Integrate Entrust KeyControl with HPE Alletra 9000
Follow these steps to register Entrust KeyControl as a KMS in HPE Alletra 9000.
Create the HPE Alletra certificate request
-
Sign in to the Alletra 9060 webGUI using an account with Security Admin privileges.
-
Select Settings in the toolbar. Then select Array certificates.
-
Select the + icon to add a certificate.
-
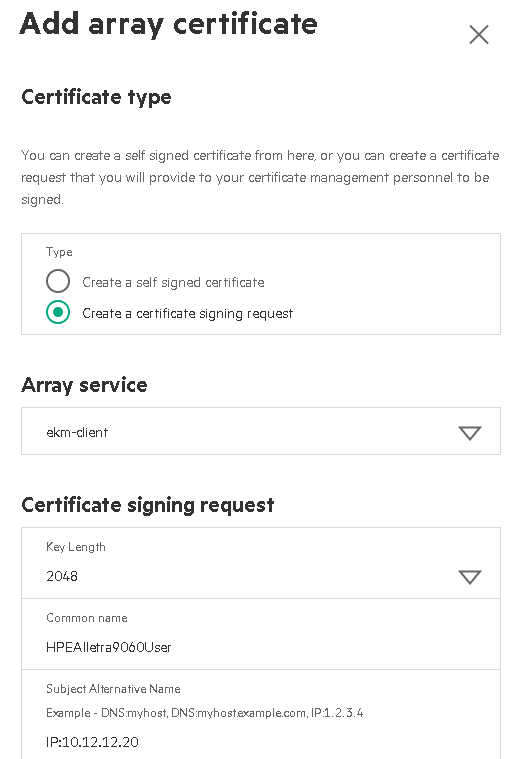
Select Create a certificate signing request for the Certificate type.
-
Select ekm-client for Array service and enter the Common name and other information. Then confirm the checkbox to proceed and select Add.
-
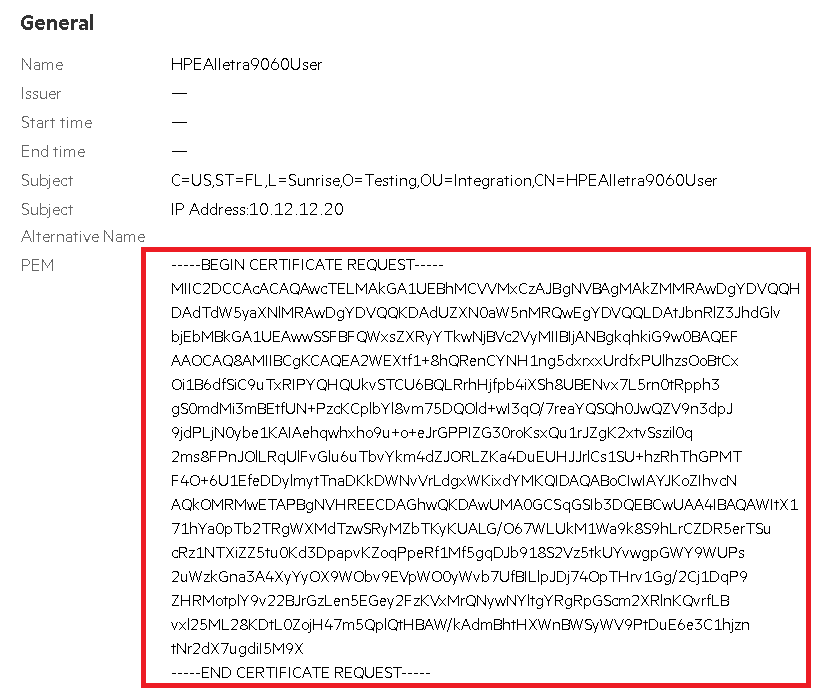
Select the certificate created.
-
Copy the PEM in the newly created certificate window.
-
Create a
csrfile type with a text editor containing the copied certificate request. May need to rename the file using the Windows CLI to get the correct file type extension if using Notepad text editor.
Create the client certificate bundle
-
Sign in to the KMIP Vault with the URL and credentials from deploy-entrust-kc.adoc#create-kmip-vault.
-
Select Security, then Client Certificates.

-
In the Manage Client Certificate page, select the + icon on the right to create a new certificate. The Create Client Certificate dialog box appears.
