Create an AWS IAM user service account
KeyControl uses an AWS IAM user service account to perform the KMS functionality in BYOK.
Create an AWS BYOK service account policy
-
In AWS, navigate to IAM.
-
In the left pane select Access management / Policies. Then select the Create policy icon.
-
In the Specify permissions window, select the JASON icon.
-
Copy the following in the policy editor window. Then select Next
{ "Version": "2012-10-17", "Statement": [ { "Sid": "ServiceAccountPolicy", "Effect": "Allow", "Action": [ "kms:*", "ec2:DescribeRegions", "ssm:GetParameter", "iam:ListUsers", "iam:GetUser", "iam:CreateAccessKey", "iam:UpdateAccessKey", "iam:ListAccessKeys", "iam:DeleteAccessKey", "iam:CreateServiceLinkedRole" ], "Resource": "*" } ] }CreateServiceLinkedRoleis needed to create multi-region keys.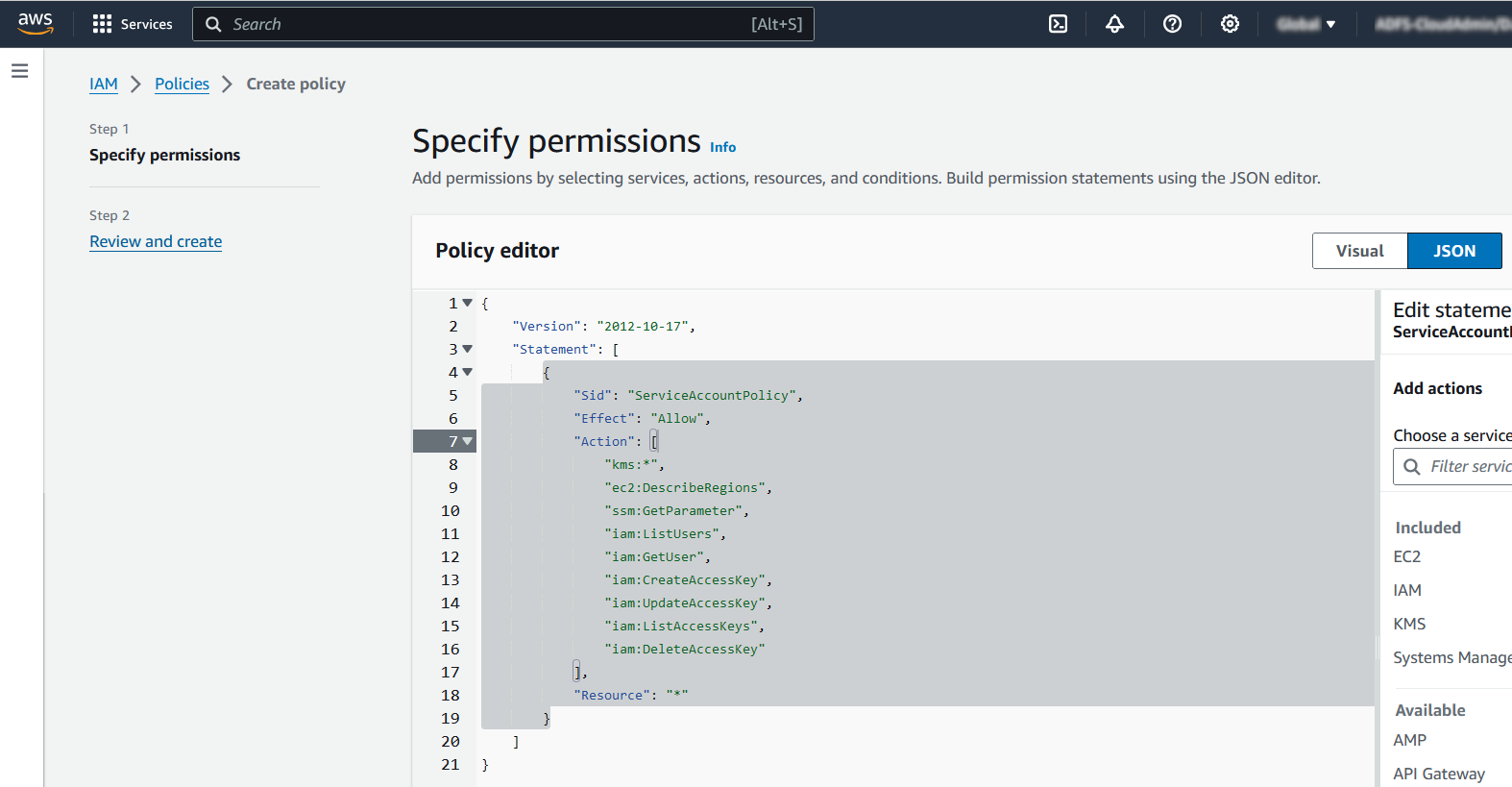
-
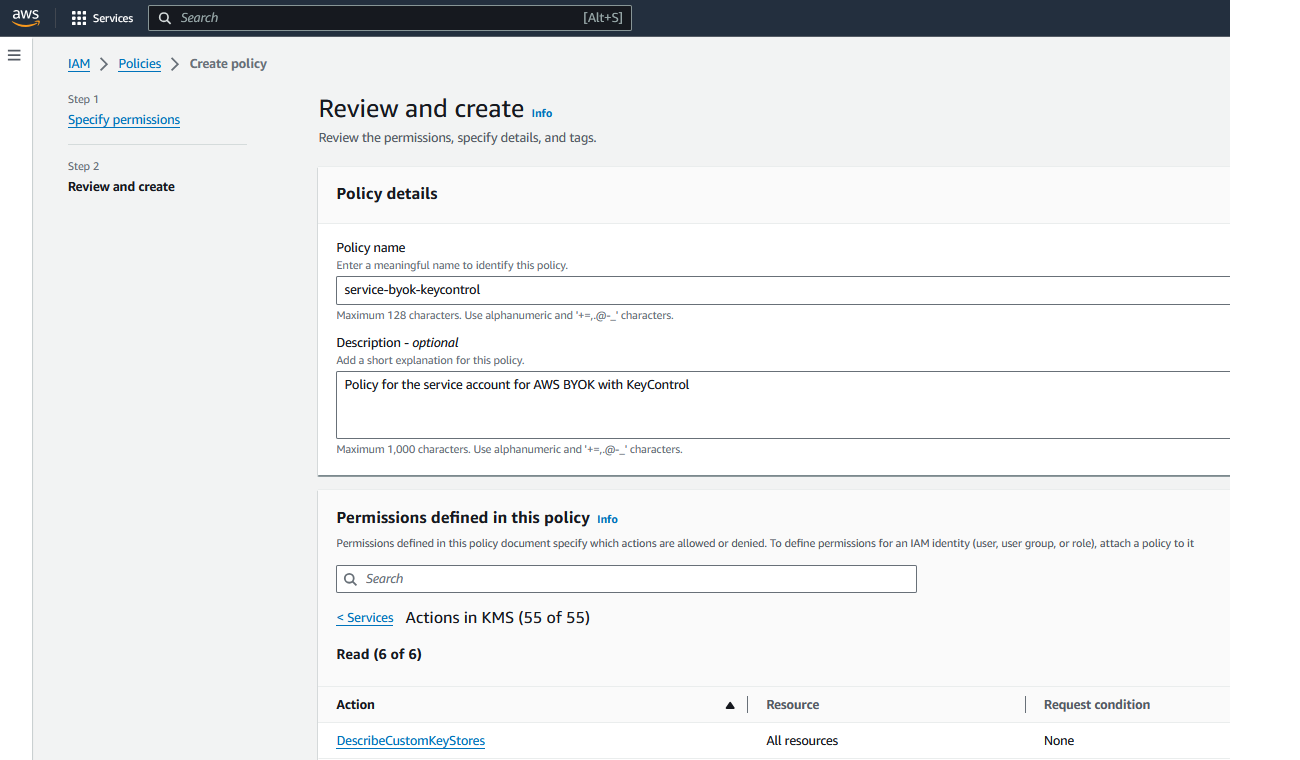
In the Review and create window, enter a name and description.
-
In the Permissions defined for this policy section, select KMS. Then select Create policy.
