Procedures
CloudControl was not configured to use Active Directory. CloudControl also supports a cluster environment and this will be documented in the installation guide.
Download the CloudControl software
-
Log in and select HyTrust CloudControl.
-
Open the folder
HTCC_6.6.0_2023-02-24. This folder contains version 6.6.0 that was used in this guide. -
Select the
Entrust-CloudControl-6.6.0.660934.ziplink to download the file.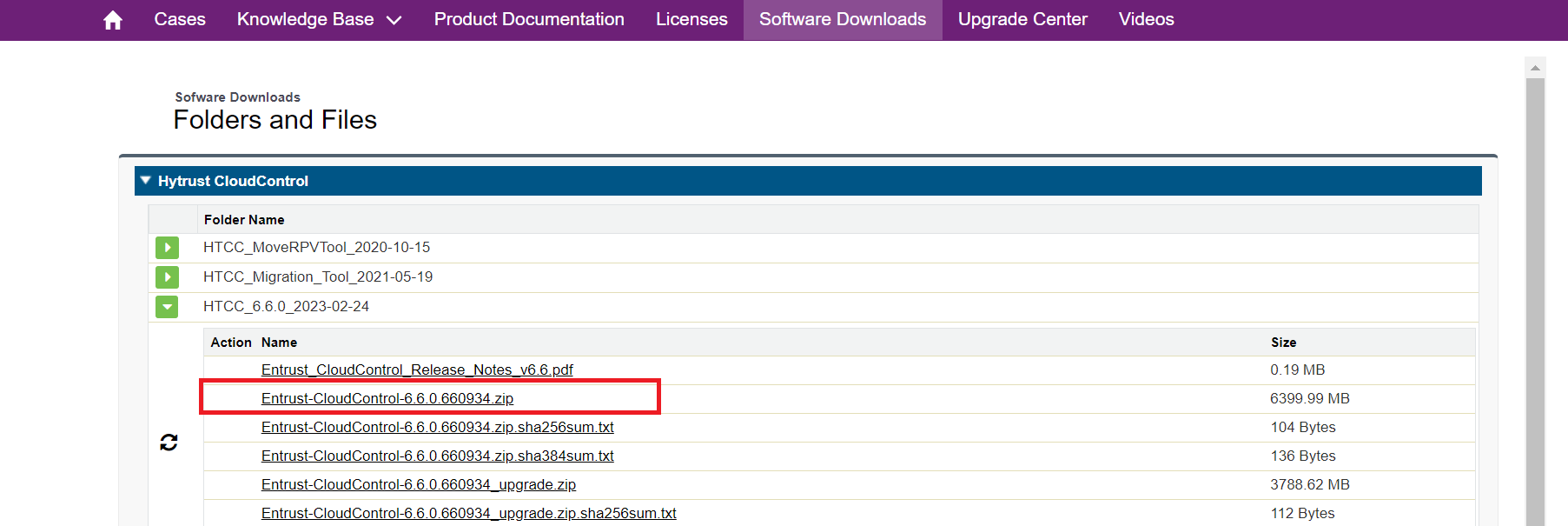
-
Once the file has been downloaded, open the ZIP file to access to the OVA file.
Deploy the CloudControl VM from the OVA
-
Log in to vCenter.
-
Navigate to Inventories > Hosts and Clusters.
-
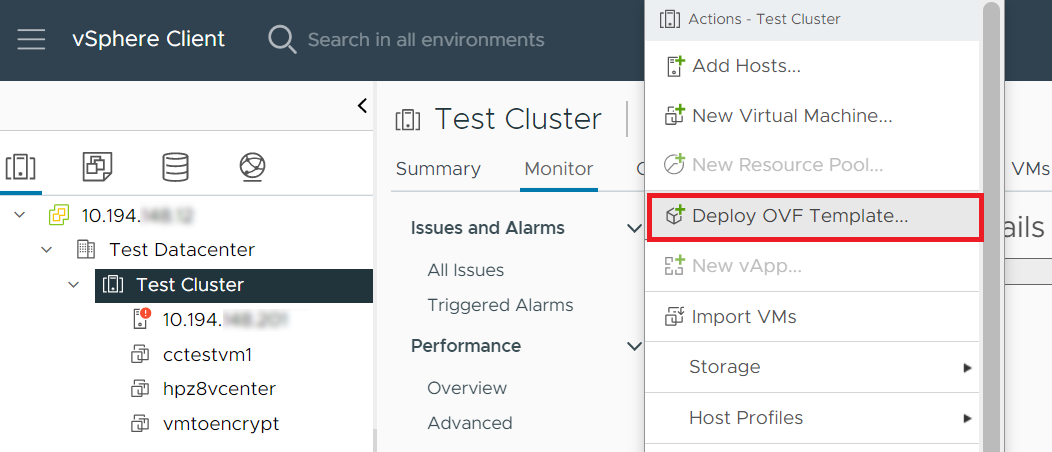
Select the resource pool where you plan to deploy CloudControl.
-
Select Actions > Deploy OVF Template from vSphere Web Client.
-
On the Select an OVF Template page, select Local File and upload the
Entrust-CloudControl-6.6.0-660934.ovafile.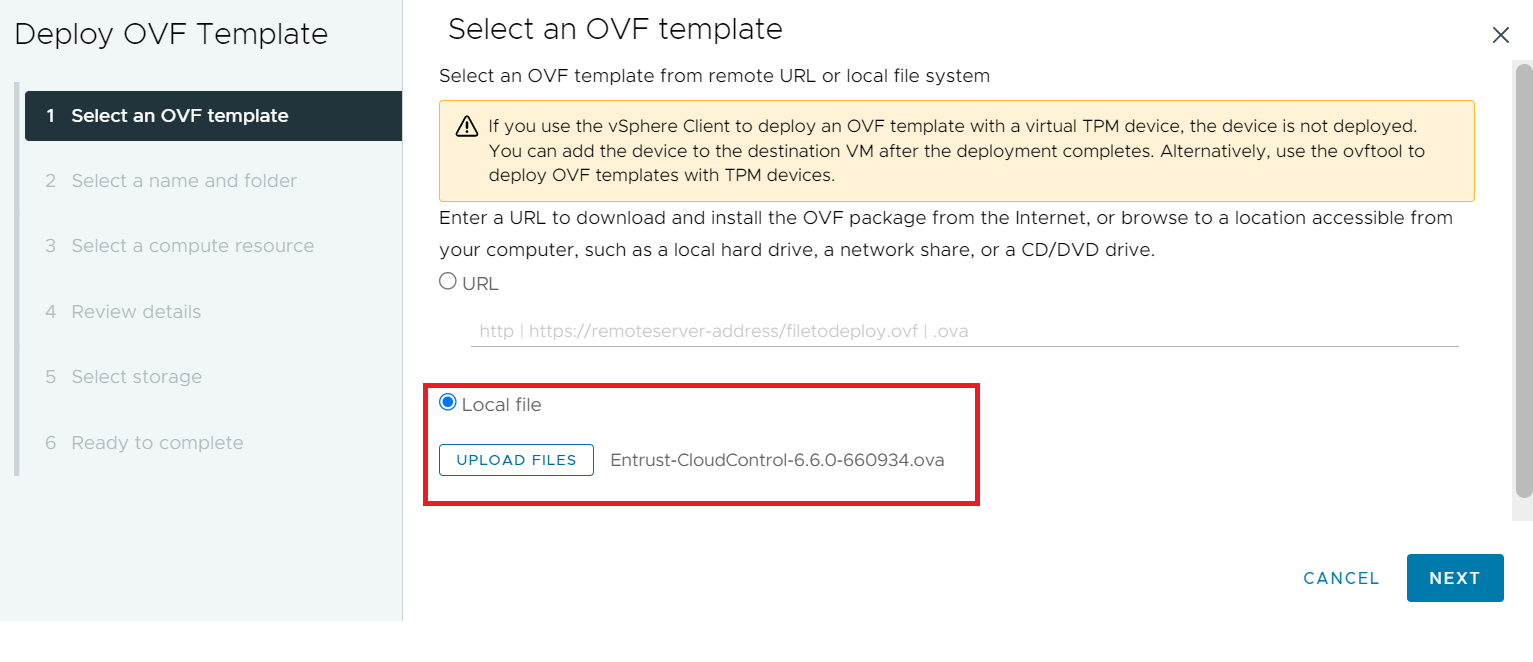
Follow the instructions on Deploying CloudControl as required.
| For more information refer to Installing CloudControl from an OVA in the online documentation. |
Power on the appliance
-
Log in to the vSphere Client.
-
Locate the Entrust CloudControl virtual machine in the inventory.
-
Right-click the CloudControl virtual machine and select Power > Power On.
Configure the CloudControl virtual appliance
This guide uses a Standalone Node setup. Follow the online documentation for instructions for Creating a Standalone Node.
Set up the CloudControl GUI
Once the standalone node has been configured, you must finish the setup using the GUI. Follow the online documentation instructions on Setting Up the CloudControl GUI.
Add vCenters to CloudControl
You can now add the VMware vSphere inventory into CloudControl.
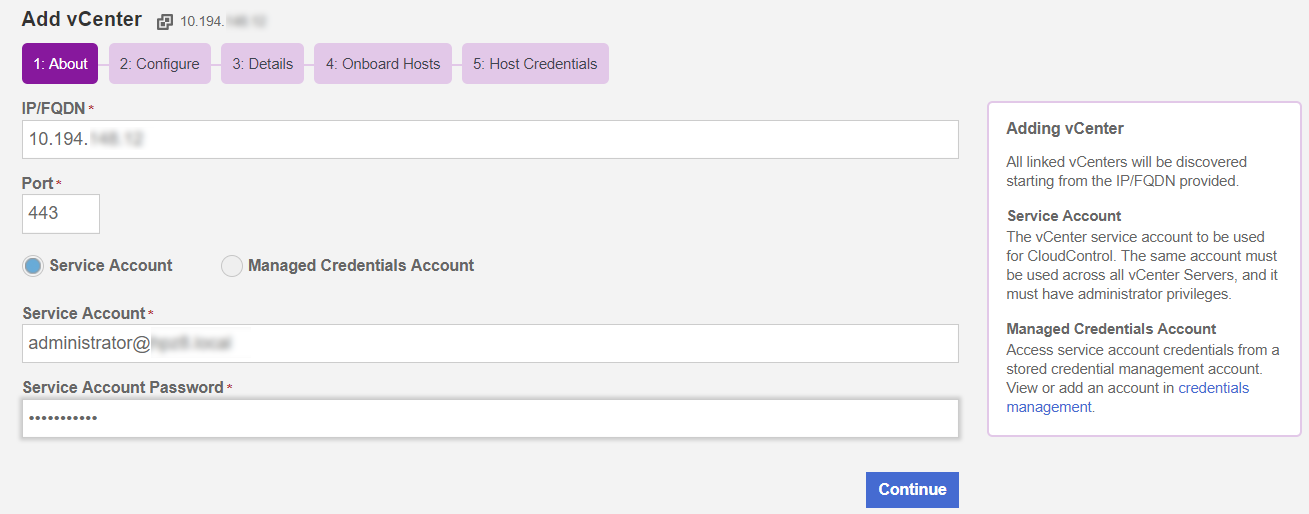
Add a vCenter to CloudControl
To add a vCenter to CloudControl:
-
From the Home tab, select Inventory > vSphere.
-
On the vSphere page, select Actions > Add vCenter.
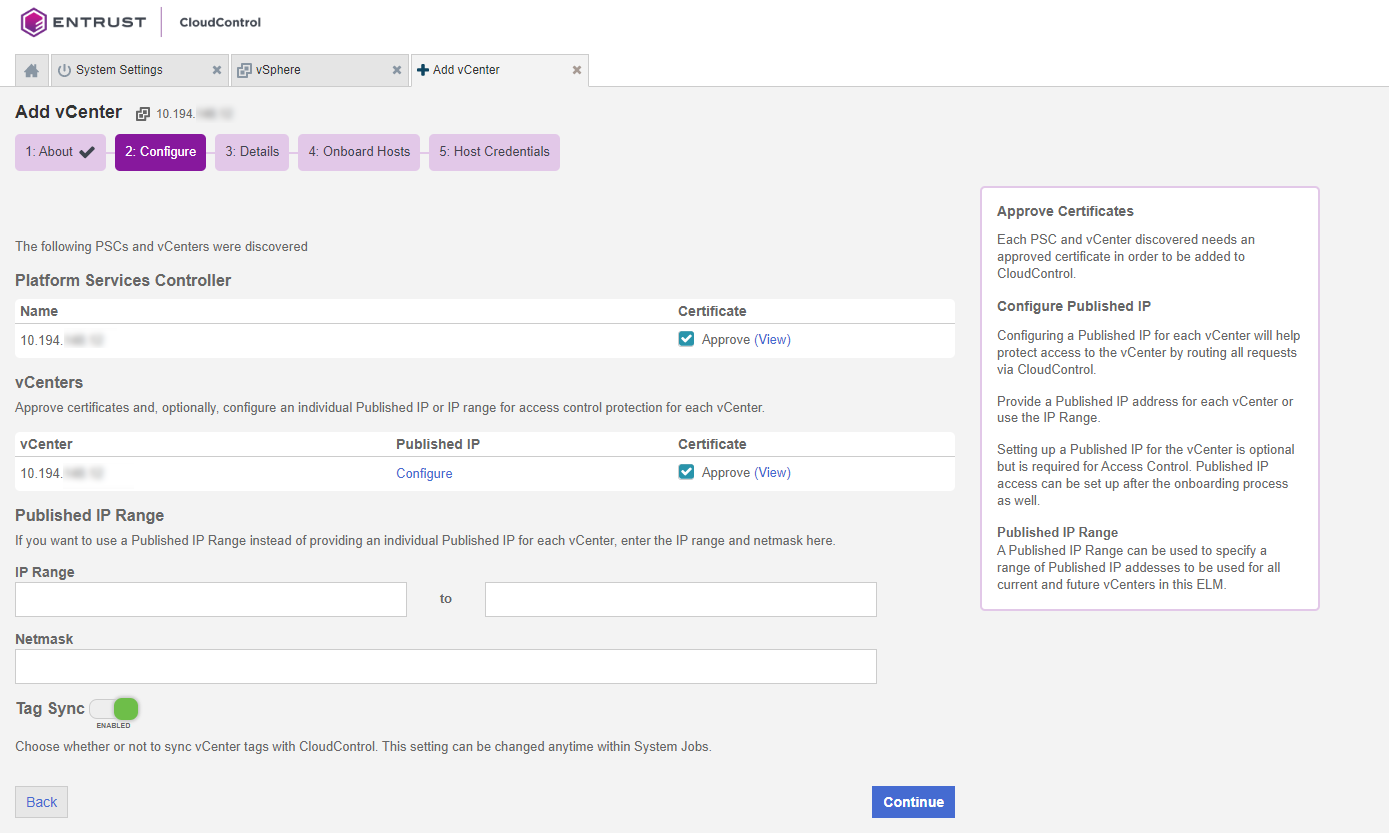
Configure CloudControl after adding a vCenter
To configure CloudControl after adding a vCenter:
-
On the Configure page, view and approve the certificates for the Platform Services Controller (PSC) and all vCenters that were discovered.
