Configure Google Cloud Platform
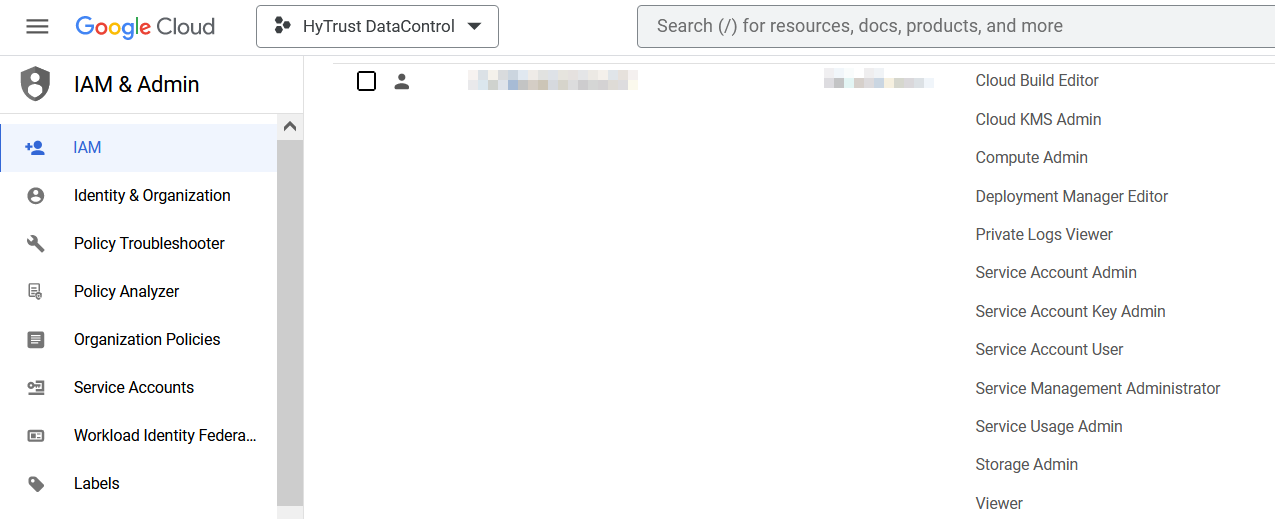
Required GCP permissions
The GCP account performing this integration had the following permissions. These were granted by the project admin. Not all these permissions are required to perform this integration.
-
Cloud Build Editor
-
Cloud KMS Admin
-
Compute Admin
-
Deployment Manager Editor
-
Private Logs Viewer
-
Service Account Admin
-
Service Account Key Admin
-
Service Account User
-
Service Management Administrator
-
Service Usage Admin
-
Storage Admin
-
Viewer
Create a service account in GCP
A service account needs to be created in a GCP IAM. This service account will be used by Entrust KeyControl to access the GCP key rings. Once created, this service account needs permissions that have to be granted by the project admin.
-
Open a browser and sign in to the GCP portal https://console.cloud.google.com.
-
Select IAM & Admin on the Welcome screen, or navigate to Cloud overview > Dashboard.
-
Select Service Accounts in the left-hand pane, or enter
IAM & Adminin the Search box and then select IAM & Admin from the pull-down menu that appears. -
Select CREATE SERVICE ACCOUNT in the right-hand pane.