-
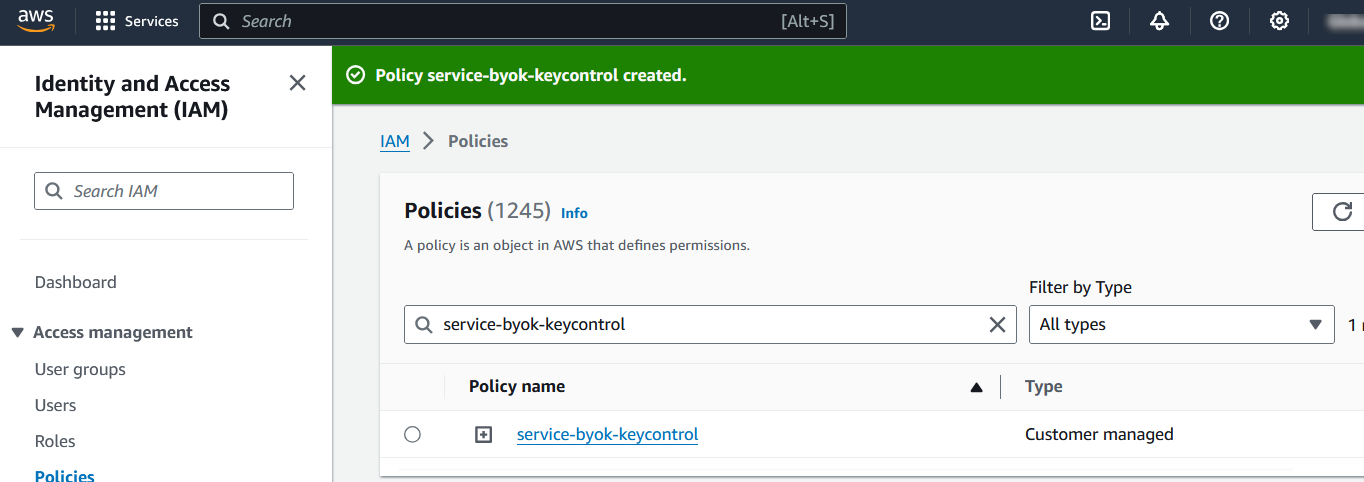
Notice the new policy created.
For further information, refer to the AWS BYOK Service Account Requirements.
Create an AWS IAM user service account
This steps create an AWS IAM user with no console access, a service account, with policy created in Create an AWS BYOK service account policy.
-
In AWS, navigate to IAM.
-
In the left pane select Access management / Users. Then select the Create user icon.
-
