Procedures
Prerequisites:
-
A Windows domain controller.
-
Domain administrator privileges to add accounts and join clients.
-
A Windows server in the domain with Internet Information Services (IIS) installed. Active Directory Certificate Service (AD CS) will be installed in this server per the instructions below.
-
A second Windows server in the domain with IIS installed. NDES will be installed in this server per the instructions below.
-
A Windows client in the domain to request CA hash and challenge password pairs.
Select the protection method
OCS or Module protection can be used to authorize access to the keys protected by the HSM. Follow your organization’s security policy to select which one. The following protection methods were used in this integration:
-
HSM OCS with no passphrase protection was used to protect the CA. This is the highest level of protection.
-
HSM Module protection was used to generate the certificate request for IIS binding for secure access to the NDES server. IIS binding is only possible with:
-
OCS without a passphrase
-
Module protection
-
-
Microsoft cryptography provider was used to protect the RA keys. For RA keys, only Cryptographic Application Programming Interface (CryptoAPI) Service Providers are supported.
For secure HTTPS connections, you can only use OCS with no passphrase or module protection. This is required when setting up the binding on the IIS server for the https protocol. At that stage the IIS server does not provide any mechanism to enter passphrases for OCS or softcard protection, therefore any protection method that uses a passphrase will fail.
Install the Security World software and create a Security World
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Install the Security World software by double-clicking on the
SecWorld_Windows-xx.xx.xx.isofile. For detailed instructions, see the Installation Guide for the HSM on https://nshielddocs.entrust.com/. -
Add the Security World utilities path
C:\Program Files\nCipher\nfast\binto the Windows system path. -
Open the firewall port
9004outbound for the HSM connections. -
Install the nShield Connect HSM locally, remotely, or remotely via the serial console.
-
Open a command window and run the following to confirm that the HSM is
operational:C:\Users\dbuser>enquiry Server: enquiry reply flags none enquiry reply level Six serial number ... mode operational ... Module #1: enquiry reply flags none enquiry reply level Six serial number ... mode operational. ... -
Create your Security World if one does not already exist, or copy an existing one. Follow your organization’s security policy for this. ACS cards cannot be duplicated after the Security World is created. Create a quorum K/N appropriate for your implementation and to protect against card failure or loss.
-
Confirm the Security World is
usable:C:\Users\dbuser>nfkminfo World generation 2 state 0x37270008 Initialised Usable ... ... Module #1 generation 2 state 0x2 Usable ... -
Sign in to the NDES server using the domain name,
<domain_name>\Administratorand repeat the above steps, but copying the Security World from the CA server.
Generate the OCS in the CA server
To create the OCS:
-
If you are using remote administration, ensure that the
C:\ProgramData\nCipher\Key Management Data\config\cardlistfile contains the serial number of the card(s) to be presented. -
Open a command window as a user with administrator privileges.
-
Execute the following command.
Follow your organization’s security policy for the values K/N. In this example,
K=1andN=1.The OCS cards cannot be duplicated after it was created. Make sure no passphrase is provided at the prompt. Notice
slot 2, remote via a Trusted Verification Device, is used to present the card.The authentication provided by the OCS as shown in the command is non-persistent and is only available for
K=1and while the OCS card is present in the HSM front panel slot, or TVD. If you are using OCS card protection and non-persistent card configuration, OCS cards need to be inserted in the front panel or always present in the TVD. Add the-p(persistent) option in the command to retain authentication after the OCS card has been removed from the HSM front panel slot or from the TVD.>createocs -m1 -s2 -N testOCS -Q 1/1 FIPS 140-2 level 3 auth obtained. Creating Cardset: Module 1: 0 cards of 1 written Module 1 slot 0: Admin Card #1 Module 1 slot 2: empty Module 1 slot 3: empty Module 1 slot 2: blank card Module 1 slot 2:- passphrase specified - writing card Card writing complete. cardset created; hkltu = ... -
Verify that the OCS has been created:
nfkminfo -c Cardset list - 1 cardsets: (P)ersistent/(N)ot, (R)emoteable/(L)ocal-only Operator logical token hash k/n timeout name 8b652e480d6307c32a1b1395a7a12c8ef07fbd24 1/1 none-NL testOCSThe
rocsutility also shows the OCS that was created:>rocs `rocs' key recovery tool Useful commands: `help', `help intro', `quit'. rocs> list cardset No. Name Keys (recov) Sharing 1 testOCS 0 (0) 1 of 1 rocs> quit
Configure the CNG provider in the CA server
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Select Start > nCipher > CNG configuration wizard.
-
Select Next on the Welcome window.
-
Select Next on the Enable HSM Pool Mode window, leaving Enable HSM Mode for CNG Providers un-checked.
-
Select Use existing security world on the Initial setup window. Then select Next.
-
Select the HSM (Module) if more than one is available on the Set Module States window. Then select Next.
-
In Key Protection Setup, select Operator Card Set protection > Next, then select the relevant option: Module protection or Operator Card Set protection.
For Module Protection, the Software Installation window will come up. For OCS Protection, choose from Current Operator Card Sets. Notice this was created above.
-
Select Next > Finish.
-
Verify the provider:
>certutil -csplist | findstr nCipher Provider Name: nCipher Security World Key Storage Provider
Configure the CNG provider on the NDES server
-
Sign in to the NDES server using the domain name,
<domain_name>\Administrator. -
Select Start > nCipher > CNG configuration wizard, then follow the steps to configure the CNG as described in Configure the CNG provider in the CA server.
Install and configure AD CS on the CA server
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Select Start > Server Manager to open the Server Manager.
-
Select Manage, then select Add Roles & Features. The Before you begin window appears. Select Next.
-
Select Role-based or feature-based installation on the Select installation type window. Select Next.
-
Select the local server from the pool on the Select destination server window. Select Next.
-
Select Active Directory Certificate Services role on the Select server roles window. The Add Roles and Features Wizard will appear. Select Add Features and then select Next.
-
In Select features, select Next.
-
Select Next on the Active Directory Certificate Services window.
-
Select Certification Authority on the Select role services windows.
-
Select Next.
-
Verify the information, then select Install on the Confirm installation selections window.
