Testing
Encrypting a virtual machine with a trusted key provider looks the same as the virtual machine encryption user experience that was first delivered in vSphere. See Use Encryption in Your vSphere Environment.
This chapter demonstrates the encryption of a VM using VMware Trust Authority.
-
Connect to vCenter Server of the Trusted Cluster (Workload cluster) by using the vSphere Client.
-
Log in as the vCenter Server Administrator, or an Administrator that has the
Cryptographic operations.Manage key serversprivilege. -
Locate a VM that you would like to encrypt.
-
Make sure the Power state for the VM indicates that it is powered off.
-
Right-click the VM for which you would like to enable encryption, and select VMPolicies > Edit VM Storage Policies.
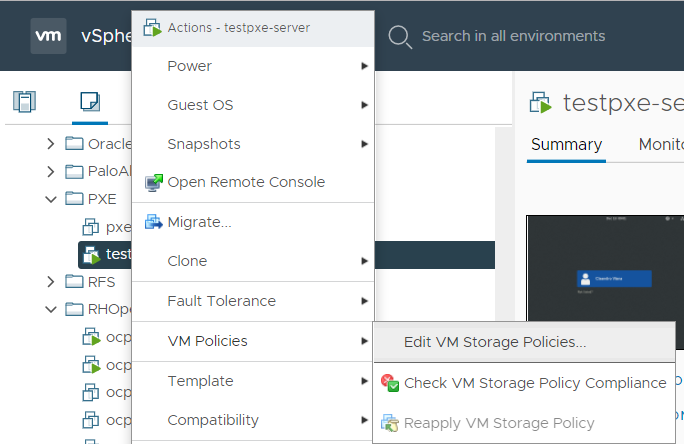
-
Select the storage policy VM Encryption Policy and select OK.
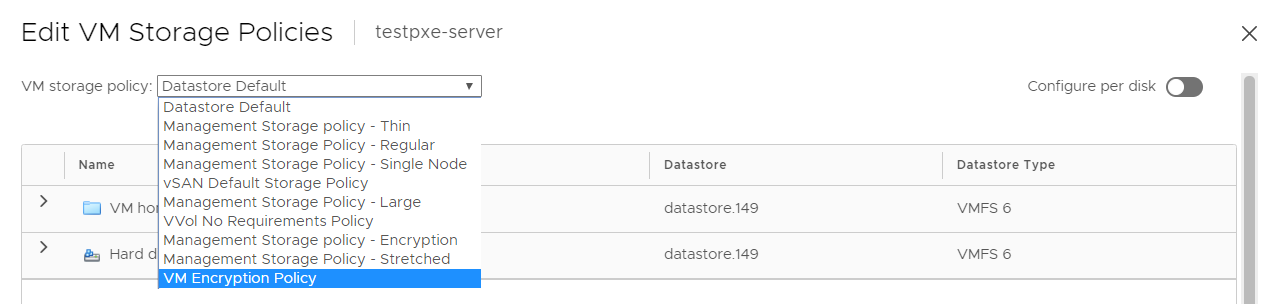
This will trigger a reconfiguration of the VM.
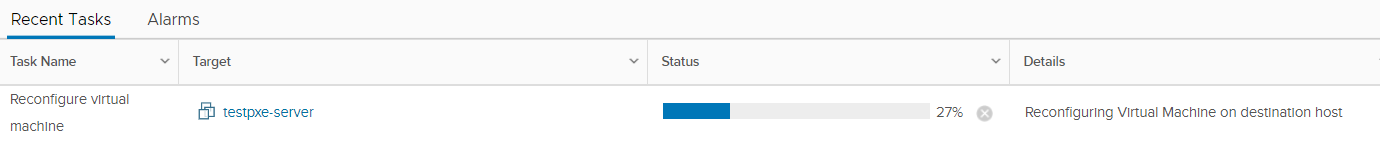
Once the reconfiguration is complete, the disks are encrypted and the keys are managed by the configured KMS, in our case KeyControl.
Troubleshooting
Secure Boot is not enabled
When attempting to Encrypt a VM, the following error occurs:
A general runtime error occurred. Key Provider KeyControl1 is not compatible with the host xx.xxx.xxx.201.
Reason: "Attestation failed because Secure Boot is not enabled."To resolve this, make sure Secure Boot is enable at the VM.