Create a generic web application
Create a generic web application that uses OpenID Connect and OAUTH Cloud Integration. This is the application Entrust CloudControl uses to integrate with Entrust IDaaS.
Create Entrust IDaaS application
-
Sign in to your unique Entrust IDaaS registration URL.
-
Select Home > Applications.
-
Select the + icon on the left of the page and scroll down to OpenID Connect and OAuth Cloud Integration.
-
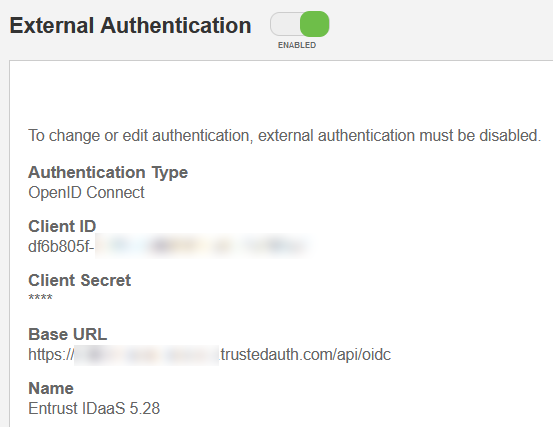
Select Generic Web Application. The Add Generic Web Application page appears.

-
Change the Application Name, Description and Add an Application Logo as required. Check both Enable user login and Enable passkey login.
-
Select Next.
-
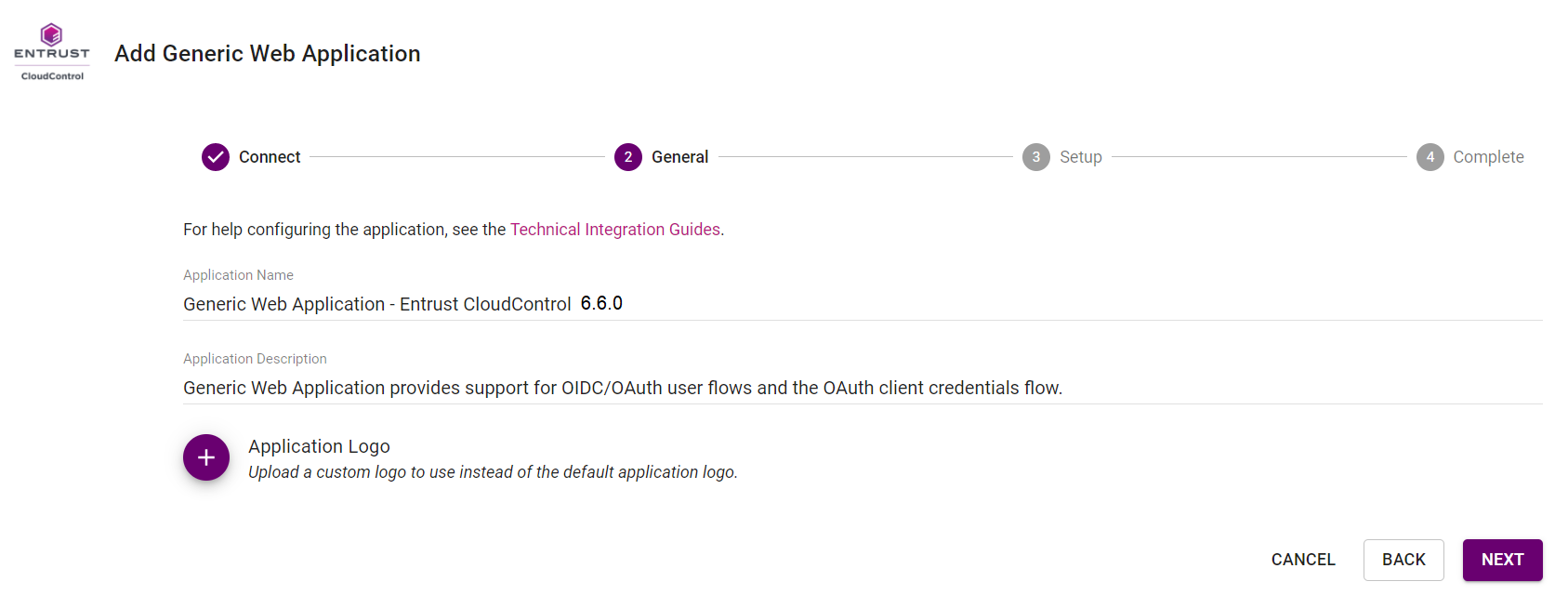
In the Setup page, under General Settings, do the following:
-
Copy and paste the Client ID and the Client Secret to a safe location. These will be used when configuring the OpenID connect in Entrust CloudControl.