-
The Approve checkbox must be checked for all certificates before you can add the vCenter.
-
Certificates from a trusted source have the Approve checkbox checked automatically.
-
Select the Certificate link to view the certificate details.
Certificates without a certificate authority are displayed with a warning icon. Select the link in the tool tip to add a CA. You can manually approve these certificates by checking the Approve checkbox. Certificates that are invalid or expired are displayed with an error icon. These certificates cannot be approved. All vCenter and PSC certificates are displayed on the Certificate Authorities tab on the Certificates page.
-
Select Approve to populate the approve checkbox for the certificate, or select the x icon to close the window.
-
Determine if you want to use a single Published IP for each vCenter or a Published IP Range to be used for all current and future vCenters in this ELM.
If you plan to use Access Control, you must have a Published IP address or range.
-
For a Published IP, select the Configure link in the Published IP column of the vCenter table, enter the Published IP Address and Netmask, and select Apply.
-
For a Published IP Range, enter the Published IP Address and Netmask in the Published IP Range section.
-
Enable Tag Sync if you want vCenter Tags in CloudControl.
-
When all certificates are approved, select Continue.
| You cannot select Continue until all of the Approve checkboxes are checked. |
Check the online documentation instructions for more detail on Adding vCenters to CloudControl.
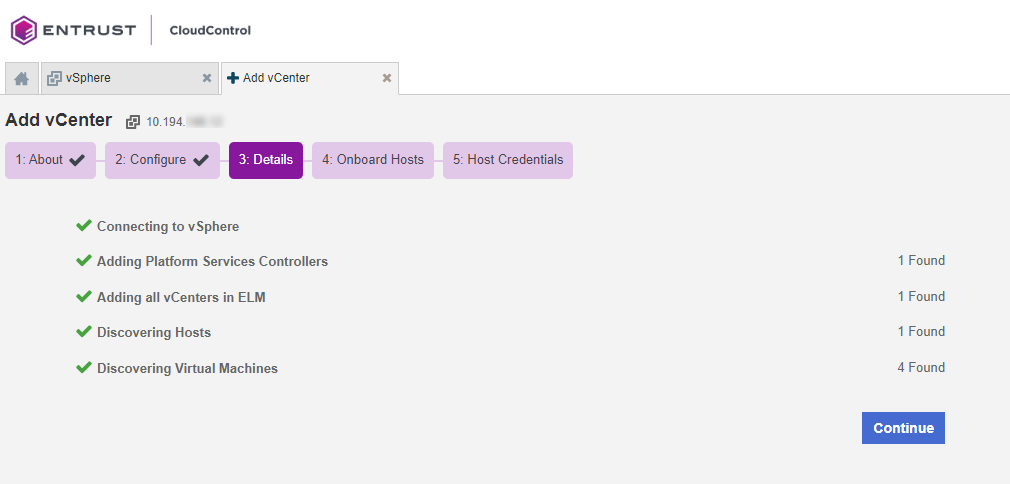
View Details
On the Details page, you can monitor the process as all of your vSphere information is collected.
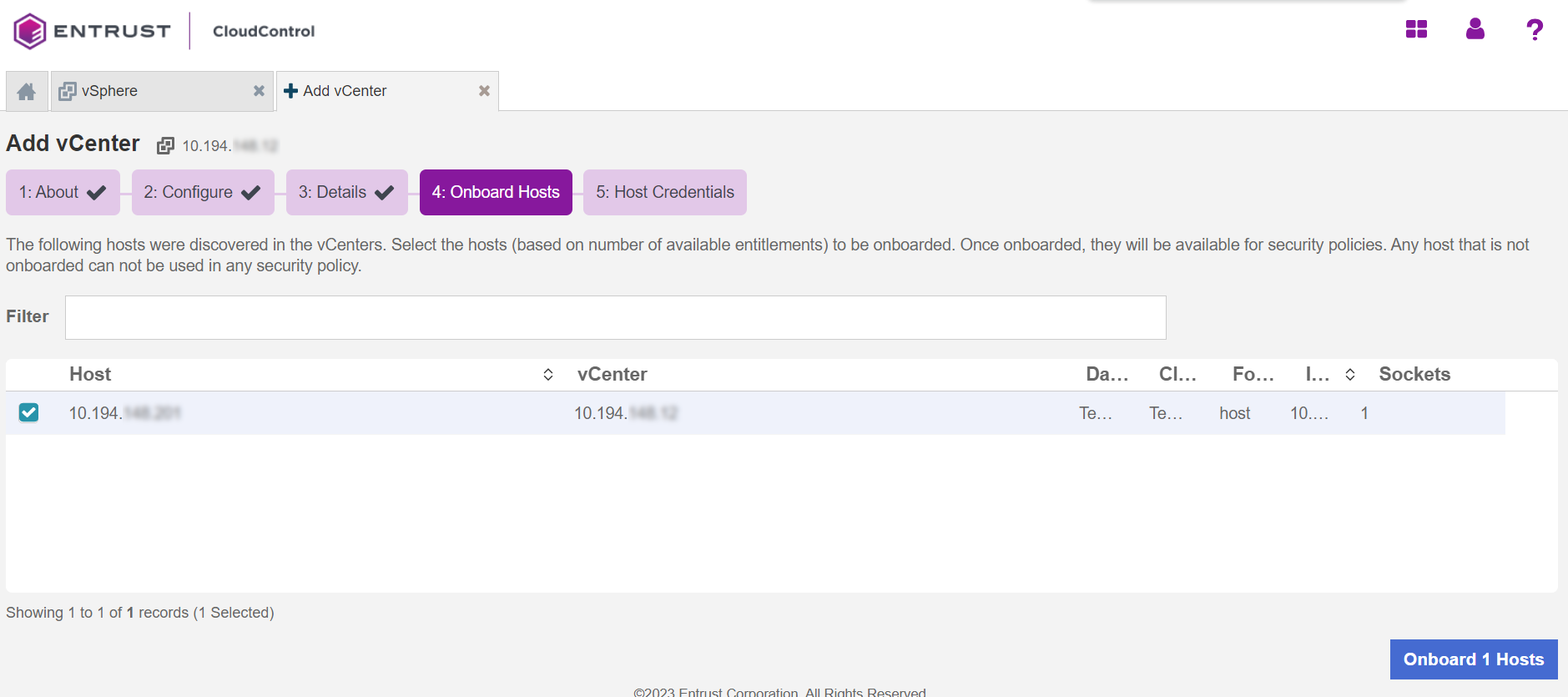
Onboard the hosts
On the Onboard Hosts page, you can view the hosts that were discovered, remove hosts, or add additional hosts to be added to CloudControl. Select the hosts that you want to add and select Onboard Hosts.
| You must add hosts before you can run Configuration Hardening policies (assessment and remediation) against your hosts. |
Host credentials
On the Hosts Credentials page, you can add or import the credentials for your ESXi hosts.
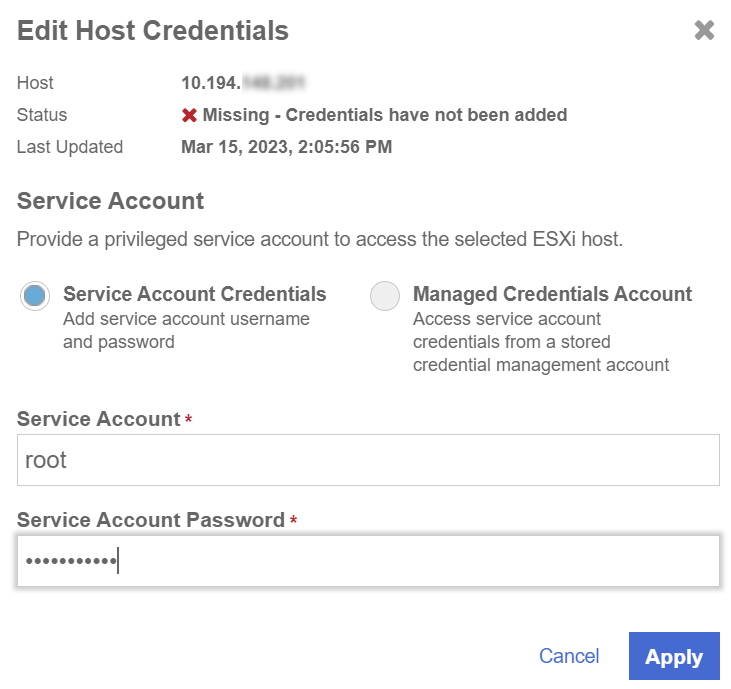
Add credentials
To add credentials:
-
Select one or more ESXi hosts that share the same credentials and select the Missing link in the Credentials column.
-
In the Add Host Credentials window, enter the User Name and Password for the ESXi hosts and select Apply.
The Credentials column for each host shows the host status. This can be one of the following:
-
Missing
-
Valid
-
Invalid
You may encounter an Invalid Certificate when adding the Host Credentials. To resolve this issue, the vCenter root CA must be imported into the CloudControl’s Certificate Authorities. Check [certificate-invalid] for troubleshooting. -
Import credentials
To import credentials, you must upload a CSV file in the following format: ESXINAME FQDN, PASSWORD, USERNAME:
-
Select one or more ESXi hosts that share the same credentials and select Import Credentials.
-
Select the file that you want to import and select Continue.
-
Review the summary on the Discovered page.
-
Select Apply.
If you do not add the credentials, then you cannot run Configuration Hardening policies (assessment and remediation) against your hosts. -
After you have added the credentials, you can enable Global PIP. Global PIP is disabled by default. For more information, see Enable Global PIP.
-
Select Continue.
-
Select Done to view the dashboard for the newly added vCenters.
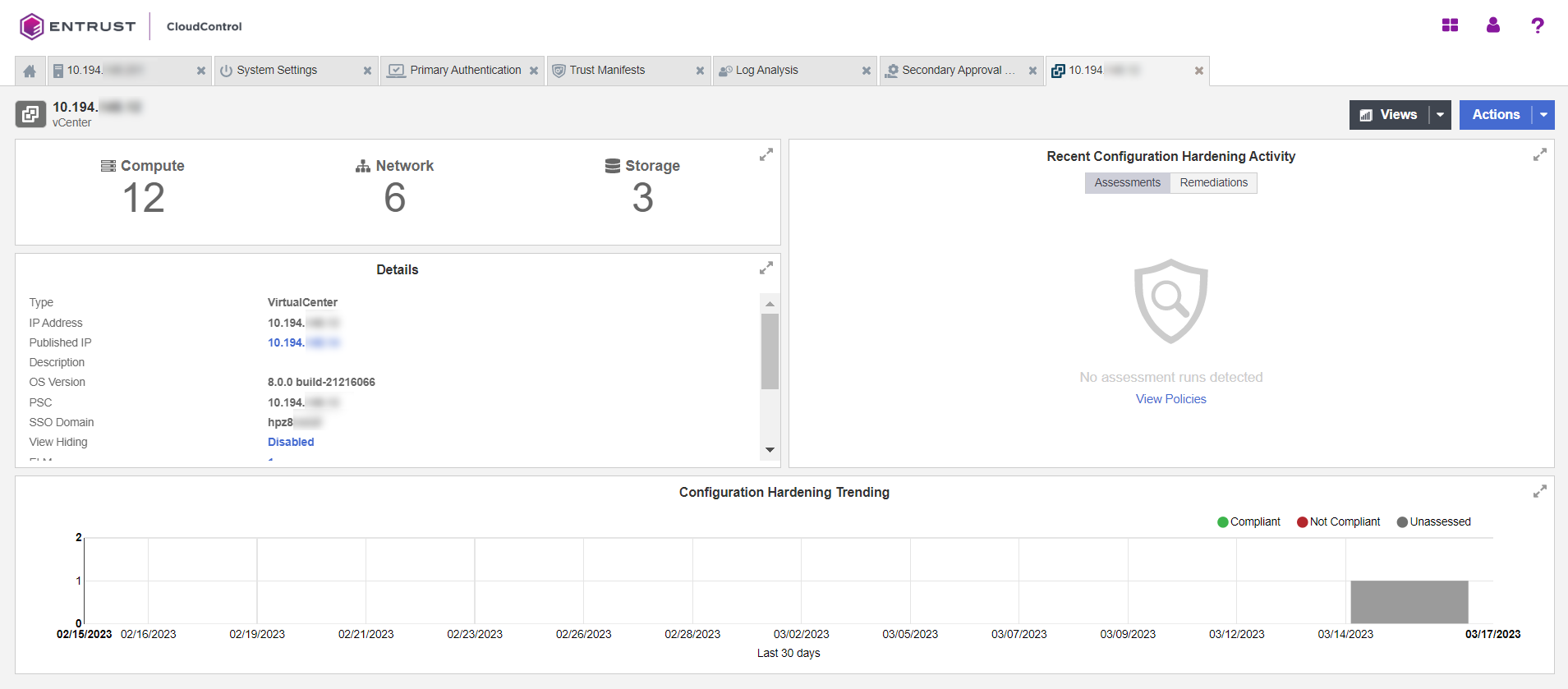
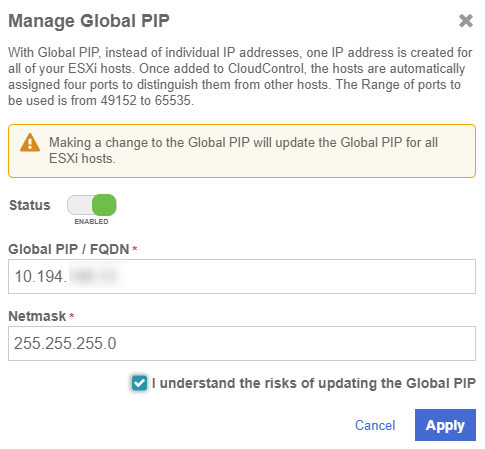
Enable Global PIP
-
From the Home tab, select Inventory > vSphere.
-
On the vSphere page, select the Compute link.
