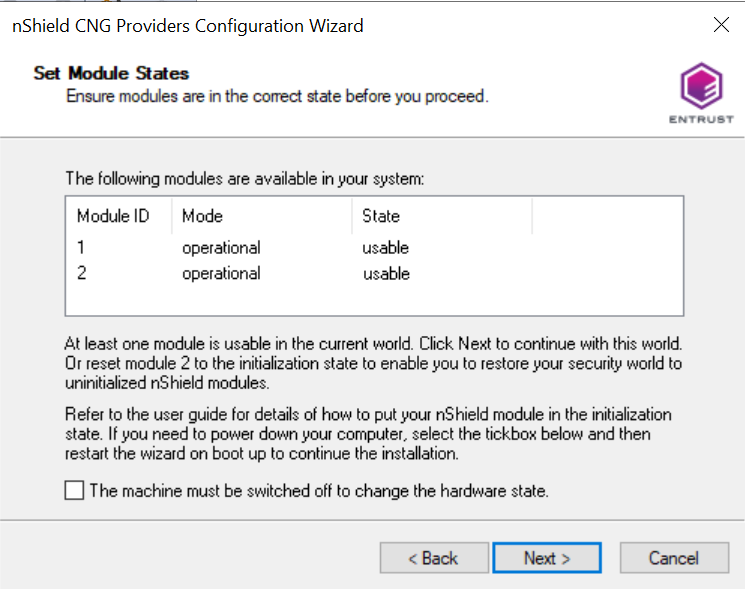
Select the HSM (Module) if more than one is available on the Set Module States window. Then select Next.
-
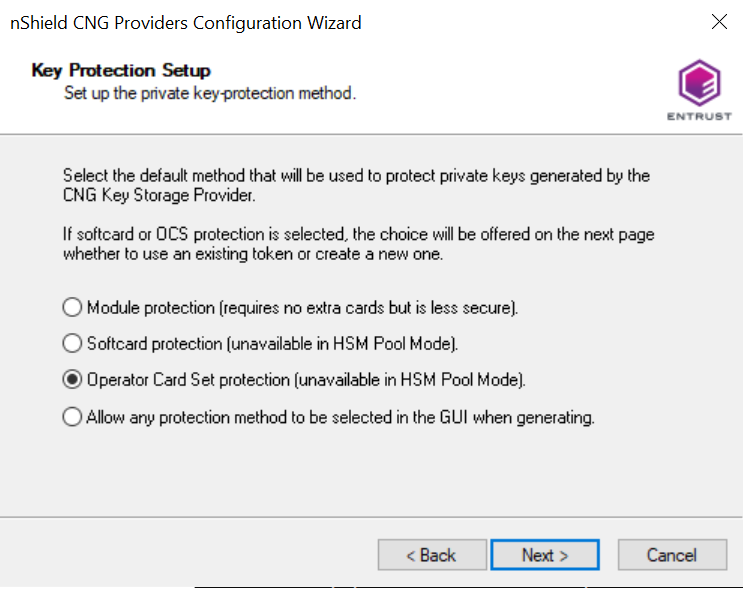
In Key Protection Setup, select Operator Card Set protection. Then select Next.
-
Choose from the Current Operator Card Sets or Current Softcards list. These were created above. Then select Next and Finish.
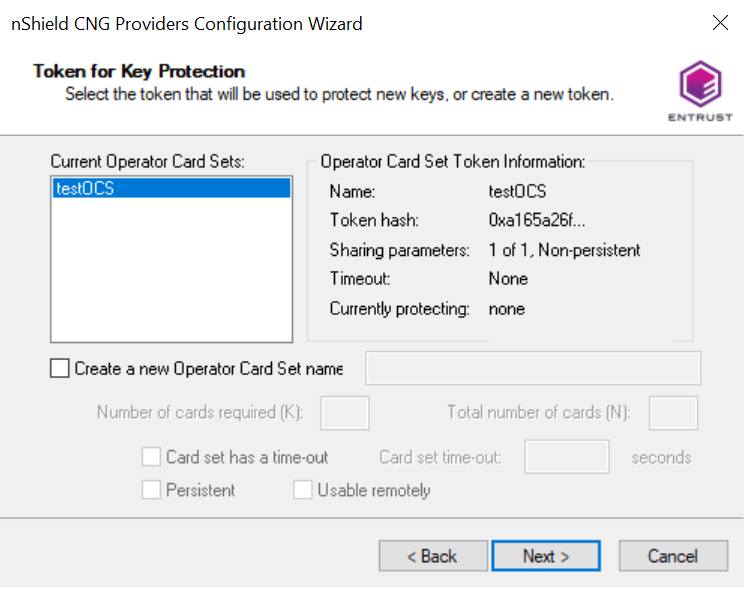
-
Verify the provider with the following commands:
>certutil -csplist | findstr nCipher Provider Name: nCipher DSS Signature Cryptographic Provider Provider Name: nCipher Enhanced Cryptographic Provider Provider Name: nCipher Enhanced DSS and Diffie-Hellman Cryptographic Provider Provider Name: nCipher Enhanced DSS and Diffie-Hellman SChannel Cryptographic Provider Provider Name: nCipher Enhanced RSA and AES Cryptographic Provider Provider Name: nCipher Enhanced SChannel Cryptographic Provider Provider Name: nCipher Signature Cryptographic Provider Provider Name: nCipher Security World Key Storage Provider >cnglist.exe --list-providers | findstr nCipher nCipher Primitive Provider nCipher Security World Key Storage Provider -
Check the registry in
CNGRegistry:HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Cryptography\Providers\nCipherSecurityWorldKeyStorageProvider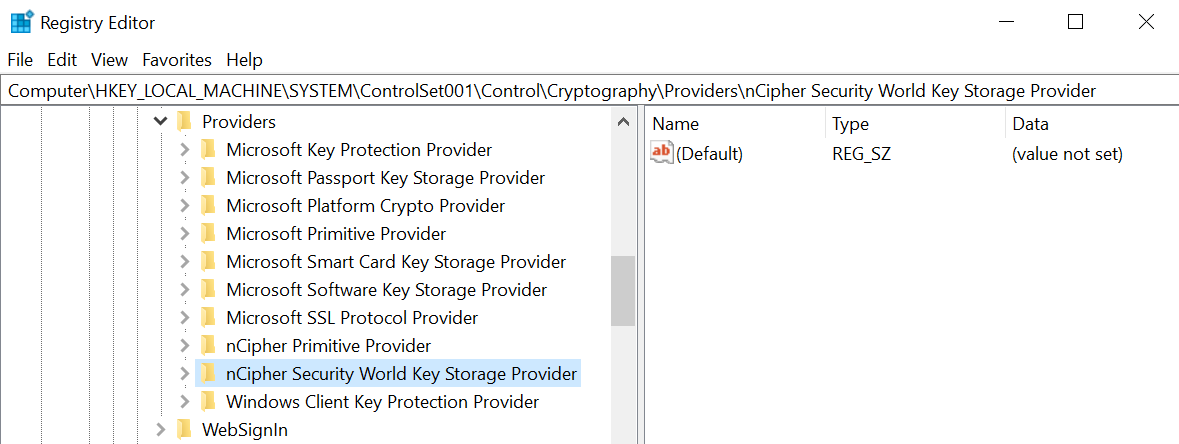
Install and configure SqlServer PowerShell module
-
Open a PowerShell session as Administrator and run:
