Generate the encryption keys
Generate the Always Encrypted Column Master Key (CMK)
The CMK is protected by the nShield HMS.
-
Log in to the client using the <domain>\dbuser, or a suitable security administrator account.
-
Launch PowerShell and run the
Generate_AECMK.ps1script (shown below).$cngProviderName = "nCipher Security World Key Storage Provider" $cngAlgorithmName = "RSA" $cngKeySize = 2048 $cngKeyName = "AECMK" $cngProvider = New-Object System.Security.Cryptography.CngProvider($cngProviderName) $cngKeyParams = New-Object System.Security.Cryptography.CngKeyCreationParameters $cngKeyParams.provider = $cngProvider $cngKeyParams.KeyCreationOptions = [System.Security.Cryptography.CngKeyCreationOptions]::OverwriteExistingKey $keySizeProperty = New-Object System.Security.Cryptography.CngProperty("Length", [System.BitConverter]::GetBytes($cngKeySize), [System.Security.Cryptography.CngPropertyOptions]::None); $cngKeyParams.Parameters.Add($keySizeProperty) $cngAlgorithm = New-Object System.Security.Cryptography.CngAlgorithm($cngAlgorithmName) $cngKey = [System.Security.Cryptography.CngKey]::Create($cngAlgorithm, $cngKeyName, $cngKeyParams)-
Run the following command:
> PowerShell -ExecutionPolicy Bypass -File Generate_AECMK.ps1The following dialog appears.
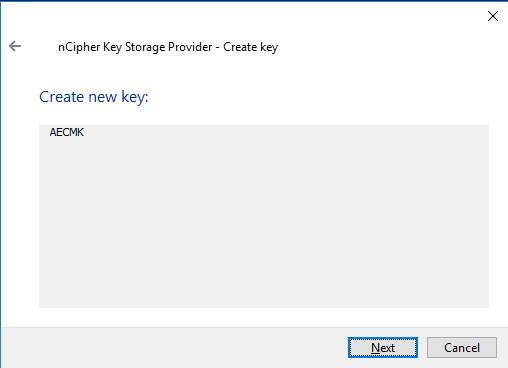
-
Select Next.
-
Select the Operator Card Set Protection. Insert the OCS card in the HSM or via the TVB is using remote administration and select Next.
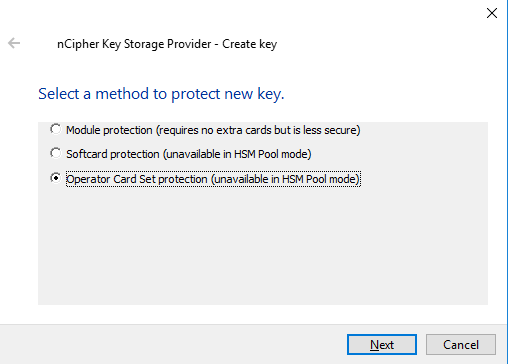
-
Select the OCS and then select Next.
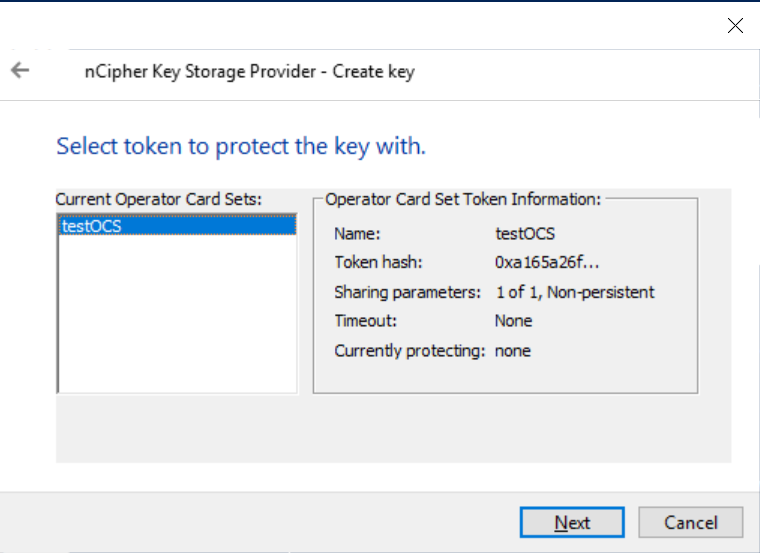
-
Select the HSM and select Finish.