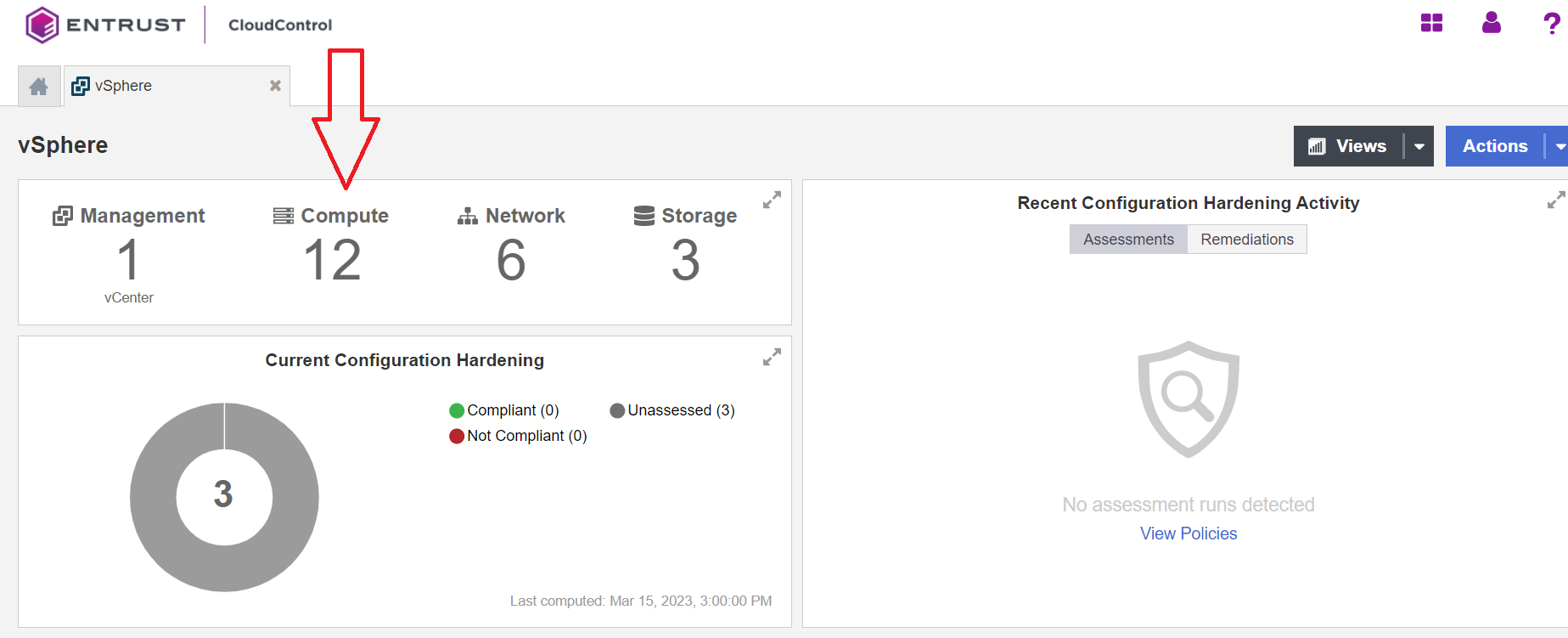
-
On the Compute tab, select the Hosts link.
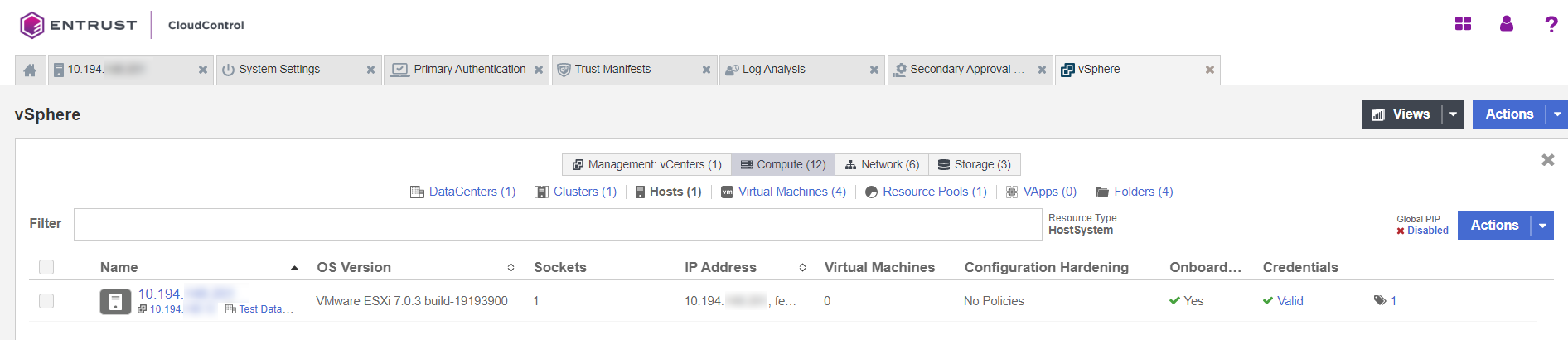
-
On the Hosts page, next to the Actions button, select the Global PIP Disabled link.
-
Alternatively, you can select one or more hosts and select Actions > Manage Global PIP.
-
In the Manage Global PIP window, do the following:
-
Set the Status to Enabled.
-
For Global PIP / FQDN, enter the IP address or FQDN to use for the Global PIP.
-
Enter the Netmask.
-
Check the confirmation checkbox.
-
Select Apply.
-
Global PIP is now enabled for all hosts that have been added to CloudControl.
Select Download CSV to download a CSV file that contains the details of all assigned ports.
Follow the online documentation to view the assigned ports for Global IP.
| For more details, view the online documentation on Enabling Global PIP. |
Add local users to the system
If you are not using AD, you can add local users to the system so they can be used to log in to vCenter and ESXi hosts using the Published IP address for the vCenter and GPIP for the ESXi hosts.
To create a local user to the following:
-
From the Home tab, select System > Primary Authentication.
-
Select the Add button.
-
In the Add Local User window, fill the information accordingly:
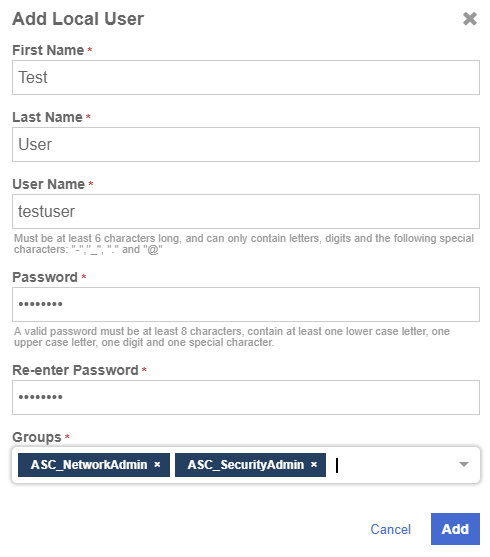
| You can select one or more groups for the user. |
For more details, view the online documentation on Adding Local Users.
Test the vCenter Published IP (PIP) and ESXi Hosts Global IP (GPIP) address and ports
vCenter Published IP (PIP)
Once the vCenter Published IP is set/enabled, you can test it by pointing your browser to:
https://PIPESXi Global IP (GPIP) and ports
When you know the ports that were assigned when you enabled GPIP, you can log in to any ESXi using the GPIP and the https_port:
https://GPIP:https_portMore information
Check the online documentation for more details on connecting to the ESXi hosts using the GPIP.
If CloudControl is not in AD mode, use one of the local users in CloudControl. If local users have not been created you can use the superadminuser local account with the password set during CloudControl configuration. Initially users must be in the ASC_SuperAdmin group to be able to log in using GPIP and PIP. You can change this when you implement your own access control policy.
Configure email
It is important to setup your email settings so the system can provide notification to users when required. Your SMTP and email information settings are configured during installation. You can modify them at any time.
-
From the Home tab, select System > System Settings.
-
On the System Settings page, select Settings > Email.
-
On the Email page, select ON or OFF to enable SMTP.
-
Fill in the information according to your settings:
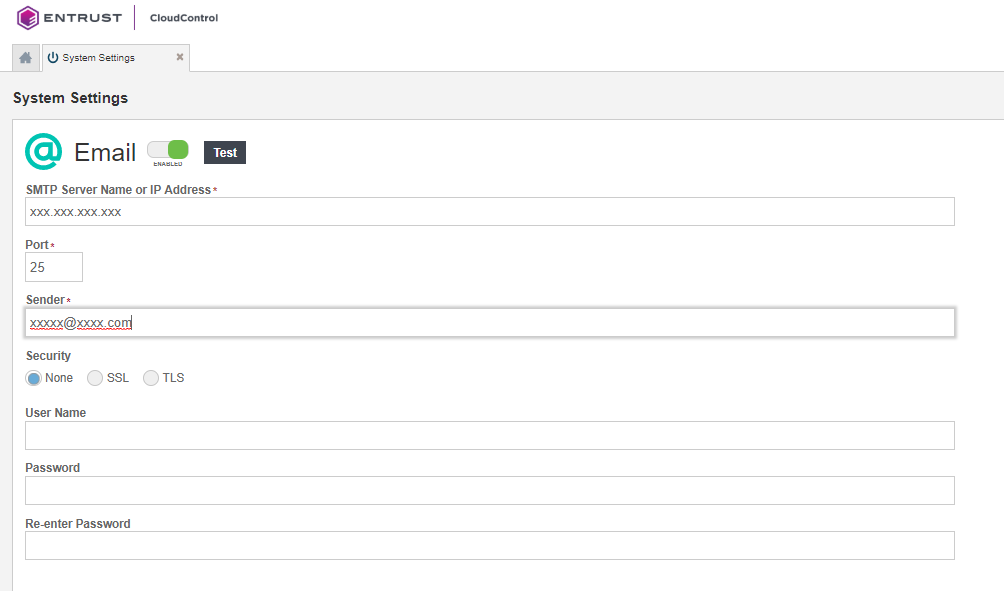
Check the online documentation for more details on how to modify your email settings.
| Email notification to users is only available when Active Directory settings are enabled. This integration was performed with local users. Active Directory was not configured. |
View the vSphere inventory
Now that the VMware inventory has been catalogued by CloudControl, check the online documentation on Viewing the vSphere Inventory inside CloudControl.
Logs
You can look at the logs in the system in the following places:
-
Log Analysis.
-
System Logs.
Log analysis
Go to the Home tab, select Security > Log Analysis.
Check the online documentation for more information on log analysis.
System logs
To view the system logs page, from the Home tab, select System > System Logs.
Check the online documentation for more information on system logs.
Access Control
This section will show how you can use an Access Control Policy to control access to VMware resources in the system. This example creates an access control policy that will allow anyone that belongs to the ASC_NetworkAdmin or ASC_SuperAdmin group to log in to ESXi hosts in CloudControl. Anyone that doesn’t belong to these groups will be denied access. Keep in mind that you also can use tags to constrain the access control policy to only resources that have the specified tags.
Users
Three users were created in the system that will allow to implement and demonstrate the access control policy in action.
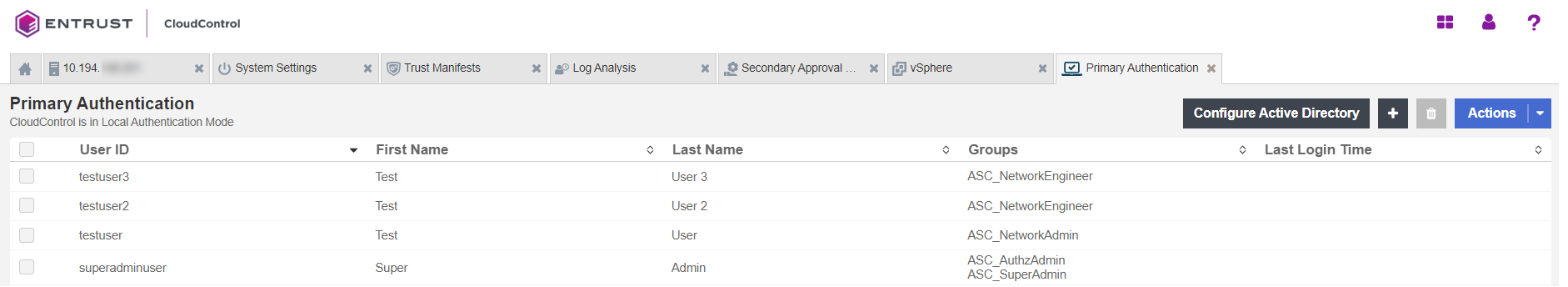
Two users belonging to the ASC_NetworkEngineer. One user belonging to the ASC_NetworkAdmin group. And lastly, the superadminuser (which already existed) which belongs to the ASC_SuperAdmin group.
Tags
Tags will not be used in the example but here is an example of how to create a tag and assign it to a resource in the system. For instance, once assigned, you could use tags to constrain the access control policy to resources that have the tag.
Check the online documentation for more information on tags.
-
Create a tag called ESXi_Host. This will be used to tag the ESXi Hosts in the system.
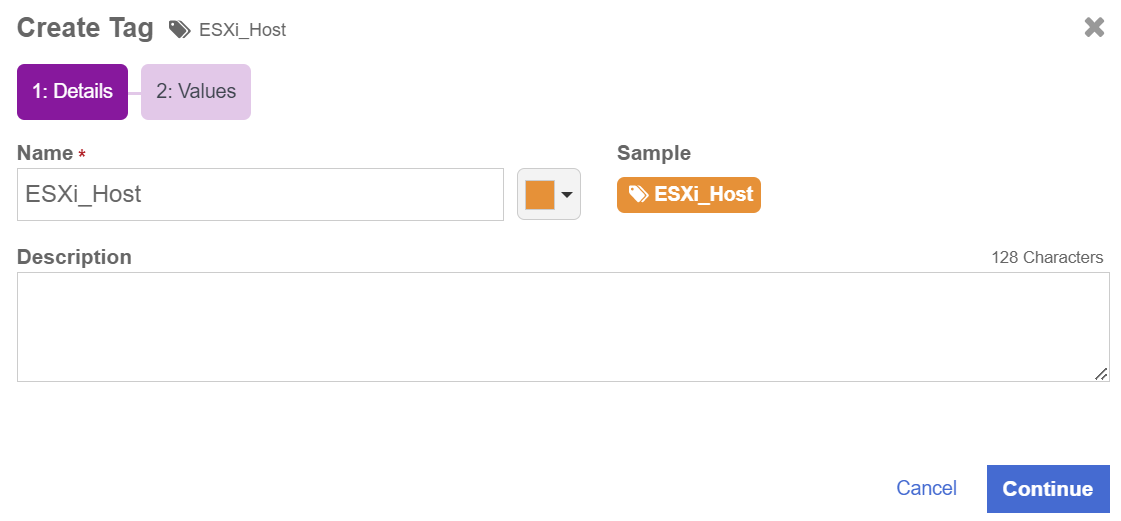
-
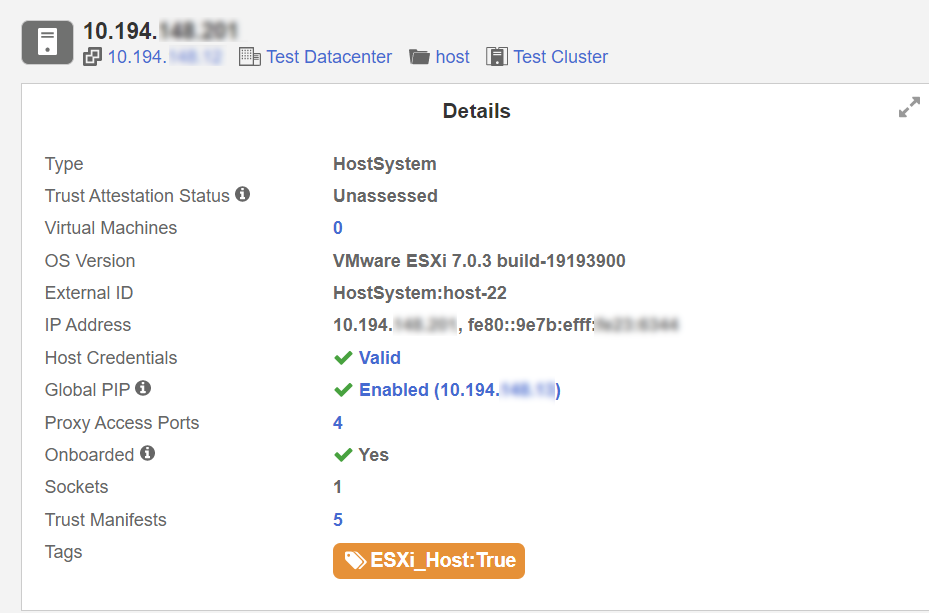
Tag the ESXi Hosts with the tag created.
-
Now tag the ESXi Hosts in the system with the ESXi_Host tag created.
Create and validate the access control policy
-
From the Home tab, select Security > Trust Manifests.
-
On the Manage Trust Manifests page, select Actions > Create Trust Manifest.
-
On the Details tab of the Create Trust Manifest page, enter the name and optional description for the trust manifest.
-
For Policy Type, select Access Control.
-
In the Access Control Policy section, create a rule for the NetworkAdmin Group:
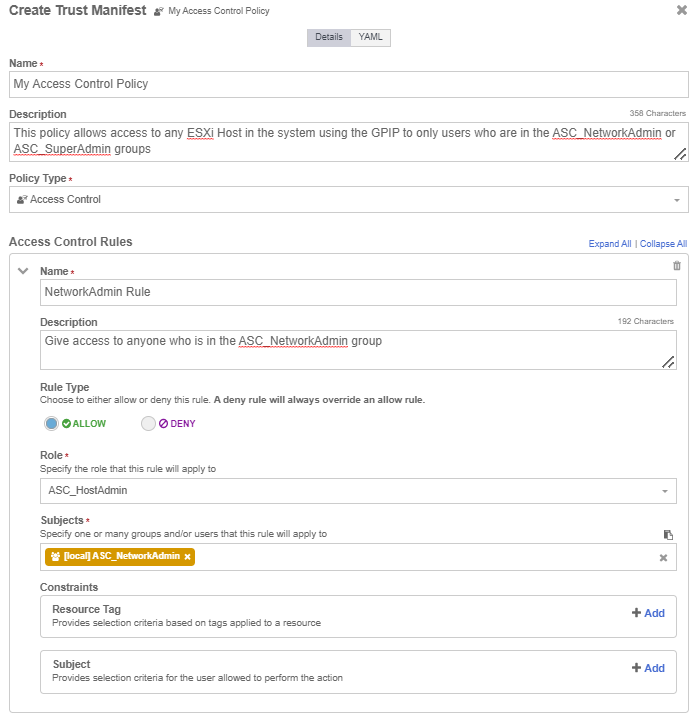
-
Select Add Another Rule and add the rule for the SuperAdmin group to the policy.
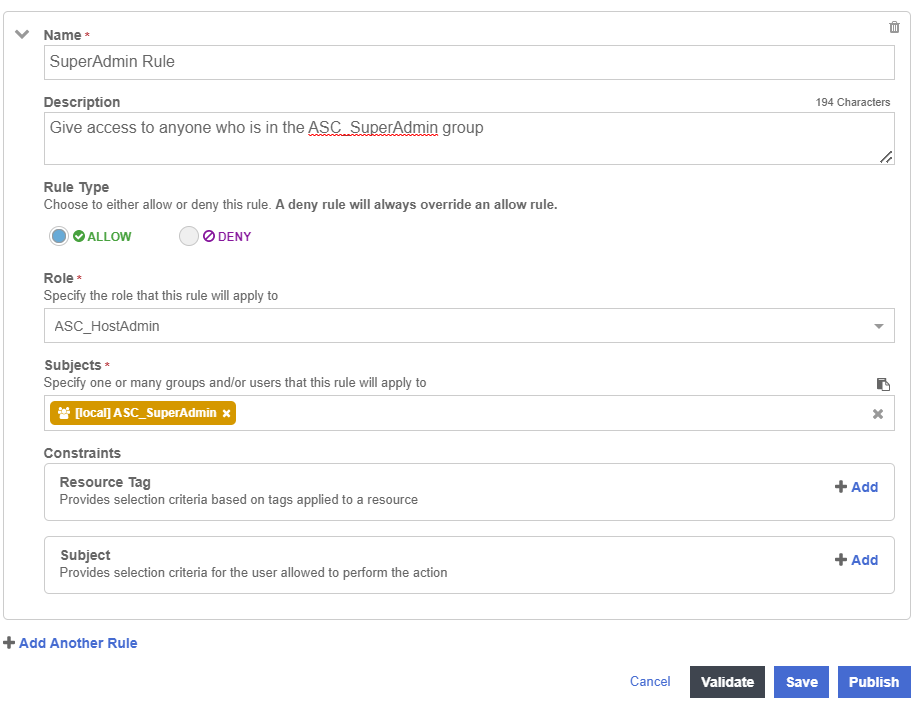
-
Select Validate to validate the policy.
-
Select Save to save the policy.
-
Select Publish to publish the policy When you publish the policy it will ask you to assign resources to the policy. Select host and select Assign.
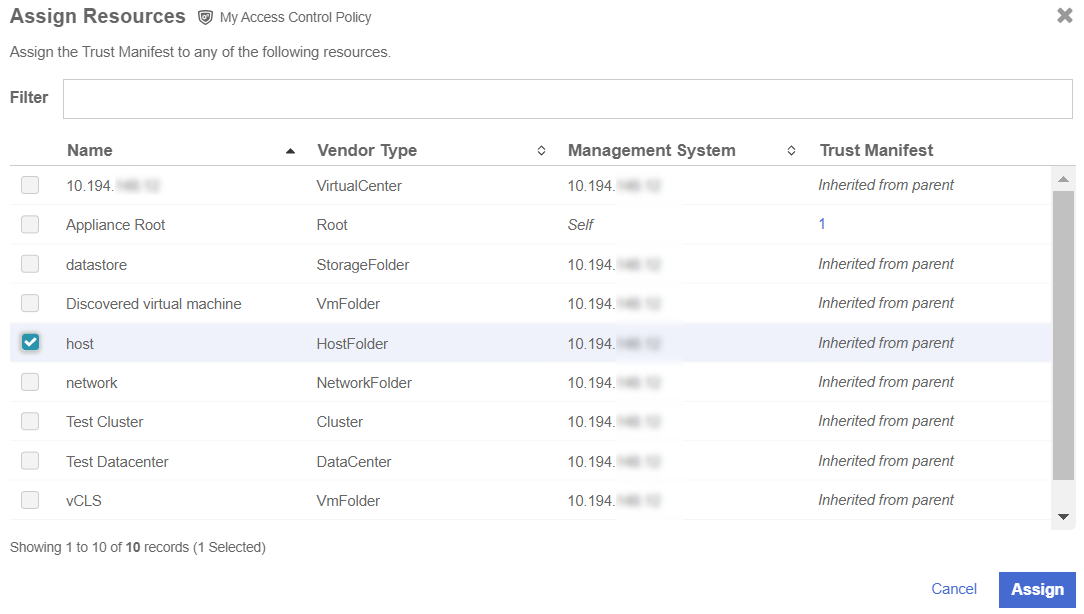
-
Select Close.
Check the online documentation for more details on Creating an Access Control Trust Manifest from the CloudControl GUI.
Test the Access Control Policy
When the access control policy is in place, point your browser to the GPIP address of the ESXi host and see if you can log in.
-
Success:
Login should be successful for the superadminuser and testuser.
-
Failure:
Login should fail for the testuser2 and testuser3 local users.

Logs
You can use the Logs in the system to check why access has been denied to a user. In the example, testuser2 has been denied access. You can view the logs to see the reasons.
-
From the Home tab, select Security > Log Analysis.
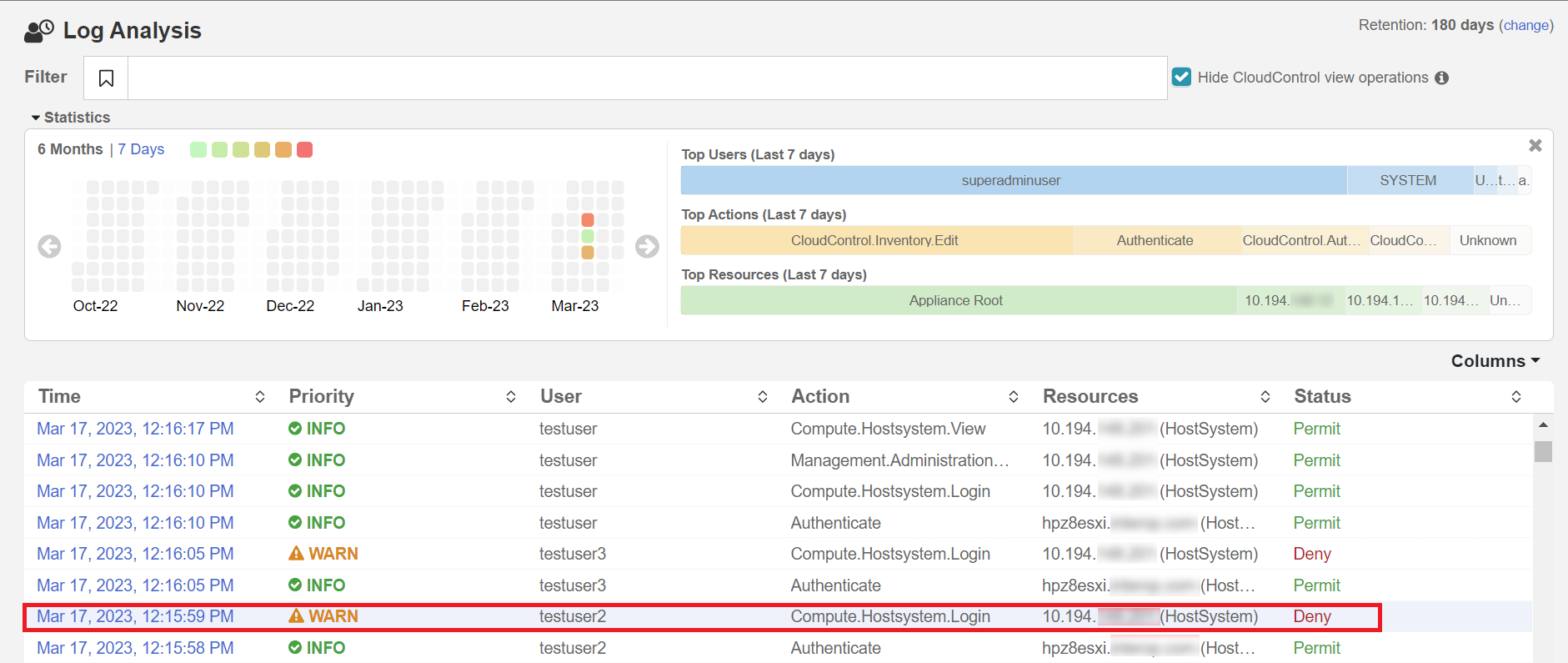
-
Select the record that shows the Deny status to see the reason for the denial.
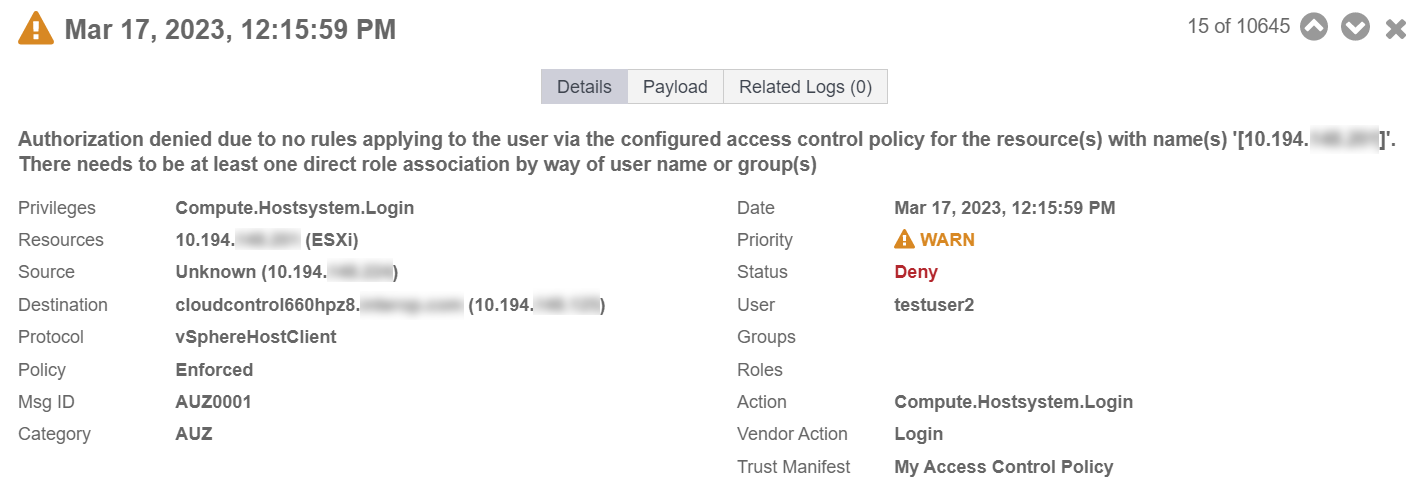
-
You will be able to see the My Access Control Policy was used to control the access.