PS C:\Users\Administrator.EXAMPLE> [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 PS C:\Users\Administrator.EXAMPLE> Install-PackageProvider Nuget -force -verbose VERBOSE: Acquiring providers for assembly: C:\Program Files\WindowsPowerShell\Modules\PackageManagement\1.4.7\fullclr\Microsoft.PackageManagement.CoreProviders.dll ... VERBOSE: Imported provider 'C:\Program Files\PackageManagement\ProviderAssemblies\nuget\2.8.5.208\Microsoft.PackageManagement.NuGetProvider.dll' . -
Update PowerShellGet:
PS C:\Users\Administrator.EXAMPLE> Install-Module -Name PowerShellGet -force -verbose VERBOSE: Using the provider 'PowerShellGet' for searching packages. ... VERBOSE: Module 'PowerShellGet' was installed successfully to path 'C:\Program Files\WindowsPowerShell\Modules\PowerShellGet\2.2.5'. -
Download and install the SqlServer module to configure Always Encrypted using Power Shell:
PS C:\Users\Administrator.EXAMPLE> Install-Module -Name SqlServer -force -verbose -AllowClobber VERBOSE: Using the provider 'PowerShellGet' for searching packages. ... VERBOSE: Module 'SqlServer' was installed successfully to path 'C:\Program Files\WindowsPowerShell\Modules\SqlServer\21.1.18256'.The -AllowClobberparameter allows you to import the specified commands if it exists in the current session. -
Once installed, confirm the install by running the command below.
If you are using PowerShell ISE, refresh the Commands pane. If you are using PowerShell, open a new session. PS C:\Users\Administrator.EXAMPLE> Get-Module -list -Name SqlServer Directory: C:\Program Files\WindowsPowerShell\Modules ModuleType Version Name ExportedCommands ---------- ------- ---- ---------------- Script 21.1.18256 SqlServer {Add-RoleMember, Add-SqlAvailabilityDatabase, Add-SqlAvail...