Integrate Delinea Secret Server with an Entrust nShield HSM
There are two cryptography API options for this integration: the CNG cryptography provider, and the PKCS #11. Both are covered in this section.
Configure the Delinea Secret Server using the CNG cryptography provider
-
Select Windows Start > Entrust nShield Security World > CNG configuration wizard. The nShield CNG Providers Configuration Wizard appears.
-
Select Next twice.
-
Select Use the existing security world if one was created in deploy-entrust-nshield.adoc#install-security-world-hsm.
-
Select Next twice.
-
Select the protection method. If you are using OCS protection, insert your OCS card into the proper slot.
Example for OCS protection:
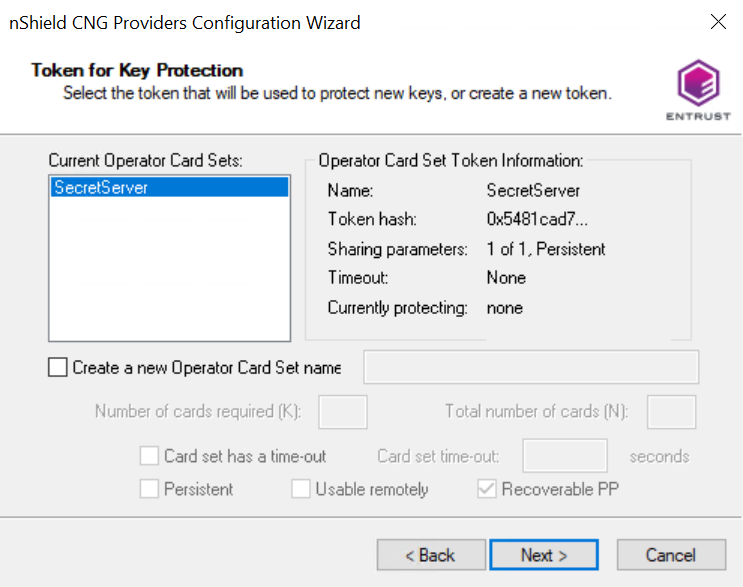
-
Run
certutil -csptest > <filename>on a command window.For example:
C:\Users\Administrator.INTEROP>certutil -csptest > Documents\cryptographic-providers -
Search for Provider Name: nCipher in the file created above, and make sure that it shows Pass.
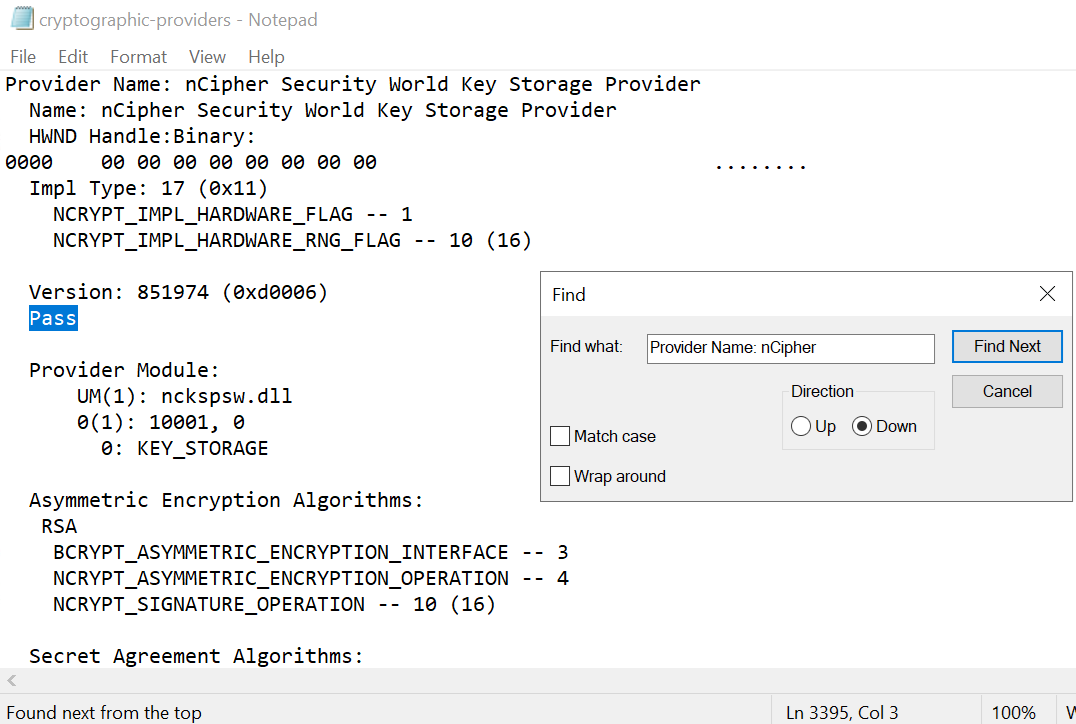
-
Log in to the Delinea Secret Server via a browser at https://localhost/SecretServer.