-
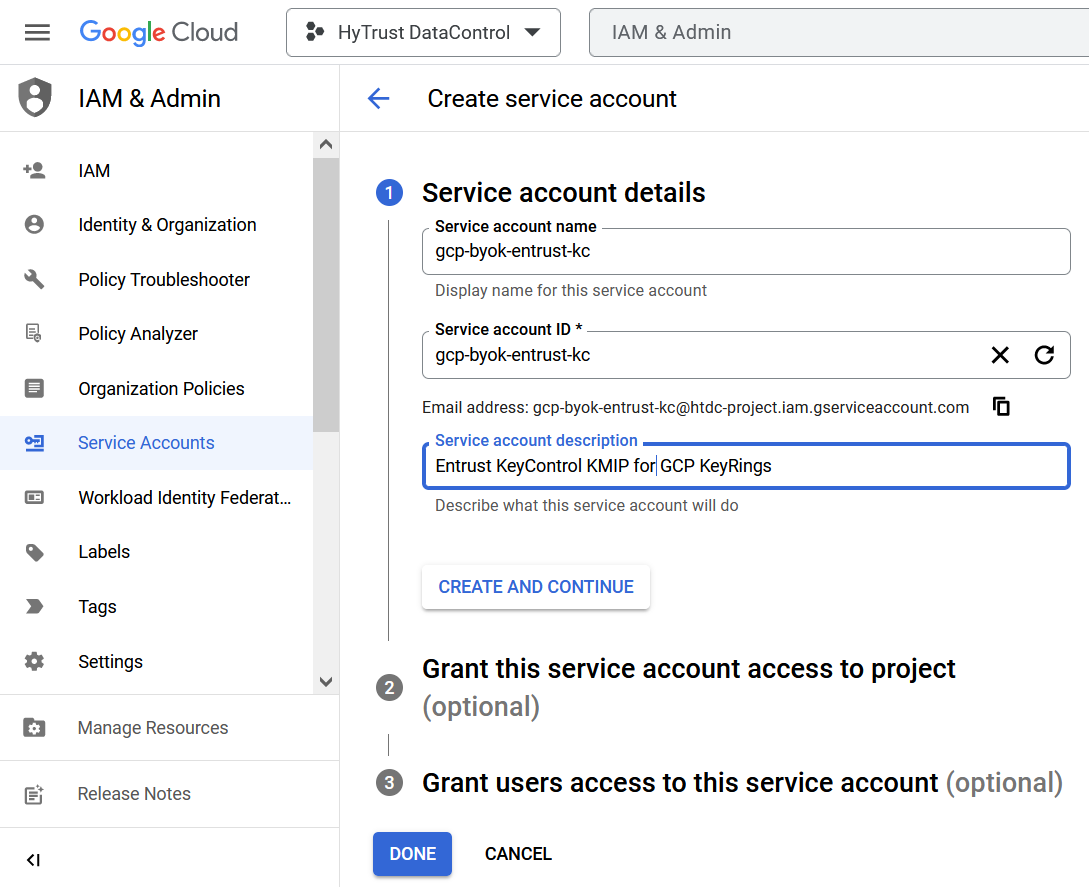
Enter the Service account details and then select DONE.
For example:
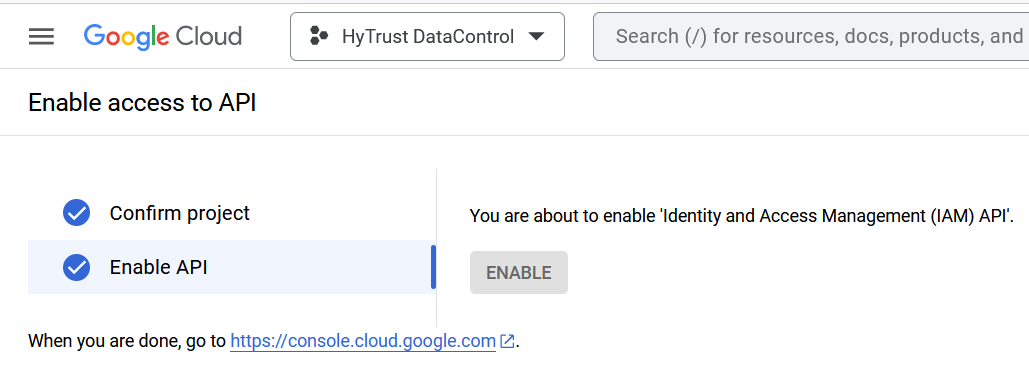
Yourself or the project administrator may need to enable access to APIs. Once enabled, the screen appears as follows. For example:
-
Select Service Accounts > Service accounts and then select the service account you just created.
-
Select the DETAILS tab. Take note of the Unique ID.