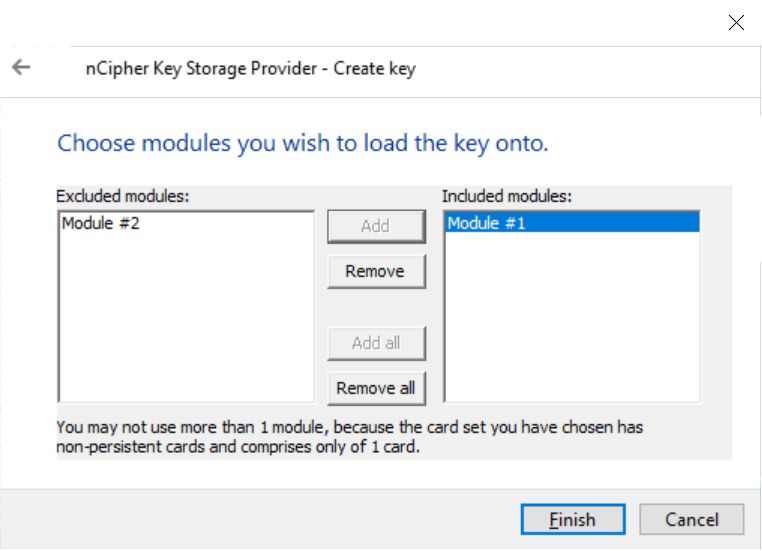
-
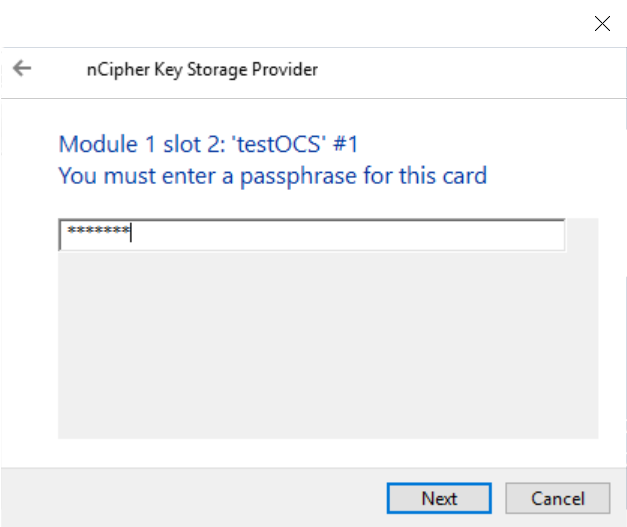
Enter the OCS passphrase and select Next.
-
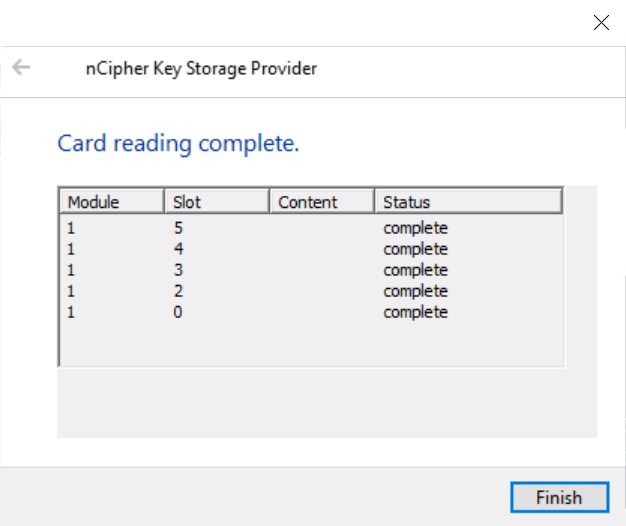
Select Finish.
A 2048-bit RSA key pair, called
AECMK, has been generated. The key is encrypted in the HSM and then pushed to the requesting client server, where it is stored as an Application Key Token in the%NFAST_KMDATA%\localfolder. This folder is typicallyC:\ProgramData\nCipher\Key Management Data\local. -
-
Verify the new key:
>nfkminfo -k Key list - 1 keys AppName caping Ident user--e57798f862740453d02379579c1758ddfa2189db -
Display the information about the key by copy-pasting the key name above as follows:
>nfkminfo -k caping user--e57798f862740453d02379579c1758ddfa2189db Key AppName caping Ident user--e57798f862740453d02379579c1758ddfa2189db BlobKA length 1128 BlobPubKA length 484 BlobRecoveryKA length 1496 name "AECMK" hash bccc75af6b2b8348815b14185712d5407ceffcb5 recovery Enabled protection CardSet other flags PublicKey !SEEAppKey !NVMemBlob +0x0 cardset edb3d45a28e5a6b22b033684ce589d9e198272c2 gentime 2025-10-01 17:09:54 SEE integrity key NONE BlobKA format 6 Token other flags 0x0 hkm b01a7d6ac910b720bf4319f5067a4569f087f81b hkt edb3d45a28e5a6b22b033684ce589d9e198272c2 hkr none BlobRecoveryKA format 9 UserKey other flags 0x0 hkm none hkt none hkr d00f8956fcda01bd4c7f539ee042ef6b5ac75917 BlobPubKA format 5 Module other flags 0x0 hkm c2be99fe1c77f1b75d48e2fd2df8dffc0c969bcb hkt none hkr none Extra entry #1 typecode 0x10000 65536 length 60 Not a blob
Generate My Column Master Key (MyCMK) and My Column Encryption Key (MyCEK) with SSMS
This key will encrypt all subsequent Column Encryption keys (CEKs) in your database.
