Integrate Pure Storage FlashArray and KeyControl
Configure TLS EMS in KeyControl
-
Sign in to the KeyControl Vault Server web GUI using the secroot credentials.
-
The screen should default to Appliance Management. Otherwise, in the top-right corner select Appliance Management.
-
In the toolbar, select Settings.
-
Scroll down and select TLS Configuration.
-
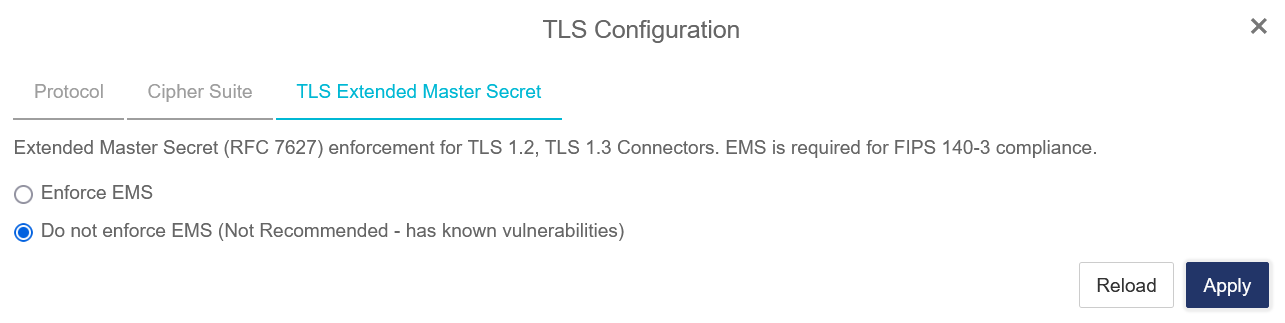
In the TLS Configuration window, select the TLS Extended Master Secret tab.
-
Select the Do not enforce EMS radio button, Then select Apply.
Configure the TLS version in KeyControl
The tested version of Pure Storage FlashArray supports TLS v1.2. Configure KeyControl accordingly.
-
Sign in to the KeyControl Vault Server web GUI using the secroot credentials.
-
In the top-right corner select Manage Vaults.
-
In the top-right corner, select Settings.
-
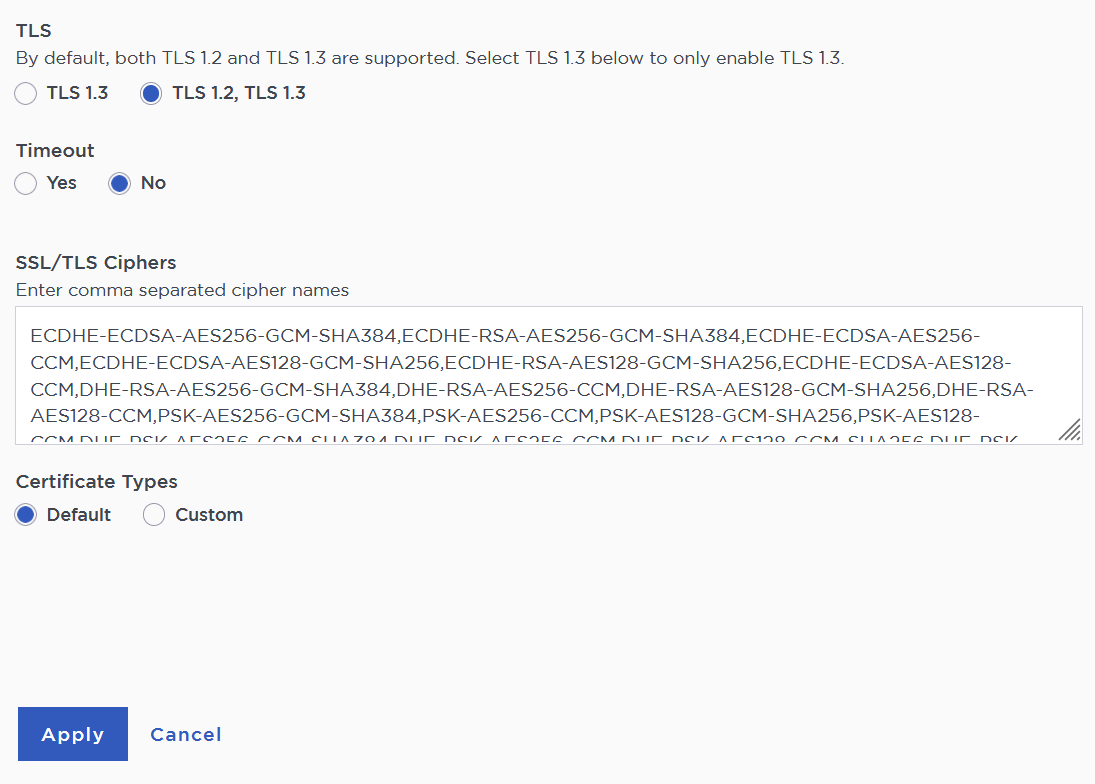
Under TLS, select the TLS 1.2, TLS 1.3 radio button.