For example:
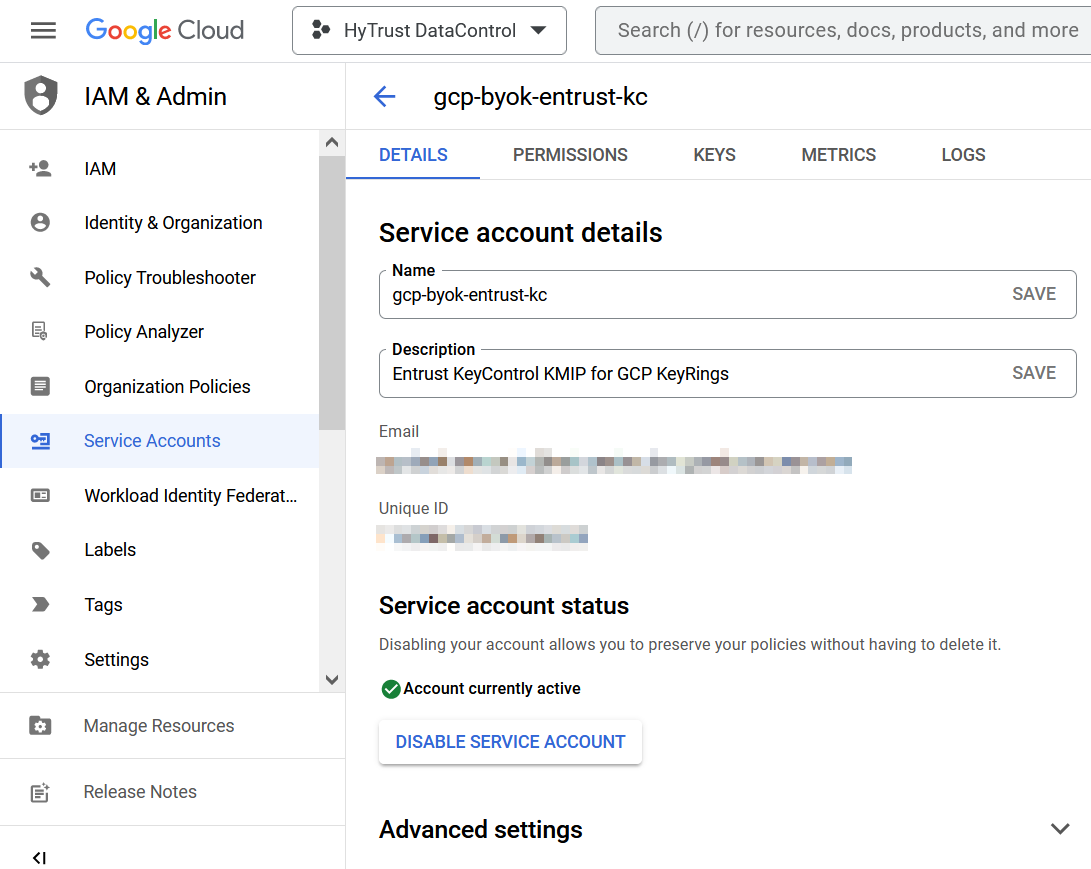
-
The following permissions were given to this service account by the system admin after it was created:
-
Browser
-
Cloud KMS Admin
-
Service Account Key Admin
For example:
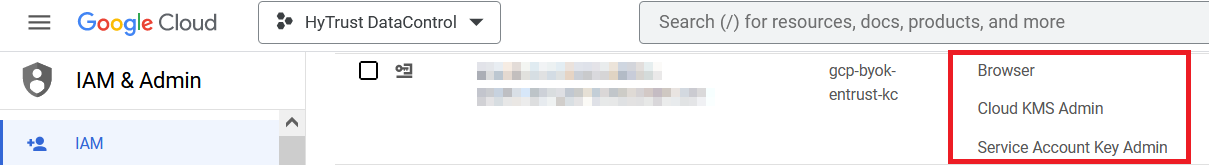
-
Create a key for the service account
A key needs to be created for the service account created in Create a service account in GCP. This key will be used by Entrust KeyControl to access the GCP service account.
-
Open a browser and sign in to the GCP portal: https://console.cloud.google.com.