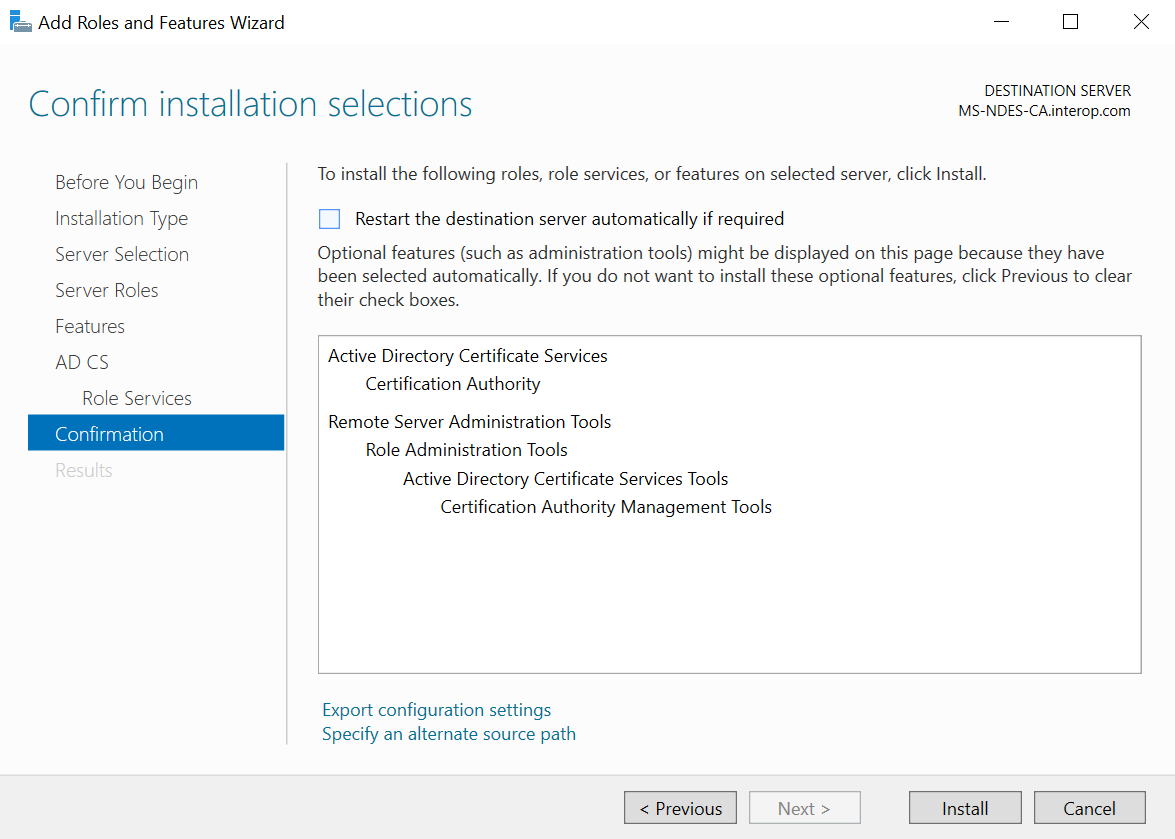
-
Do not select Close the Installation progress windows once the installation is complete. Instead, select the Configure Active Directory Certificate Services on the destination server link.
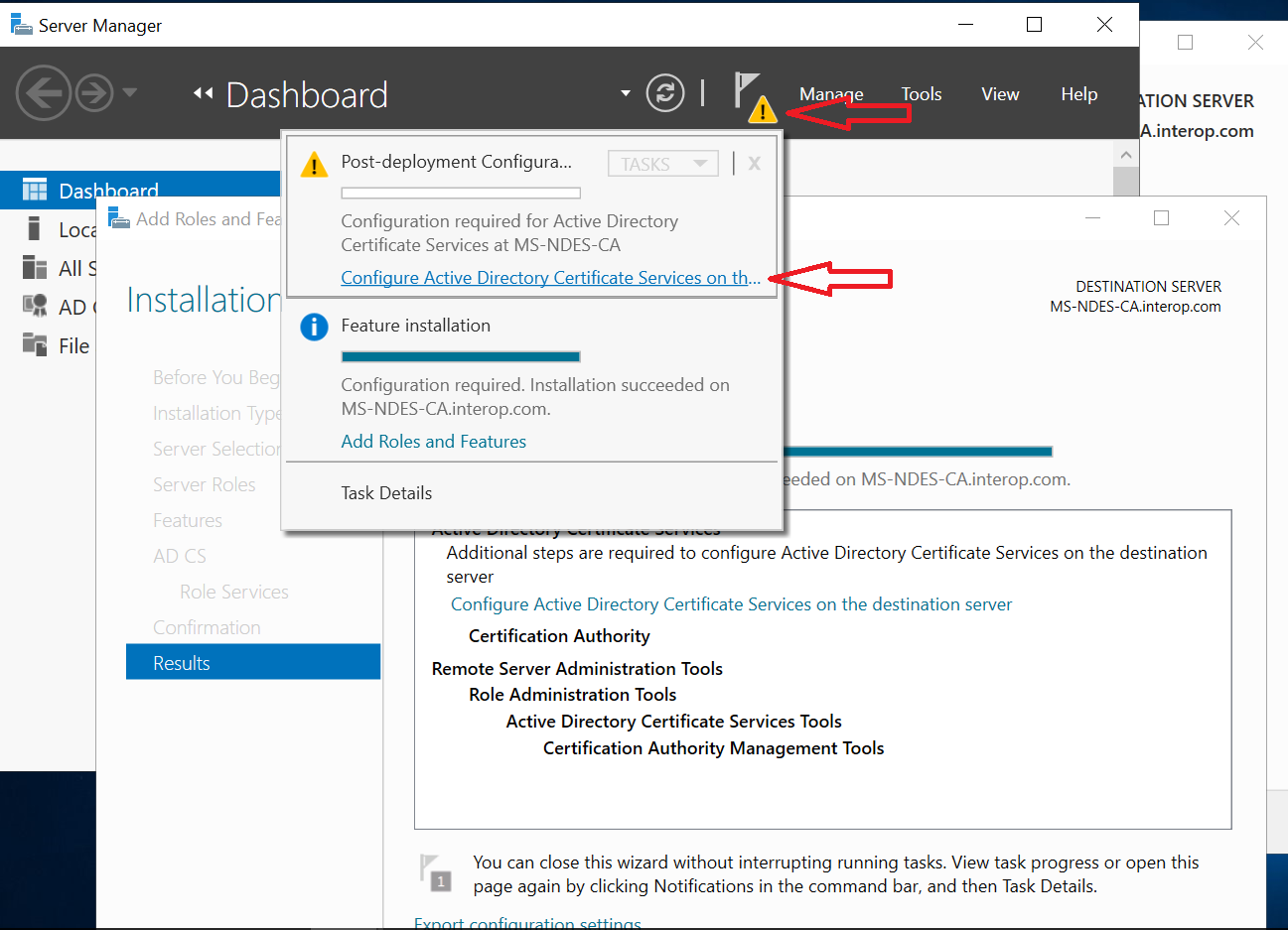
-
Verify the Administrator credentials,
<domain_name>\Administratoron the Credentials text box on the Credentials windows. If needed select Change and specify the appropriate credentials. Select Next. -
Select Certification Authority on the Role Services window. This is the only available selection when the certification authority role is installed on the server. If using OCS key protection, present the OCS card in the HSM or TVD. When the communication with the HSM has been established the button becomes active. Select Next.