Secondary Approval
Use Secondary Approval to configure CloudControl to require additional approval before users can perform selected disruptive operations on a resource. For example, you can require secondary approval before deleting or powering off a virtual machine or vApp, editing a firewall, or creating an Edge gateway service.
When a user attempts to perform a vSphere operation that requires secondary approval, the operation fails with a notification that secondary approval is required, and that a request was generated.
| If you have SMTP configured, and the users or groups have an email address in AD, then email messages are generated. |
This example will require the user testuser a secondary approval to log in to any ESXi host.
Create a Secondary Approval Trust Manifest from the CloudControl GUI
-
From the Home tab, select Security > Trust Manifests.
-
On the Manage Trust Manifests page, select Create Trust Manifest (The Plus sign in the GUI).
-
On the Details tab of the Create Trust Manifest page, enter the name and optional description for the trust manifest.
-
For Policy Type, select Secondary Approval.
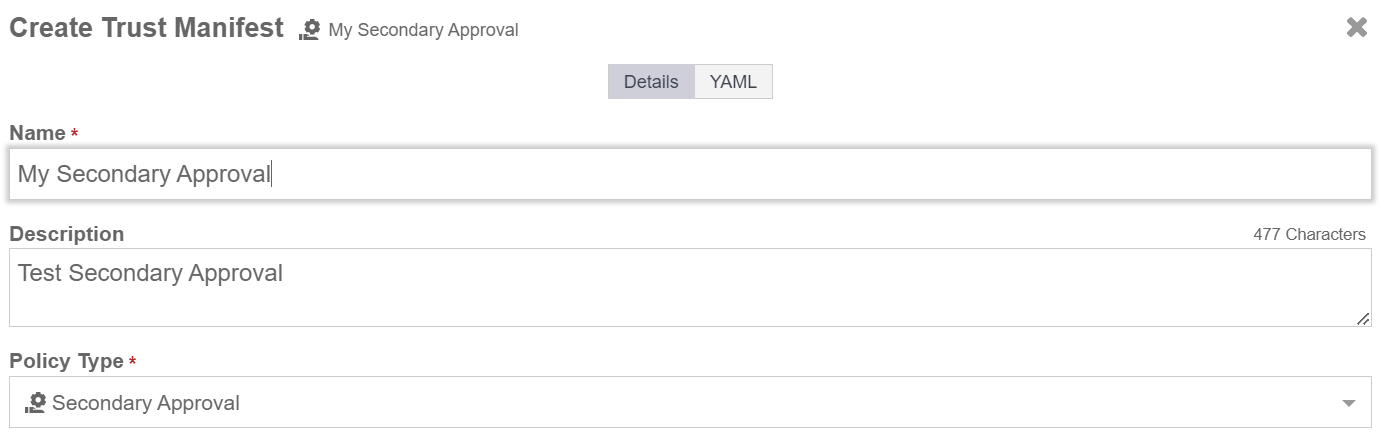
-
In the Secondary Approval Policy section, complete according to the image below:
-
Select the testuser as the subject.
-
Select the superadminuser as the approver.
-
Select the Compute.Hostsystem.Login as the operation.
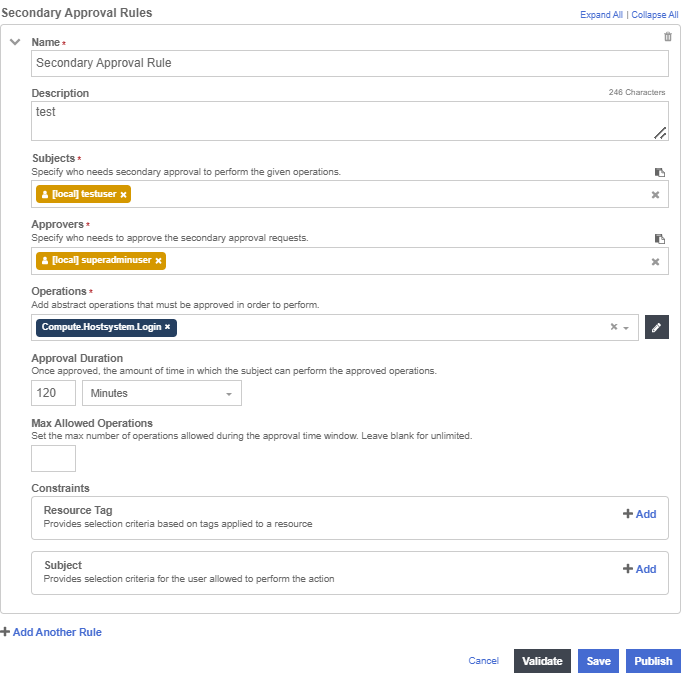
-
-
Publish the policy.
-
When you publish the policy you must assign resources to it. Select host as the resource. This will make policy applicable to any ESXi host in the system.
Validate Secondary Approval Policy
When the secondary approval policy is in place, point your browser to the GPIP address of the ESXi host and see if you can log in. Log in with the user that you used in the policy definition. The attempt should fail.

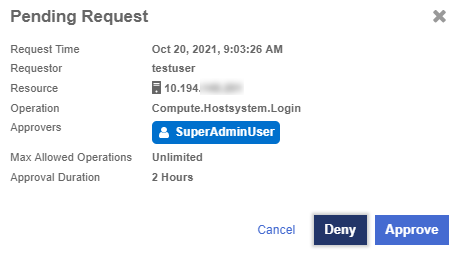
Approve the secondary approval request
Approve the secondary approval so that the user can log in to the ESXi Host.
-
From the Home tab, select Security > Secondary Approval Requests.
-
On the Secondary Approval Requests page, select a tab to view Pending or All requests.
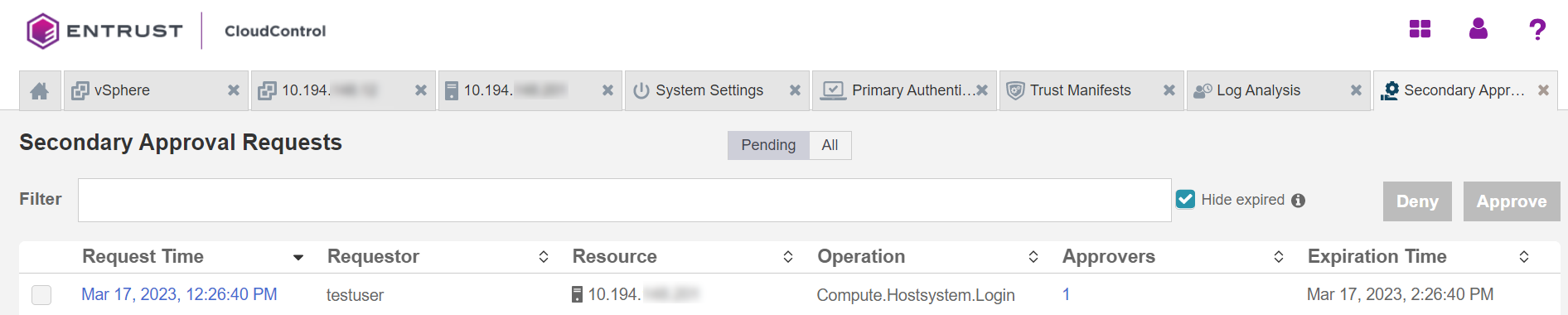
-
(Optional) Select Approve for a pending request to approve the request.
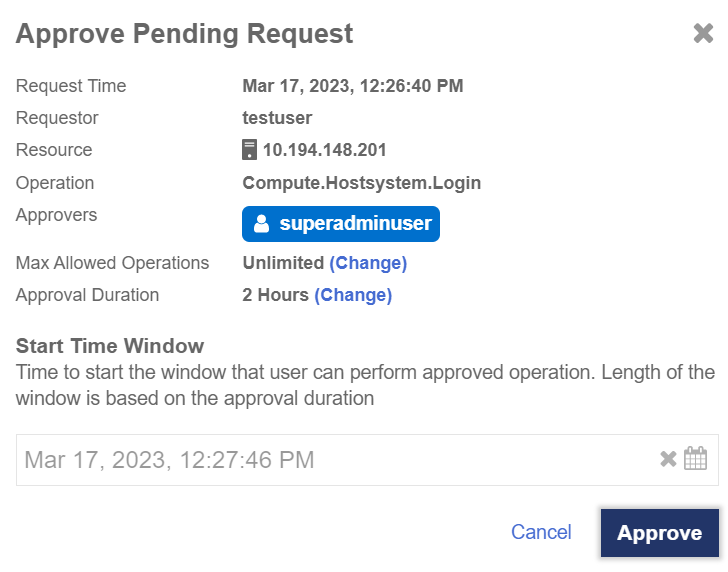
-
(Optional) Select Deny for a pending request to reject the request.
Configuration Hardening
Configuration hardening allows you to improve the security posture of your vSphere environment by hardening the configuration to meet either your company’s specific security policy, industry best practices such as CIS or NIST, or compliance standards such as PCI or HIPAA. By automating the hardening process, you can reduce your operational burden during a compliance audit.
With CloudControl, you can:
-
Create and customize templates to use in configuration hardening checks.
-
Assess and remediate your environments against the configuration hardening checks defined in the templates.
-
Review dashboards, reports and alerts to monitor the results of assessments and remediations.
About Templates
CloudControl uses templates to support all Configuration Hardening activities. CloudControl supports the following types of templates:
-
Catalog templates—Read-only collection of hardening operations. There is a vSphere operations catalog of templates that you can use.
-
System templates—Read-only collection of operations derived from a catalog template for a given compliance standard For example, the vSphere - HIPAA Security Standards template is derived from the vSphere operations catalog template.
-
Custom templates—Templates created by users. In most cases, they are copied or cloned from existing system or catalog templates. Custom templates can be modified and used in configuration hardening policies.
| CloudControl also includes sample custom templates that can immediately be used in a policy. |
Templates can contain both assessment and remediation hardening operations. It is recommended that you review all operations in the template to ensure that any parameter values are set to those that appropriate for your infrastructure requirements.
About Policies
Configuration Hardening Policies are used to run custom templates. Each policy associates a template with one or more resources or tag-based resource configurations, and can be run manually or as a scheduled activity. Policies can either assess or remediate a resource, but cannot do both.
More information
Consult the online documentation for more information on Configuration Hardening.
Creating a Configuration Hardening Policy Example
For this guide a configuration hardening policy will be created based on one of the templates available. Enforcement will be based on a rule in the template to check and make sure the ESXi vSphere version is at least version 7 and above.
-
From the Home tab, select Security > Configuration Hardening.
-
On the Configuration Hardening Management page, select the Policies tab.
-
Select the Create (+) button.
-
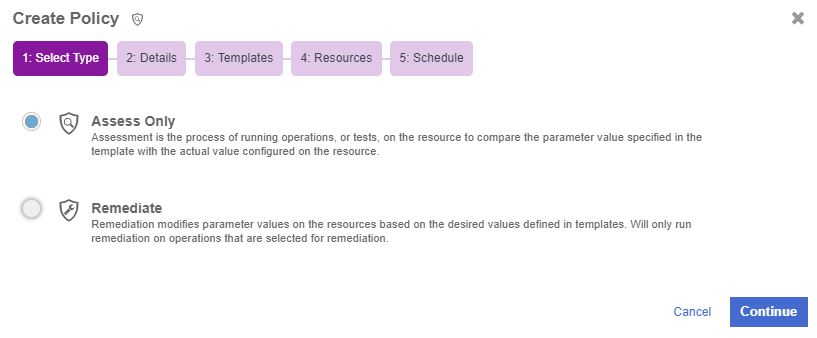
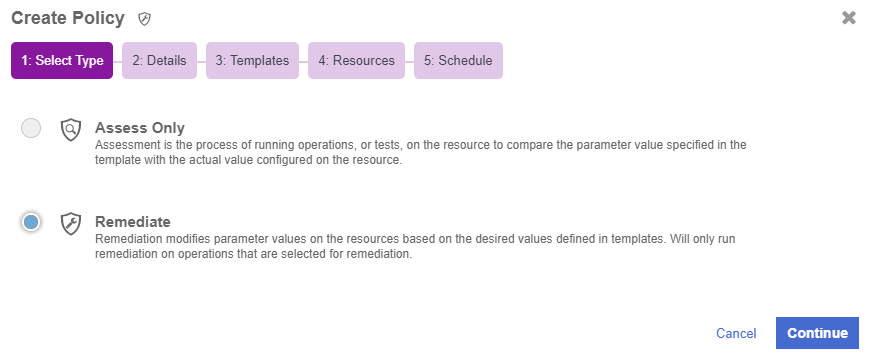
In the Create Policy wizard on the Select Type page, select the type of policy that you want to create. This can be one of the following:
-
Assess Only - Runs operations on the host to compare the parameter values specified in the template with the actual values on the host.
-
Remediate Only - Modifies the parameter values on the host in order to match the values specified in the templates.
-
-
Select Assess Only.
-
Select Continue.
-
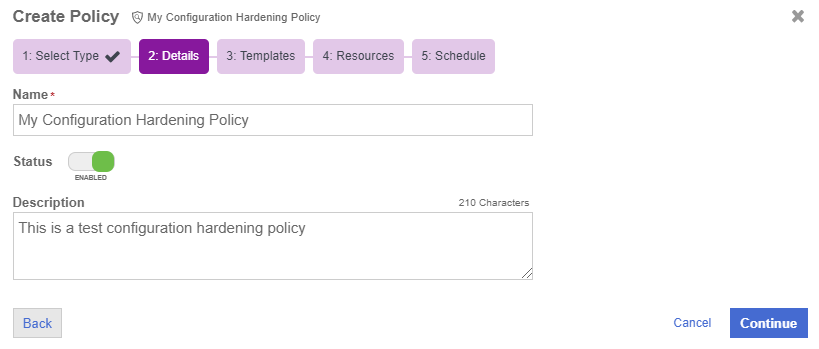
On the Details page, enter the name and optional description of the policy, and specify whether the policy is enabled.
-
Select Continue.