-
Select IAM & Admin on the Welcome screen, or navigate to Cloud overview > Dashboard.
-
Select Service Accounts in the left-hand pane, or type
IAM & Adminin the Search box and then select IAM & Admin from the pull-down menu that appears. -
Select the service account created in Create a service account in GCP from the list in the right-hand pane.
-
Select the KEYS tab.
-
Select ADD KEY and then select Create new key.
-
Select JSON from the available Key type options.
For example:
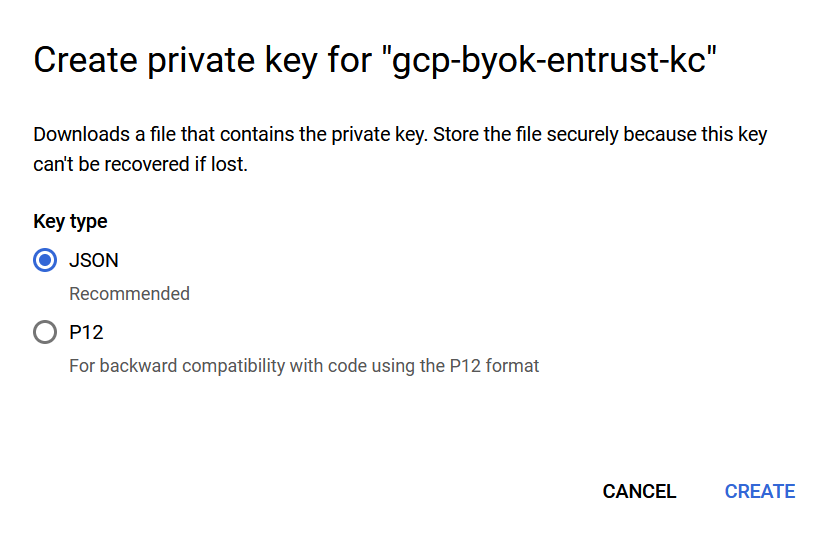
-
Select CREATE. A pop-up message appears indicating that the key created was downloaded to your computer.
For example:
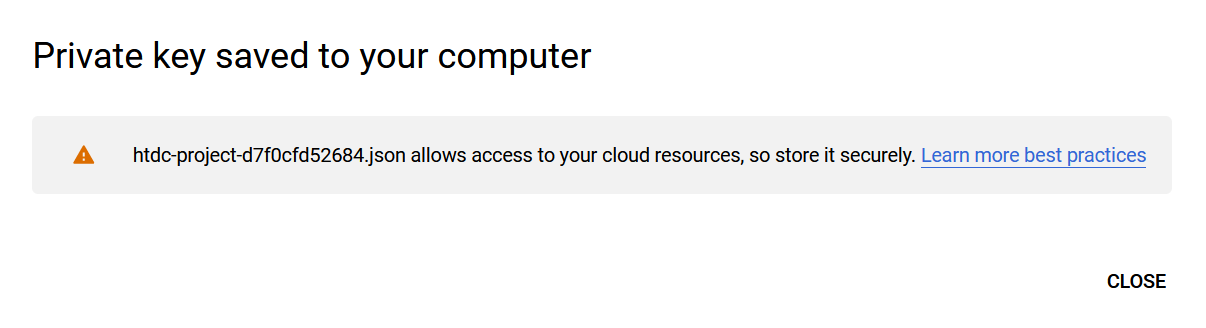
-
Verify by checking your
Downloadsfolder.For example:
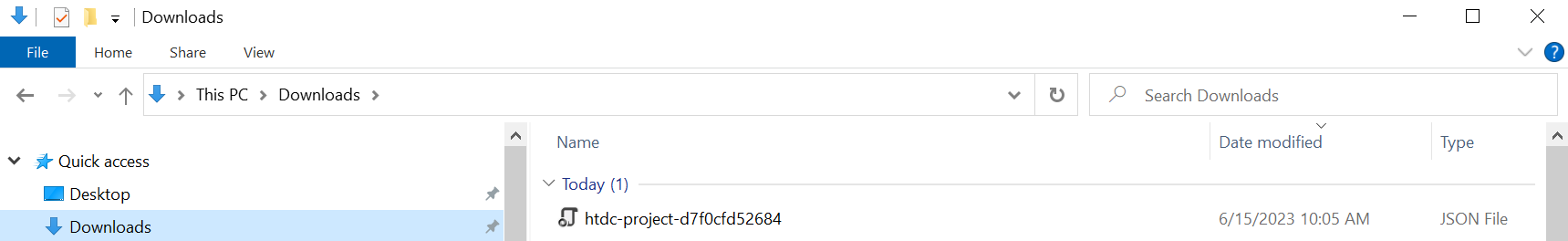
-
Take note of the new key in the GCP console.
