Integrate a new IIS deployment with the nShield HSM
This section describes how to integrate a new IIS server installation with an nShield HSM.
Create a certificate request
IIS Manager does not support the creation of certificate requests protected by CNG Keys. These must be created using the Microsoft command line utilities on Windows PowerShell.
-
Verify the nCipher Primitive Provider and nCipher Security World Key Storage Provider are available. Otherwise, see section Install and register the CNG provider.
>cnglist.exe --list-providers Microsoft Key Protection Provider Microsoft Passport Key Storage Provider Microsoft Platform Crypto Provider Microsoft Primitive Provider Microsoft Smart Card Key Storage Provider Microsoft Software Key Storage Provider Microsoft SSL Protocol Provider Windows Client Key Protection Provider nCipher Primitive Provider nCipher Security World Key Storage Provider -
Create a
request.inffile for an SSL certificate linked to a 2048 RSA key protected by the HSM. Notice the ProvideName set to nCipher Security World Key Storage Provider.For example:
[Version] Signature= "$Windows NT$" [NewRequest] Subject = "CN=interop.local,C=US,ST=Florida,L=Sunrise,O=InteropLocal,OU=WebServer" HashAlgorithm = SHA256 KeyAlgorithm = RSA KeyLength = 2048 ProviderName = "nCipher Security World Key Storage Provider" KeyUsage = 0xf0 MachineKeySet = True [EnhancedKeyUsageExtension] OID = 1.3.6.1.5.5.7.3.1
-
Run the following command to create the certificate request.
> certreq.exe -new request.inf IISCertRequest.csr -
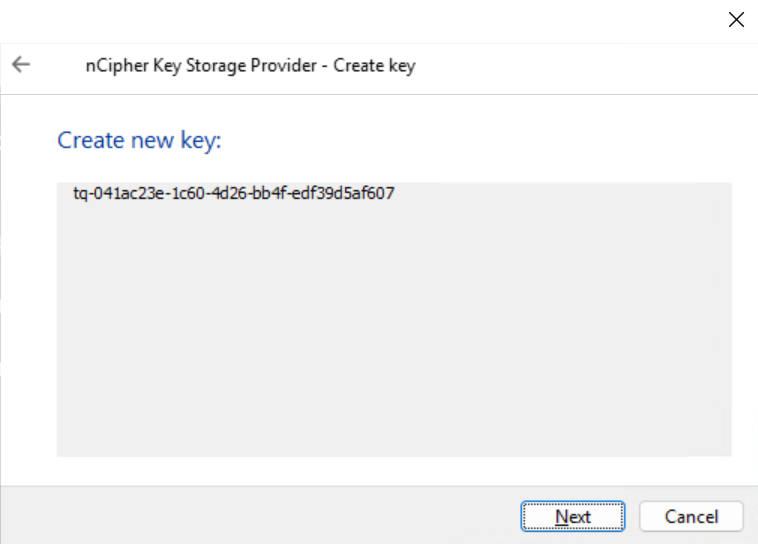
In the nCipher Key Storage Provider - Create Key pop-up window, select Next.
-
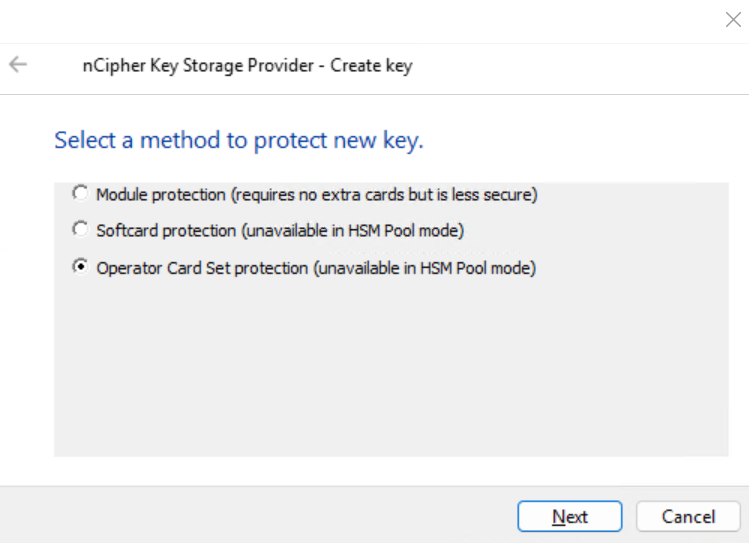
Select Operator Card Set protection. Then select Next.
-
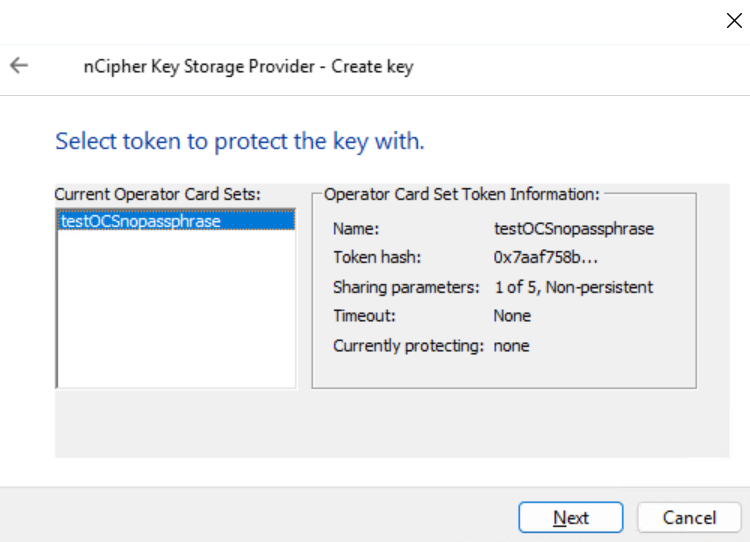
Chose the OCS. Then select Next.
-
Chose the HSM. Then select Finish.
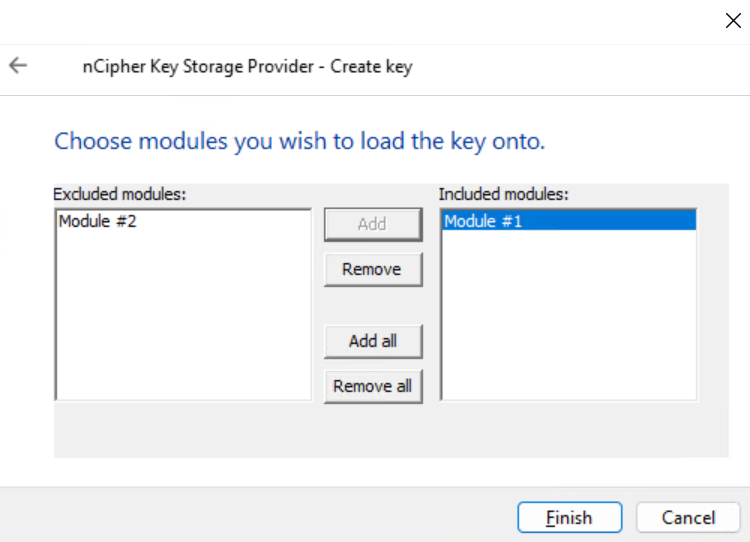
-
Present the OCS to the HSM.
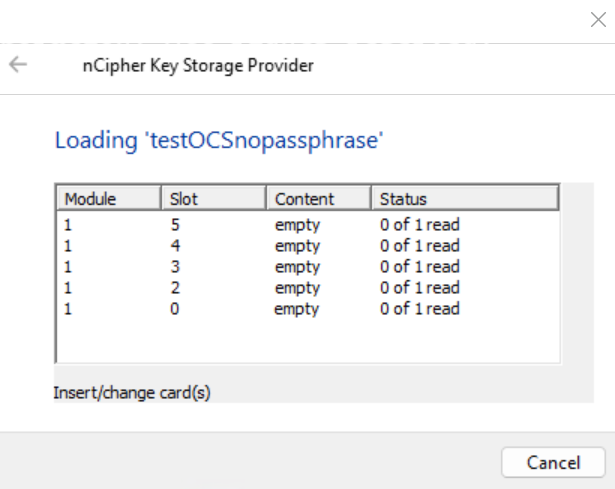
-
In the Card reading complete. window, select Finish.
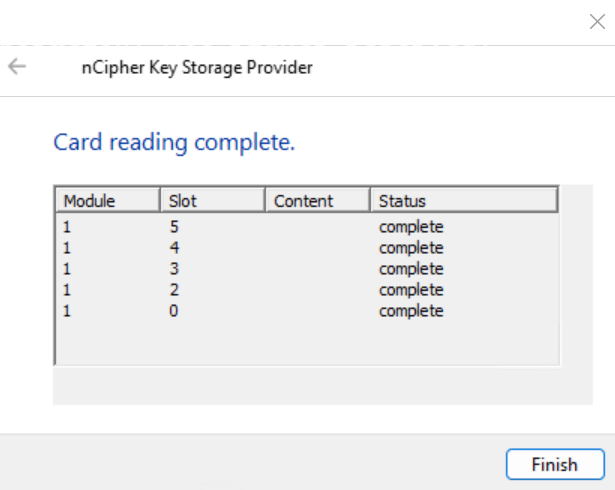
-
Notice the command completed in the CLI.
>certreq.exe -new request.inf IISCertRequest.csr CertReq: Request Created -
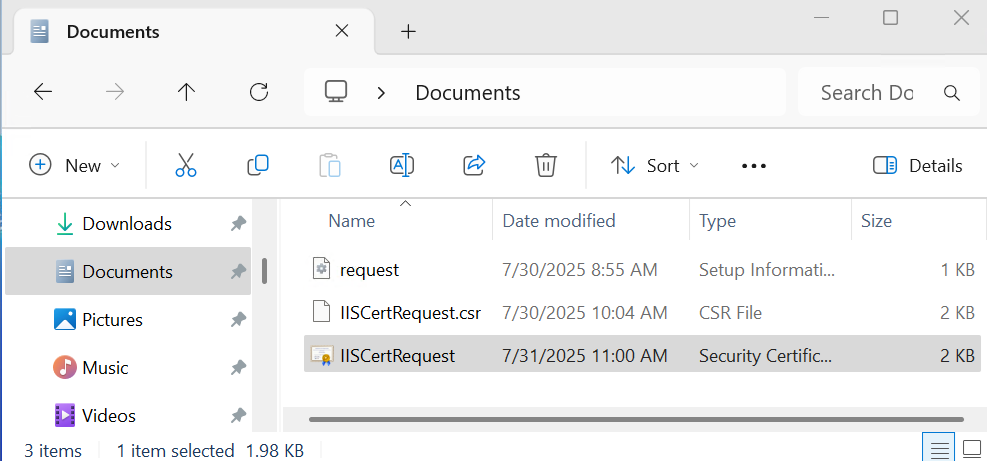
Notice the
csrfile created.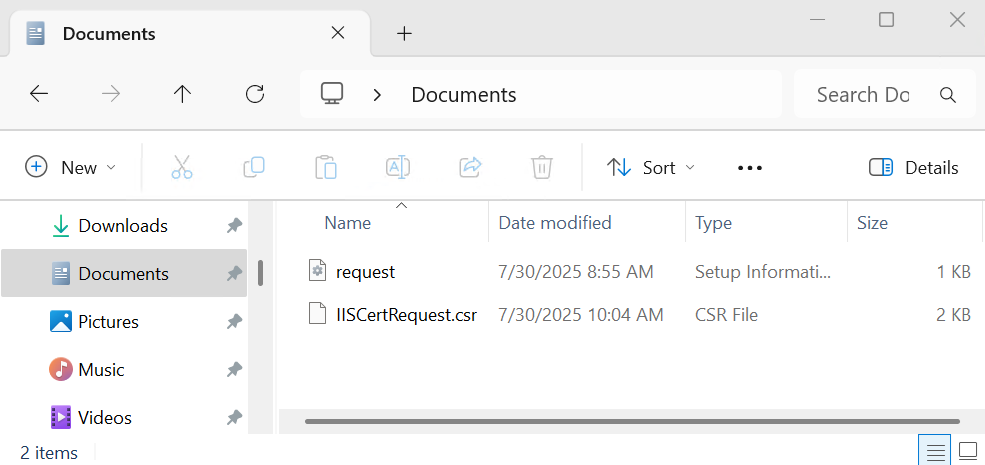
Sign the certificate request
Submit the CSR file for signature to your organization’s CA.
For this integration a local two-tier PKI infrastructure was used for signing.
The signed certificate file is IISCertRequest.cer.
Install the certificate
Open a command window and run the following to make the signed certificate available for use in IIS.
>certreq -accept IISCertRequest.cer
Installed Certificate:
Serial Number: 39000000171fd041e27d84cc65000000000017
Subject: CN=interop.local, OU=WebServer, O=InteropLocal, L=Sunrise, S=Florida, C=US
NotBefore: 7/31/2025 10:46 AM
NotAfter: 7/31/2027 10:46 AM
Thumbprint: bc504bb69b98ec801d8907b47d0a82b80f6dcd92Bind the certificate to the IIS server
-
Go to Start > Internet Information Service Manager.
-
Select the hostname, then double-click Server Certificates and verify the certificate you accepted in the previous step is listed.
-
Under Sites on the left-hand side of the IIS Manager screen, select Default website.
-
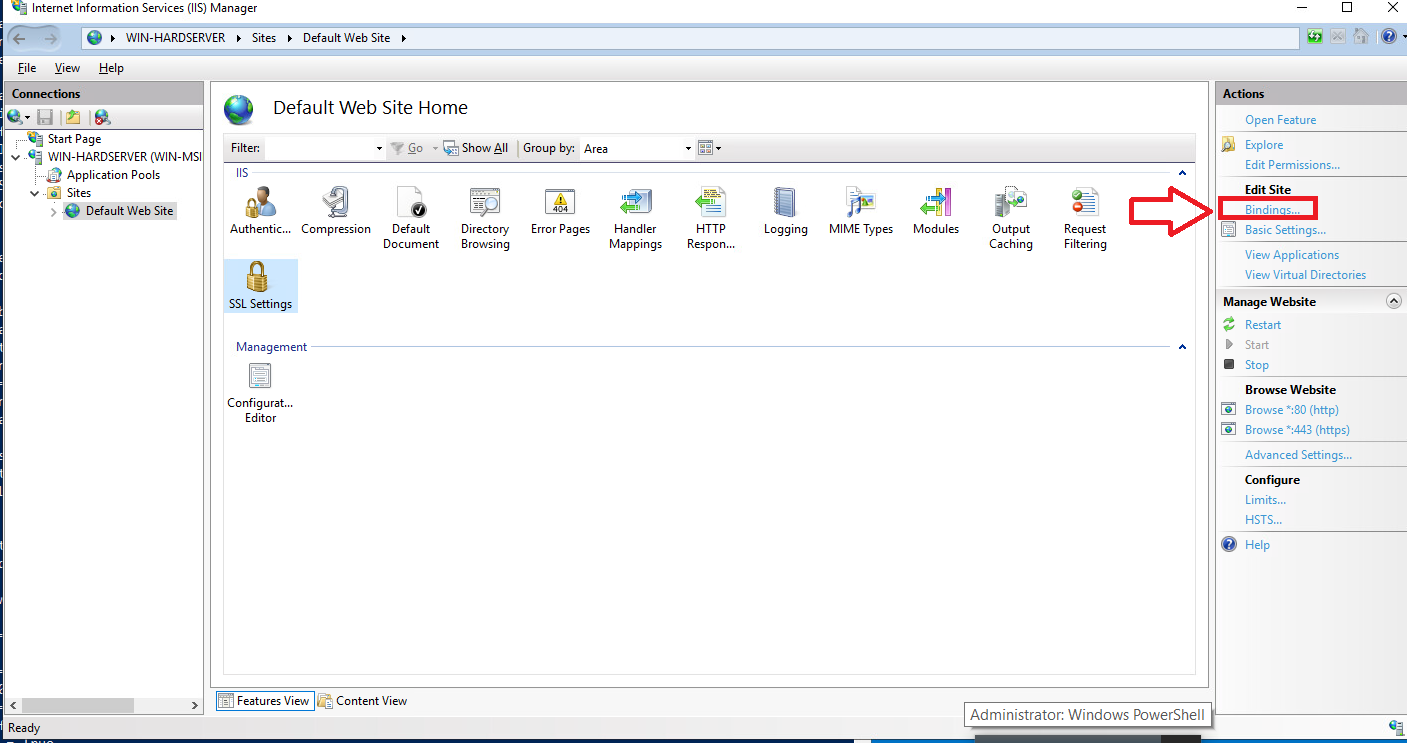
Select Bindings link on the right-hand side of the IIS Manager.
-
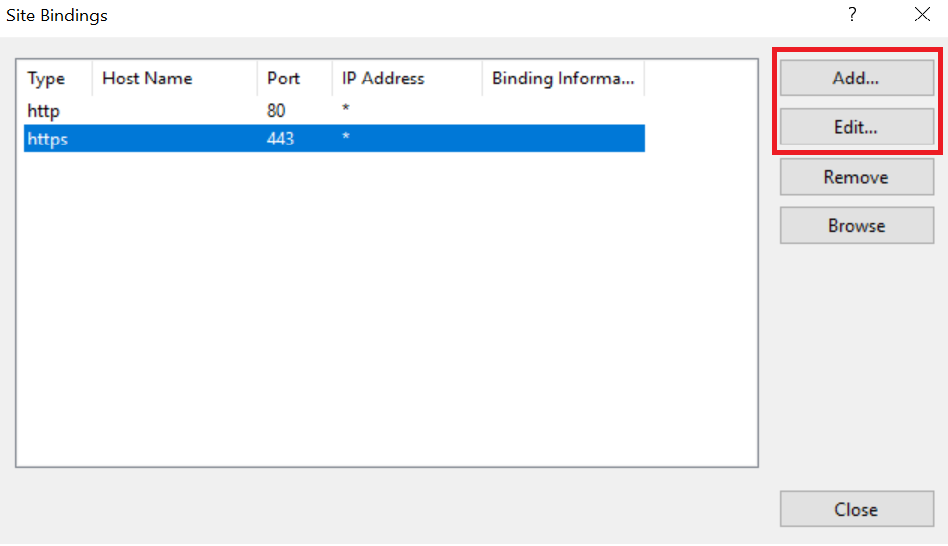
In the Site Bindings window, if the https protocol is not listed add it now. To do this, select Add, set the protocol as https and select the required certificate from the list.
-
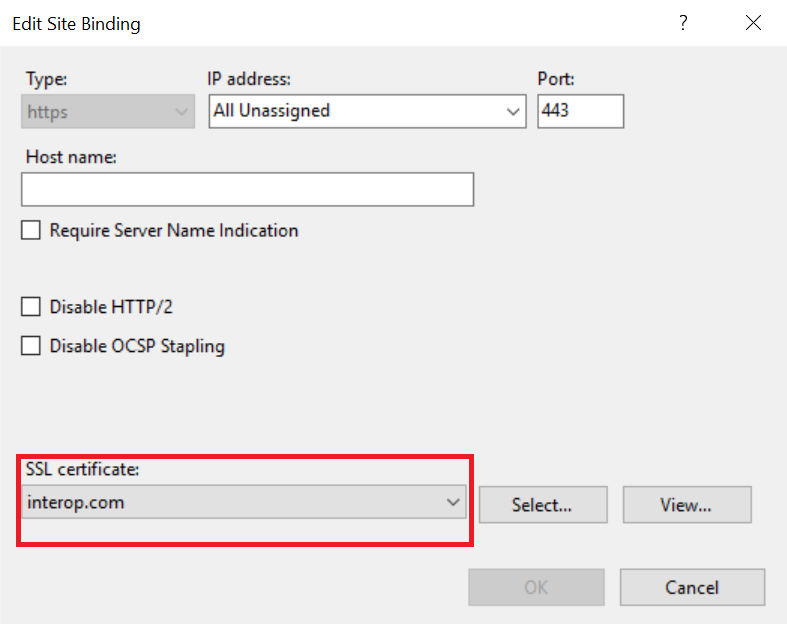
Select the https protocol, select Edit, and then select the certificate from the list:
-
Select OK to complete the certificate binding for SSL connection.
-
Select Close on the Site Bindings screen.
-
Restart the IIS server.