-
From the menu in the left pane, select Settings > All settings > General > HSM. The HSM configuration page appears.
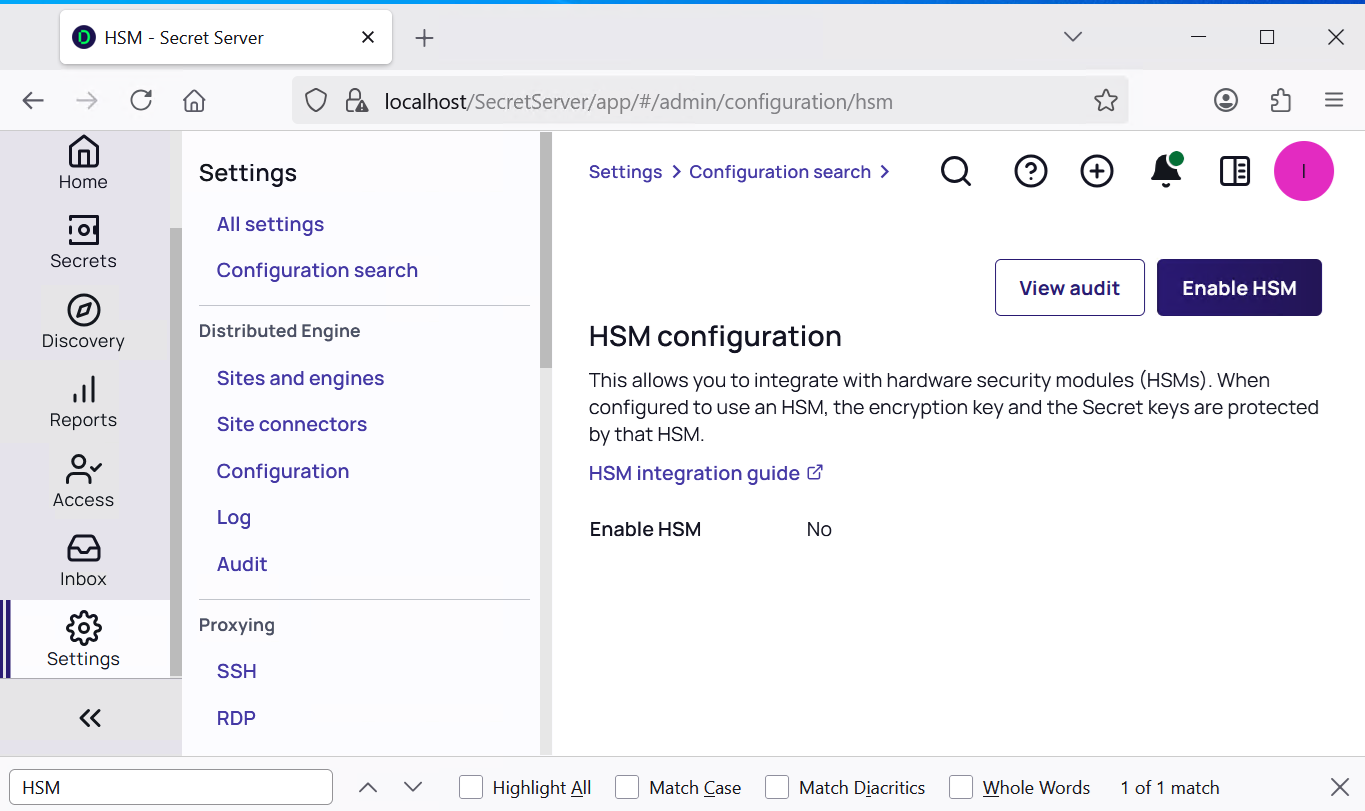
-
Select Enable HSM. Then select Next.