For example:
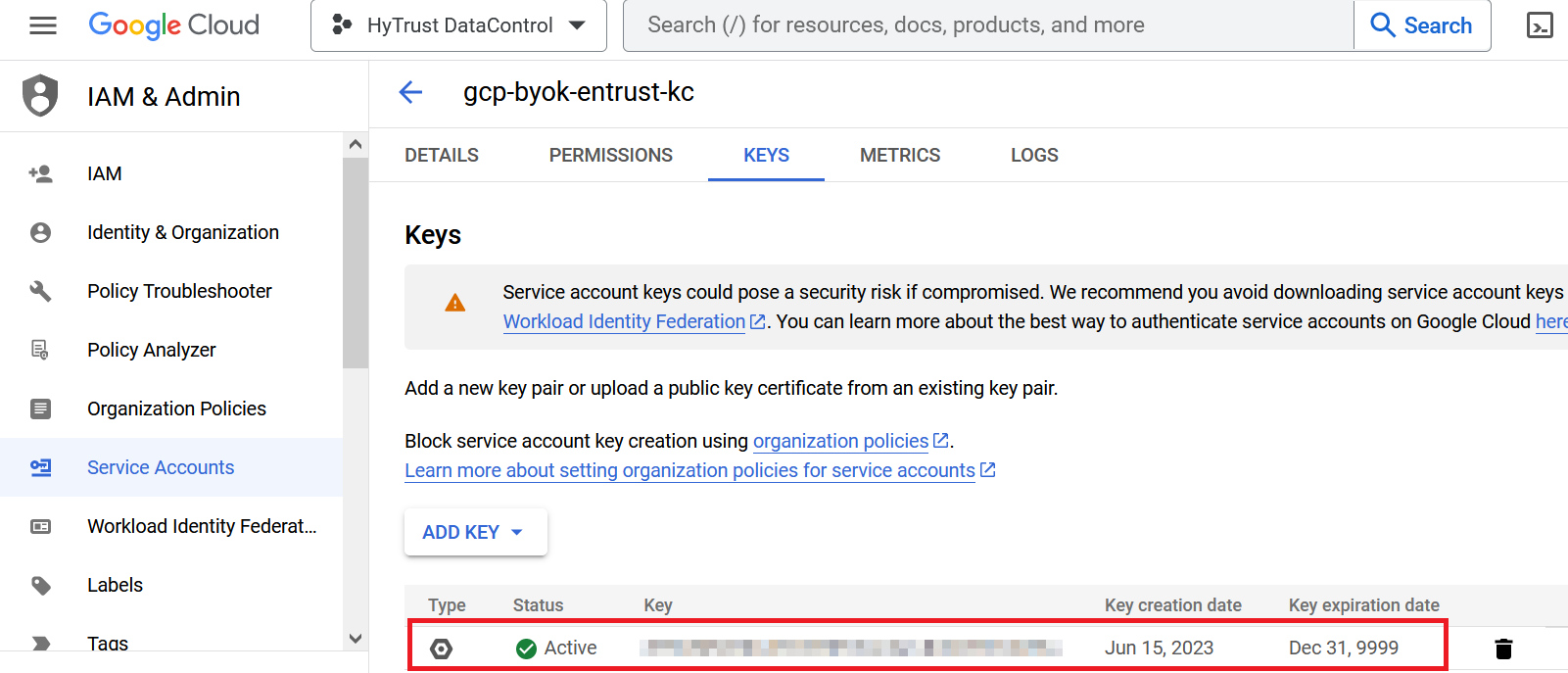
Create a GCP key ring
This key ring will be used to store keys managed by Entrust KeyControl. A new GCP key ring was created for this integration to show the entire process. You can use an existing key ring instead.
