Procedures
To integrate the UiPath Robotic Process Automation platform with the nShield HSM:
Deploy the backbone server
To deploy the backbone server:
Configure the backbone server, domain groups, and users
To configure the backbone server, domain groups, and users:
-
For prerequisites, see https://docs.uipath.com/orchestrator/standalone/2022.4/installation-guide/orchestrator-prerequisites-for-installation.
-
Install and configure Microsoft Windows Server Operating System.
-
Install and configure the ADDS role.
-
Create a domain group. (i.e., AutoEnrollGroup)
-
Create the user accounts to be used by the Robots for authentication.
-
Open Active Directory Users and Computers through the Windows Start menu or the Microsoft Management Console.
-
Enable the advanced view so you can see the Published Certificates tab for user accounts.
-
Right-click Users under your domain name and select New.
-
Select User.
-
Create users such as RobotVM3 for the Robot user on system VM3. This helps distinguish that this particular Robot user has its Softcard or key on VM3.
-
-
Add group memberships to the Robot accounts so they can sign in to the Windows Server machines.
-
In AD Users and Computers, select Users and find the users that were created.
-
Right-click each user and select Properties.
-
Select the Member Of tab.
-
Add the following groups:
-
Administrators
-
Enterprise Admins
-
Domain Admins
-
Domain Users
-
AutoEnrollGroup
-
-
-
Enable Log On as a batch job rights for the Application Pool user.
-
Select Windows > Run > mmc.
-
Select File > Add/Remove Snap-in.
-
Add Group Policy Object.
-
Select Finish.
-
Select OK.
-
Configure ADCS
Microsoft ADCS does not have to be installed on the same "backbone" server as ADDS. For testing purposes, this document describes the specific steps for setting up all needed roles on the same machine.
To configure ADCS:
Install and configure the Active Directory Certificate Services role
To install and configure the Active Directory Certificate Services role:
-
Open Server Manager and Install ADCS.
-
Configure as an enterprise root CA.
-
Optionally, if you want the CA to use the HSM for its signing key:
-
Select the nShield CNG provider to write the CA key.
-
Select RSA2048/SHA256.
-
Select module protected key for simplicity.
-
Configure the ADCS certificate templates
To configure the ADCS certificate templates:
-
Open the Certification Authority Microsoft Management Console.
-
Expand the CA node.
-
Right-click Certificate Templates and select Manage to create a new certificate template for the Robot.
-
Right-click Smartcard Logon and select Duplicate Template.
-
Configure the following tabs:
Do not select Apply or OK until the end, else the template will be saved with the incorrect name. Tab Configuration option Recommended setting or value Compatibility
Show resulting changes
Clear the selection box.
Certification Authority
Windows Server 2012 or higher (required for CNG)
Certificate recipient
Windows 8 / Windows Server 2012 or higher (required for CNG)
General
Template Display Name
UiPath Robot nShield KSP
Validity period
Select appropriate value
Renewal period
Select appropriate value
Publish certificate in Active Directory
Select this option
Do not automatically reenroll if a duplicate certificate exists in Active Directory
Select this option
Request handling
If an ECC key is to be used instead of RSA, the Signature and smartcard logon choice forces an ECDH key which will not work with the nShield.
To force ADCS into issuing an ECDSA certificate for SCL: After previously selecting Signature and smartcard logon, change to Signature. ADCS will add the appropriate certificate extensions/attributes to the template for Signature and smartcard logon. When you afterwards switch to Signature, it retains those extensions/attributes but allows ECDSA keys.
Signature and smartcard logon, select YES in the dialog
Do the following when the subject is enrolled and when the private key associated with this certificate is used
Prompt the user during enrollment
Cryptography
Provider Category
Key Storage Provider (which is CNG)
Algorithm name
RSA or ECDSA_P384
Minimum key size
2048 (for RSA)
384 (for ECDSA_P384)
Choose which cryptographic providers can be used for requests
Requests must use one of the following providers
Providers
nCipher Security World Key Storage Provider
Request Hash
SHA256 (for RSA)
SHA-384 (for ECDSA_P384)
Security
Select Add, enter AutoEnrollGroup and select Check Names.