-
In the Enable HSM window, select as follows. Then select Next.
Parameter Value API type
CNG
Persistent provider
nCipher Security World Key Storage Provider
Key type
RSA
Key size
Your selection
Padding type
OAEP (PKCS1 is not supported)
For example:
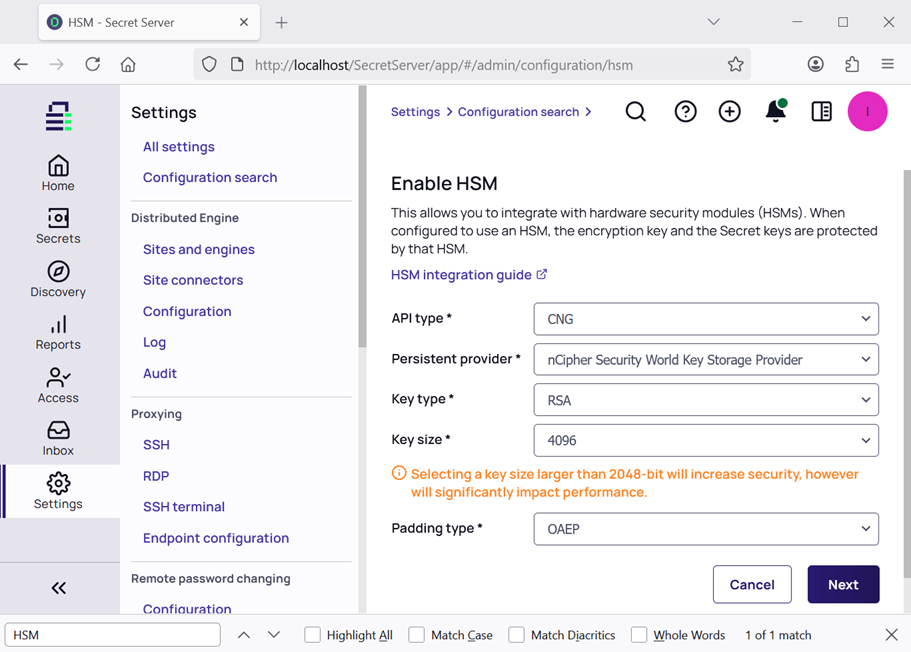
-
Check the HSM Provider Test Results. Then select Next.
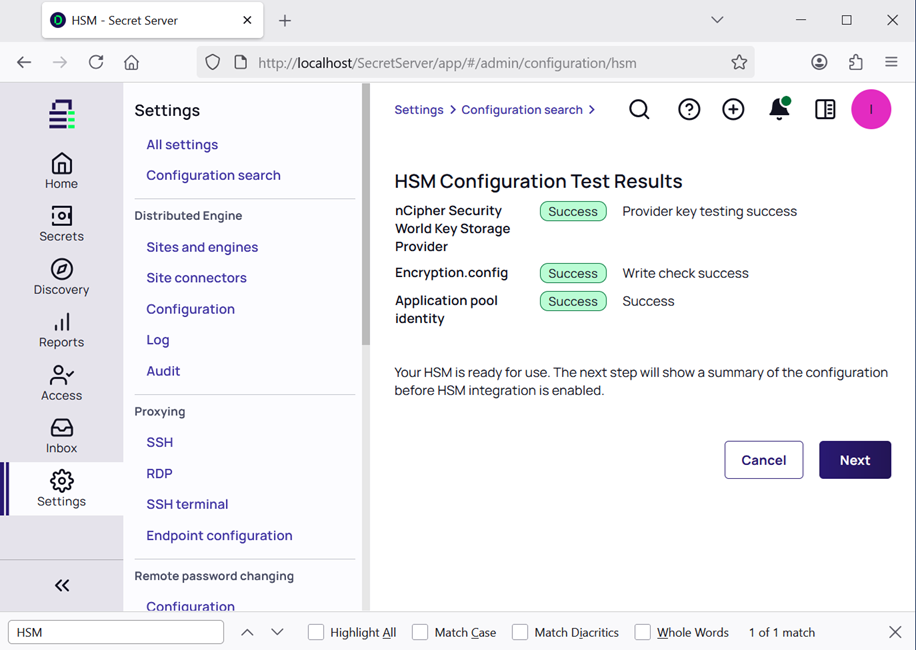
-
In the Verify HSM configuration page select Save.