-
Log in to the client using the <domain>\dbuser account.
-
Launch Microsoft SQL Server Management Studio.
-
Connect to the database on the remote SQL server:
-
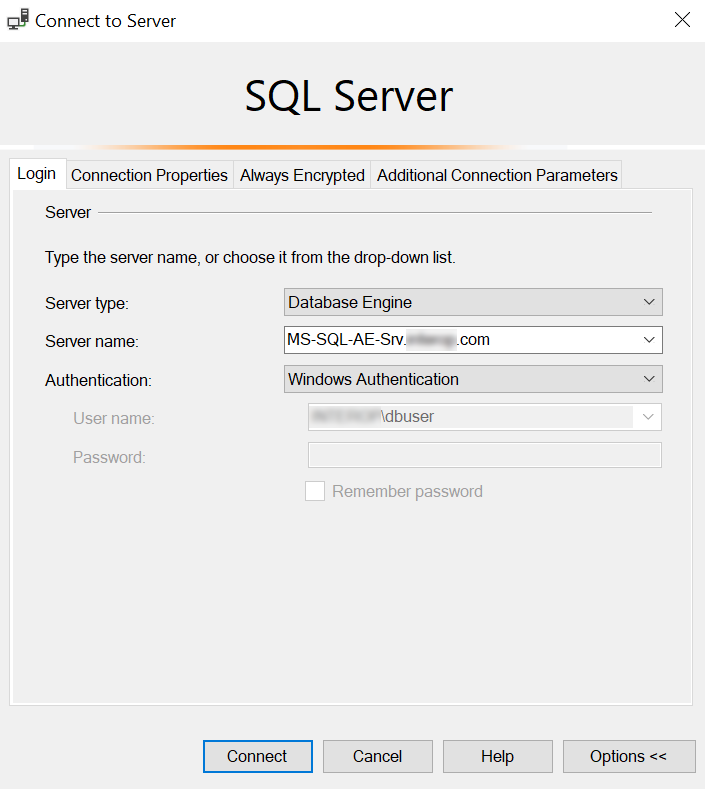
Select the Login tab and set it as follows:
-
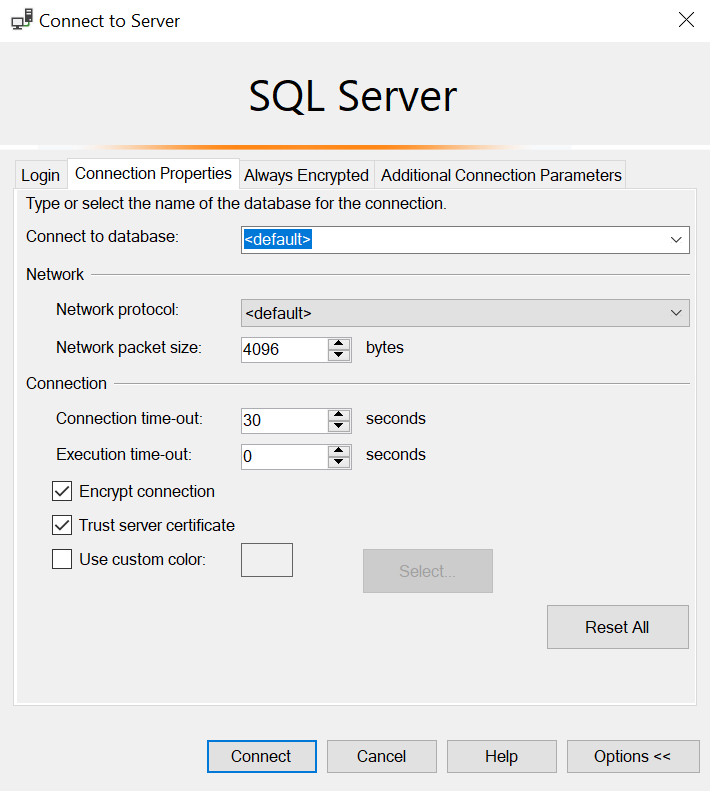
Select the Connection Properties tab, as set as follows:
-
Select the Always Encrypted tab and select Enable Always Encrypted:
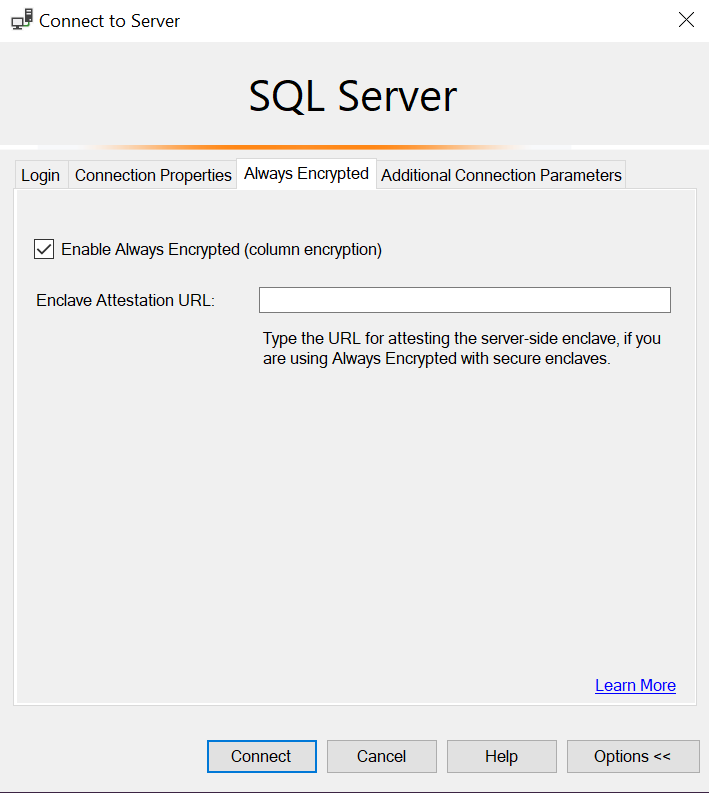
-
Select Connect.
-
-
Using the Object Explorer, select the Security directory under the required database, then select Always Encrypted Keys > Column Master Key > New Column Master Key.
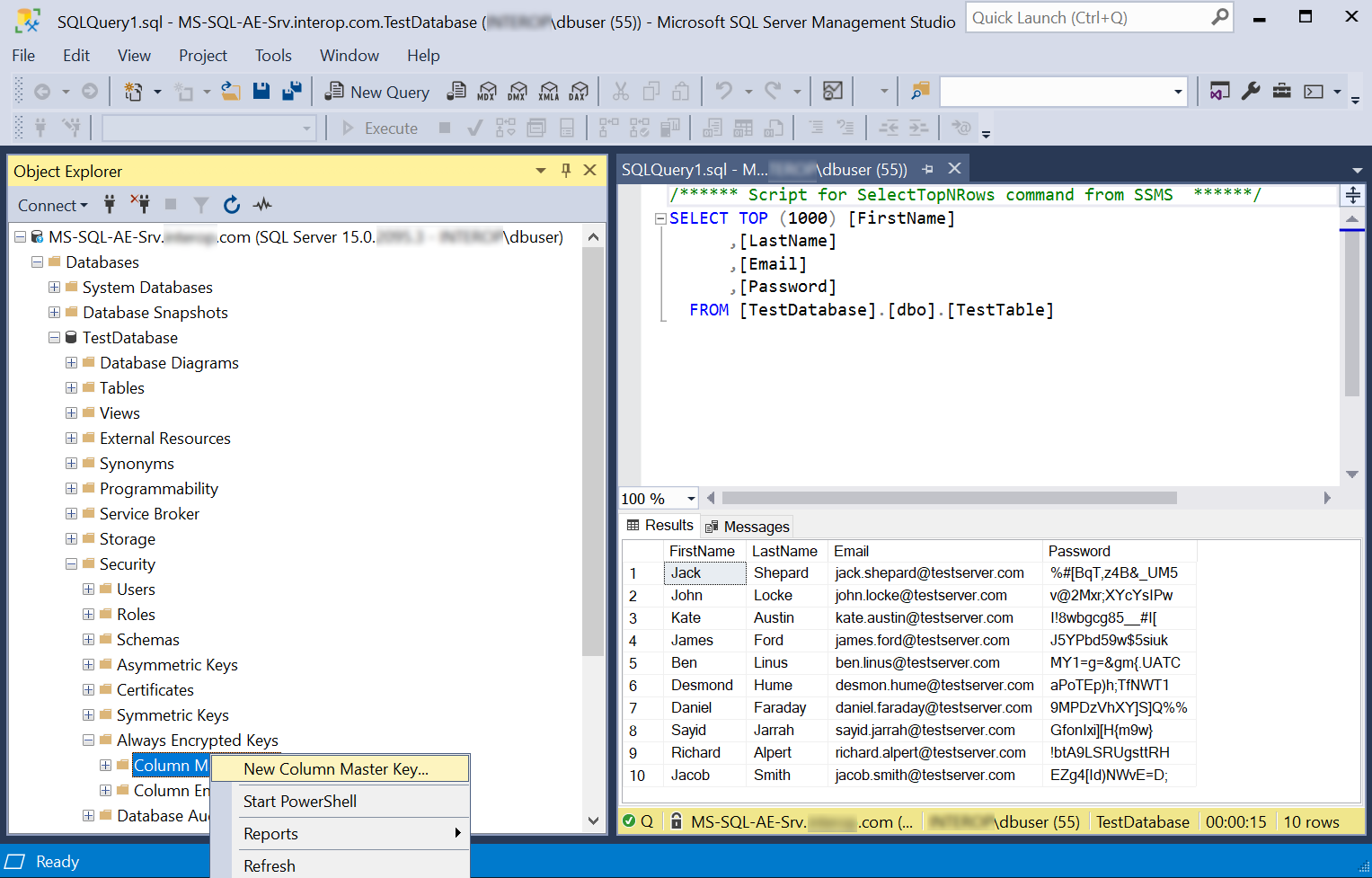
-
Enter the following information on the Column Master Keys dialog:
-