Then select OK.
Select AutoEnrollGroup from the list and enable permissions read enroll autoenroll.
Subject name
Build from this Active Directory Information
Select this option
Subject name format
Fully distinguished name
Include this information in alternate subject name
Ensure only UPN is selected
-
Select OK.
The new certificate template is included in the list.
-
In the Certification Authority Microsoft Management Console, right-click Certificate Templates and select New > Certificate Template to issue.
-
Ctrl+click to select both Web Server and UiPath Robot nShield KSP and select OK.
-
Both templates are added to the Certificate Templates list and can now be issued.
Set up UiPath Orchestrator
The procedures described in this guide are an example test set-up for integration purposes. Your organization’s needs may require alternate steps for set-up and deployment.
For information, see also https://docs.uipath.com/installation-and-upgrade/docs/orchestrator-about-installation.
Select one of the three following installation options:
Set up a cloud Orchestrator
To set up a cloud Orchestrator:
-
Go to https://cloud.uipath.com.
-
Create an account and sign in.
-
Select Create new.
-
Under Services, select the Orchestrator link.
-
Use a UI Path License to allocate one Unattended Runtime slot for each Robot you intend to use.
-
Create a machine:
-
Go to Tenant and then select Machines.
-
Select Add machine.
-
Select Standard machine.
-
Enter a name for the machine.
The name must match exactly the name of the workstation on which the Robot is installed. To check it, run hostnameon the Robot machine.Add one Production (Unattended) runtime.
This is a type of license that allows the Robot to run triggered from Orchestrator.
-
Select Provision.
-
Make sure to copy the Machine key. You will need the key when you are connecting UiPath Assistant to the Orchestrator instance.
-
-
Create a Robot Account: Select Admin from the top left menu.
-
Select Manage.
-
Select Accounts & Groups.
-
Select Robot accounts.
-
Select Add Robot Account:
-
Enter a name for the Robot Account.
-
Designate the Group Membership for the account.
-
Select Add.
-
-
-
On the Orchestrator, select Tenant > Manage Access > Assign roles > Robot Account, then set its properties:
Search for a Robot account Select the Robot account that you created.
Roles Designate roles for the Robot account.
Foreground automation settings Select Use a specific Windows user account. Add credentials below.
Domain\Username <domain\username>
Credential Store Select Orchestrator Database.
Password <Softcard passphrase>
Credential type Select nShield Key Storage Provider.
The <domain\username> will be for the Robot machine account. To check the Robot username at the command prompt on the Robot machine, use whoami. -
Under Logging settings, select Login to console > YES.
-
Select Assign.
-
Assign the Robot Account to your folder:
-
Select the folder to be used and then Settings.
-
Select Assign Account/Group.
-
Enter and select the Robot Account previously created.
-
Designate roles.
-
Select Assign.
-
-
Upload a package:
Select Tenant > Packages > Upload.
-
Browse to a package to upload:
Select your Folder > Automations > Add process.
Create the process from the package that you previously uploaded.
The Orchestrator has been created and configured.
Set up a local Orchestrator through UiPath Platform
To set up a local Orchestrator through UiPath Platform:
-
Read https://docs.uipath.com/installation-and-upgrade/docs/orchestrator-about-installation.
-
Ensure that your environment meets these requirements: https://docs.uipath.com/installation-and-upgrade/docs/orchestrator-prerequisites-for-installation.
-
Run UI Path Platform.
-
Accept the Agreement.
-
Select Install Single Node, and then select Next.
-
Enter Computer Account Username and Password.
-
Select Next until the Host and Tenant passwords menu appears.
-
Enter the Host and Tenant passwords. These will be used to log in to Orchestrator later.
-
Select Enable Windows Authentication.
-
Next to Active Directory Domain, enter the domain name, and then select Next.
-
Make a note of the URL. This will be used to access the Orchestrator interface through a web browser.
-
Select Install.