-
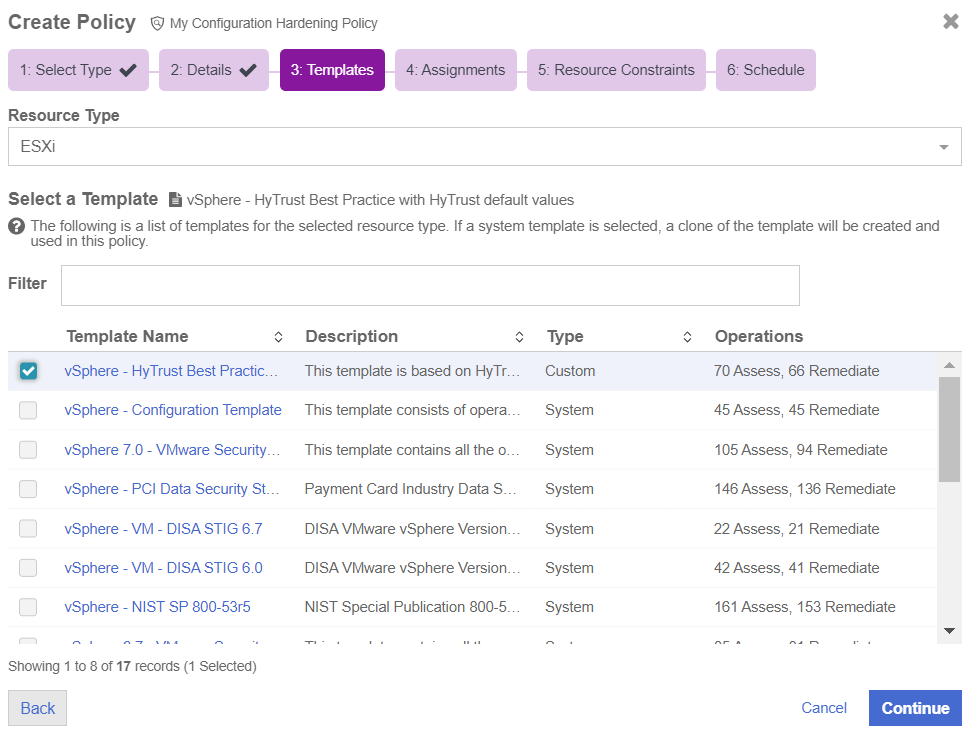
On the Templates page, select the resource type for the policy. This can be one of the following:
-
AWS Account - Runs AWS-related templates against your AWS environment.
-
ESXi - Runs vSphere related templates against your ESXi hosts.
-
Kubernetes - Runs Kubernetes related templates against your Kubernetes environment.
-
NSXDataCenter - Runs NSX-T related templates against your NSX-T environment.
-
-
Select ESXi as the template to run against your environment.
-
The template list displays the name, description and type of operations Select a template that contains the type of operations that you selected for the policy.
-
Select vSphere - HyTrust Best Practice template. This template is used in the example.
See the online documentation for more information on Creating a Custom Template. -
Select Continue.
-
On the Assignments page, select one of the following and choose what resources to which you want to apply the policy:
-
Tags - Select the Tags radio button and then choose a tag or tags assigned to the resource. Select the + icon if you want to assign more tags to the resource. If there are no tags assigned, you can select the Assign Tags Now link.
-
Resources - Select Specific Resources and then choose one or more resources.
For vSphere only, you can choose a parent for the resource type. This can be one of the following:
-
vCenter - Allows you to select all ESXi hosts in the selected vCenter. All onboarded ESXi hosts in the selected vCenter will be considered for hardening. You can select multiple vCenters. When the Configuration Hardening policy is run, CloudControl retrieves all onboarded ESXi hosts from the vCenter inventory to ensure the list of ESXi hosts is always current.
-
Appliance Root - Allows you to select all ESXi hosts under Appliance Root. All onboarded ESXi hosts will be considered for hardening. When the Configuration Hardening policy is run, CloudControl retrieves all onboarded ESXi hosts from the vCenter inventory to ensure the list of ESXi hosts is always current.
-
DataCenter - Allows you to select all ESXi hosts in the selected DataCenter. All onboarded ESXi hosts in the selected vCenter will be considered for hardening. You can select multiple DataCenters. When the Configuration Hardening policy is run, CloudControl retrieves all onboarded ESXi hosts from the vCenter inventory to ensure the list of ESXi hosts is always current.
-
Cluster - Allows you to select all ESXi hosts in the selected Cluster. All onboarded ESXi hosts in the selected Cluster will be considered for hardening. You can select multiple Clusters. When the Configuration Hardening policy is run, CloudControl retrieves all onboarded ESXi hosts from the vCenter inventory to ensure the list of ESXi hosts is always current.
-
ESXi Host - Allows you to choose which individual ESXi hosts that you want to use as a resource. If additional ESXi hosts are onboarded, they will not be included.
-
-
-
Select Tags for the resources you want to apply the policy.
-
Select the Assign Tags to Policy Now link to select the tags.
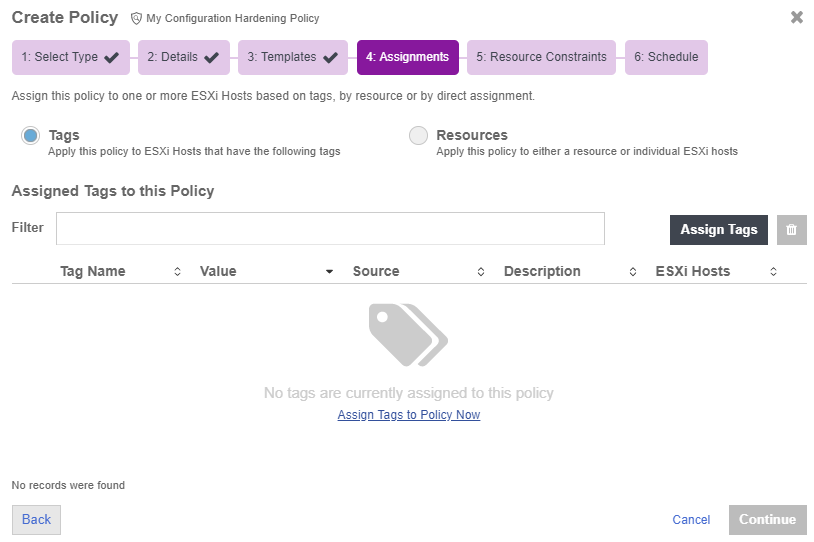
The Assign Tags dialog appears.
-
Select the ESXi_Host tag created earlier.
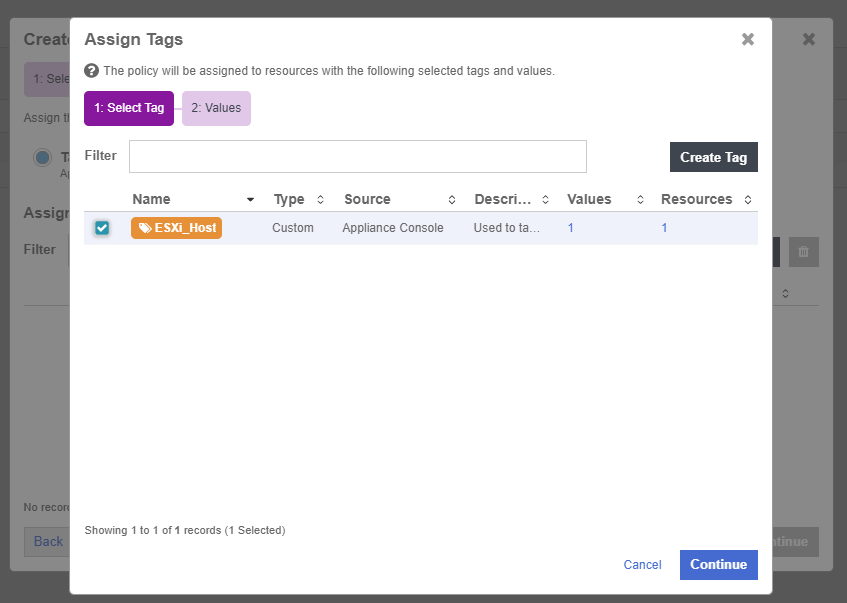
-
Select Continue.
-
Select the Tag value True that applies to the ESXi_Host tag.
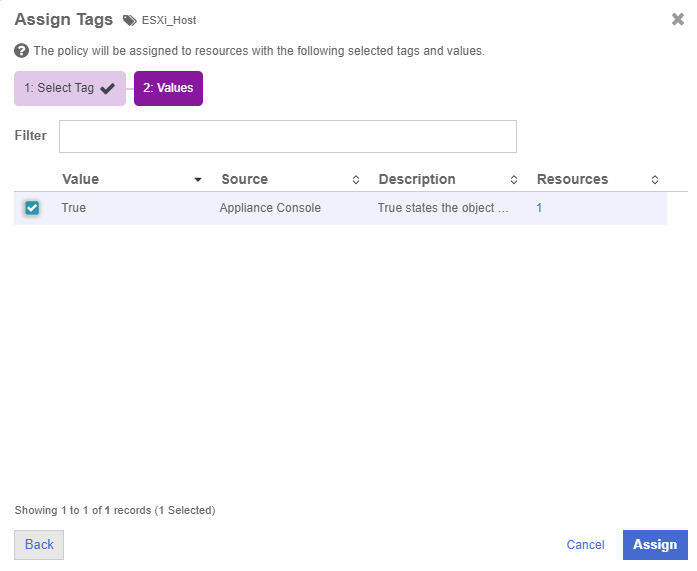
-
Select Assign.
-
Select Continue.
-
(Optional) For vSphere only. On the Resource Constraint page, choose which tag-based resource constraints that you want to use for your ESXi hosts. This option is not described in detail.
-
Select Continue.
-
On the Schedule page, select if you want to enable a recurring schedule.
If enabled, select the type of schedule that you want to use to run the policy, and then specify the start date. This can be one of the following:
-
Daily - The policy will run every day at the time that you specify.
-
Hourly - The policy will run periodically throughout the day, based on the schedule you define.
-
Weekly - The policy will run on every day that you select at the time that you specify.
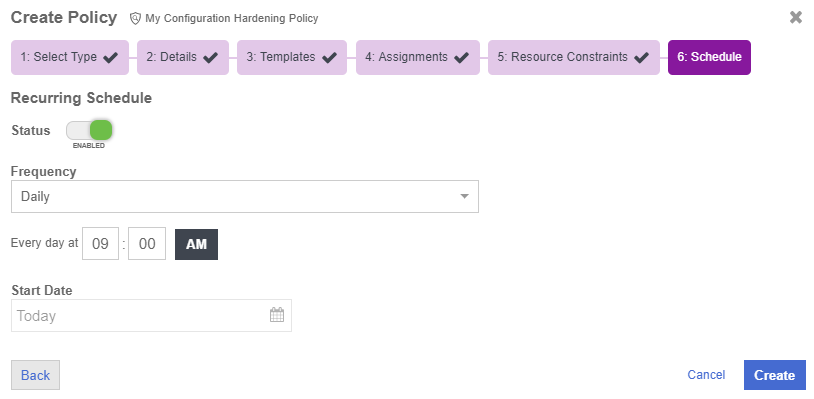
-
-
Select Create.
-
The newly created policy will be displayed on the Policies tab.
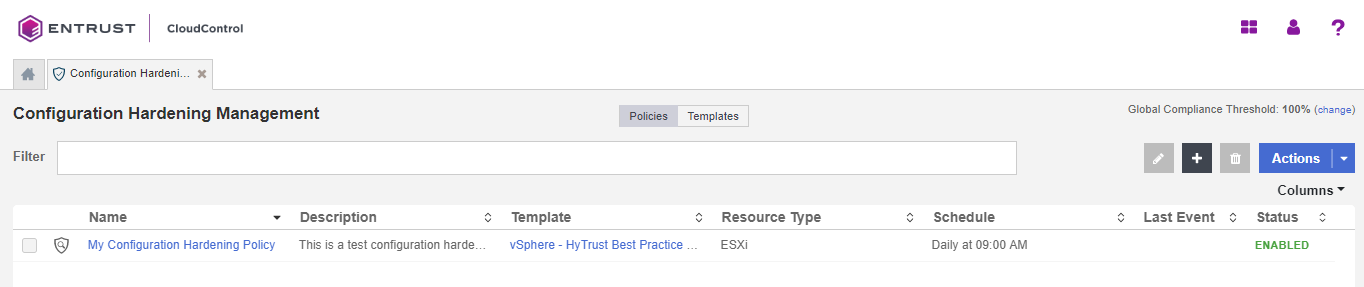
-
Edit the Check ESXi Patch Version Rule in the template. Select the vSphere - HyTrust Best Practice link in the Template Column. The template details appears.
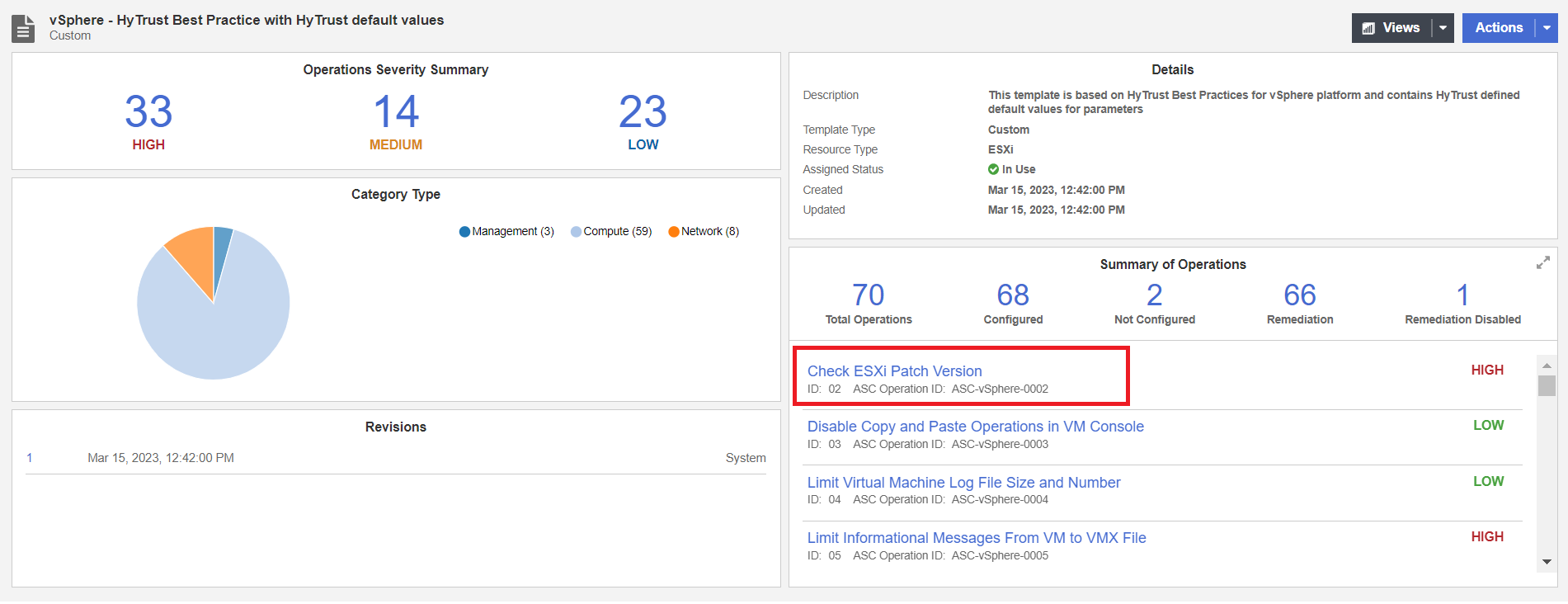
-
Under Summary of Operations look for Check ESXi Patch Version.