-
Change Token / Revocation Endpoint Client Authentication Method to Client Secret Post using the pull-down menu.
-
Change Subject ID Attribute to UserPrincipalName.
-
For Login Redirect URLs and Logout Redirect URLs, select ADD and enter the URL as described in Configuring Entrust Identity as a Service to use with Entrust CloudControl.
For example:
-
-
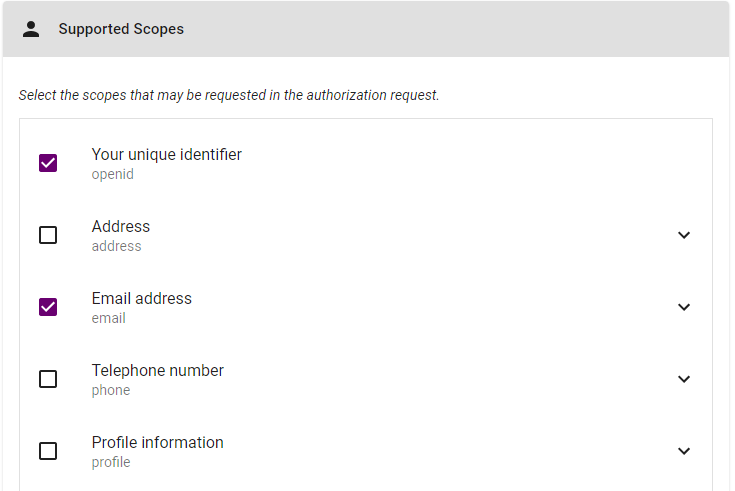
In the Setup page, under Supported Scopes:
-
Select Your Unique Identifier.
-
Select Email Address.
-
Leave all other settings as default.
For example:
-
-
Select Submit to complete the application creation. The Add Generic Web Application Complete page appears.
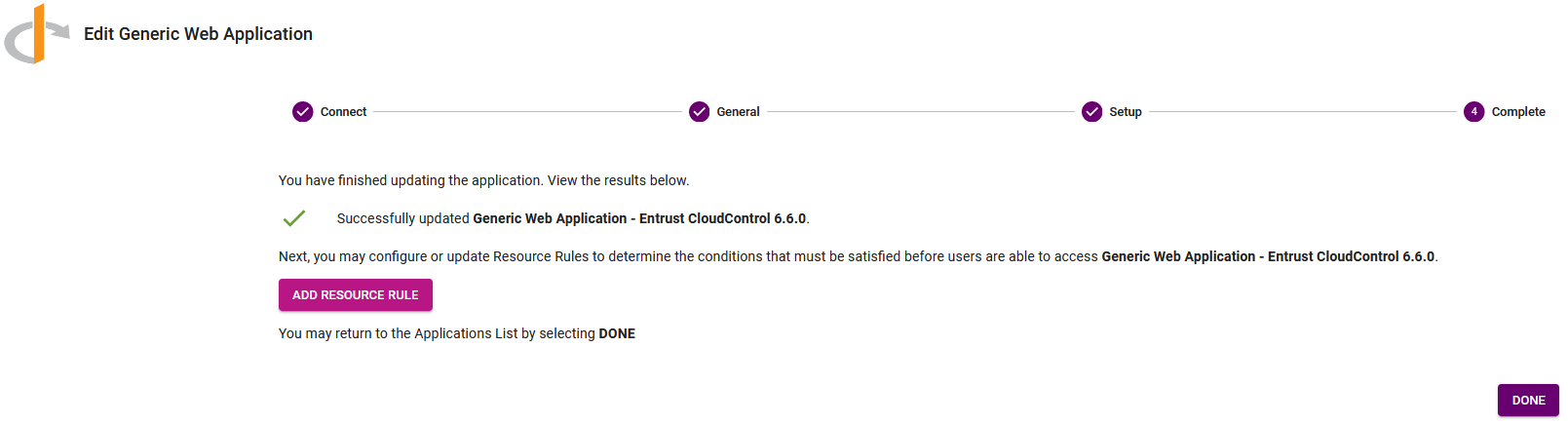
Add a resource rule to the application
Add a resource rule to the Entrust IDaaS application for the AD group and users to access the application. For additional information, refer to Create a resource rule in the online documentation.
-
Sign in to your unique Entrust IDaaS registration URL.
-
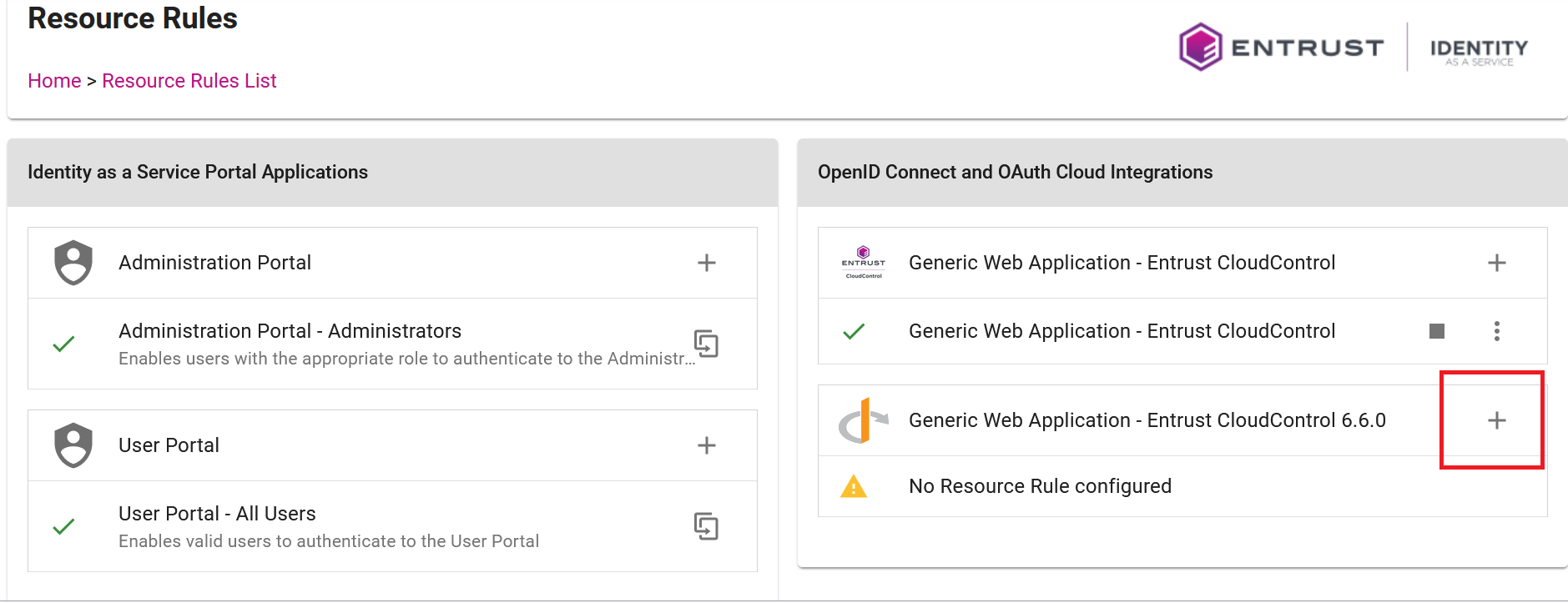
From the Main Menu in the top-right, select Resources > Resource Rules. The Resource Rules List page appears.
-
Select the + icon on the generic web application created in Configure your Active Directory. The Add Resource List page appears.