Set up a local Orchestrator with the installer
It is required to set up Microsoft IIS and SQL Server before proceeding with the on-premise local Orchestrator install.
To configure Internet Information Services (IIS):
-
Request a Web Server certificate from ADCS using RSA2048/SHA256.
-
Open IIS.
-
Select Server Certificates.
-
Select Create Domain Certificate.
-
Fill in the required information and then select Next.
-
Specify the Certificate Authority that was created earlier.
-
Enter Friendly Name.
-
Select Finish.
To install Microsoft SQL Server:
-
Select Custom Installation.
-
Select New SQL Server stand-alone installation or add features to an existing installation.
-
Select the product license.
-
Accept the terms.
-
Select Use Microsoft Update to check for updates (recommended), and then select Next.
-
Select the following features:
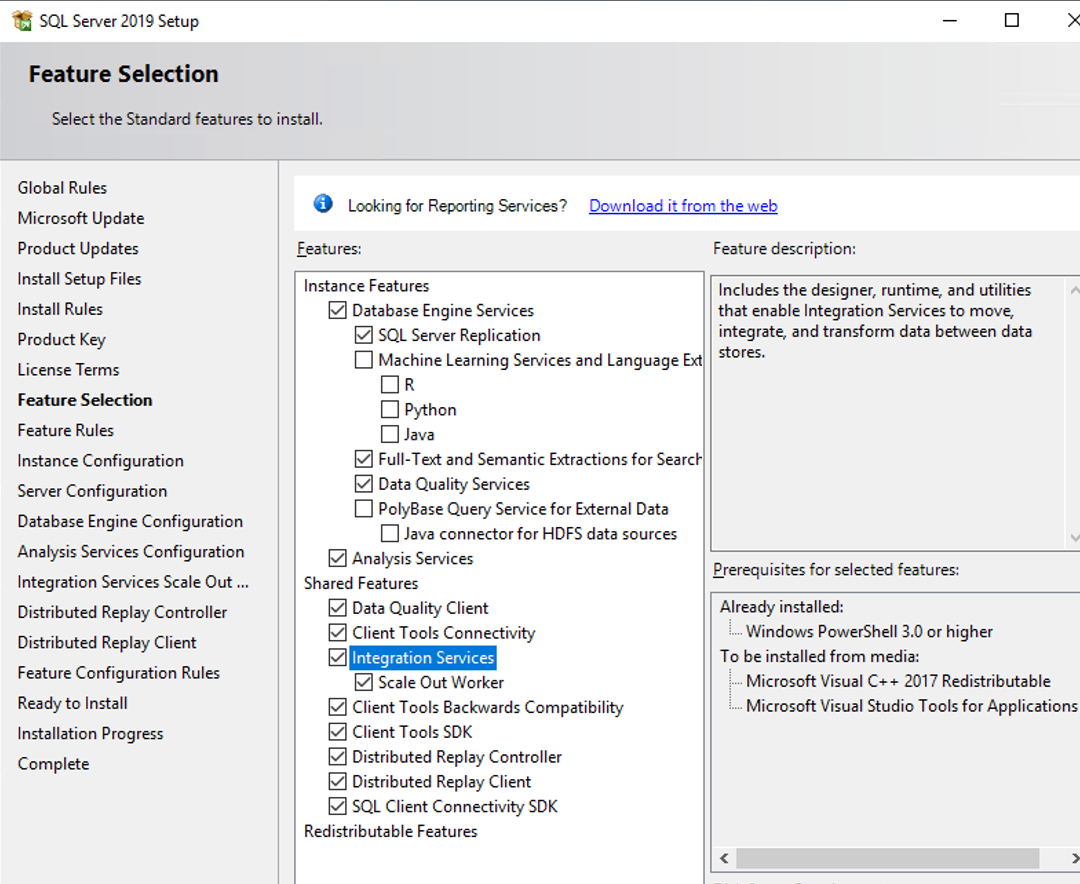
-
Select Next.
-
Select Next.
-
Select Add Current User and select Next.
-
Continue selecting Next until Install.
-
Close the installer.