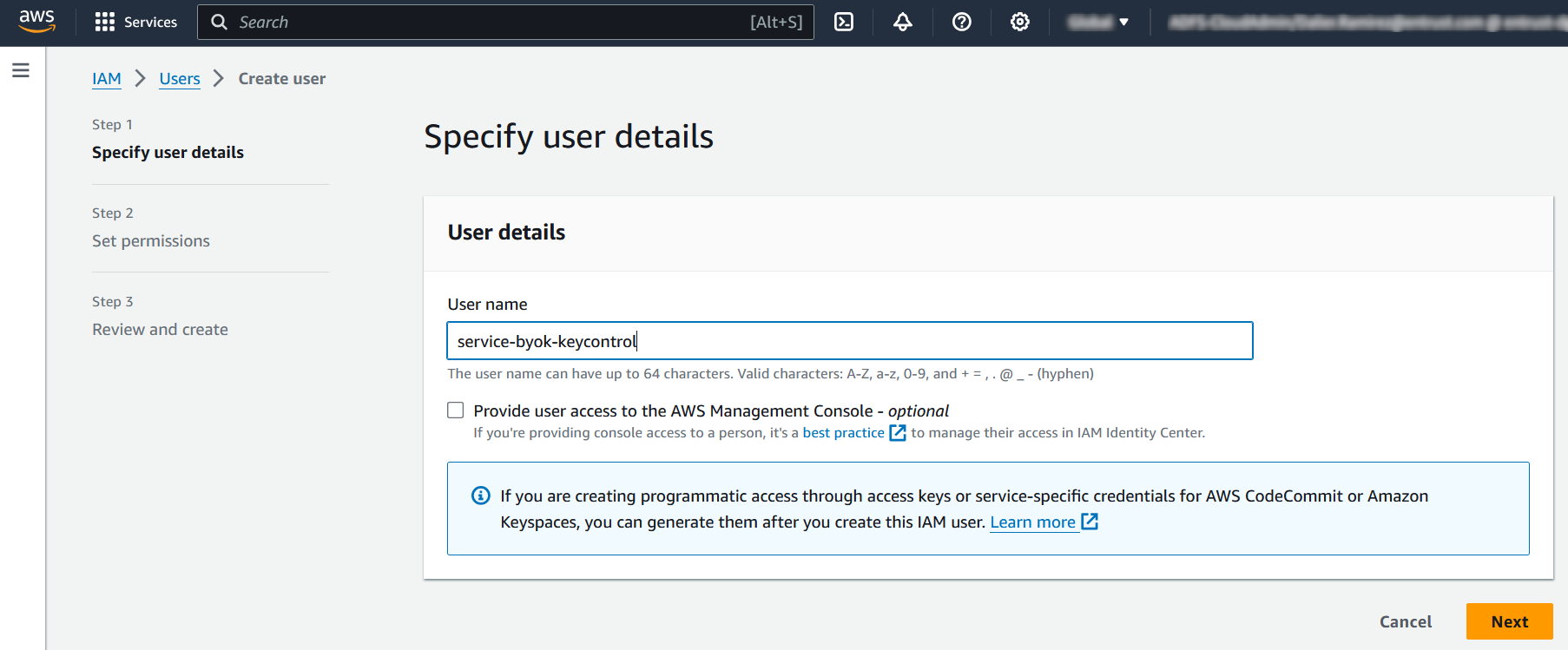
Enter the user name. Uncheck Provide user access to AWS Management Console - optional since we are creating a service account. Then select Next.
For example:
-
In the Set permissions window, select the Attach policies directly radio button.
-
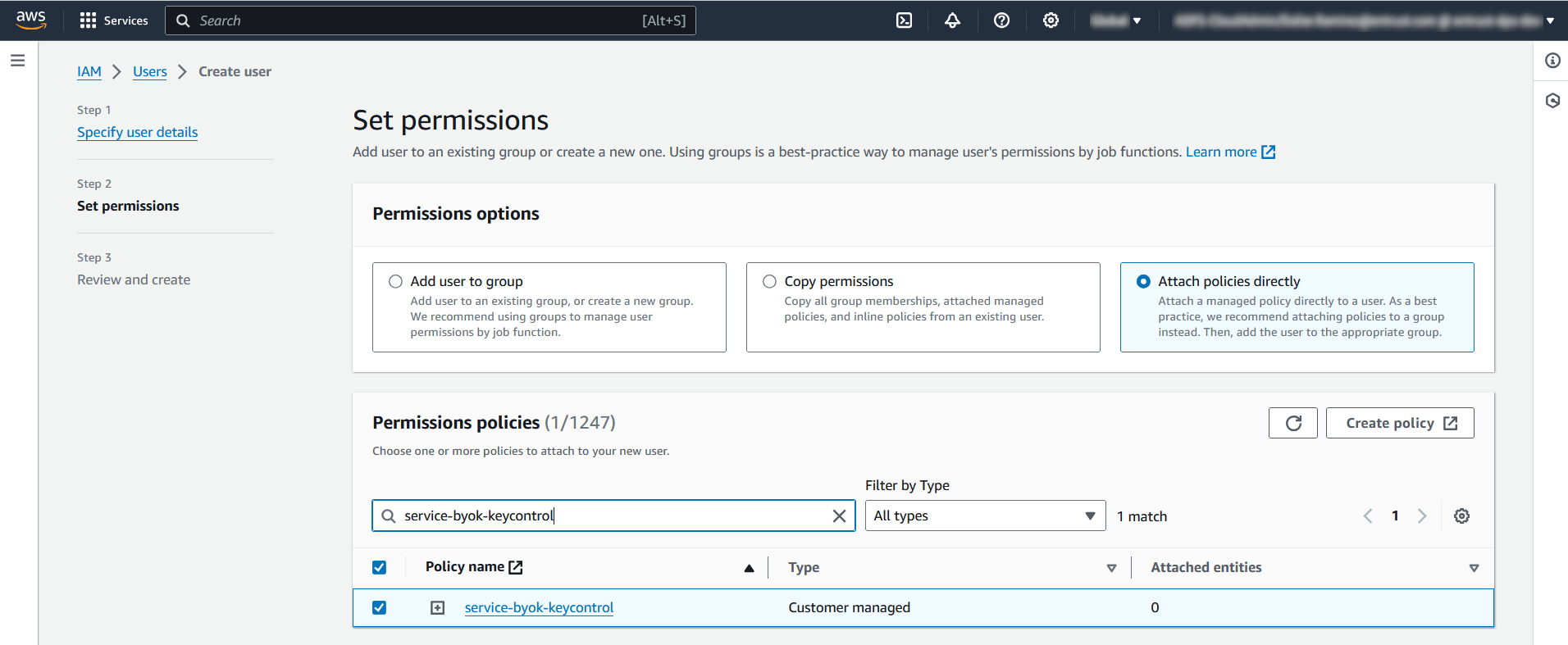
In the Permissions policy section, enter the policy created in Create an AWS BYOK service account policy. Check the policy. Then select Next.
-
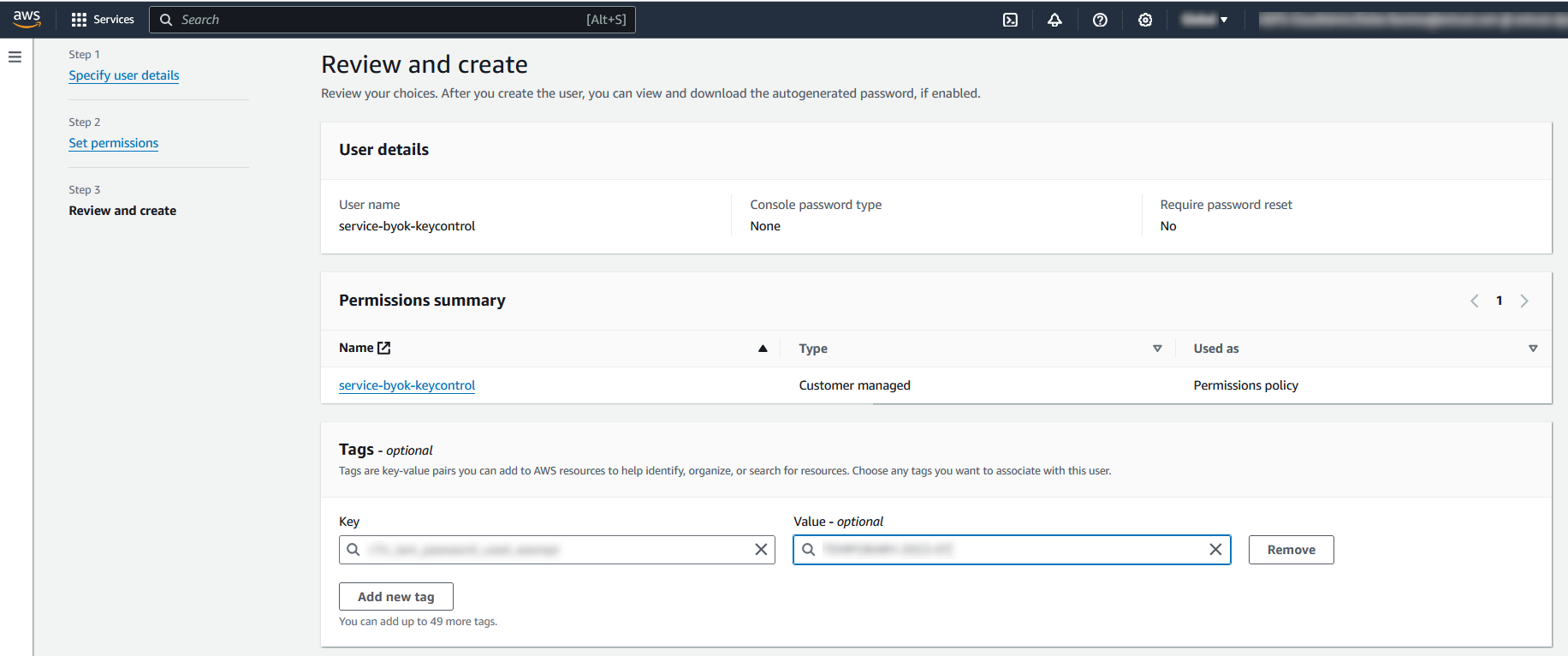
In the Review and create window, go to section Tags - optional and select Add new tag if required by your organization. Enter the key-value pair. Then select Create user.