-
Under Certificate Types, select according to your deployment, then select Apply.
Create a certificate signing request in Pure Storage FlashArray
-
Sign in to the Pure Storage FlashArray CLI with administrator privileges.
-
Create a self-signed certificate.
interop@denqamgmtscl03> purecert create entrust-kmip-cert --self-signed \ --common-name entrust-keycontrol Name Status Key Algorithm Key Size Issued To Issued By entrust-kmip-cert self-signed rsa 2048 entrust-keycontrol entrust-keycontrol Valid From Valid To Country State/Province Locality 2025-01-27 11:52:28 MST 2035-01-25 11:52:28 MST - - - Organization Organizational Unit Email Common Name Pure Storage, Inc. Pure Storage, Inc. - entrust-keycontrol -
Display the self-signed certificate created above.
interop@denqamgmtscl03> purecert list entrust-kmip-cert --certificate -----BEGIN CERTIFICATE----- MIurioqwerCgAwIBAgIEfhphKTANBgkqhkiG9w0BAQsFADBXMQswCQYDVQQGEwJV . . . I10E4uaYtxxxKYUv -----END CERTIFICATE----- -
Construct a certificate signing request (CSR).
interop@denqamgmtscl03> purecert construct entrust-kmip-cert --certificate-signing-request -----BEGIN CERTIFICATE REQUEST----- MIIC2jCCruiotwpueritoerkGA1UEAwwSZW50cnVzdC1rZXljb250cm9sMRswGQYD . . . 3i62111tOn1hZNU4ekw= -----END CERTIFICATE REQUEST----- -
Copy the above certificate into a text editor and create a
csrfile.
Create the client certificate bundle in KeyControl
The following steps describe how to import into KeyControl the csr created in Create a certificate signing request in Pure Storage FlashArray and create the client certificate bundle.
-
Sign in to the KMIP vault URL created in Create a KMIP Vault in the KeyControl.
-
Select the Security icon. Then select the Client Certificates icon.
-
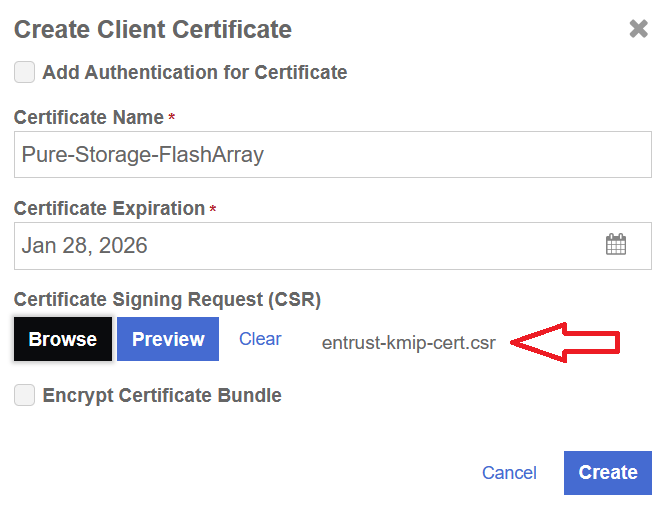
Select the + icon to create a client certificate. Enter the certificate name and expiration date, and upload the csr created in section Create a certificate signing request in Pure Storage FlashArray. Then select Create.