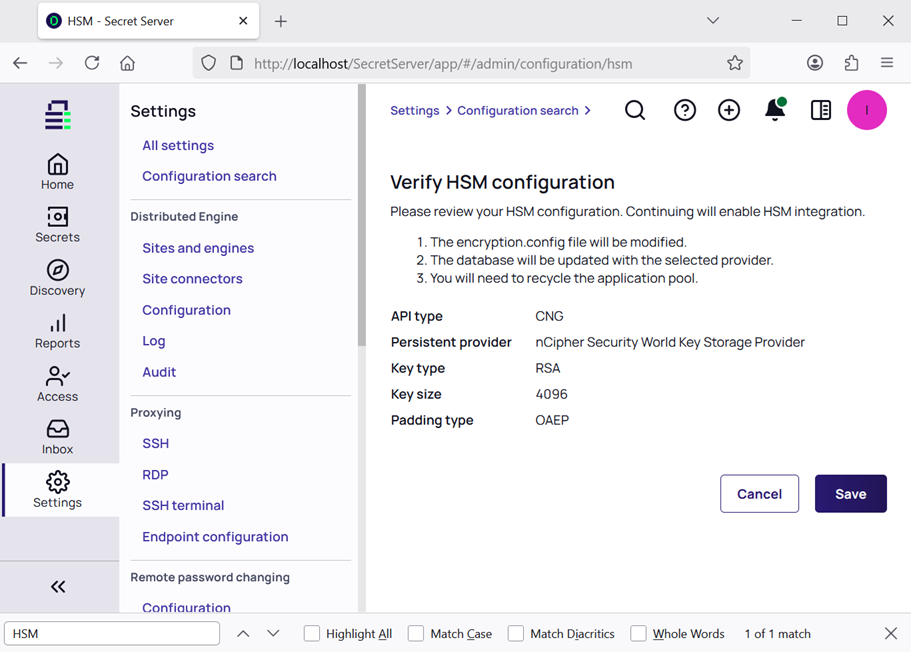
-
In the Notice about HSM configuration change, recycle the application pool. Then select Continue.
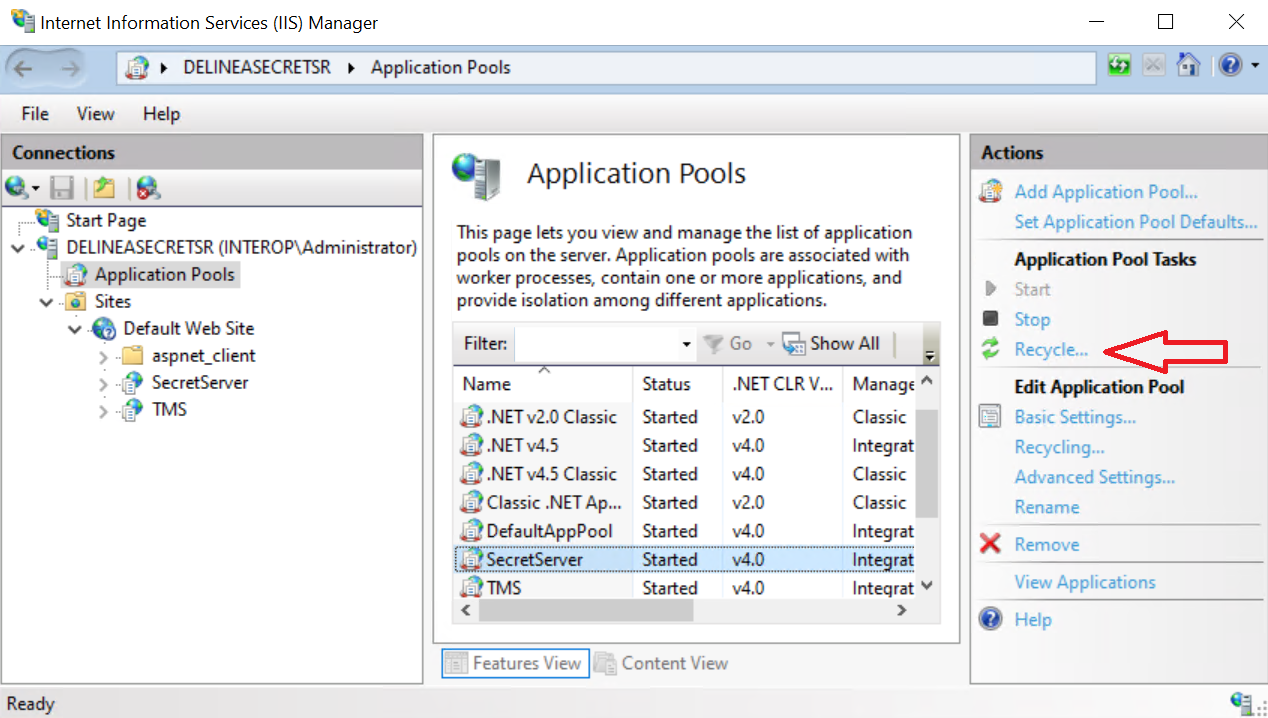
-
Refresh the browser. Then from the menu in the left pane, select Settings > All settings > General > HSM. Notice the completed HSM configuration.