-
Select Enterprise CA on the Setup Type window. Select Next.
-
Select Root CA on the CA Type window. Select Next.
-
Select Create a new private key on the Private Key window. Select Next.
-
In Cryptography for CA > nCipher Security World Key Storage Provider, select a provider with key length 2048 or longer. Also check Allow administrator interaction when the private key is accessed by the CA. Then select Next.
-
Take the default CA name given, or modify if required on the CA Name window. Select Next.
-
Enter the number of years for the certificate to be valid on the Validity Period window. Select Next.
-
Take the default locations for the database and database log files, or modify if required on the CA Database window. Select Next.
-
Select Configure on the Confirmation window.
-
A Create new key wizard window appears on the task bar. It may be hidden behind the other windows. Open it and select Next.
-
Select the protection method for the new key. Select Next.
You will be prompted to present the OCS cards if OCS protection method was chosen when the CNG provider was installed. There will be no prompt if Module protection was chosen.
If you are using a FIPS 140 Level 3 Security World, you will need to present an OCS card for FIPS authorization before the AD CS key can be generated, irrespective of your chosen protection method.
-
Present the OCS and select the module if more than one nShield Connect is available. Select Finish to close the wizard.
-
Select Next on the Load key window.
-
Select the module on the Choose modules you wish to load the key onto window. Select Next.
-
Select Finish. Successful configuration is shown as follows. Select Close.
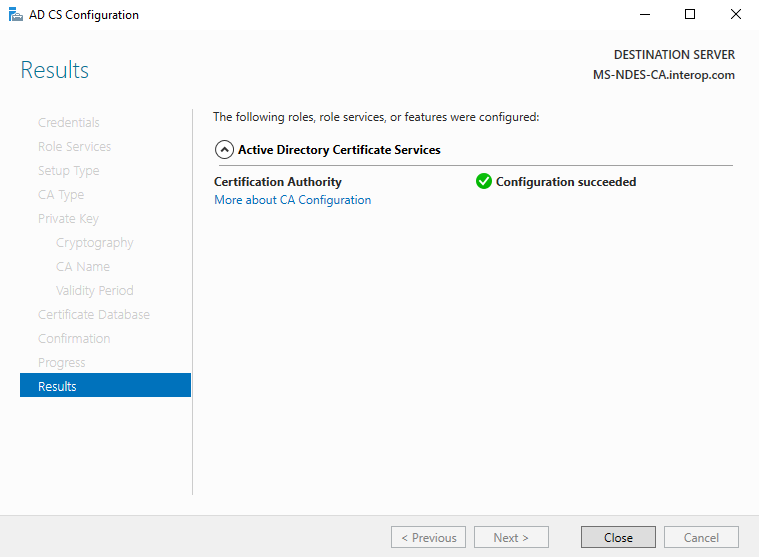
-
The key generated can be verified using a CLI command:
>nfkminfo -l Keys protected by cardsets: key_caping_machine--75393afa6878b98e3d91b5ff360284f706a97572 `interop-MS-NDES-CA-CA`The
rocsutility shows the names and protection methods of the keys.>rocs `rocs' key recovery tool Useful commands: `help', `help intro', `quit'. rocs> list keys No. Name App Protected by 1 interop-MS-NDES-CA-CA caping MSaDCSnDESocs rocs> quit -
Register
nFast Serveras a dependency of AD CS with thencsvcdeptool in thenfast/bindirectory. This is needed as the nShield service must have started before CA, otherwise the nShield CNG providers will fail.Run the command:
>ncsvcdep -a certsvcExample output:
Dependency change succeeded. -
Verify that the CA service has started successfully.
Run the command:
>sc query certsvcExample output:
SERVICE_NAME: certsvc TYPE : 110 WIN32_OWN_PROCESS (interactive) STATE : 4 RUNNING (STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0 -
In Installation progress, select Close.
Add certificates templates to the CA server
-
Sign in to the CA server using
<domain_name>\Administrator. -
Select Server Manager > Tools > Certification Authority.
-
Expand the issuing CA node in the left-hand pane.
-
Right-click Certificate Templates, then select New > Certificate Template to Issue.
-
Select the following templates, then select OK:
-
Exchange Enrollment Agent (Offline Request)
-
CEP Encryption
-
IPSEC (Offline request)
-
-
Check that the templates have been added.