-
Notice the new client certificate.
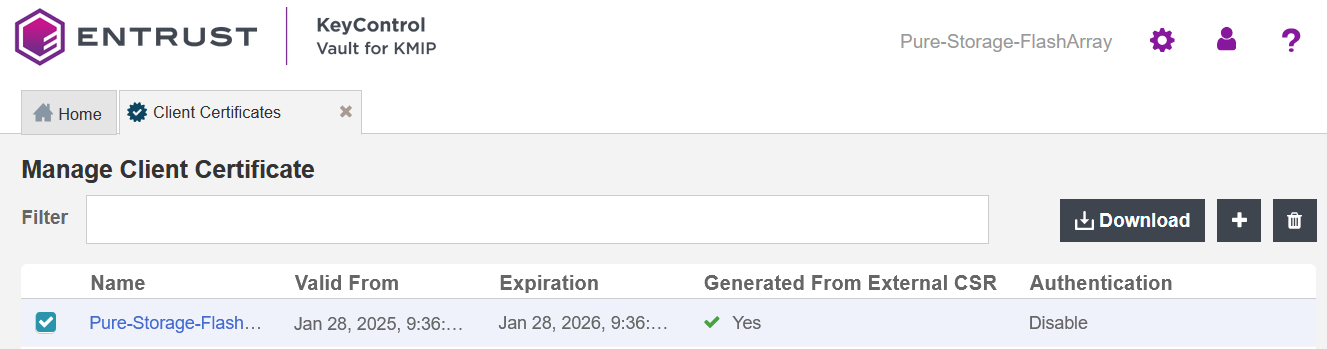
-
Select the certificate. Then select Download and save it for later use.
-
The client certificate bundle
.zipfile includes the signed client certificate and CA certificate on.pemformat.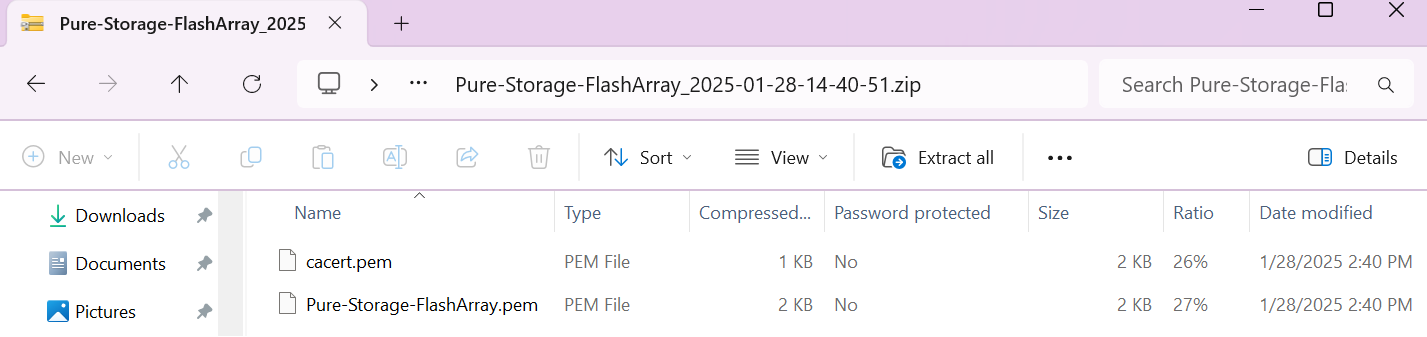
For more information, see Managing KMIP Client Certificates.
Input the client bundle into Pure Storage FlashArray
-
Sign in to the Pure Storage FlashArray CLI with administrator privileges.