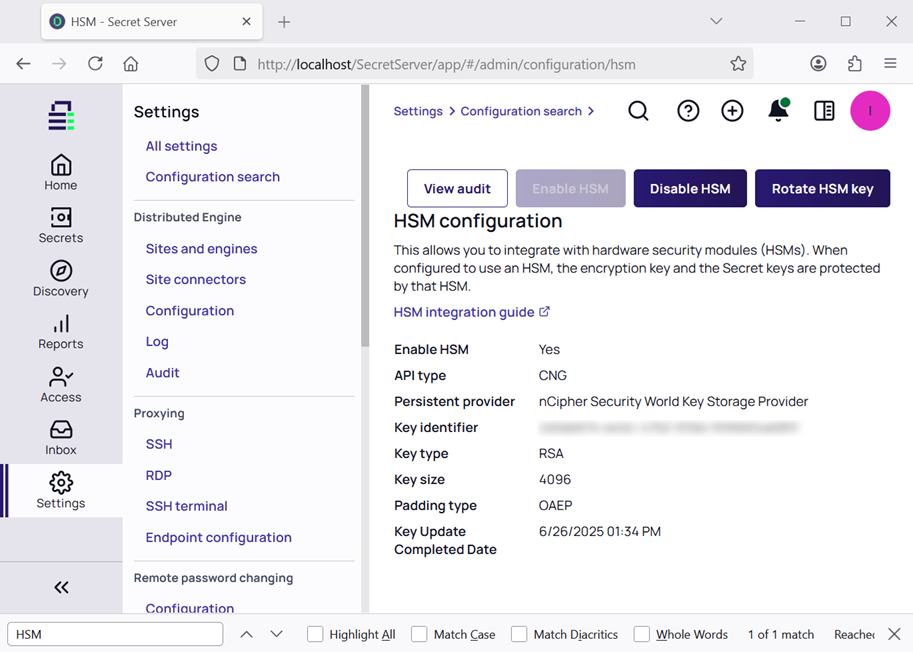
Configure the Delinea Secret Server using the PKCS #11 API
-
Log in to the Delinea Secret Server via a browser at https://localhost/SecretServer.
-
If the HSM was previously configured using the CNG cryptography provider, select Disable HSM, recycle the application pool, and refresh the browser. Otherwise, continue to the next step.
-
Copy the HSM
cryptokilibrary (dll) for PKCS #11 to the Secret Sever application pool as shown:C:\Users\Administrator.INTEROP>copy "C:\Program Files\nCipher\nfast\toolkits\pkcs11\cknfast.dll" C:\inetpub\wwwroot\SecretServer\pkcs11\. 1 file(s) copied. -
If you are using OCS protection, insert your OCS card into the proper slot.
-
From the menu in the left pane, select Settings > All settings > General > HSM. The HSM configuration page appears.

-
Select Enable HSM. Then select Next.
-
In the Enable HSM window, select as follows. Then select Next.