-
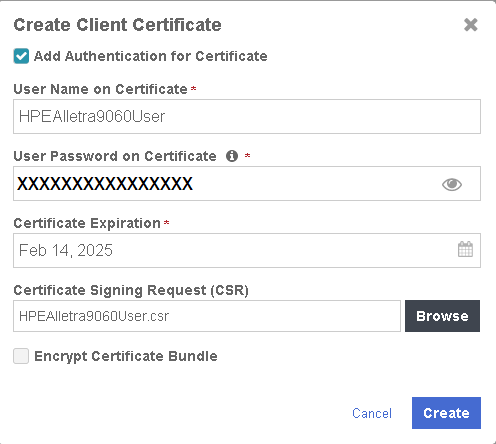
In the Create Client Certificate dialog box:
-
Check Add Authentication for Certificate.
-
Enter the User Name on Certificate.
-
Enter the User Password on Certificate.
-
Enter the Certificate Expiration.
-
Upload the certificate request created in Create the HPE Alletra certificate request.
-
Select Create.
For example:
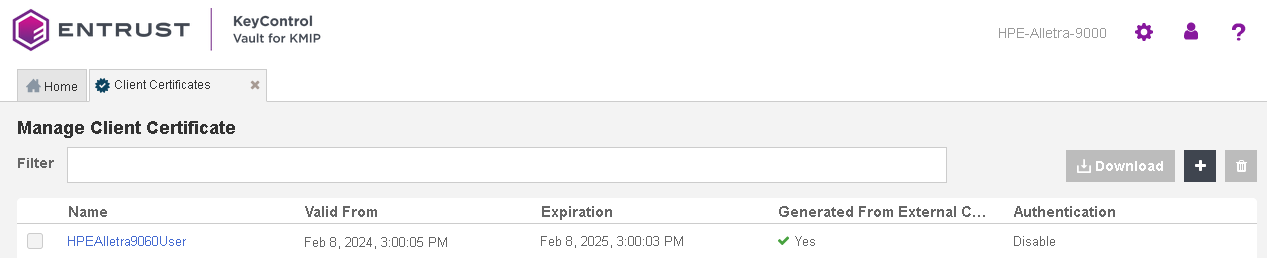
The new certificates are added to the Manage Client Certificate pane.
-
-
Select the certificate and select the Download icon to download the certificate.
-
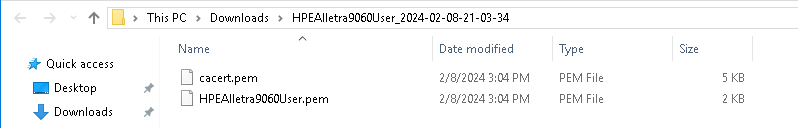
Unzip the downloaded file. It contains the following:
-
A
certname.pemfile that includes both the client certificate and private key. In this example, this file is calledHPEAlletra9060User.pem.The client certificate section of the
certname.pemfile includes the lines “-----BEGIN CERTIFICATE-----" and “-----END CERTIFICATE-----" and all text between them.The private key section of the
certname.pemfile includes the lines “-----BEGIN PRIVATE KEY-----" and “-----END PRIVATE KEY-----" and all text in between them. -
A
cacert.pemfile which is the root certificate for the KMS cluster. It is always namedcacert.pem.
-
See the following link for additional information Managing KMIP Tenant Client Certificates.
Import client certificate into Alletra
-
Sign in to the Alletra 9060 webGUI using an account with Security Admin privileges.
-
Select Settings in the toolbar. Then select Array certificates.
-
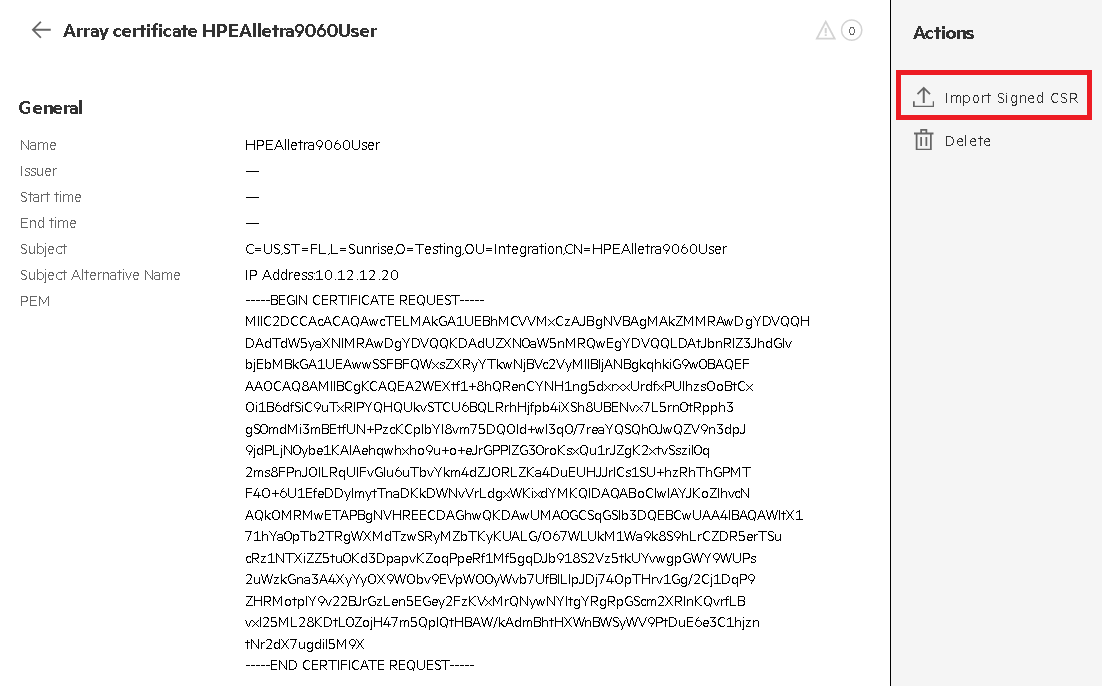
Select the certificate that was created in Create the HPE Alletra certificate request. Then select Import Signed CSR in the Actions tab.
-
Paste the content of the extracted
cacert.pemfile from Create the client certificate bundle in the Authority chain text box. When pasting the content, only include the certificate section of the file starting from -----BEGIN CERTIFICATE----- and ending with -----END CERTIFICATE-----. -
Paste the content of the extracted
HPEAlletra9060User.pemfile from Create the client certificate bundle in the Certificate text box. Only paste the certificate section starting from -----BEGIN CERTIFICATE----- and ending with -----END CERTIFICATE-----. Then select Add.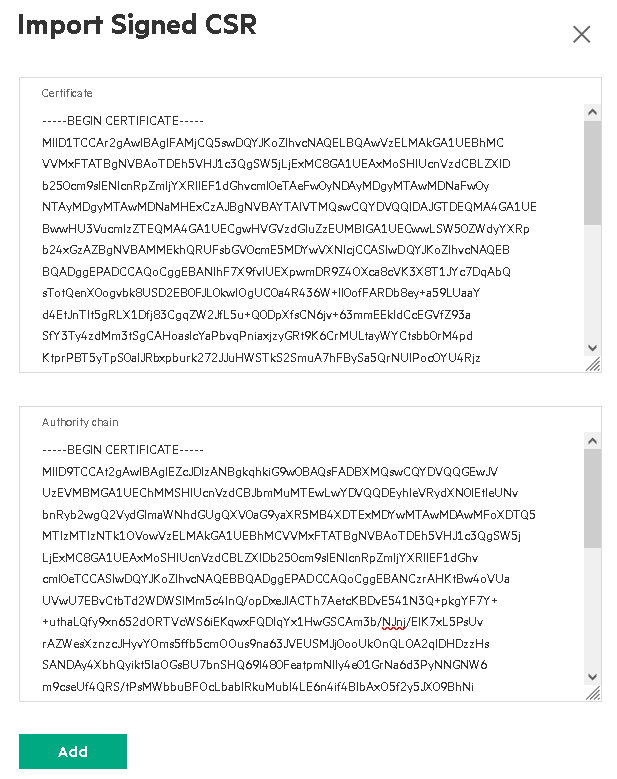
-
Check I have read and understand the implications. Then select Add.
-
Notice the new status of the Certificate along with the Root Certificate now showing up beside our created certificate.
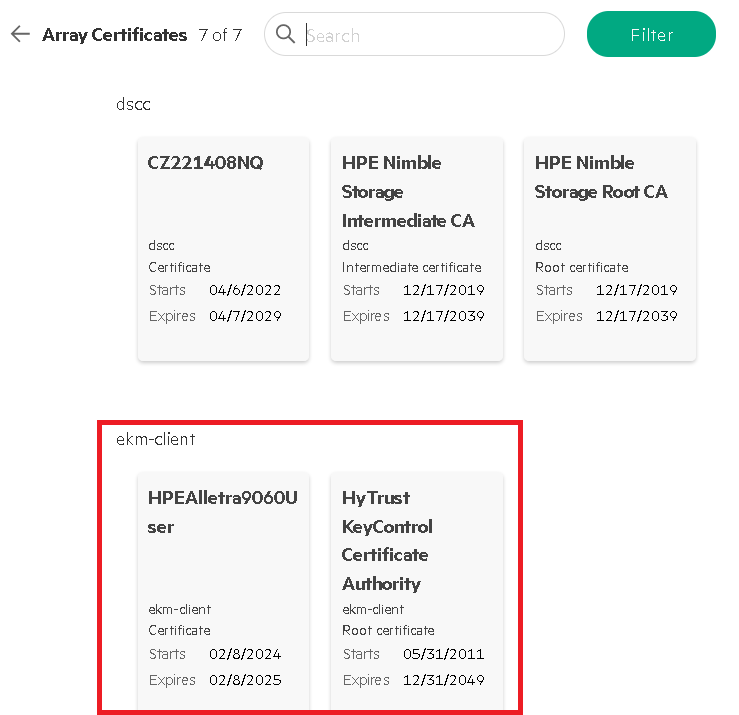
-
Launch the Alletra 9060 CLI using an account with Security Admin privileges.
Microsoft Windows [Version 10.0.17763.5329] (c) 2018 Microsoft Corporation. All rights reserved. C:\Users\Administrator>ssh 3paradm@10.12.12.20 The authenticity of host '10.12.12.20 (10.12.12.20)' can't be established. RSA key fingerprint is SHA256:e1K15j9xCCcQyuMTV4hOcCIW25boA9jypH1tJzAbB5I. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.12.12.20' (RSA) to the list of known hosts. 3paradm@10.12.12.20's password: TAC1-Alletra-9060 cli% -
Verify that the certificates were created with the
showcertcommand.TAC1-Alletra-9060 cli% showcert Service Commonname Type Enddate Fingerprint ekm-client HPEAlletra9060User cert Feb 8 21:00:03 2025 GMT 88b2042086346406396f6a347172aa1e52ba54ac ekm-client* HyTrust KeyControl Certificate Authority rootca Dec 31 23:59:59 2049 GMT ed1e2e09efe0ef77c7546afa8b58adcba2575222 ekm-server* HyTrust KeyControl Certificate Authority rootca Dec 31 23:59:59 2049 GMT ed1e2e09efe0ef77c7546afa8b58adcba2575222
Register the Entrust KeyControl KMS
-
Launch the Alletra 9060 CLI using an account with Security Admin privileges.
Microsoft Windows [Version 10.0.17763.5329] (c) 2018 Microsoft Corporation. All rights reserved. C:\Users\Administrator>ssh 3paradm@10.12.12.20 The authenticity of host '10.12.12.20 (10.12.12.20)' can't be established. RSA key fingerprint is SHA256:e1K15j9xCCcQyuMTV4hOcCIW25boA9jypH1tJzAbB5I. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.12.12.20' (RSA) to the list of known hosts. 3paradm@10.12.12.20's password: TAC1-Alletra-9060 cli% -
Create an External Key Manager Server with the
controlencryption setekmcommand in the CLI.Notice the IP of all the nodes in the Entrust KeyControl cluster. TAC1-Alletra-9060 cli% controlencryption setekm -setserver 10.12.12.200,10.12.12.201 -port 5696 -ekmuser HPEAlletra9060User -kmipprotocols 1.3 Password for EKM user: -
Verify that the external key manager has been created with the
controlencryption status -dcommand.TAC1-Alletra-9060 cli% controlencryption status -d Licensed Enabled BackupSaved State SeqNum Keystore FIPS non-SEDs FailedDisks nodeNonSED yes no no normal 0 --- --- 0 0 0 Number of EKM servers defined: 1 EKM servers: EntrustKeyControl.tac1.net EKM server port: 5696 EKM username: HPEAlletra9060User KMIP Protocols: 1.3 -
Verify communication with the newly created External Key Management server with the
controlencryption checkekmcommand to show that EKM settings are correct.TAC1-Alletra-9060 cli% controlencryption checkekm EKM settings are correct.