-
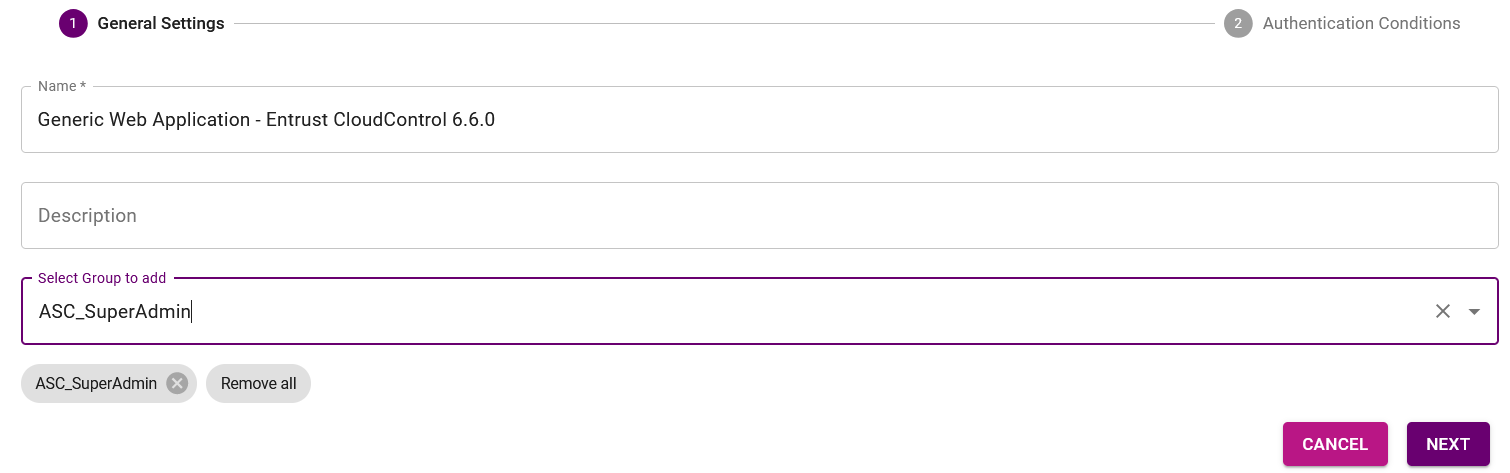
In the General Settings go to the the Select Group to add pull-down menu and select ASC_SuperAdmin, then select Next. This is the group created in [configure-active-directory].
-
In the Authentication Conditions page:
-
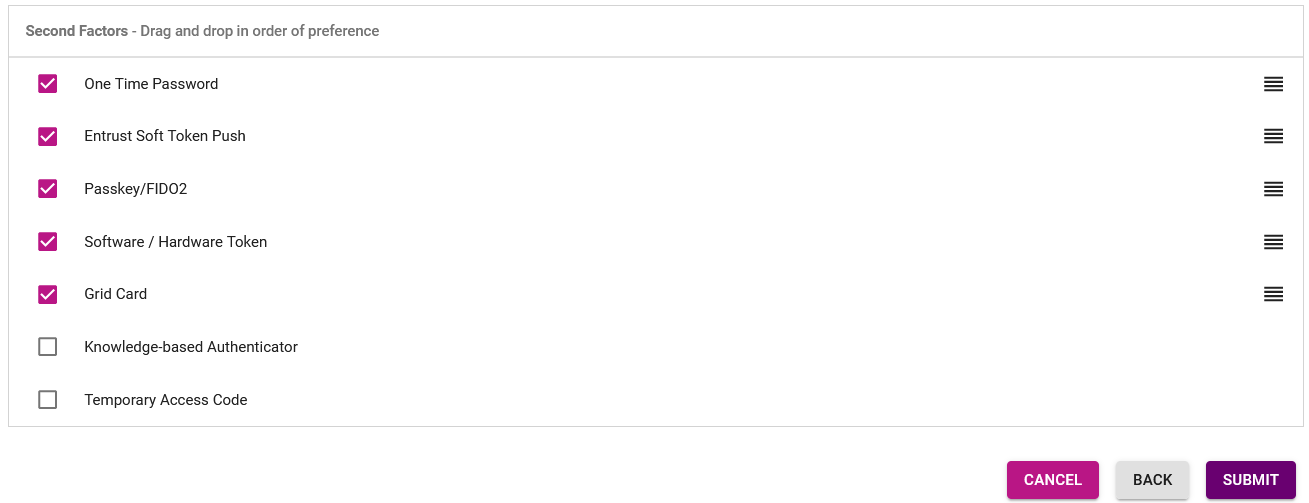
Select Password from the First Factor pull-down menu.
-
In the Second Factor box, select the checkboxes for the following factors and rearrange them into the order in which they are listed here, unless determined otherwise by your organization. Clear the checkboxes for all other factors not listed here.
-
One Time Password
-
Entrust Soft Token Push
-
Passkey/FIDO2
-
Software / Hardware Token
-
Grid Card
-
-
-
Select Submit. A check mark appears next to the generic web application.