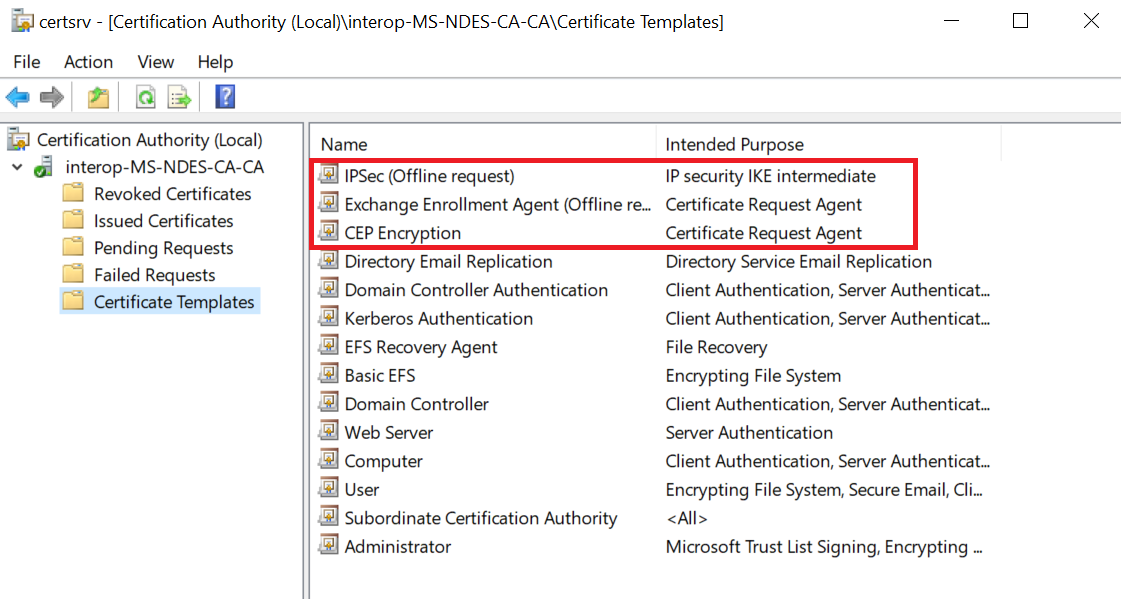
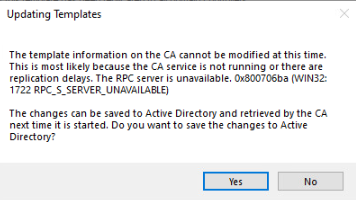
If you get a message indicating the CA service is not running, stop and then restart the Certificate Authority Service or reboot the CA server and try to add the certificate template again. A message like this gets displayed when this occurs:
Install Web Server (IIS) on the CA server
-
Sign in to the CA server using
<domain_name>\Administrator. -
Select Start > Server Manager to open the Server Manager.
-
Select Manage, then select Add Roles & Features. The Before you begin window appears. Select Next.
-
Select Role-based or feature-based installation on the Select installation type window. Select Next.
-
Select the local server from the pool on the Select destination server window. Select Next.
-
Select Web Server (IIS) on the Select server roles window. The Add Roles and Features Wizard will appear. Select Add Features and then select Next.
-
In Select features, select Next.
-
Select Next on the Web Server Role (IIS) window.
-
Select Next on the Select role services window.
-
Verify the information, then select Install on the Confirm installation selections window.
-
Select Close, once installation completes.
Create a virtual directory to serve as the public key infrastructure (PKI) repository
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Create a local directory for PKI repository, for example
C:\PKIRepository. See the following Microsoft link for instructions, https://docs.microsoft.com/en-us/troubleshoot/windows-server/networking/create-virtual-directory-folder-remote-computer. -
Create a virtual directory. Notice the alias, physical path, and path credentials.
-
Create a local directory for PKI repository, for example
C:\PKIRepository.% mkdir c:\PKIRepository -
Select Start, point to Programs > Administrative Tools, and then select Internet Information Services (IIS) Manager.
-
In the Internet Information Services window, expand server name (where server name is the name of the server).
-
Right-click the Web site that you want (for example, Default Web Site), and select Add Virtual Directory.
-
On the Add Virtual Directory window, type the Alias that you want (for example, PKIRepository), select the Physical Path, and then select OK.
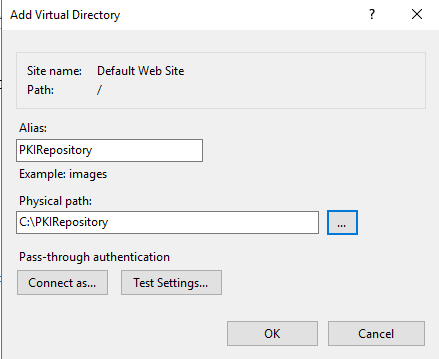
-
Right-click the new created Virtual Directory and select Manage Virtual Directory > Advanced Settings.
-
In the Advanced Settings window, select Physical Path Credentials.
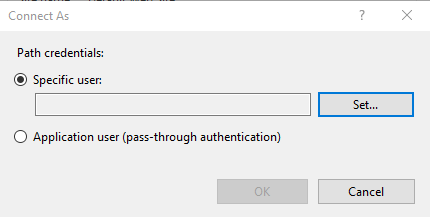
-
In the Connect As window, select Specific User > Set.
-
In the Set Credentials windows, enter the domain name user id for User Name, and the password information for the user. Select OK.
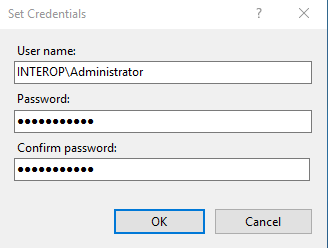
-
-
Test the virtual directory per the same link above.
-
Start Microsoft Edge.
-
In the Address box, type the URL to your Web server (for example, http://CA-SERVER-IP-ADDRESS), and then select Go.
-
Verify that you can view the default Web site.
-
Append the alias of the virtual directory to the address that you typed (for example, http://CA-SERVER-IP-ADDRESS/PKIRepository), and then select Go.
-
The virtual directory Web content is displayed in the browser window. You may get a forbidden error. If that’s the case, create a index.htm file in
C:\PKIRepositorywith some HTML content on it and reload the page, which should display properly.
-
Create domain user accounts to act as the NDES service account
-
Sign in to the Domain Controller as Domain Administrator.
-
Select Active Directory Users and Computers from the Start menu.
Add users SCEPAdmin, SCEPSvc, and SCEPDeviceAdmin.
-
Expand <domain_name>.com, right-click Users and select New > User.
-
Enter the name SCEPAdmin and select Next. Follow your organization’s security policies to set the password. Never expires was selected for the purpose of this integration.