Some organizations uses tags manage IAM users key. Check your organization’s policies. For example:
-
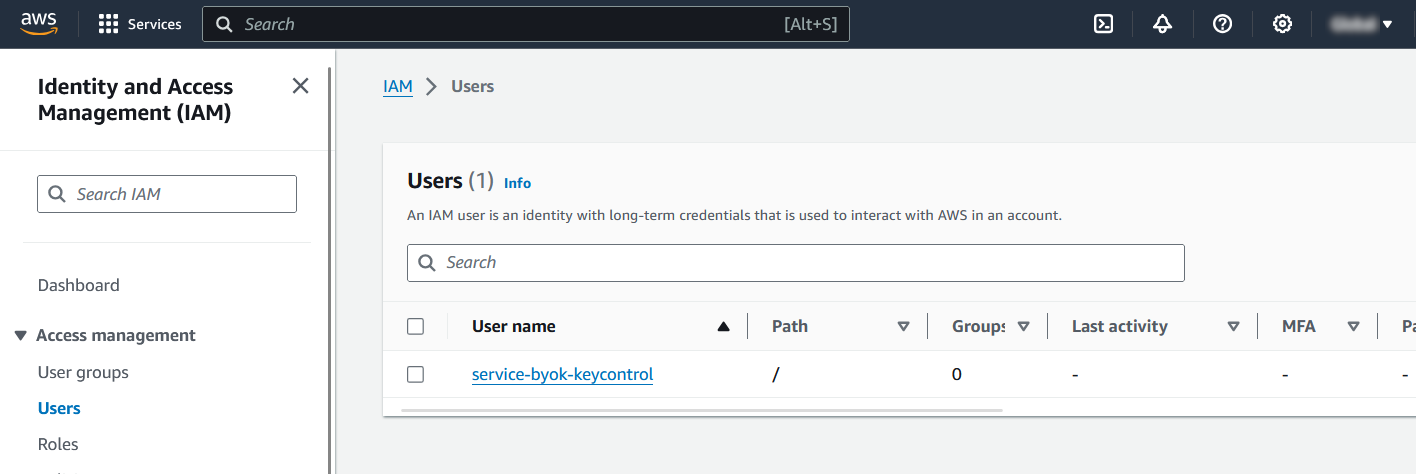
Notice the new user created.
-
Select the new user. Then select the Security credentials tab.
-
In the Access keys (
x) section, select the create access key icon. -
In the Access key best practices & alternatives window, select the Third party