Integrate Scality RING and KeyControl
Create the client certificate in KeyControl
-
Sign in to the KMIP vault URL created in Create a KMIP Vault in the KeyControl.
-
Select the Client Certificates tab.
-
Select the + icon to create a client certificate. Enter your information. Then select Create.
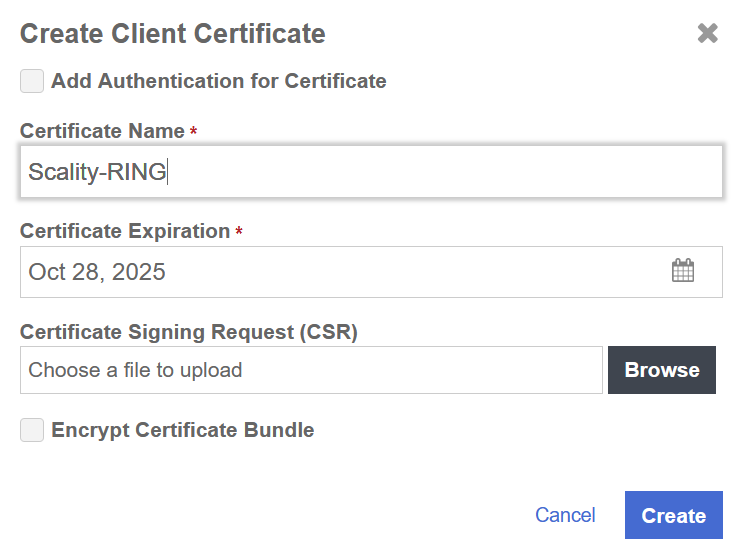
-
Notice the new client certificate.
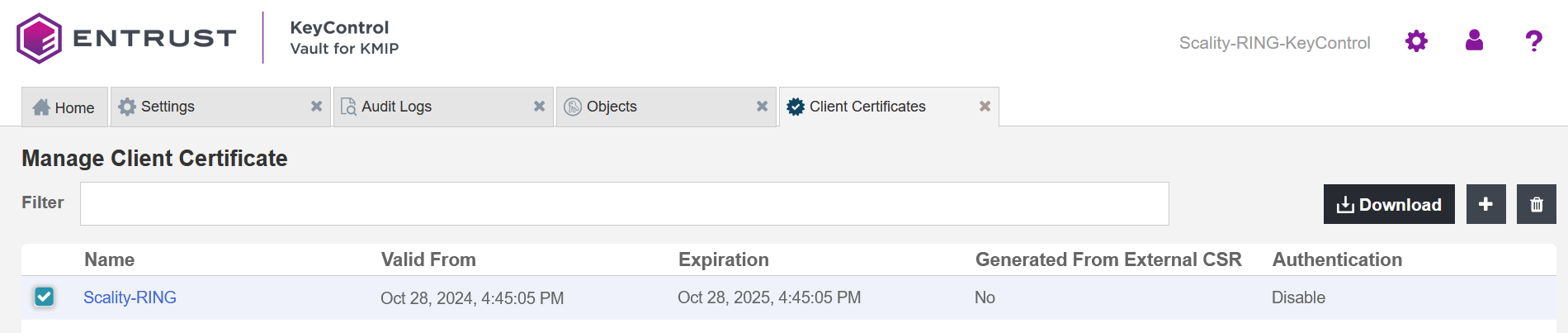
-
Select the certificate. Then select Download and save it for later use.
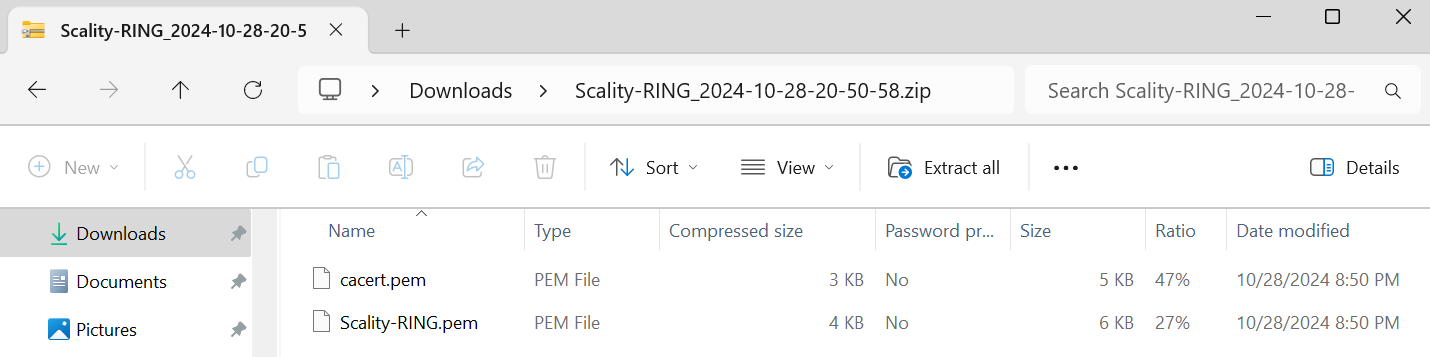
For more information, see Managing KMIP Client Certificates.
Configure the Scality RING for KMIP
-
In the supervisor VM, login (SSH) as root. The password is listed in the document titled "Scality OVA 9.3.0.2 Deployment guide - 3-server RING - 4TB.pdf".