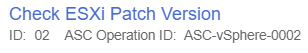
-
Once you find it, select the Check ESXi Patch Version link to edit the rule.
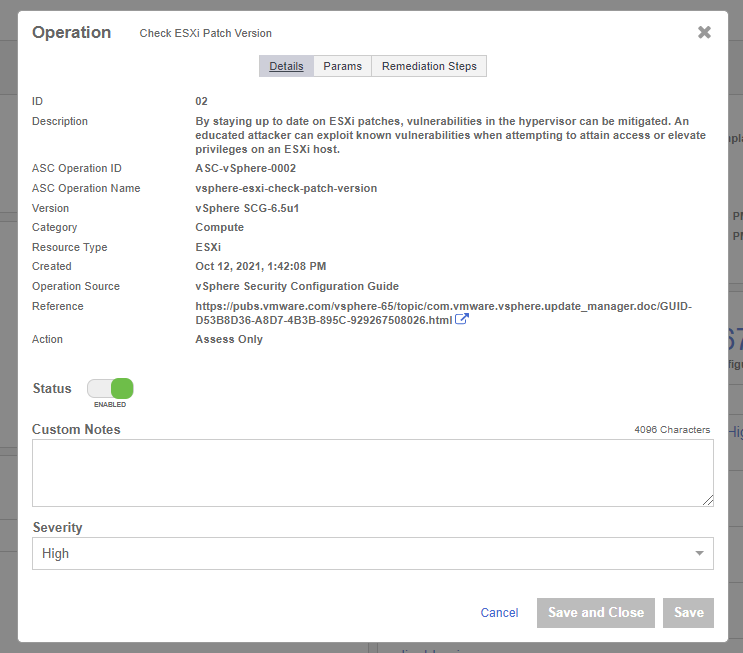
-
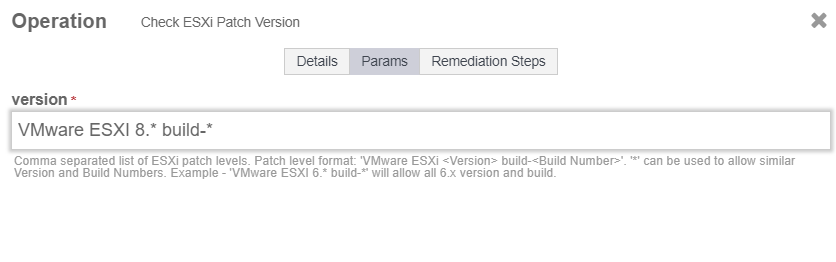
Select the Params tab and enter the version according to the image below.
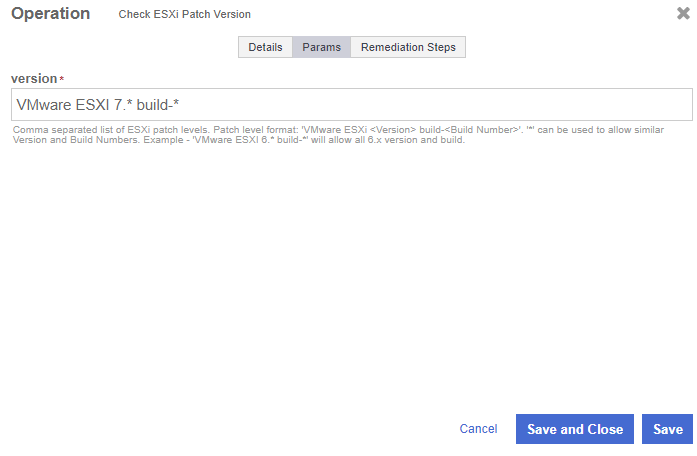
-
Select Save and Close.
Now when the Configuration Hardening Policy runs, this rule will check to see if the version of the ESXi Host will match what is on the version field of the rule.
When you run a remediation policy, the assessment policy will automatically run immediately following its completion. This ensures that your compliance score is updated with the new percentage.
-
From the Home tab, select Security > Configuration Hardening.
-
On the Configuration Hardening Management page, select the Policies tab.
-
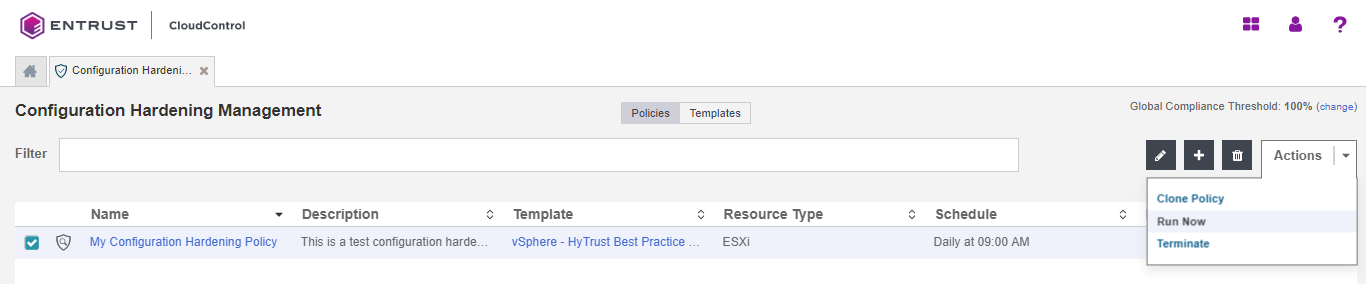
Select the Policy that you want to run.
-
Select Actions > Run Now.
-
In the confirmation window, select Run Now.
-
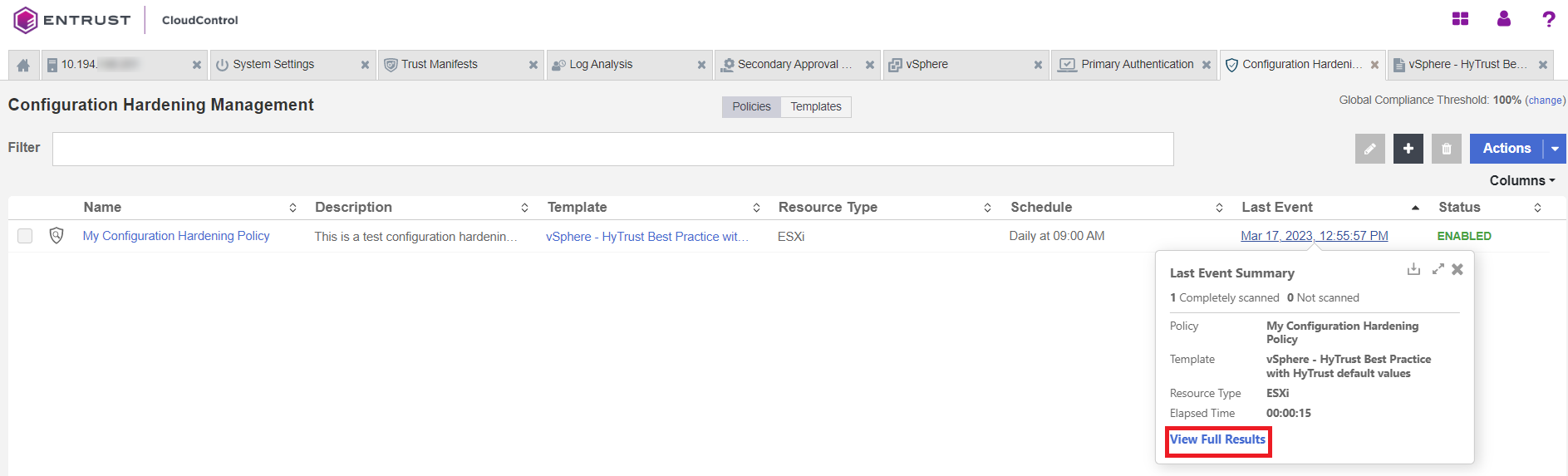
You can view the results by selecting the link in the Last Event column.
-
Select View Full Results.
-
In the Last Event Summary Tab, select Resource.
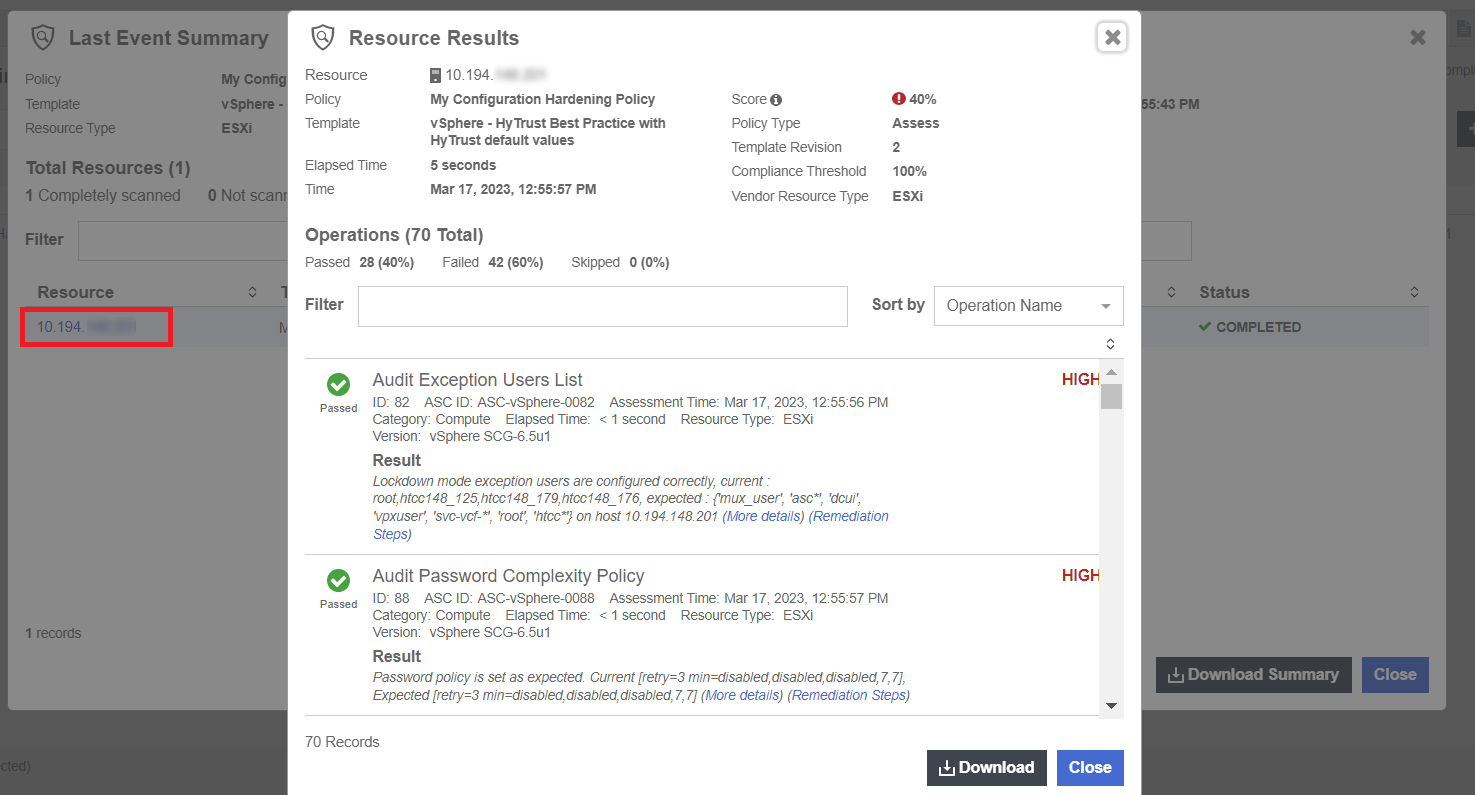
If you used resource constraints on your ESXi hosts, you can see which hosts were analyzed and which were skipped. -
As you look to the results, you will be able to see that the ESXi Version test that was in the policy, Passed.
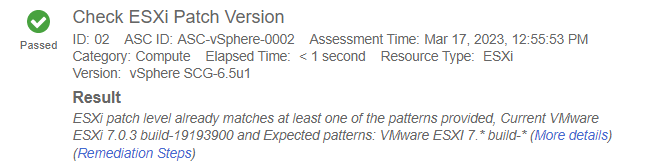
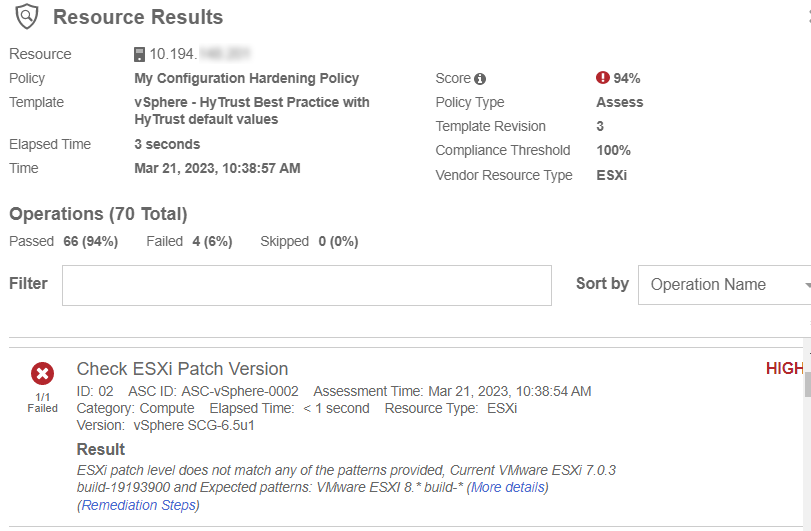
If you enter the incorrect version in the Check ESXi Patch Version Params, the Configuration Hardening Policy will catch the failure. For example, if you enter VMware ESXi version 8 instead of 7:
When you run the Configuration Hardening Policy, the system will catch the error and report a failed result.