Enter a Name, for example MyCMK.
-
Select Key Storage Provider (CNG) from the Key store drop-down list and then Select a provider.
-
Select nCipher Security World Key Storage Provider from the drop-down list.
The AECMK key created in an earlier step appears in Name.
-
Select OK to create a new key using the nShield HSM and CNG KSP.
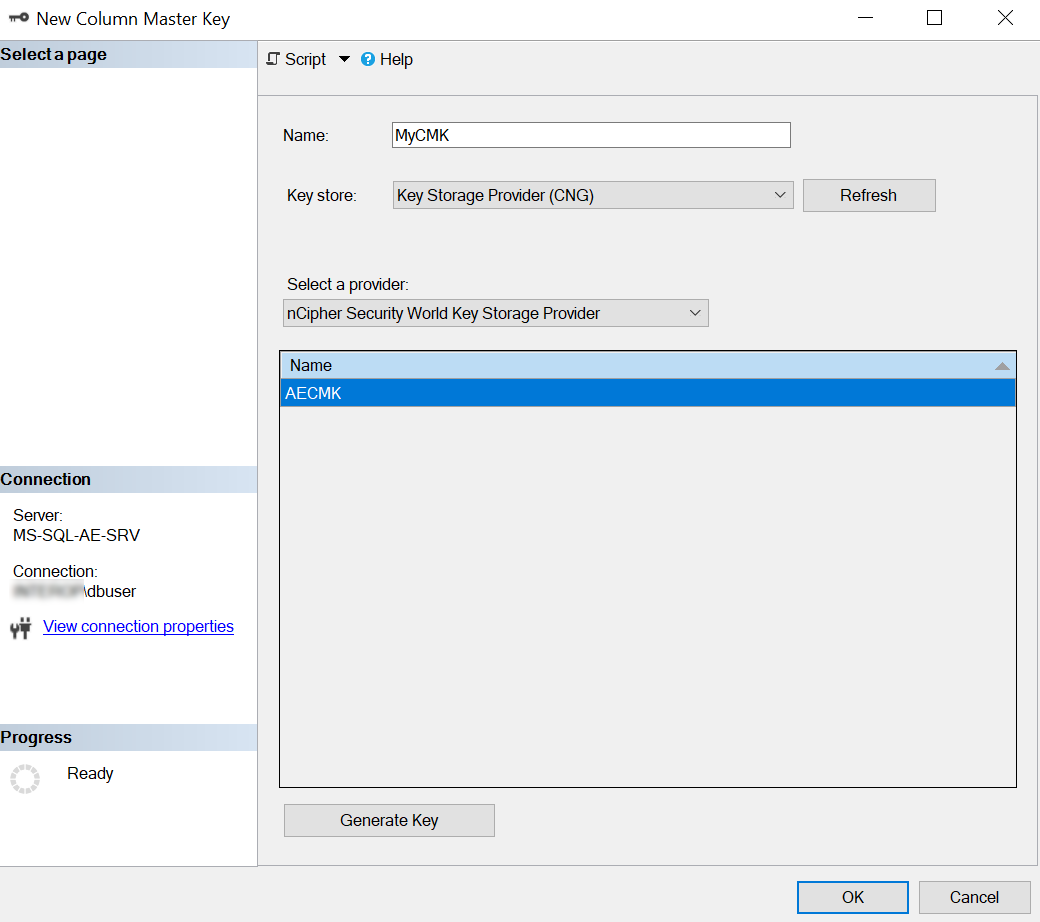
-
-
Select Next.