-
Update the Pure Storage FlashArray certificate with the signed key details. When prompted, paste the client certificate contained within the
Pure-Storage-FlashArray.pemfile from section Create the client certificate bundle in KeyControl.The client certificate includes the lines “-----BEGIN CERTIFICATE-----" and “-----END CERTIFICATE-----" and all text between them.
interop@denqamgmtscl03> purecert setattr entrust-kmip-cert --certificate Please enter certificate followed by Enter and then Ctrl-D: -----BEGIN CERTIFICATE----- MIIDyDCCArCgRTIQOPTJKPRAwIBAgIEfhphKjANBgkqhkiG9w0BAQsFADBXMQswC . . . f+qTL000zjC9iSWa -----END CERTIFICATE----- Name Status Key Algorithm Key Size Issued To entrust-kmip-cert imported rsa 2048 entrust-keycontrol Issued By Valid From Valid To HyTrust KeyControl Certificate Authority 2025-01-29 11:52:20 MST 2026-01-28 11:52:20 MST Country State/Province Locality Organization Organizational Unit Email - - - Pure Storage, Inc. Pure Storage, Inc. - Common Name entrust-keycontrol -
Create the KMIP server configuration. When prompted, paste the CA certificate contained within the
cacert.pemfile from section Create the client certificate bundle in KeyControl.For the URI, enter the name or IP of the first KeyControl node. The CA certificate includes the lines
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----and all text between them.interop@denqamgmtscl03> purekmip create Entrust-KeyControl-KMIP-Server \ --uri 10.194.148.126:5696 --certificate entrust-kmip-cert --ca-certificate Please enter CA certificate followed by Enter and then Ctrl-D: -----BEGIN CERTIFICATE----- MIID9TC urtoiqpeurtioewCAt2gAwIBAgIEZxphGjANBgkqhkiG9w0BAQsFADBX . . . XURIE3S1a3f8u -----END CERTIFICATE----- Name URI Certificate Ca Certificate Configured Entrust-KeyControl-KMIP-Server 10.194.148.126:5696 entrust-kmip-cert True -
Update the KMIP server information by adding the second KeyControl node. Notice both KeyControl nodes, in a comma separated list.
interop@denqamgmtscl03> purekmip setattr Entrust-KeyControl-KMIP-Server \ --uri 10.194.148.126:5696,10.194.148.127:5696 --certificate entrust-kmip-cert Name URI Certificate Ca Certificate Configured Entrust-KeyControl-KMIP-Server 10.194.148.126:5696 entrust-kmip-cert True Entrust-KeyControl-KMIP-Server 10.194.148.127:5696 entrust-kmip-cert True
Test secure connection from Pure Storage FlashArray to KeyControl
-
Sign in to the Pure Storage FlashArray CLI with administrator privileges.
-
Test the connections to each KeyControl node.
interop@denqamgmtscl03> purekmip test Entrust-KeyControl-KMIP-Server Name URI Status Details Entrust-KeyControl-KMIP-Server 10.194.148.126:5696 OK Entrust-KeyControl-KMIP-Server 10.194.148.127:5696 OK
Enable enhanced data security in Pure Storage FlashArray
-
Enable enhanced data security using the KeyControl KMIP server.
interop@denqamgmtscl03> purearray enable security-token --kmip Entrust-KeyControl-KMIP-Server Enabled Type Signature Server True KMIP ded2ca2146869dbcddd6a26117f8f16e07f4a4889bbdcf162b2bcb5996492f90 Entrust-KeyControl-KMIP-Server -
List the security token.
interop@denqamgmtscl03> purearray list --security-token Enabled Status Type Signature Server True enabled KMIP ded2ca2146869dbcddd6a26117f8f16e07f4a4889bbdcf162b2bcb5996492f90 Entrust-KeyControl-KMIP-Server -
Wait up to 30 minutes before executing the next command.
-
Again, test the connections to each KeyControl node.
interop@denqamgmtscl03> purekmip test Entrust-KeyControl-KMIP-Server Name URI Status Details Entrust-KeyControl-KMIP-Server 10.194.148.126:5696 OK Entrust-KeyControl-KMIP-Server 10.194.148.127:5696 OK