Remediation Policy
Now that the Configuration Hardening Policy has been created, the same process will be used to create a Remediation Policy. The process is basically the same, with the exception that instead of selecting Assess Only as the type, the Remediate type will be selected during the policy creation process.
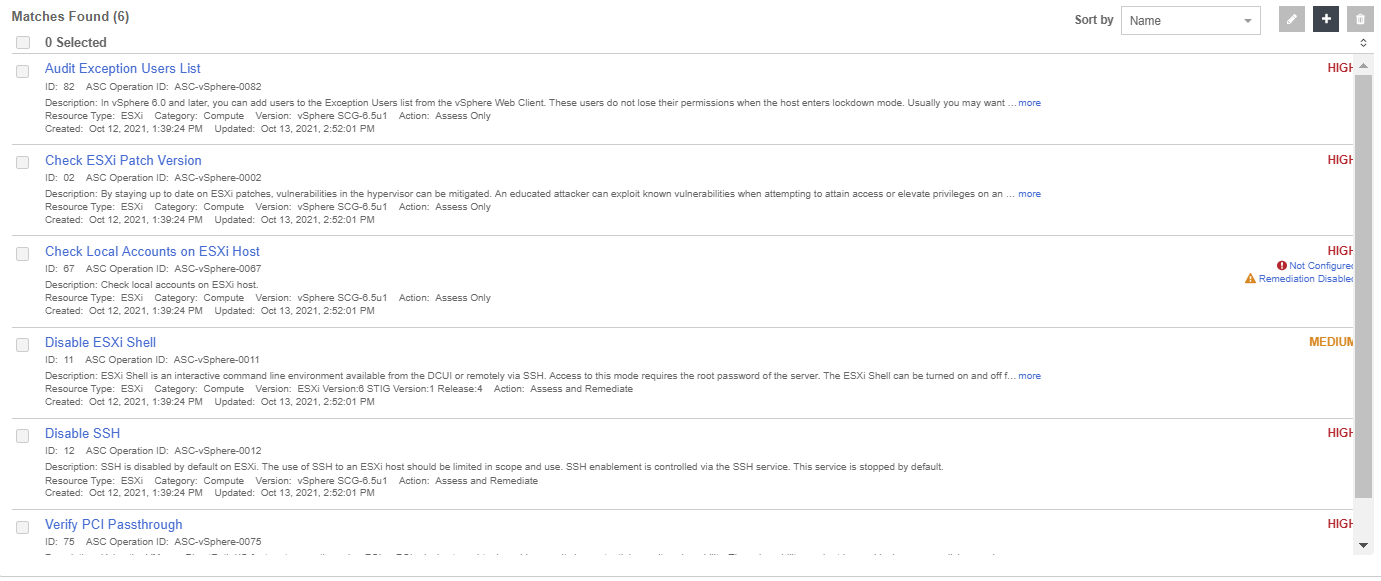
After the policy is created, edit the policy template to contain only the items you want to remediate.
You do this in the Configuration Hardening Management page, by selecting the template in the Template column of the policy you want to edit. On the Template page, under the Summary of Operations, select Total Operations. The Manage Operations page appears. This page is used to select the rules that you want in the template. You can also Add and Delete selected rules.
Now that the template has been defined with the wanted rules, perform the remediation. This example shows how to Disable SSH on the ESXi host just by running the remediation policy.
The following rules are in the template. (One of them is Disable SSH).
Before running the policy, go to the ESXi Host and validate that SSH service is running.
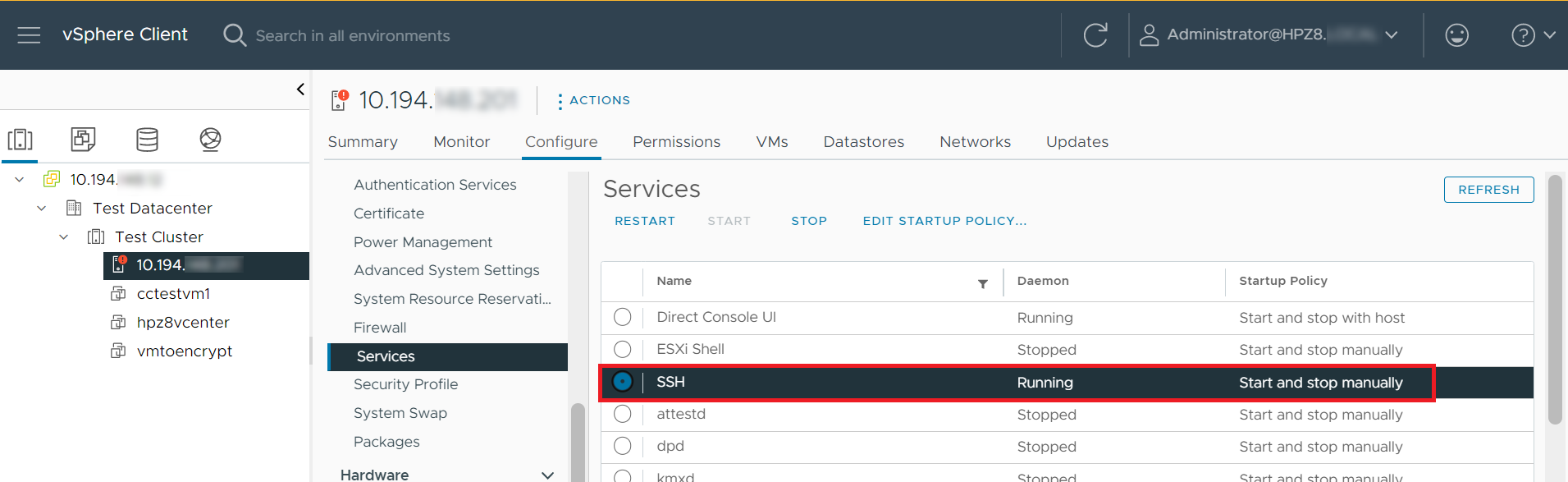
Run the remediation policy and see what happens to SSH in the ESXi Host.
In the Entrust CloudControl VM do the following:
-
From the Home tab, select Security > Configuration Hardening.
-
On the Configuration Hardening Management page, select the Policies tab.
-
Select the remediation policy that you want to run.
-
Select Actions > Run Now.
-
In the confirmation window, select Run Now.
-
Once it finishes running, you can view the results by selecting the link in the Last Event column.
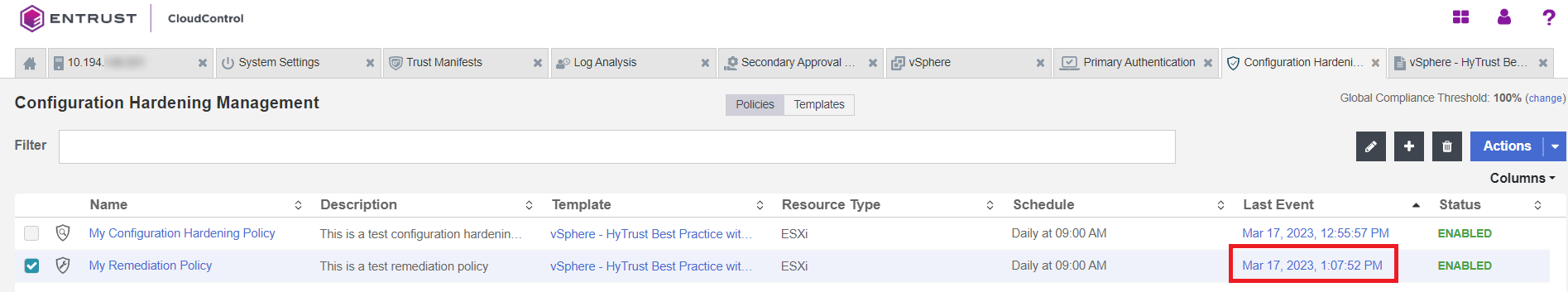
-
Locate the Disable SSH result and validate that it Passed.
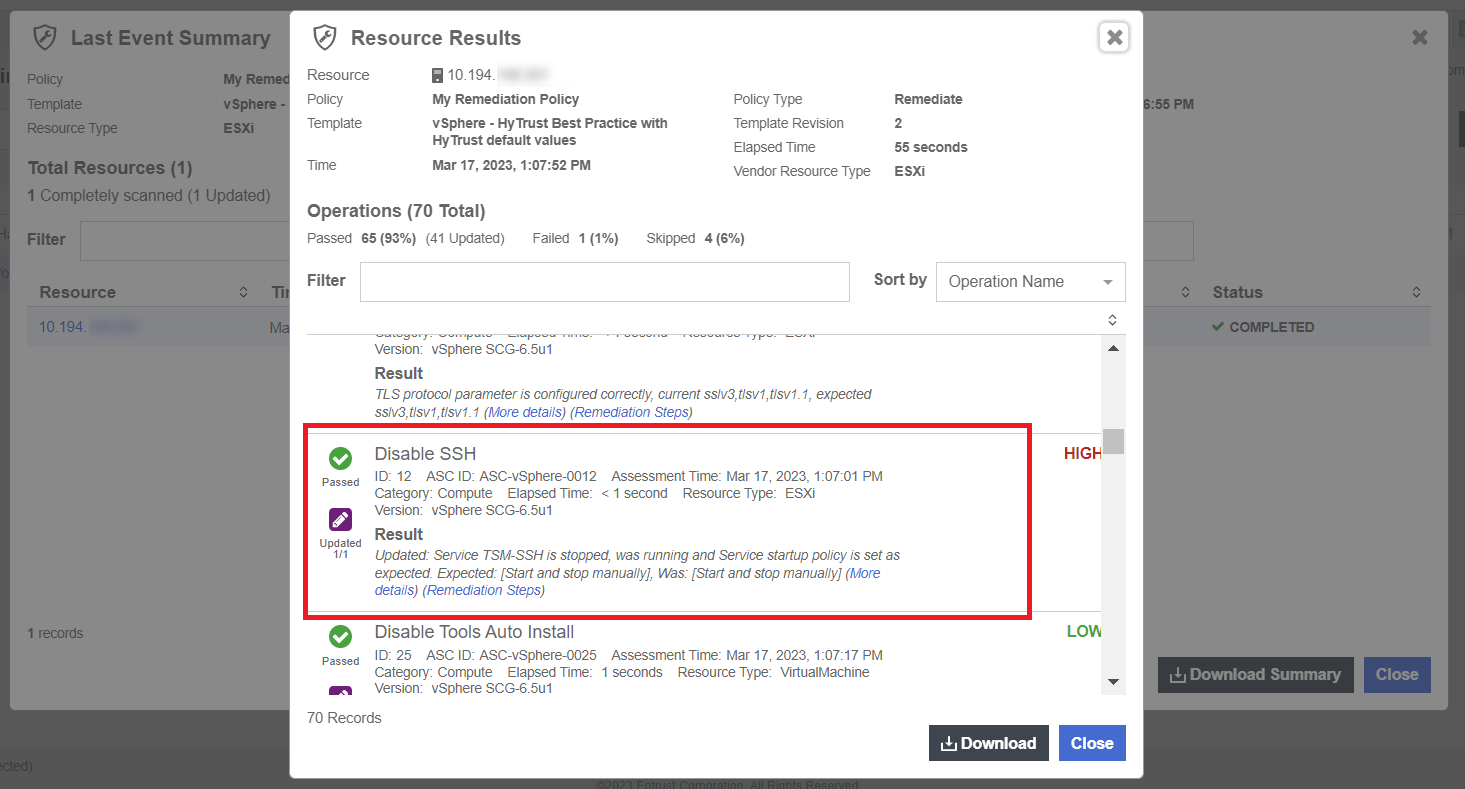
-
Now go back to the ESXi Host and check if the SSH service is running. It should be set to Stopped.
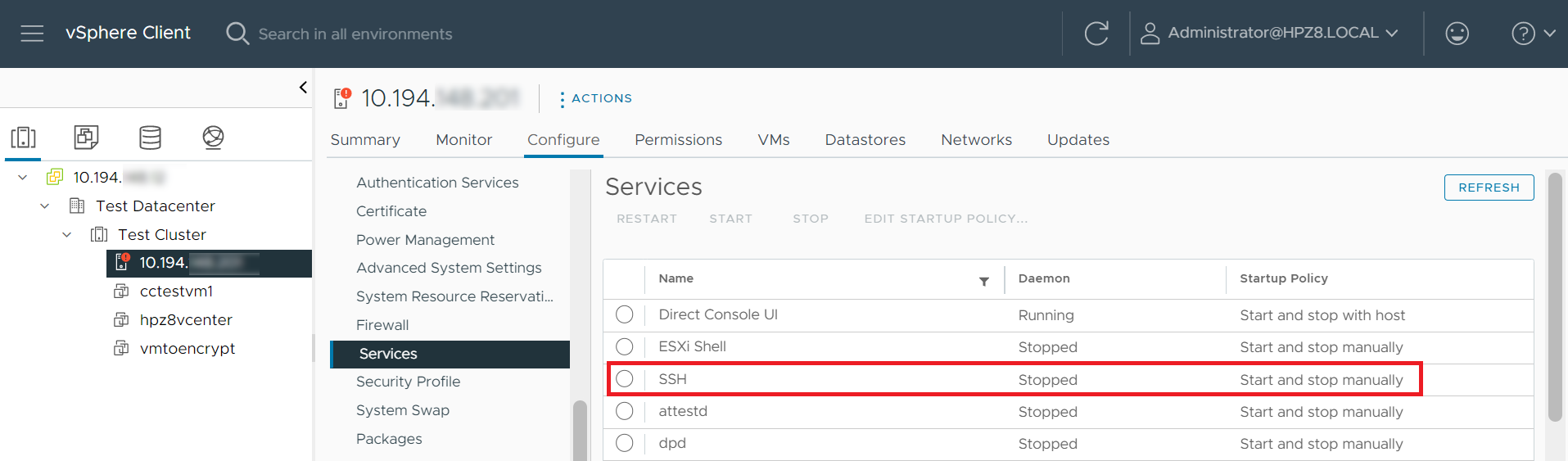
This example shows how you can use the remediation policy to automatically enforce configuration settings on your vSphere environment.