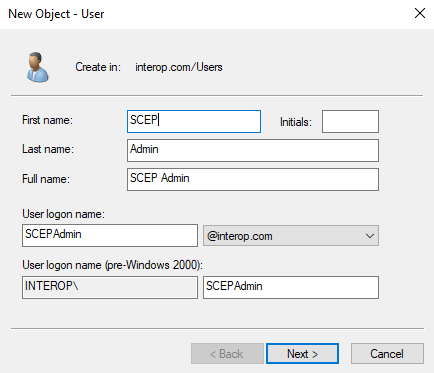
-
Create new users for SCEPSvc and SCEPDeviceAdmin by repeating the previous steps.
Add user SCEPAdmin to the Enterprise Admins and Domain Admins groups.
-
Right-click Enterprise Admins on the right pane and select Properties.
-
Select the Members tab and then select Add.
-
Enter the SCEPAdmin account, select Check Names, and if found then select OK.
-
Select Apply and OK.
-
Repeat the above steps for the Domain Admins group.
Add the SCEPAdmin account and SCEPSvc service account to the local IIS_IUSRS group
-
Sign in to the NDES server using the domain name,
<domain_name>\Administrator. -
Open Computer Management (
compmgmt.msc). -
Expand Local User and Groups on the Computer Management console tree, under System Tools. Select Groups.
-
Double-click IIS_IUSRS on the details pane.
-
Select Add on the IIS_IUSRS Properties window.
-
Enter the SCEPAdmin account, select Check Names, and if found then select OK.
-
Select Apply and OK.
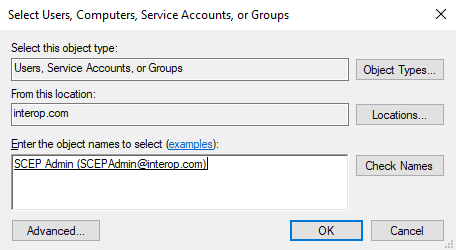
-
Repeat the above steps for the SCEPSvc service account.
Configure the SCEPAdmin account and SCEPSvc service account with request permission on the CA
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Select Certification Authority from the Tools menu on the Server Manager window.
-
Right-click the certification authority (this CA server) and then select Properties.
-
Select the Security tab.
Notice the accounts that have Request Certificates permissions. By default the group Authenticated Users has this permission. The SCEPAdmin account will be a member of Authenticated Users when it is in use, which has Request Certificates permission. However, if that is not the case, do as follows:
-
Select Add.
-
On the Select Users, Computers, Service Accounts, or Groups text box, type the name of the SCEPSvc account, select Check Names, and if found select OK.
-
Select the SCEPSvc account and select the Allow check box that corresponds to Request Certificates.
-
Select Apply and then select OK.
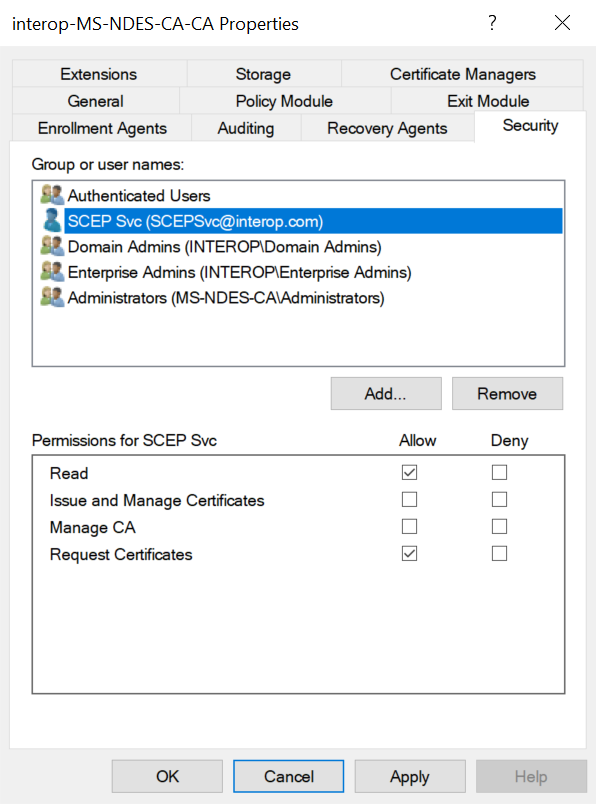
-
Repeat the steps for the SCEPAdmin account.
Configure the SCEPDeviceAdmin account with enroll permission to the IPSEC (offline request) certificate template
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Select Certification Authority from the Tools menu on the Server Manager window.
-
Expand the server on the left pane, then right-click Certificate Templates and select Manage.
-
Right-click IPSEC on the Template Display Name pane and select Properties.
-
Select the Security tab. Then select Add.
-
On the Select Users, Computers, Service Accounts, or Groups text box, type the name of the SCEPDeviceAdmin account, select Check Names, and if found then select OK.
-
Select the SCEPDeviceAdmin account and verify the Allow check box that corresponds to Enroll is selected. Select Apply and then select OK.
Install and configure NDES
-
Sign in to the NDES server using the domain name,
<domain_name>\Administrator. -
Select Start > Server Manager to open the Server Manager.
-
Select Manage, then select Add Roles & Features. The Before you begin window appears. Select Next.
-
Select Role-based or feature-based installation on the Select installation type window. Select Next.
-
Select the local server from the pool on the Select destination server window. Select Next.
-
Select Active Directory Certificate Services role on the Select server roles window. The Add Roles and Features Wizard appears. Select Add Features and then select Next.
-
Select Next on the Select features window.
-
Select Next on the Active Directory Certificate Services window.
-
Uncheck Certification Authority and check Network Device Enrollment Service on the Select role services window. The Add Roles and Features Wizard will appear.
-
Select Add Features and then select Next on the Select role services window.
-
Verify the information, then select Install on the Confirm installation selections window.
-
Do not select Close on the Installation progress windows once the installation is complete. Select the Configure Active Directory Certificate Services on the destination server link instead.
-
Change the Credentials to <domain_name>\SCEPAdmin on the Credentials windows. Select Change, enter new credential, then select Next.
-
From Select Role Services to configure, select Network Device Enrollment Service, then select Next.
-
Select the Specify service account on the Service Account window, then select Select.
-
Enter the credential for the SCEPSvc service account and then select OK and Next.
-
Select CA name on the CA for NDES windows, then select Select.
-
Choose the CA server on the Select Certificate Authority window, then select OK and Next.