The newly-created MyCMK is in the database under Security > Always Encrypted Keys > Column Master Keys.
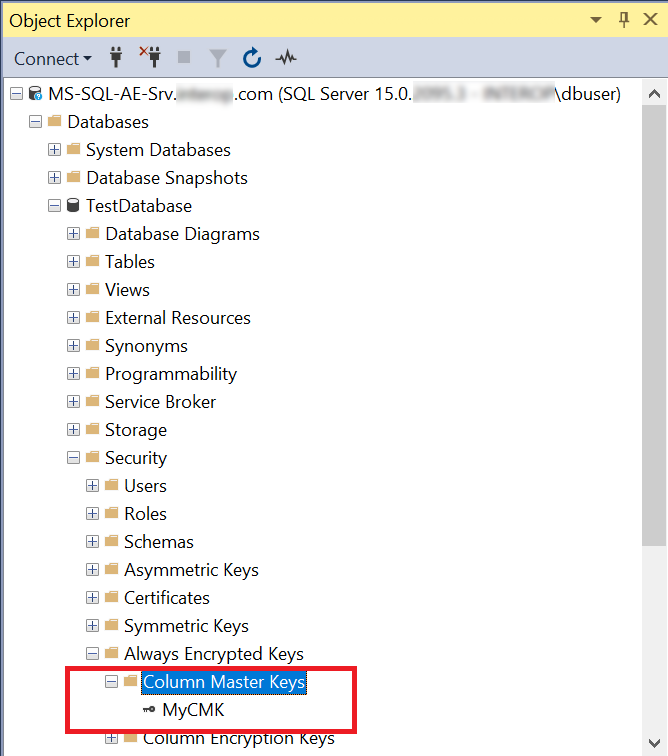
-
Using Object Explorer, select the Security directory under the required database. Select Always Encrypted Keys to expand it, then select New Column Encryption Key.
-