To set up a local Orchestrator with the installer:
-
Right-click the
UiPathOrchestrator.msifile, and select Install. -
Select Next on the welcome screen.
-
Accept the terms and select Install.
-
On the Product Features menu, select Next.
-
The Orchestrator IIS Settings should be auto-filled.
-
If there is an error about SSL certificate, edit the box and paste in the thumbprint of the certificate requested in IIS.
-
Select Next.
-
On the Orchestrator Application Pool Settings screen, make sure Custom Account is selected.
-
Enter the username and password of the Orchestrator Computer Account, and then select Next.
-
On the Orchestrator Database Settings screen, select Leave as is.
-
Select Next.
-
On the Identify Server Settings screen, make a note of the Orchestrator public URL.
-
Paste in the Signing Certificate Thumbprint.
-
Select Next.
-
On the Orchestrator Elasticsearch Log Settings screen, select Next.
-
On the Orchestrator Authentication Settings screen, enter passwords for the Host and Default Tenant.
-
Select Enable Windows Authentication.
-
Enter the Domain Name.
-
Select Next.
-
Select Install.
-
Select Finish.
Deploy a Robot service
To deploy a Robot service:
-
Install the operating system on the machine that will host the Robot service.
Windows Server 2022, Windows 10, Windows Server 2019, and Windows Server 2016 were tested as the host operating systems for the Robot service.
-
Join the server to the domain.
-
Install the nShield Security World client.
-
Configure the existing Security World.
-
Run the CNG wizard or the
cnginstallcommand. -
Create an HSM Softcard.
For example, at the command prompt run the following command:
ppmk --new RobotVM1
-
-
Configure the custom CNG provider.
The
SmartCardLoginfunctionality is protected by a registry setting. Configure the followingSmartCardModeregistry settings to the recommended values in the table. This will enable theSmartCardLoginsupport on any machine where the revised CNG provider is installed:Parameter Value HKEY_LOCAL_MACHINE\SOFTWARE\nCipher\CryptoNG\SmartCardMode1aHKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\nCipher\CryptoNG\SmartCardMode1bHKEY_LOCAL_MACHINE\SOFTWARE\nCipher\CryptoNG\UseModuleKeys0cHKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\nCipher\CryptoNG\UseModuleKeys0ca It will be necessary to add the
DWORDvalue for the 64-bit CNG provider.b It will be necessary to add the
DWORDvalue for the 32-bit CNG provider.c This value is set to
0so distinct protection tokens can be used for each user associated with aSmartCardLogincertificate. -
Sign in to the Robot machine with the Robot user account that was created in Configure the backbone server, domain groups, and users.
-
Request the user certificate UiPath Robot nShield KSP using the HSM Softcard.
-
Select Control Panel > Manage User Certificates.
-
Right-click the Personal node, and select All Tasks > Request New Certificate.
-
On the Before You Begin screen, select Next.
-
On the Select Certificate Enrollment Policy screen, keep the default Active Directory Enrollment Policy selected and then select Next.
-
On the Request Certificates screen:
-
Select the UiPath Robot nShield KSP certificate template and Select Enroll.
-
On the nCipher Key Storage Provider - Create Key screen, select Next.
-
On the Select a method to protect new key screen, select Softcard protection (unavailable in HSM Pool mode), and select Next.
-
Select the previously created Softcard and select Finish.
-
On the password screen, enter the Softcard passphrase and select Finish.
-
-
On the Certificate Installation Results screen, ensure that it shows successful enrollment and select Finish.
-
-
Install UiPath Studio (Robot):
-
Double-click on the MSI installer to begin installation.
-
On the Please read the UiPath Studio License Agreement screen:
-
(Optional) Select Advanced to configure any specific packages.
-
Select I accept the terms in the License Agreement.
-
Select Install.
-
-
On the Completed the UiPath Studio Setup Wizard screen, select Finish.
-
Configure UiPath for Robots
To configure UiPath for Robots:
Configure UiPath for nShield HSMs
Configure the Robot to use only the 64-bit nShield CNG provider with the Microsoft CorFlags tool: https://docs.microsoft.com/en-us/dotnet/framework/tools/corflags-exe-corflags-conversion-tool.