service radio button. Check I understand the above recommendation and want to proceed to create an access key. Then select Next.
KeyControl gives you the ability to rotate the access keys. You can set the rotation schedule later on, in integrate-kc-aws-byok.adoc#create-csp-account-for-aws. 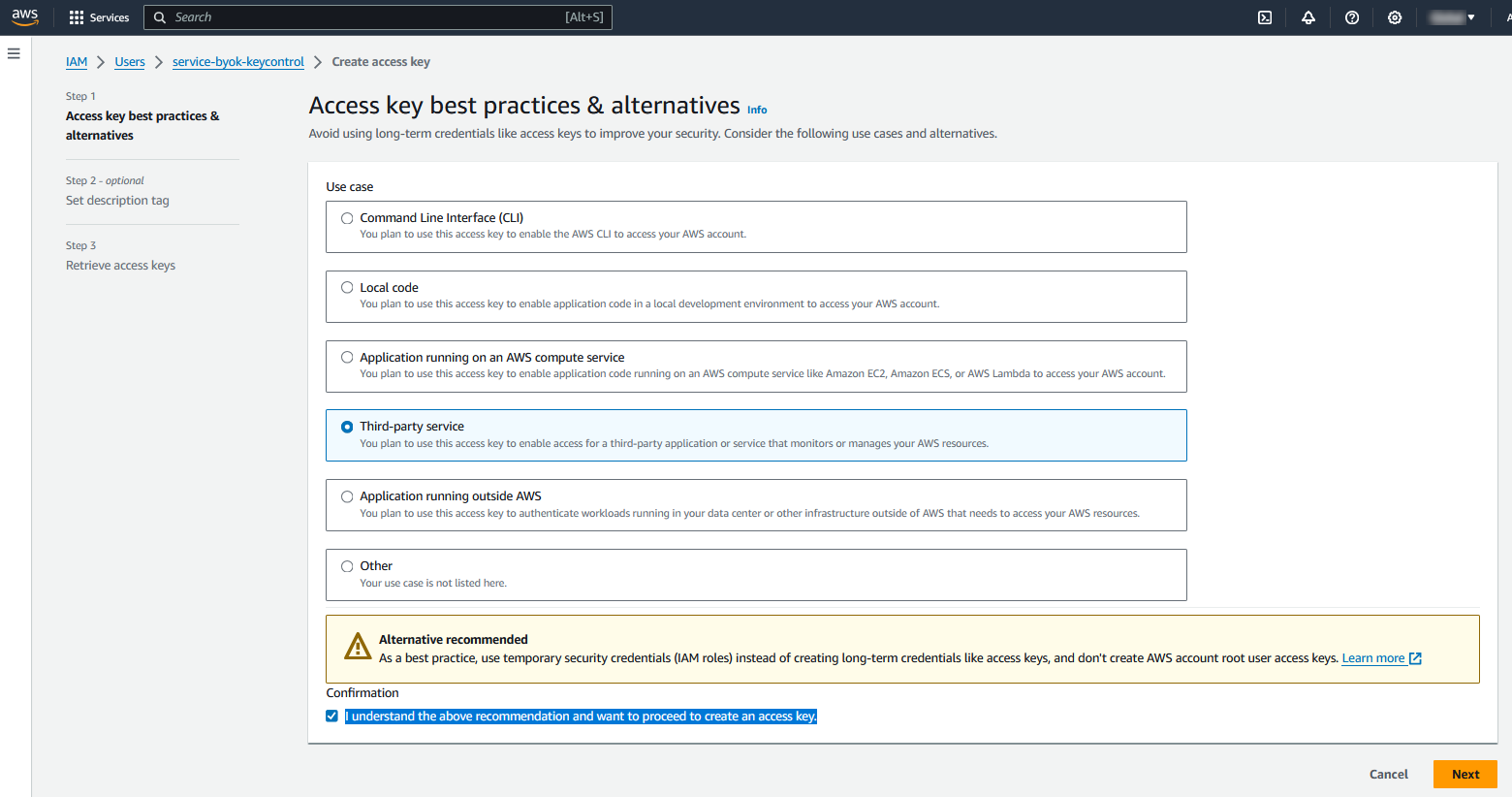
-
In the Set description tag - optional window, enter a description tag if desired. Then select Create access key.
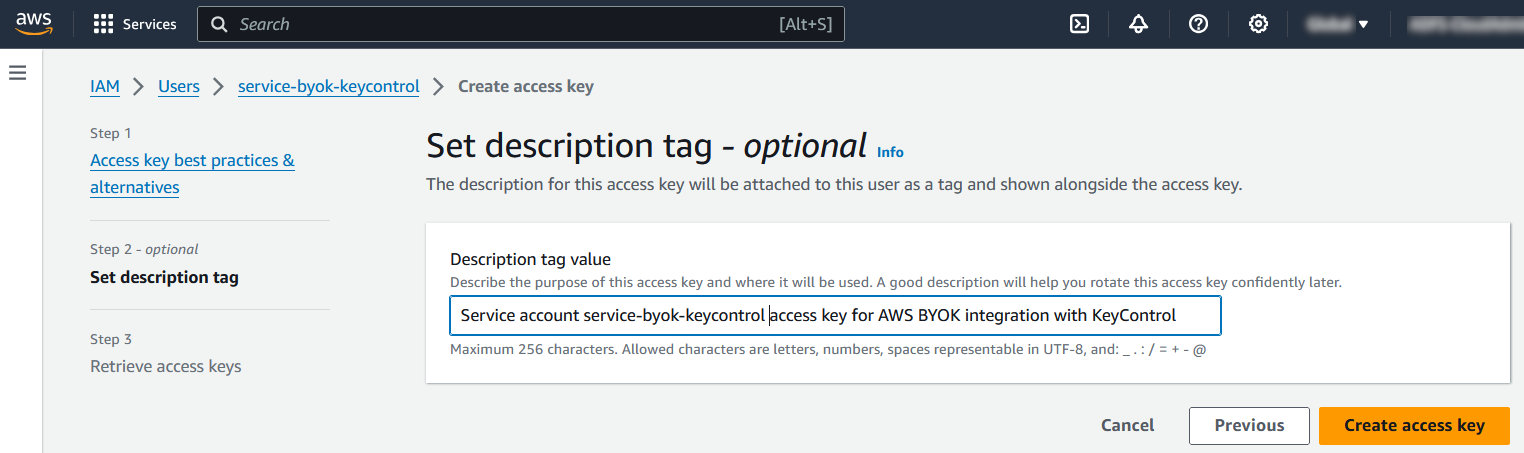
-
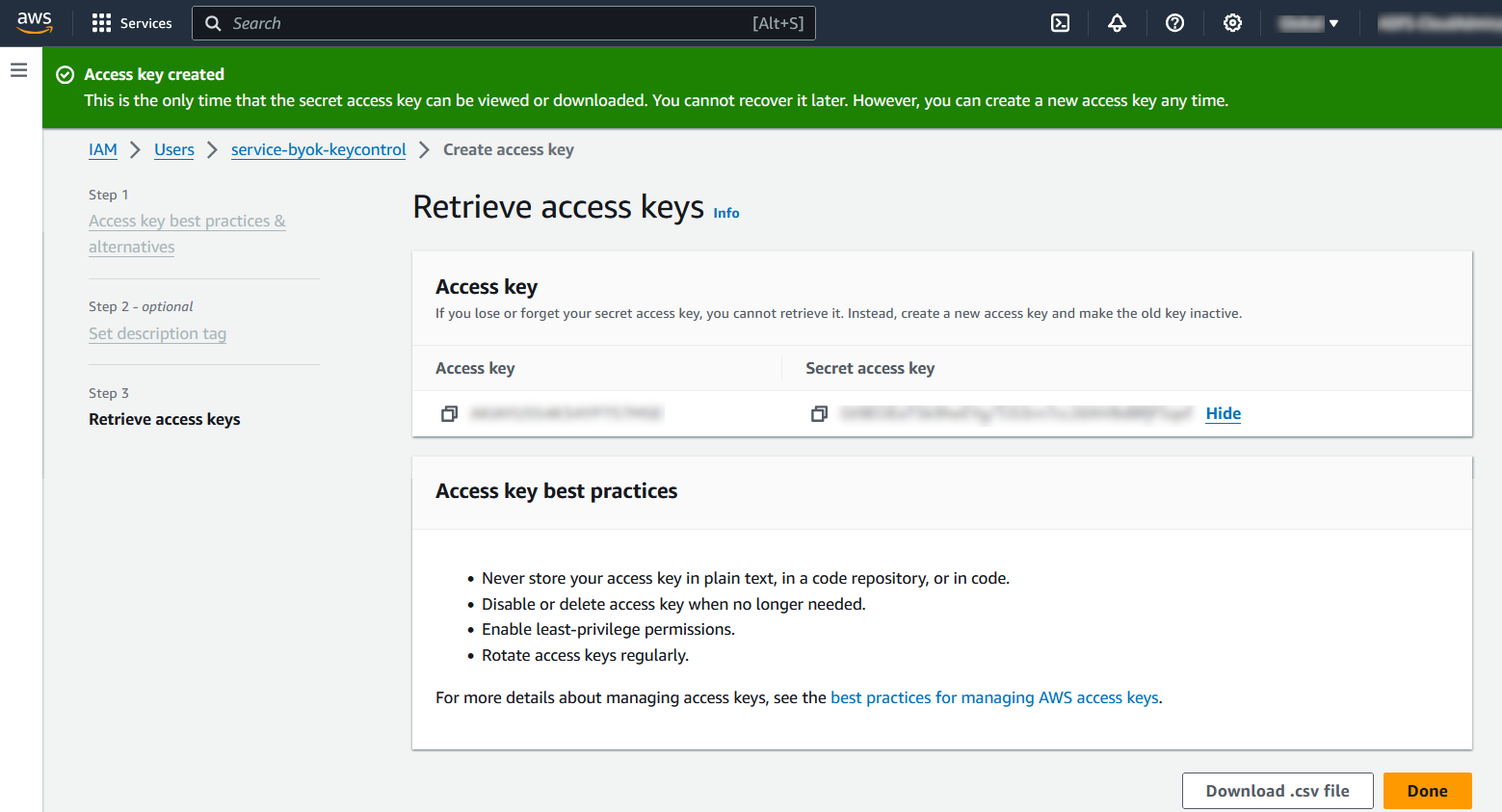
In the Retrieve access key window, select Download .csv file to download a file containing the Access key and Secret access key. Save these keys. You will need them to integrate-kc-aws-byok.adoc#create-csp-account-for-aws. Then select Done.