Parameter Value API type
PKCS11
Library name
cknfast.dll
Token label
<OCS cardset name>
User pin
<OCS cardset passphrase>
Key type
AES
Key size
256
For example:
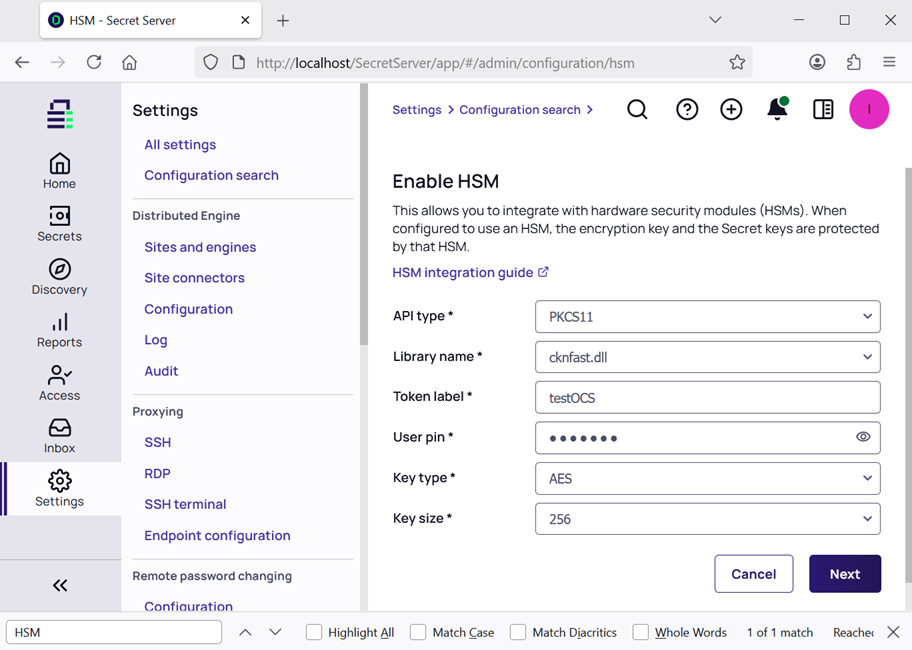
-
Check the HSM Provider Test Results. Then select Next.
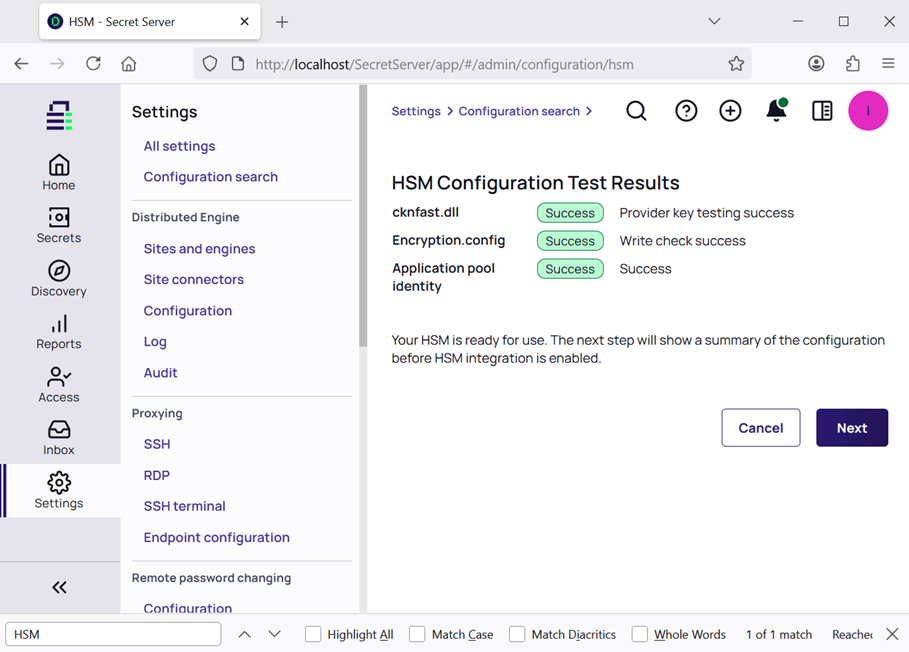
-
In the Verify HSM configuration page select Save.
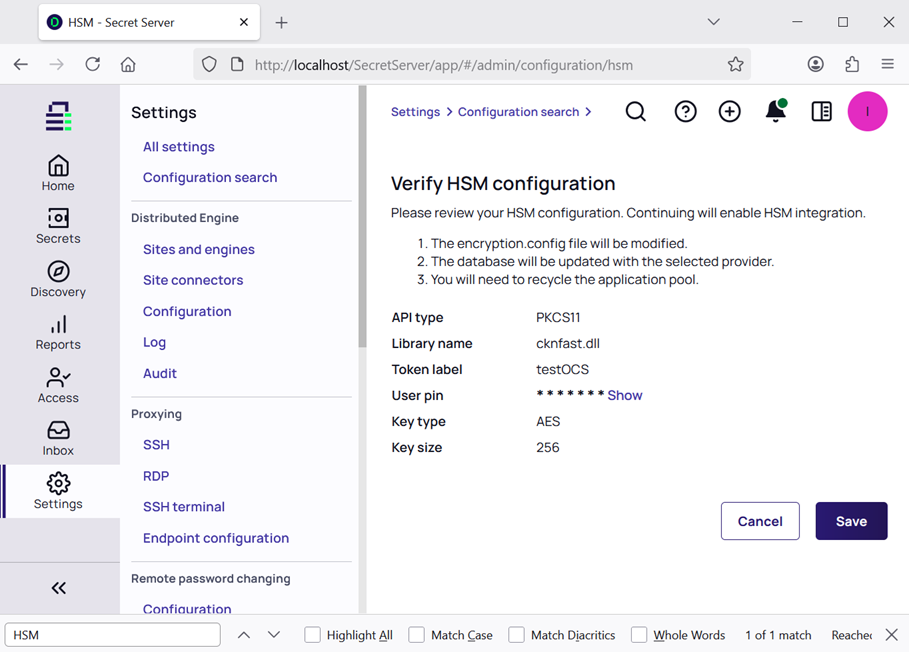
-
In the Notice about HSM configuration change, recycle the application pool. Then select Continue.

-
Refresh the browser. Then from the menu in the left pane, select Settings > All settings > General > HSM. Notice the completed HSM configuration.
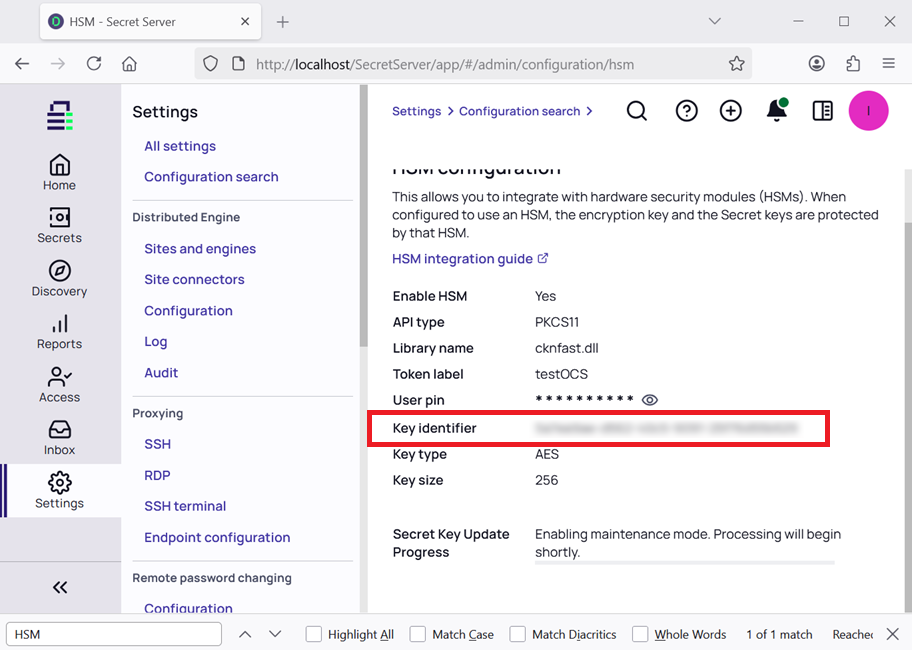
Verify integration
-
List the keys protected by the HSM using the
nfkminfoutility.C:\Users\Administrator.INTEROP>nfkminfo -l Keys protected by cardsets: key_pkcs11_ucedb3d45a28e5a6b22b033684ce589d9e198272c2-5c65ec9a8fd17ea4ff069e88f552f926d35252d0 `5a7ea9ae-d562-40c5-9091-25f76d55b529' -
Notice the Key identifier in the completed HSM configuration matches the
nfkminfoutility output above. In this case the key corresponds to the the Delinea Secret Server using the PKCS #11 API.
This completes the integration of Delinea Secret Server with the Entrust nShield HSM. Secrets created in Delinea Secret Server will use encryption keys that are stored in the HSM.