-
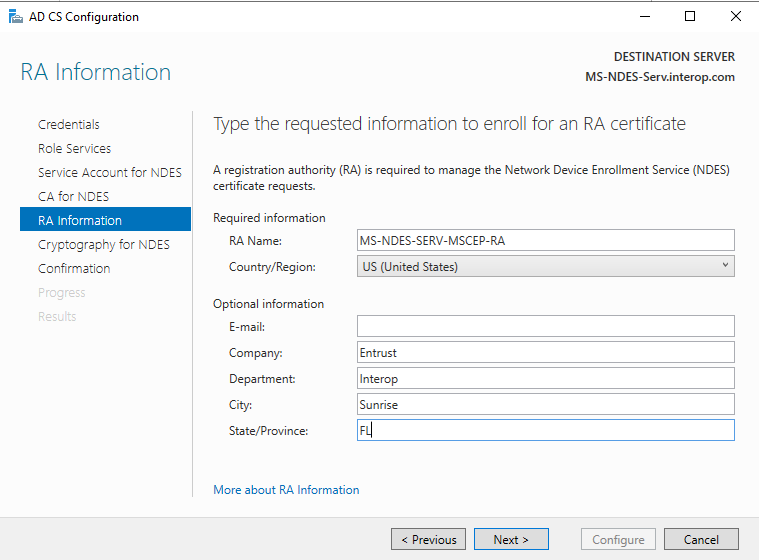
Note the specified Registration Authority (RA Name) on the RA Information window. Complete any of the optional information as required. Then select Next.
-
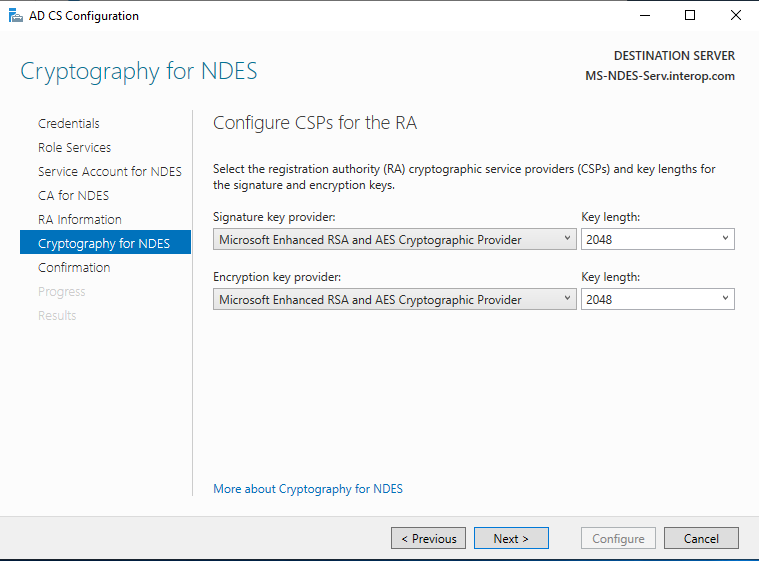
Choose the Signature key provider and Encryption key provider on the Cryptography for NDES window. A key size of 2048 or larger is recommended.
-
Select Next and review the chosen options at the Confirmation window. Then select Configure.
-
Sign in to the CA server and present the OCS if OCS protection was selected. Look for an icon on the Taskbar if the Load key window is not present. You may be prompted to present the OCS.
-
Go back to the NDES server. Check for the Configuration succeeded message on the Results window, then select Close.
If you get a message that it failed to add certificate templates at the end of the NDES installation see troubleshoot.adoc#failed-to-add-certificate-templates.
Configure the NDES admin page to use an SSL certificate
Create a template for the NDES Admin web service certificate request.
This will ensure that the nCipher KSP is used to generate the key pair.
-
Sign in to the NDES server using the domain name,
<domain_name>\Administrator. -
Create a
request.inffile using a text editor as follows. Change Subject to the Fully Qualified Domain Name (FQDN) of the NDES Server, for example:ms-ndes-serv.interop.com.[Version] Signature= "$Windows NT$" [NewRequest] Subject = "CN=<FQDN-of-NDES-Server>" HashAlgorithm = SHA256 KeyAlgorithm = RSA KeyLength = 2048 ProviderName = "nCipher Security World Key Storage Provider" KeyUsage = 0xf0 MachineKeySet = True [EnhancedKeyUsageExtension] OID=1.3.6.1.5.5.7.3.1For example:
[Version] Signature= "$Windows NT$" [NewRequest] Subject = "CN=ms-ndes-serv.interop.com" HashAlgorithm = SHA256 KeyAlgorithm = RSA KeyLength = 2048 ProviderName = "nCipher Security World Key Storage Provider" KeyUsage = 0xf0 MachineKeySet = True [EnhancedKeyUsageExtension] OID=1.3.6.1.5.5.7.3.1 -
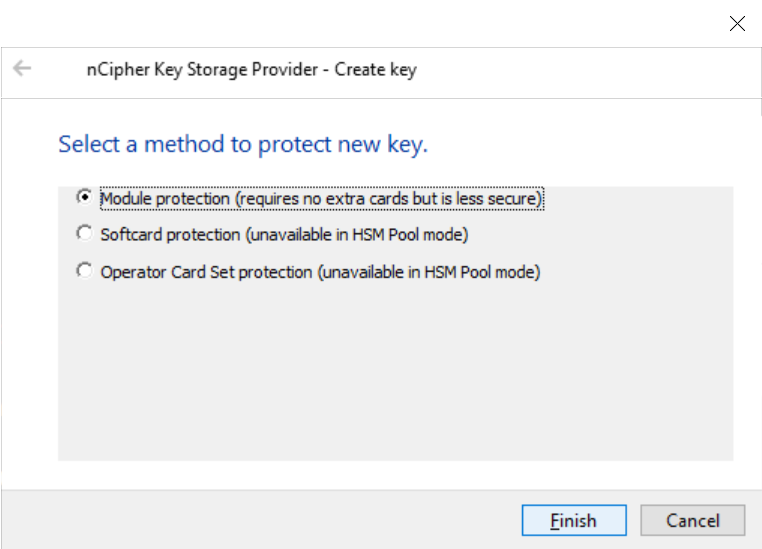
Create a Certificate request file by running the following command. Select Module protection when prompted.
certreq.exe -new <Path-to-Request.inf> <Name-of-Request>.reqExample output:
>certreq -new NDES-SSL-Cert.inf NDES-SSL-Cert.req CertReq: Request Created -
For OCS protection the system will ask to present the OCS card.