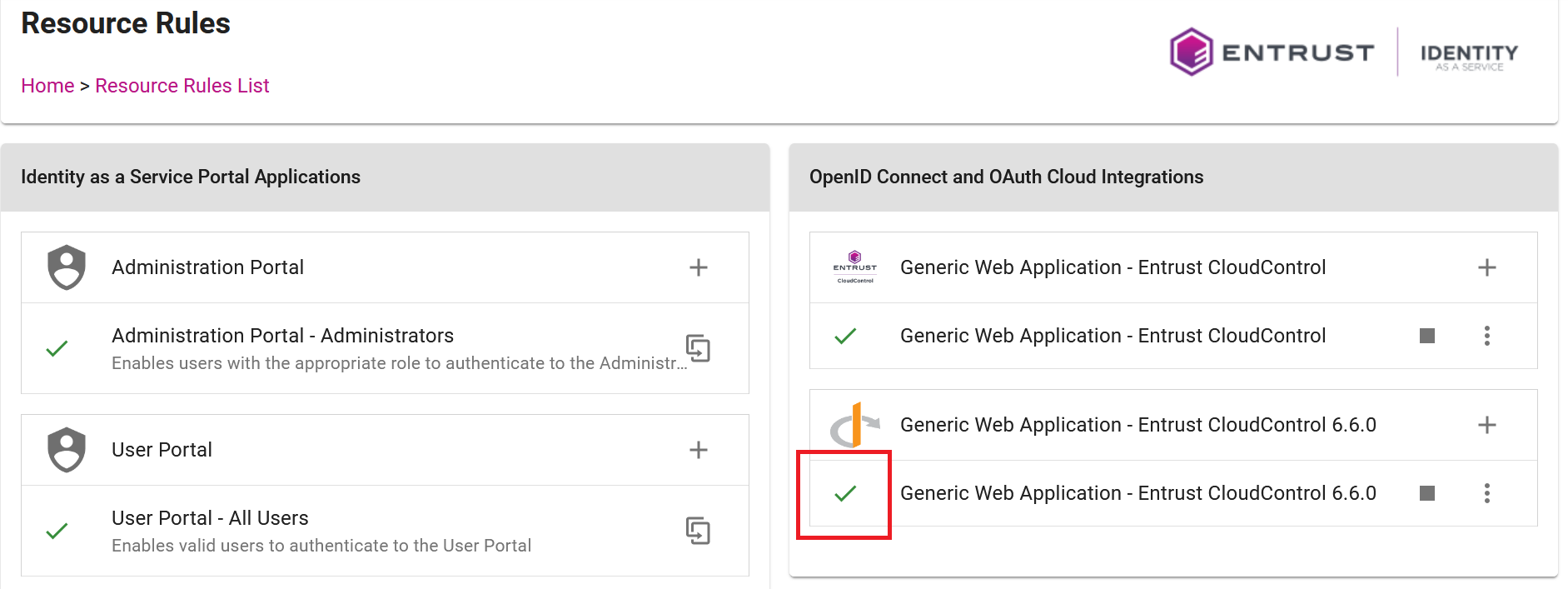
Enable external authentication in Entrust CloudControl to use Entrust IDaaS
-
Sign in to the Entrust CloudControl virtual appliance with the etccadmin account created in Configure your Active Directory.
-
Select Home > System > External Authentication.
-
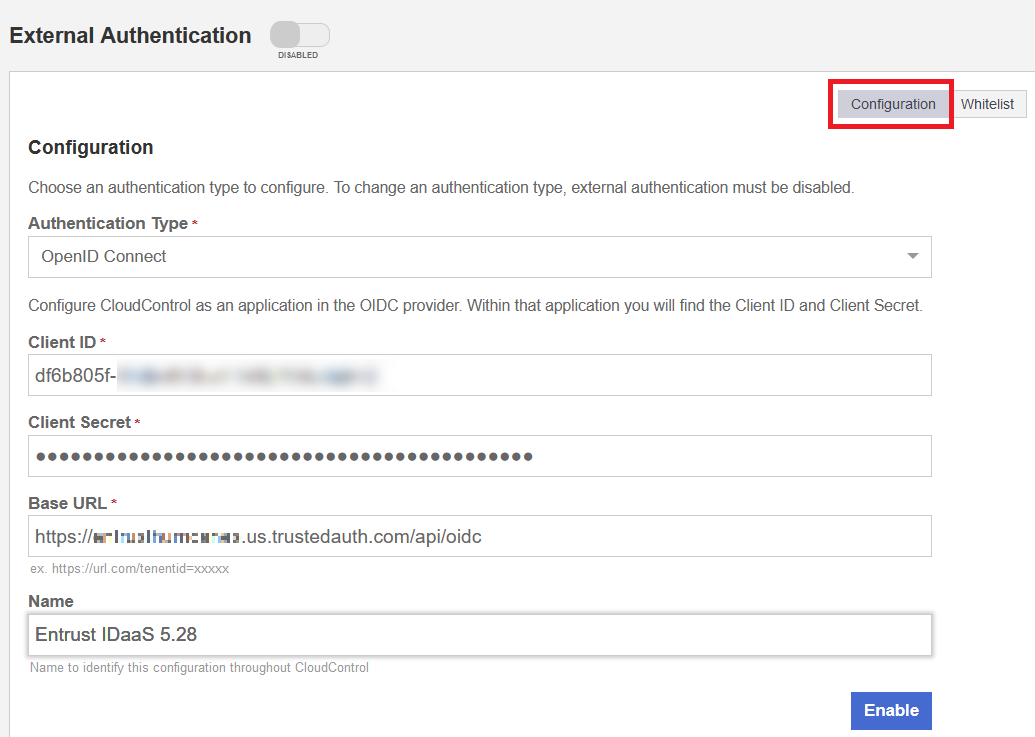
In the External Authentication tab, select Configuration, and enter the following information:
Item Value Authentication Type
OpenId Connect (from pull-down menu)
Client ID
Client ID from section Create Entrust IDaaS application
Client Secret
Client Secret from section Create Entrust IDaaS application
Base URL
Your unique Entrust IDaaS registration URL followed by
api/oidc.Name
Enter a name.