Visual Studio 2019 is required to run the Visual Studio Command Line, which is needed to run the corflags.exe command.
|
-
Stop the
UiRobotSvcservice. -
From the Administrator command prompt, run the
corflags.execommand:CorFlags.exe "C:\Program Files (x86)\UiPath\Studio\UiPath.Service.Host.exe" /32BITPREF- -
Restart the
UiRobotSvcservice.
Configure UiPath for Robots if a local Orchestrator was used
| Skip this section if the Robot was set up through a cloud Orchestrator. This is because these steps would already have been completed in Set up a cloud Orchestrator. |
If a local Orchestrator was used, the Robot must be set up to get the machine key.
-
Sign in to the machine with Orchestrator.
-
Enter the Orchestrator URL into a browser.
-
Make sure the organization is set to host.
-
Enter admin as the username and use the password set for the host when the local Orchestrator was installed.
-
Select License and enter your license in whichever way works best: online or offline.
-
When the license has been activated, select Tenants and select the 3 vertical dots on the right side of the Default Tenant.
-
Select Allocate Licenses.
-
Allocate one Production (Unattended) Runtime slot for each Robot you intend to use.
-
Log out of the tenant host and login with the organization set to default. Use admin as the username and use the password set for tenant when the local Orchestrator was installed.
-
Select Tenant.
-
Select Add machine.
-
Select Standard Machine.
-
Enter the machine name.
The name must match exactly the name of the workstation on which the Robot is installed. To check it, run hostnameon the Robot machine. -
Under License - Unattended Runtimes, enter 1.
-
Select Provision, then select Copy to copy the machine key.
-
Go to Default > Robots > Add > Standard Robot.
-
Under Runtime license (execution slots) - Production (Unattended), enter 1.
-
Select Provision, then select Copy to copy the machine key. You will need the key when you are connecting UiPath Assistant to the Orchestrator instance.
-
Select Tenant > Folders > Your_Folder > Machines > Manage Machines in Folder
-
Add the previously created machine.
-
Create a Robot Account:
-
Select Tenant.
-
Select Manage Access.
-
Select Manage Accounts & Groups.
-
Select Robot accounts.
-
Select Add Robot Account.
-
Enter a name for the Robot Account.
-
Designate the Group Membership for the account.
-
Select Add.
-
-
-
On the Orchestrator, select Tenant > Manage Access > Assign roles > Robot Account, then set its properties:
Search for a Robot account Select the Robot account that you created.
Roles Designate roles for the Robot account.
Settings Select Machine login credentials.
Domain\Username <domain\username>
Credential Store Select Orchestrator Database.
Password <Softcard passphrase>
Credential type Select nShield Key Storage Provider.
The <domain\username> will be for the Robot machine account. To check the Robot username at the command prompt on the Robot machine, use whoami. If the nShield Key Storage Provider option does not exist, ensure theFeatures.SmartCardAuthentication.Enabledparameter is set toTrueinC:\Program Files(x86)\UiPath\Orchestrator\UiPath.Orchestrator.dll.config. -
Under Logging settings, select Login to console > YES.
-
Select Assign.
-
Assign the Robot Account to your folder:
-
Select the folder to be used and then Settings.
-
Select Assign Account/Group.
-
Enter and select the Robot Account previously created.
-
Designate roles.
-
Select Assign.
-
-
Upload a package:
Select Tenant > Packages > Upload.
-
Browse to a package to upload:
-
Select your Folder > Automations > Add process.
-
Create the process from the package that you previously uploaded.
-
The Orchestrator has been created and configured.
Connect the Robot Machine to the Orchestrator
To connect the Robot Machine to the Orchestrator:
-
On the Robot Machine, start UiPath Assistant from the Windows Start menu.
-
Select Preferences > Orchestrator Settings, and add the Orchestrator URL and the machine key that you created.
-
Select Connect.
The Robot can now be connected. The processes should now be viewable.