-
Copy the above certificate request file to the CA server.
Have the CA issue a certificate based on the Web service certificate template and the certificate request above.
In this example, Authenticated Users is used for provisioning certificates. Consult your security team and reference Microsoft best practices for deploying in a production environment.
-
Sign in to the CA server using the domain name,
<domain_name>\Administrator. -
Enable the Web Server certificate template option. Open the Certification Authority tool and expand the issuing CA node on the left hand pane.
-
Right-click Certificate Templates and select Manage.
-
Right-click Web Server and select Duplicate Template on the Certificate Template Console window.
-
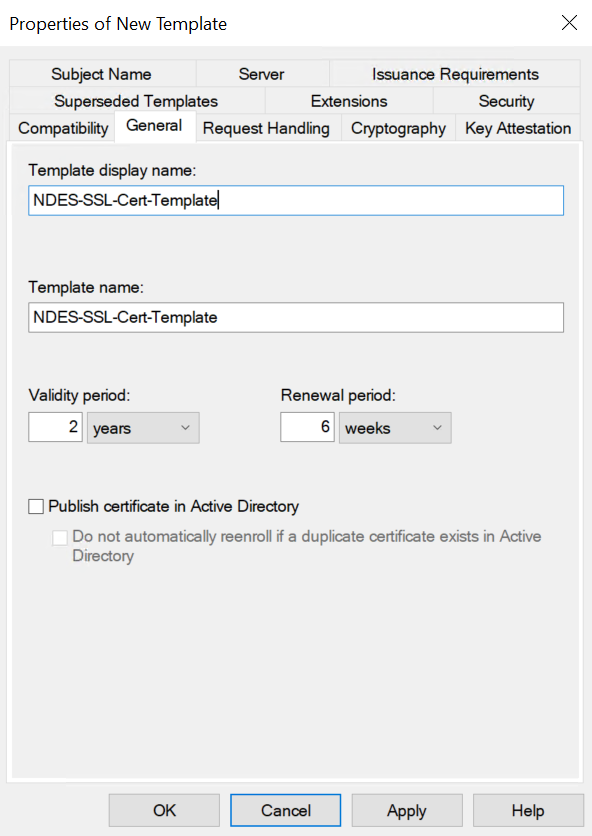
Select the General tab in the Properties of New Template dialog. Type the name you want to use on the Template Display Name. Then select Apply and OK.
-
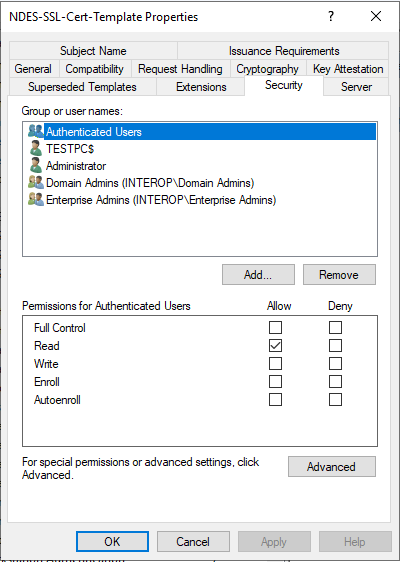
Select the Security tab.
-
Select Authenticated Users in Groups and user names. Then check Enroll in Permissions for Authenticated Users. Then select Apply and OK.
-
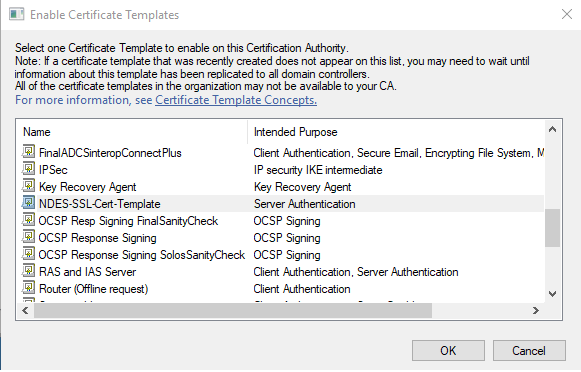
Return to the Certification Authority window, right-click Certificate Templates, and select New > Certificate Template to Issue.
-
Select the certificate template that you created earlier, then select OK.
-
Run the following command to generated the certificate:
certreq -submit -attrib “CertificateTemplate:<New-Template-Name>” <Path-to-request.req>Partial output before executing the following steps:
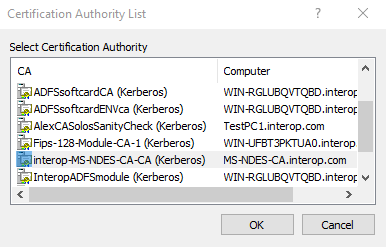
>certreq -submit -attrib "CertificateTemplate:NDES-SSL-Cert-Template" NDES-SSL-Cert.req NDES-SSL-Cert.cer Active Directory Enrollment Policy {96E14557-DDD4-48BD-BE1A-AA453F20D859} ldap: -
Select the CA server from the Certification Authority List dialog, then select OK. Look for a cog icon which may be flashing on the Taskbar. Present the OCS cards.
-
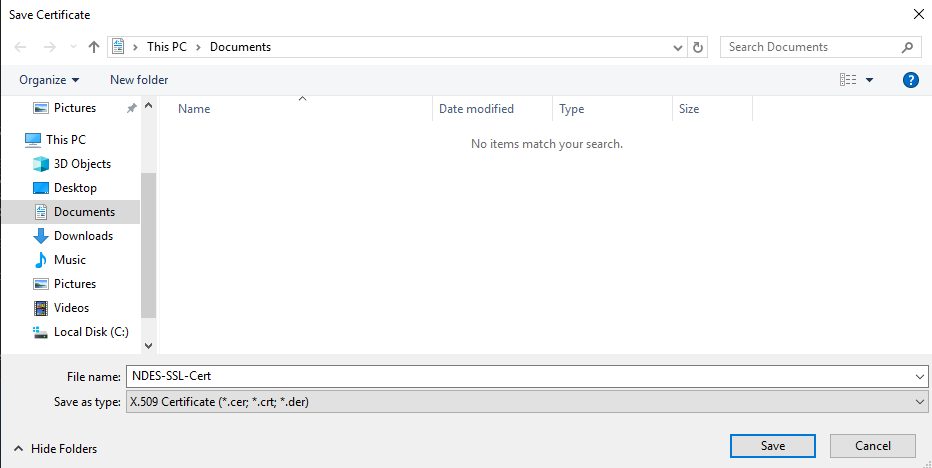
Enter the name for the certificate generated on the Save Certificate dialog.
The final output is shown below:
>certreq -submit -attrib "CertificateTemplate:NDES-SSL-Cert-Template" NDES-SSL-Cert.req NDES-SSL-Cert.cer Active Directory Enrollment Policy {96E14557-DDD4-48BD-BE1A-AA453F20D859} ldap: RequestId: 11 RequestId: "11" -
Copy the above certificate to the NDES server.
Install the certificate on the NDES server, matching it with the private key previously created using the nCipher CSP.
-
Sign in to the NDES server using the domain name,
<domain_name>\Administrator. -
Run the following command. If you are using OCS protection, present the card when prompted.
>certreq.exe -accept <Name-of-Certificate>.cerExample output:
>certreq -accept NDES-SSL-Cert.cer Installed Certificate: Serial Number: 7c0000000bf544d43dadb23a2f00000000000b Subject: CN=ms-ndes-serv.interop.com NotBefore: 10/7/2021 12:00 AM NotAfter: 10/7/2023 12:10 AM Thumbprint: a07344a115b23f7cd903851af3b66884e55aa3ea -
Open
certlm.mscby right-clicking on the Windows Start menu, then select Run, typecertlm.msc, and select OK. -
Expand the Personal store on the left pane and then select Certificates.
-
Check the certificate installed above is available.
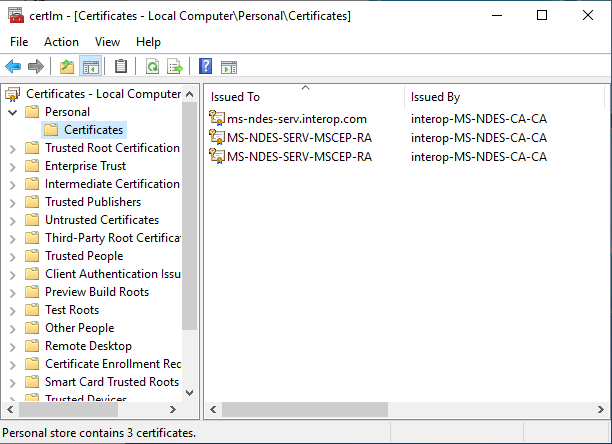
-
Open the IIS manager, expand the server and Sites on the Connections pane and select Default Web Site.
-
Select Bindings on the Actions pane.
-
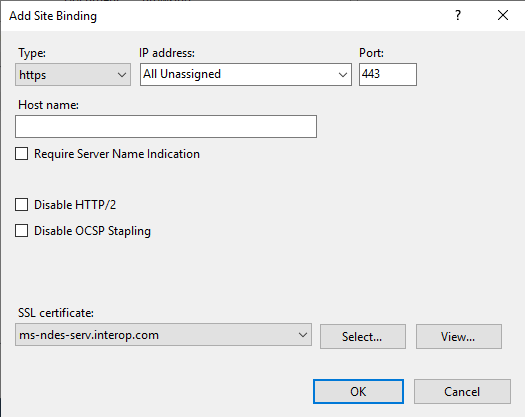
Select Add on the Site Bindings dialog.
-
Select https in Type: on the Add Site Binding dialog. Choose the certificate previously created in SSL certificate. Then select OK and Close.
Increase the maximum number of allowed unique passwords generated by the NDES service to 30 before the service needs to be restarted.
-
Sign in to the NDES server using the domain name,
<domain_name>\Administrator. -
Open regedit by right-clicking on the Windows Start menu, then select Run, type
certlm.msc, and select OK. -
Navigate to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MSCEP.
-
Right-click the right pane and select New > Key > DWORD (32-bit). Name the key PasswordMax.
-
Right-click the key and select Modify. Set Value data to 30 on the Edit DWORD (32-bit) Value dialog. Then select OK.
-
Restart the IIS server. Open the IIS manager, select the server on the Connections pane and select Restart on the Actions pane.
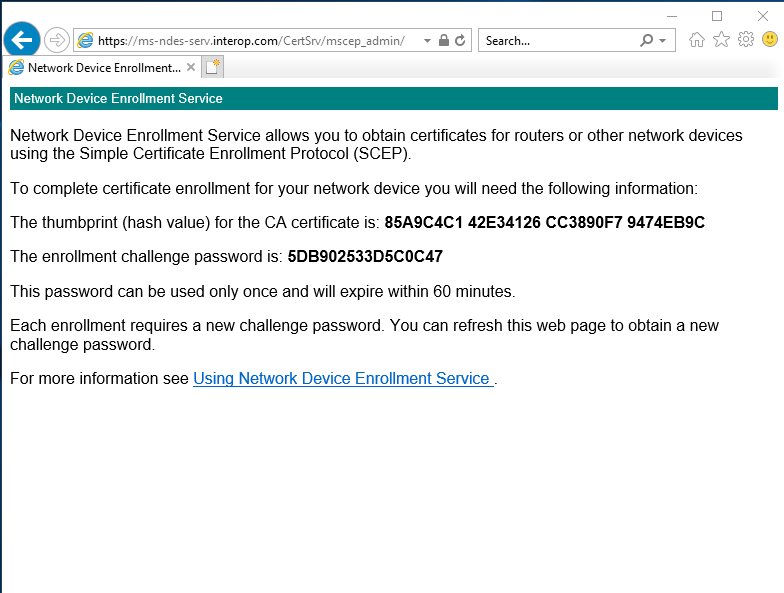
Test access to the NDES web site (secured).
-
Sign in to the Windows client.
-
Launch the browser and go to the following address:
https://<NDES-server-address>/CertSrv/mscep_admin. Sign in as<domain-name>\SCEPSvc. -
Notice the hash value of the CA certificate and the challenge password. Refreshing the browser generates a new challenge password.