Enter Name, select the CMK, then select OK.
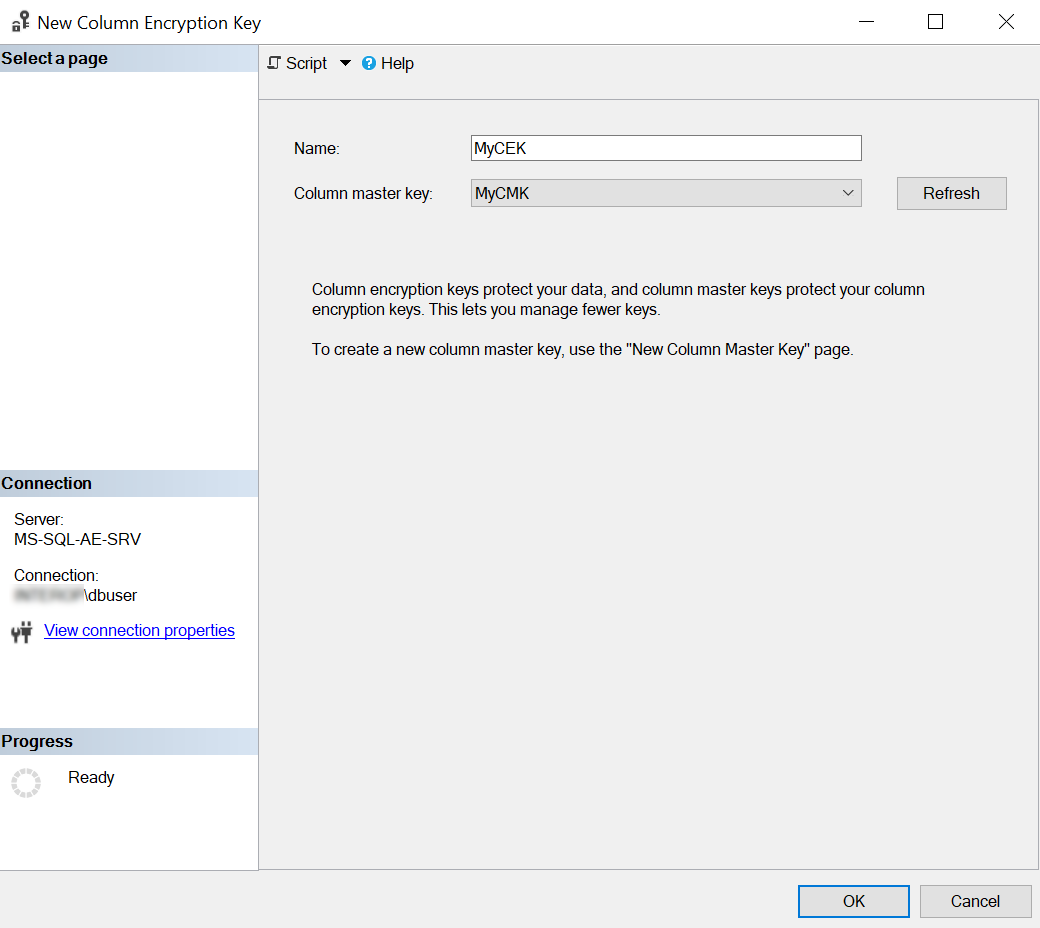
-
Insert the OCS card in the HSM or via the TVB is using remote administration. Then select Next.
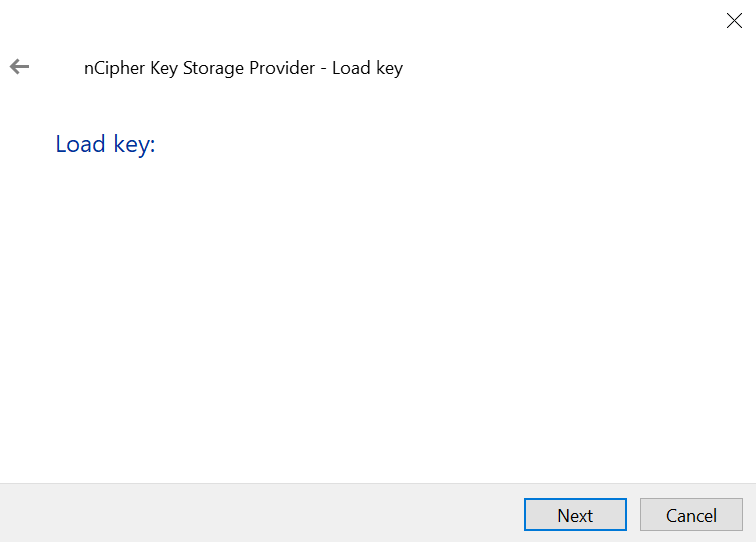
-
Select the HSM and then select Finish.
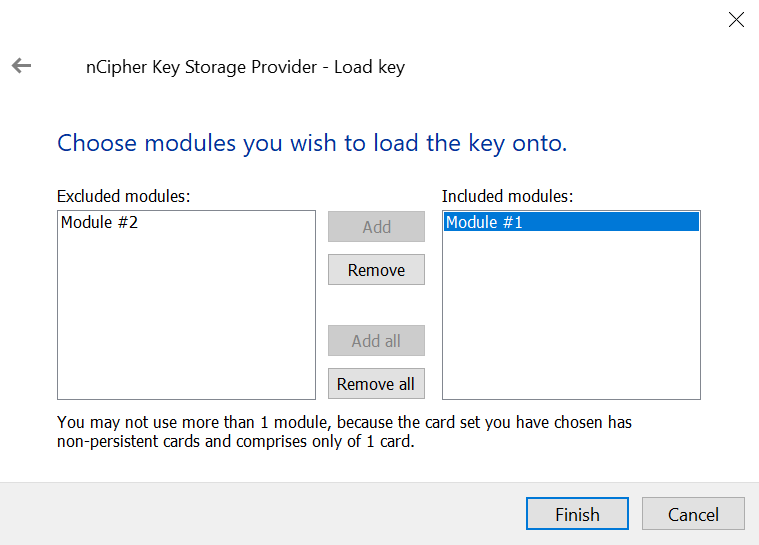
-
Enter the passphrase and then select Next.
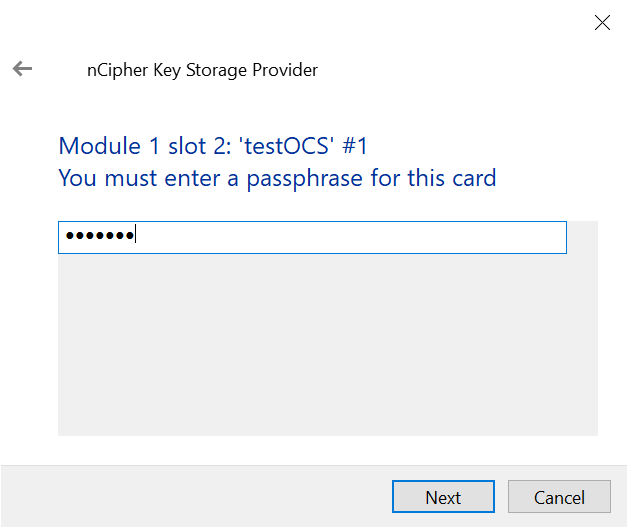
-
Select Finish after the OCS card reading completes.
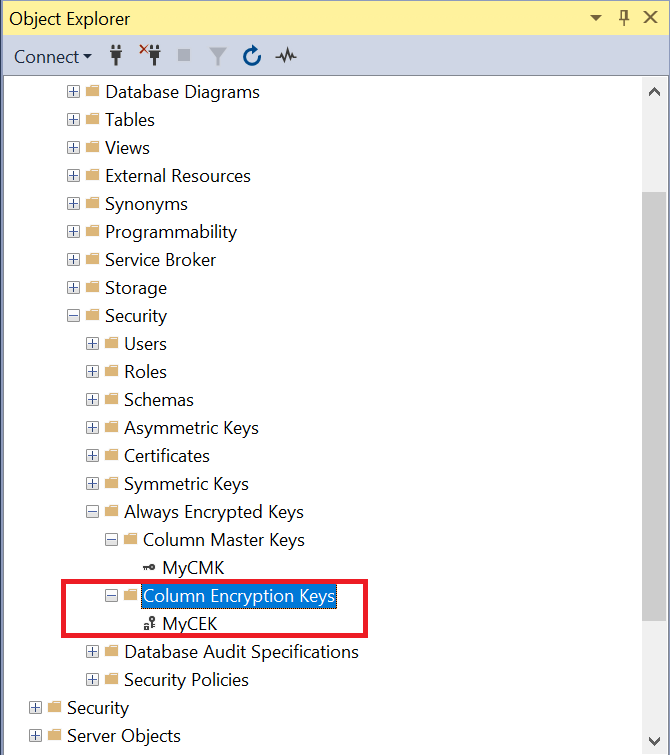
The newly-created MyCEK is in the database under Security > Always Encrypted Keys > Column Encryption Keys.
Generate MyCMK and MyCEK with PowerShell
To generate MyCMK and MyCEK with PowerShell:
-
Delete MyCEK and MyCMK in that order created above by right-clicking each key and selecting Delete.
-
Launch PowerShell and run the
Generate_MyCMK_and_MyCEK.ps1script (below).# Import the SqlServer module. Import-Module SqlServer # Connect to database. $ConnectionString = "Data Source=mssql-ae2025srv.interop.local,1433;Initial Catalog=TestDatabase;Trusted_Connection=True;MultipleActiveResultSets=False;Encrypt=True;TrustServerCertificate=True;Packet Size=4096;Application Name=`"Microsoft SQL Server Management Studio`"" $Database = Get-SqlDatabase -ConnectionString $ConnectionString # Create a SqlColumnMasterKeySettings object for your column master key. $cmkSettings = New-SqlCngColumnMasterKeySettings -CngProviderName "nCipher Security World Key Storage Provider" -KeyName "AECMK" # Create column master key metadata in the database. New-SqlColumnMasterKey -Name "MyCMK" -InputObject $Database -ColumnMasterKeySettings $cmkSettings # Generate a column encryption key, encrypt it with the column master key and create column encryption key metadata in the database. New-SqlColumnEncryptionKey -Name "MyCEK" -InputObject $Database -ColumnMasterKey "MyCMK"The command line is:
> PowerShell -ExecutionPolicy Bypass -File Generate_MyCMK_and_MyCEK.ps1 Name ----- MyCMK MyCEK -
Present the OCS, select the HSM, and enter the passphrase.
-
Check the newly-created MyCMK and MyCEK are present.