-
Go to the federation folder.
cd /srv/scality/s3/s3-offline/federation -
Set the
ENV_DIRenvironment variable pointing to the folder containing the cluster’s configuration, a directory namedenv/.ENV_DIR=s3config -
Create the
kmip/configuration directory.mkdir env/$\{ENV_DIR}/kmip -
Upload the certificates and key files created in Create the client certificate in KeyControl to
env/${ENV_DIR}/kmip. We used the WinSCP app to upload the two files.[root@scality-supervisor-01 federation]# ls -al /srv/scality/s3/s3-offline/federation/env/s3config/kmip total 20 drwxr-xr-x 2 root root 48 Oct 29 08:36 . drwxr-xr-x 10 root root 4096 Oct 29 08:27 .. -rw-r--r-- 1 root root 4710 Oct 29 08:29 cacert.pem -rw-r--r-- 1 root root 5195 Oct 29 08:29 Scality-RING.pem -
Cat file
/srv/scality/s3/s3-offline/federation/env/s3config/kmip/Scality-RING.pem. Copy the private key section to the clipboard:-----BEGIN PRIVATE KEY----- MIIJQgIBAD... ... -----END PRIVATE KEY----- -
Create file
/srv/scality/s3/s3-offline/federation/env/s3config/kmip/client.key. Edit this new file and paste the content of the clipboard. -
Cat file
/srv/scality/s3/s3-offline/federation/env/s3config/kmip/Scality-RING.pem. Copy the certificate section to the clipboard:-----BEGIN CERTIFICATE----- MIIEaTCCA1... ... -----END CERTIFICATE----- -
Create file
/srv/scality/s3/s3-offline/federation/env/s3config/kmip/client.cert. Edit this new file and paste the content of the clipboard. Notice the files created.[root@scality-supervisor-01 kmip]# ls -al /srv/scality/s3/s3-offline/federation/env/s3config/kmip total 28 drwxr-xr-x 2 root root 85 Oct 29 11:39 . drwxr-xr-x 10 root root 4096 Oct 29 08:27 .. -rw-r--r-- 1 root root 4710 Oct 29 08:29 cacert.pem -rw-r--r-- 1 root root 1590 Oct 29 11:39 client.cert -rw-r--r-- 1 root root 3272 Oct 29 11:39 client.key -rw-r--r-- 1 root root 5195 Oct 29 08:29 Scality-RING.pem -
Edit the
env/${ENV_DIR}/group_vars/allfile. Uncomment theenv_s3.kmippart of the configuration. Replace the various parameters with yours as described in document titled "Setting Up Server-Side Bucket Encryption — S3 Connector 9.3.0 documentation.pdf".cat /srv/scality/s3/s3-offline/federation/env/s3config/group_vars/all ... kmip: port: 5696 host: 10.194.148.206 compoundCreate: true bucketAttributeName: x-entrust-kmip-bucket pipelineDepth: 8 key: client.key cert: client.cert ca: - cacert.pem ...
Notice the x- inserted in front of the bucket name defined in section Deploy the Scality RING.
For further information, refer to document titled "Setting Up Server-Side Bucket Encryption — S3 Connector 9.3.0 documentation.pdf".
Post installation re-configure procedure
-
In the supervisor VM, login (SSH) as root. The password is listed in the document titled "Scality OVA 9.3.0.2 Deployment guide - 3-server RING - 4TB.pdf".
-
Go to the federation folder.
cd /srv/scality/s3/s3-offline/federation -
Set the
ENV_DIRenvironment variable pointing to the folder containing the cluster’s configuration, a directory namedenv/.ENV_DIR=s3config -
List the stateless hosts.
[root@scality-supervisor-01 federation]# ansible -i env/$\{ENV_DIR}/inventory --list-hosts runners_s3 [DEPRECATION WARNING]: DEFAULT_GATHER_SUBSET option, the module_defaults keyword is a more generic version and can apply to all calls to the M(ansible.builtin.gather_facts) or M(ansible.builtin.setup) actions, use module_defaults instead. This feature will be removed from ansible-core in version 2.18. Deprecation warnings can be disabled by setting deprecation_warnings=False in ansible.cfg. hosts (3): md1-cluster1 md2-cluster1 md3-cluster1 -
For each listed host, reconfigure s3. If the host is behind a load balancer, deactivate the server before re‐configuring it.
cd /srv/scality/s3/s3-offline/federation [root@scality-supervisor-01 federation]# ansible-playbook -i env/$\{ENV_DIR}/inventory run.yml --skip-tags requirements -t s3 > logfile cat /srv/scality/s3/s3-offline/federation/logfile SCALITY S3 CONNECTOR INSTALLER ************************************************* PLAY [all] ********************************************************************* TASK [Gathering Facts ] ******************************************************** ok: [10.15.20.102(md5-cluster1)] ok: [10.15.20.101(md1-cluster1)] ok: [10.15.20.101(md4-cluster1)] ok: [10.15.20.102(md2-cluster1)] ok: [10.15.20.103(md3-cluster1)] ... PLAY RECAP ********************************************************************* md1-cluster1 : ok=172 changed=10 unreachable=0 failed=0 md2-cluster1 : ok=124 changed=8 unreachable=0 failed=0 md3-cluster1 : ok=124 changed=8 unreachable=0 failed=0 md4-cluster1 : ok=69 changed=0 unreachable=0 failed=0 md5-cluster1 : ok=69 changed=0 unreachable=0 failed=0 If something went wrong (failed tasks), please contact Scality support and attach ./ansible.log