For example:
-
In the External Authentication tab, select Whitelist, and enter the etccadmin user created in Configure your Active Directory. This user would be able to sign in without Entrust IDaaS authentication in the event of a configuration issue. Then select Enable.
Users on the whitelist are exempt from external authentication and can sign in directly using Active Directory credentials. 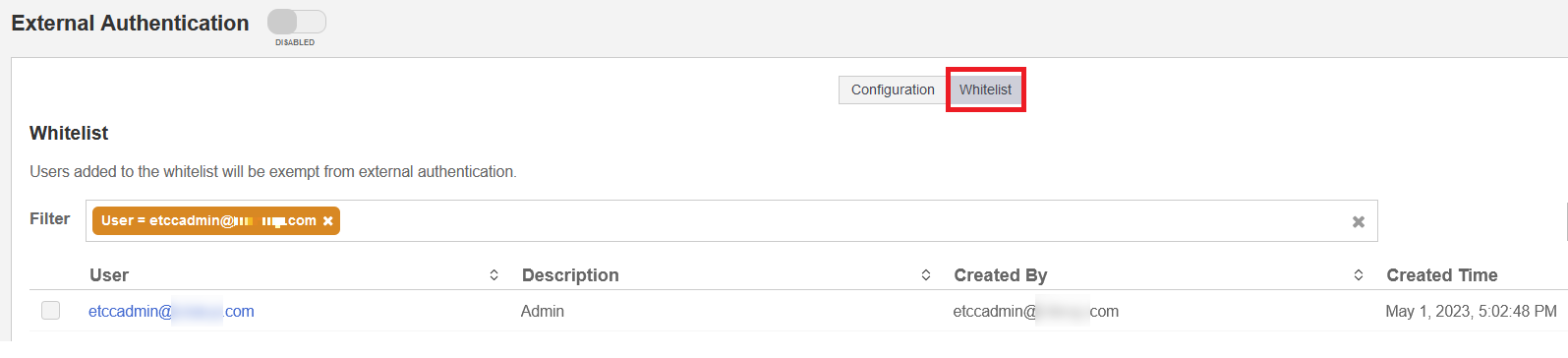
-
Select Enable back in Configuration. The OpenID Connect Configuration dialog appears.
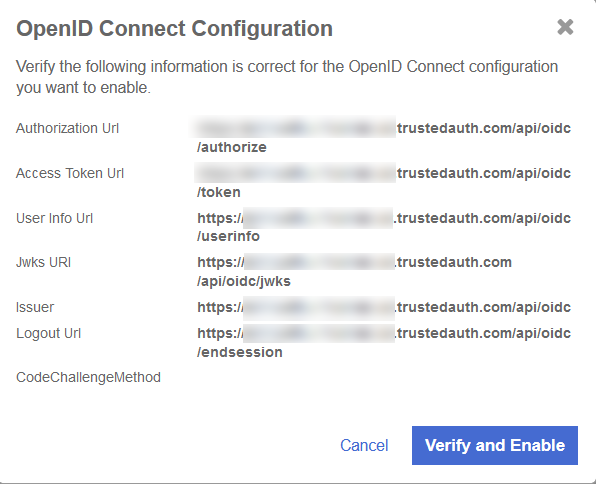
-
Return to the Configuration screen, still in the External Authentication tab, and select Enable. External configuration is now enabled.