If using an existing GCP key ring, proceed to section [create-keycontrol-csp-account] directly, skipping this section entirely.
-
Open a browser and sign in to the GCP portal: https://console.cloud.google.com.
-
In the navigation menu select Security > Key Management.
-
In the KEY RINGS tab in the left-hand pane, select + CREATE KEY RING.
-
Enter the Key ring name and select the Location type.
For example:
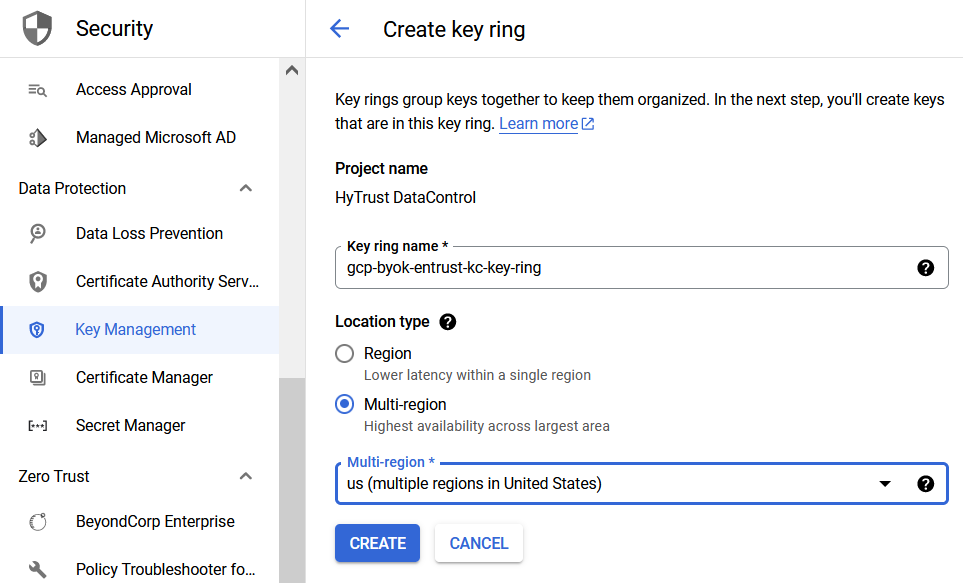
-
Select CREATE to create the key ring
-
Select CANCEL in the Create key pane.
-
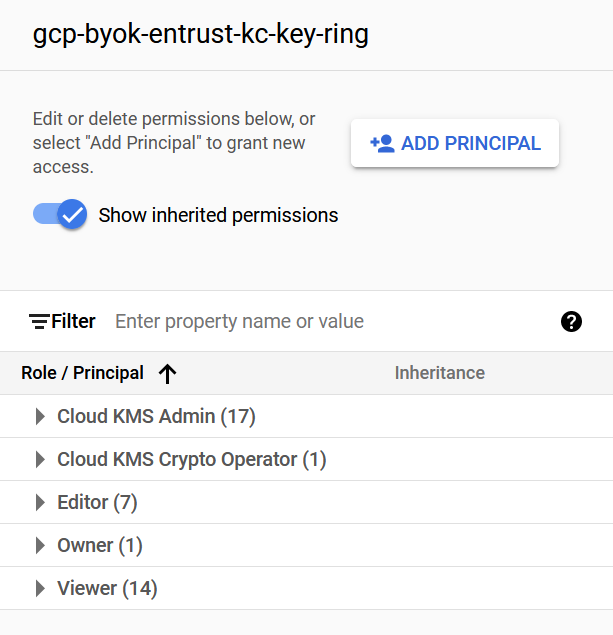
Verify your key ring has the following inherited permissions. Navigate to Security > Key Management. Select the newly created key ring. The permissions are in the right-hand pane.
For example: