Procedures
AD DS Domain Controller: Configure the Domain to Support the AD FS Service
Perform the steps in this section on an AD DS (domain controller) system serving the AD FS server.
-
Open a PowerShell window to execute the commands in this section.
-
Create a Key Distribution Services, (KDS) Root Key so that Domain Controllers (DC) can begin generating gMSA passwords:
PS C:\> Add-KdsRootKey -EffectiveTime ((get-date).addhours(-10)) Guid ----- bdab22a0-16c1-b0eb-f46c-0638024f7fc9When the root key has been created, it will take several hours to propagate across to all Domain Controllers on the network.
-
Create the Group Managed Service Account (gMSA) to run the AD FS service:
New-ADServiceAccount <Name of AD FS gMSA> -DNSHostName <FQDN of AD FS service> -ServicePrincipalNames http/<Name of AD FS service>Example:
PS C:\> New-ADServiceAccount FedServgMSA -DNSHostName adfs.example.com -ServicePrincipalNames http/adfs.example.com -
Configure the AD FS Service Principal Name (SPN):
setspn -s http/<name of the AD FS service> <Name of AD FS gMSA>Example:
PS C:\> setspn -s http/adfs1.example.com example.com\FedServgMSAThis sometimes shows a duplicate SPN, with the following message:
Checking domain DC=domain,DC=com CN=FedServgMSA,CN=Managed Service Accounts,DC=domain,DC=com http/adfs.domain.com Duplicate SPN found, aborting operation! -
Create a DNS host record for your AD FS service name and its IP address:
-
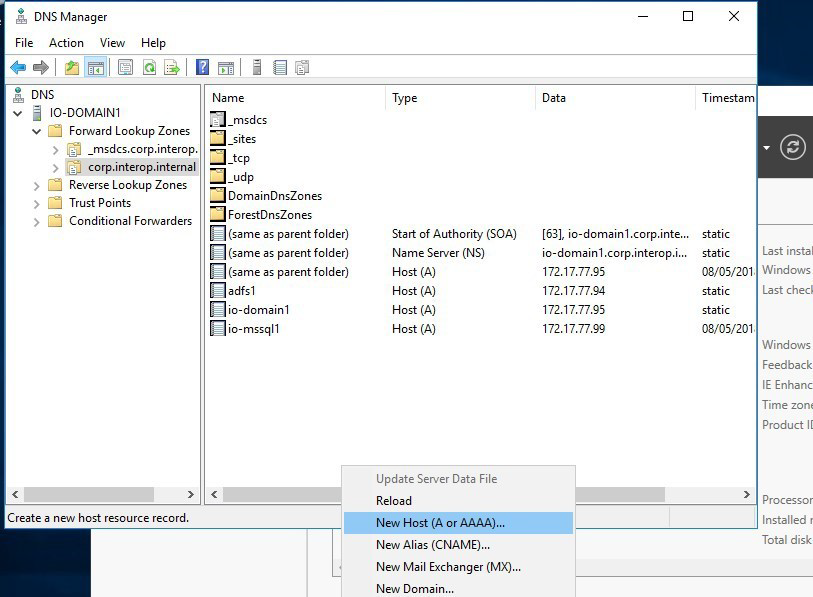
Using Server Manager, select Tools > DNS.
-
Select the Domain controller and then expand Forward Lookup Zones.
-
Select <your domain>.
-
Right-click either <your domain> in the left-hand pane or right-click in the right hand pane and select New Host (A or AAAA).
-
In New Host, enter:
Name <AD FS service name> (the FQDN will auto complete)
IP address <IP address of the AD FS host server>
-
Select Add Host at the bottom of the screen.
-
| Ensure command prompt or PowerShell is launched as Administrator. |
AD CS Server: Install and Configure AD CS Role
Perform the steps in this section on an AD CS(CA) system serving the AD FS server.
This Integration Guide relies on the availability of an Enterprise Microsoft AD CS (CA) server within the Active Directory forest. While it may be possible to use another CA product or an external CA for issuing AD FS certificates, the procedures are not in scope of this Integration Guide.
Follow the Microsoft installation and configuration procedures to deploy your CA. If you wish to deploy your Microsoft AD CS server using an nShield HSM for protection of the CA’s private signing key, see the Microsoft AD CS and OCSP Integration Guide.
AD FS Server: Create a TLS certificate template for use by AD FS
Perform the steps in this section on an AD CS (CA) system serving the AD FS server.
Create a TLS certificate template for use by AD FS as follows:
-
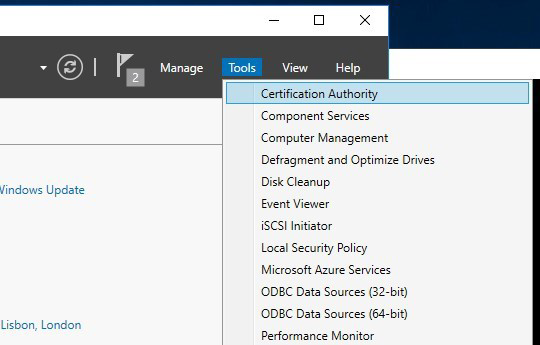
On an Issuing CA, open the Certification Authority management console.
-
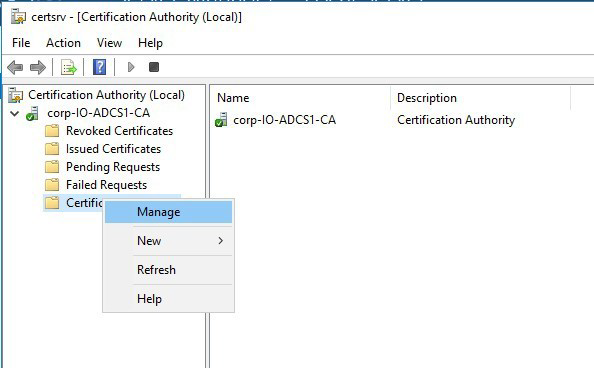
Expand the Certification Authority node in the left-hand pane, then right-click Certificate Templates and select Manage.
-
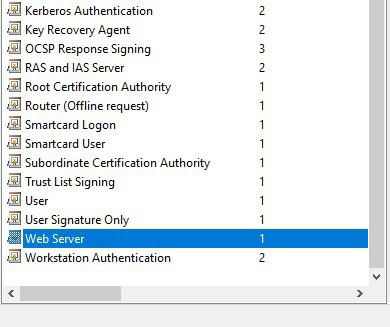
In the Certificate Templates Console, locate the Web Server certificate template, right-click it and from the context menu select Duplicate Template.
-
In the Properties of new template dialog, select the General tab.
-
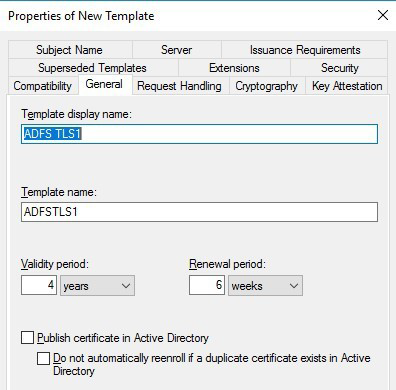
For Template display name, name the template, for example "ADFS TLS1".
-
Change the Validity Period to whatever value is desired.
-
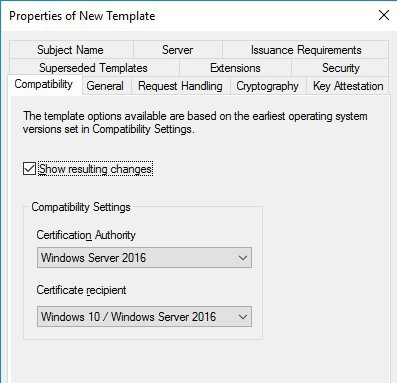
Select the Compatibility tab and change the Certification Authority to Windows Server 2016 and the Certificate Recipient to Windows 10/Windows Server 2016.
-
Select the Subject Name tab and make sure that Supply in the request is selected. This is because the AD FS service name will be different from the AD FS Server name and will need to be specified in the request.
-
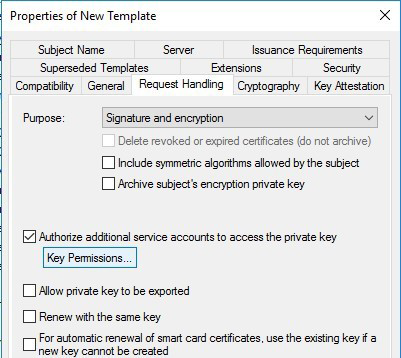
Select the Request Handling tab and under Purpose select Signature and encryption. Select Authorize additional service accounts to access the private key.
-
Select Key Permissions.
-
In the Permissions for screen, select Add.
-
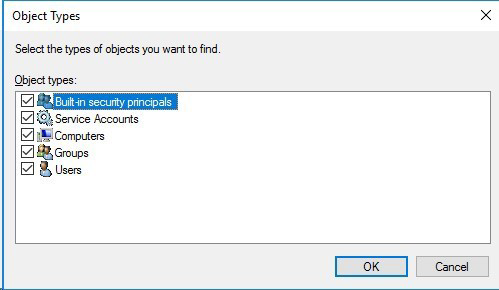
Select Object Types and then check the boxes for Service Accounts and Computers from the listed objects.
-
Select OK.
-
For Enter the object names to select, type in full/partial names for (separated by semicolons):
-
The Group Managed Service Account you created on your Domain Controller.
-
The AD FS server computer account.
-
-
Select the Advanced tab, select Find Now and select the Group Managed Service Account you created on your Domain Controller.
-
Select OK to add into Enter the object names.
-
Select OK.
-
Select Allow Full Control.
-
Repeat to add the AD FS server Computer account, make sure that the AD FS server Computer account has Full Control.
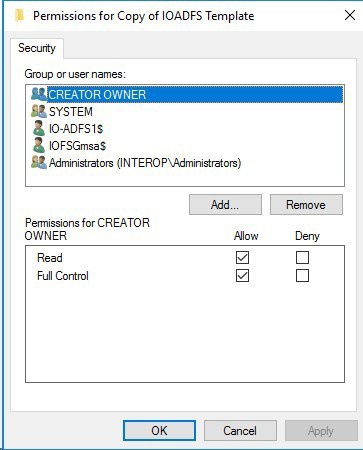
-
Select OK to close the Permissions for window.
-
Select the Cryptography tab. On this tab:
-
For Provider Category, select Key Storage Provider.
-
For Algorithm Name, select RSA.
-
Set the Minimum Key Size to at least 2048 for RSA.
-
Select Requests can use any provider available on the subject’s computer.
-
Select nCipher Security World Key Storage Provider.
-
For Request Hash, select SHA256.
-
-
Select the Security tab. On this tab:
-
Select Add
-
Select Object Types and then check the boxes for Service Accounts and Computers from the listed objects.
-
Select OK.
-
For Enter the object names to select, type in full/partial names for (separated by semicolons).
-
The Group Managed Service Account you created on your domain controller. That is, the AD FS server computer account(s) and the Domain Computers group.
-
Select Check Names to autocomplete (you may need to select Advanced to narrow down your search in large domains).
-
Select OK.
-
-
Back in the Security tab, for each account or system that was just added, select the check boxes in the Allow column labeled Read and Enroll. Do not modify the default permissions for any of the existing groups/users:
-
Authenticated Users should only have Read permission.
-
Administrator should have Read/Write permissions.
-
Domain Admins should have Read/Write/Enroll permissions.
-
Enterprise Admins should have Read/Write/Enroll permissions.
-
-
When all template configuration has been completed, select Apply and OK then close the Certificate Templates console.
-
Make sure that you are logged into the AD CA as Domain administrator.
-
Issue the new certificate template to the current CA:
-
Open the Certificate Authority console.
-
On the Server Manger Dashboard, go to Tools > Certificate Authority.
-
Under Certification Authority (local), expand the Domain (this is presented as a computer with a green tick next to it).
You may need to restart Active Directory Certificate Service to make sure the new template is available. -
Right-click Certificate Templates (last item from the list in the left-hand section).
-
Select New and then select Certificate Template to Issue.
-
Select the certificate template just created, and then select OK. The new template will now appear in the Certificate templates list.
-
-
Close the Certification Authority management console.
Security World client installation
Perform the steps in this section on the AD FS server
Install a compatible and supported version of the nShield Security World software (see the Validation Matrix in the introduction for more detail) on the designated AD FS server.
-
Sign in to the Windows workstation as an administrator.
-
Navigate to the location of the Security World software.
-
Install the Security World software:
-
Double-click on the Security World setup.msi to start installation.
-
At the Welcome screen select Next.
-
At the End-User License Agreement screen, accept the terms and then select Yes.
-
At the Product Features screen, select the appropriate packages for your environment and select Install.
-
The installation will begin installing the selected software components.
-
At the Completed screen, select Finish.
-
-
Add the Security World tools to the system path environment variable:
-
Navigate to Start > Windows System > Control Panel.
-
Navigate to System and Security.
-
Navigate to System.
-
On the left side of the System window, select Advanced system settings.
-
In the System Properties > Advanced tab that appears, select Environment Variables.
-
In the popup Environment Variables window, in the System Variables section, select Path and select Edit.
-
In the Edit environment variable dialog, select New.
-
In the text field that enables, enter in the additional path of
%NFAST_HOME%\binand select OK. -
Back in the Environment variables window, select OK.
-
Back in the System Properties window, select OK.
-
-
If using a Softcard or OCS with a passphrase (requires Security World client v12.71 or later — see section Validation Matrix for more detail), you will need to use the
preloadcommand to start the AD FS service, and thus must configure theNFAST_NFKM_TOKENSFILEsystem environment variable.-
Navigate to Start > Windows System > Control Panel.
-
Navigate to System and Security.
-
Navigate to System.
-
On the left side of the System window, select Advanced system settings.
-
In the System Properties > Advanced tab that appears, select Environment Variables.
-
In the popup Environment Variables window, in the System Variables section, select New.
-
For Variable name, select
NFAST_NKM_TOKENSFILE. -
For Variable value, enter
c:\nfast_nfkm_tokensfile(or another name/location of your choosing). -
Select OK.
-
Back in the Environment Variables window, select OK.
-
Back in the System Properties window, select OK.
-
-
If you are using the nShield Remote Administration cards, you must make sure that the cardlist file,
C:\ProgramData\nCipher\Key Management Data\config\cardlist, has either the relevant card serial number(s) (recommended) or contains a single line with a wildcard*(not recommended for production environments). See the contents of the defaultcardlistfile for more info. -
Close any open PowerShell or Command Prompt windows (when you open new ones later on, the system environment variables will be known in the new shells)
Configure the nShield HSM
Refer to the applicable User Guide for your nShield HSM for installation and configuration instructions.
If using an nShield Connect HSM or nShield-as-a-Service (nSaaS) HSM, be sure to perform the required procedures to enroll the AD FS server with the HSM (with the nethsmenroll command).
If you are using an nShield-as-a-Service (nSaaS) fully-managed environment, the nSaaS Operations Team will configure your HSM subscription and assist you with establishing a VPN connection to the HSM datacenter(s).
Once your server is configured to communicate with an HSM, verify the HSM connection with enquiry before continuing.
The output below should be similar:
PS C:\> enquiry -m 1
Module #1:
enquiry reply flags UnprivOnly
enquiry reply level Six
serial number EEEE-SSSS-NNNN
mode operational
version 12.50.11
speed index 15843
rec. queue 43..150
level one flags Hardware HasTokens SupportsCommandState
version string 12.50.11-270-fb3b87dd465b6f6e53d9f829fc034f8be2dafd13 2019/05/16 22:02:33
BST, Bootloader: 1.2.3, Security Processor: 12.50.11 , 12.70.8-0-dca4ca4
checked in 000000005cddcfe9 Thu May 16 21:02:33 2019
level two flags none
max. write size 8192
level three flags KeyStorage
level four flags OrderlyClearUnit HasRTC HasNVRAM HasNSOPermsCmd ServerHasPollCmds
FastPollSlotList HasSEE HasKLF HasShareACL HasFeatureEnable HasFileOp HasLongJobs
ServerHasLongJobs AESModuleKeys NTokenCmds JobFragmentation LongJobsPreferred Type2Smartcard
ServerHasCreateClient HasInitialiseUnitEx AlwaysUseStrongPrimes Type3Smartcard HasKLF2
module type code 12
product name nC3025E/nC4035E/nC4335N
device name Rt3
EnquirySix version 7
impath kx groups DHPrime1024 DHPrime3072 DHPrime3072Ex
feature ctrl flags LongTerm
features enabled StandardKM EllipticCurve ECCMQV AcceleratedECC HSMHighSpeed
version serial 37
connection status OK
connection info esn = EEEE-SSSS-NNNN; addr = INET/10.0.0.253/9004; ku hash = bf83413225927f7d5c3795d03c645d408be24f24, mech = Any
image version 12.70.8-358-dca4ca4
level six flags none
max exported modules 1000
rec. LongJobs queue 42
SEE machine type PowerPCELF
supported KML types DSAp1024s160 DSAp3072s256
using impath kx grp DHPrimeMODP3072
active modes UseFIPSApprovedInternalMechanisms AlwaysUseStrongPrimes
hardware status OK| Ensure to verify the following: HSM serial number, the version, features enabled, version serial, connection info, and image version. |
| Ensure command prompt or PowerShell is launched as Administrator. |
Create or load a Security World
Refer to the applicable User Guide for your nShield HSM for instructions on creating or loading a Security World that fits your organizational security requirements. If you are using an nShield-as-a-Service (nSaaS) fully-managed environment, the Entrust nSaaS Operations Team will create the Security World for you and provide you with the necessary world data files for your AD FS server.
A valid Security World must be loaded in the HSM, and world data must exist in the AD FS server in the C:\ProgramData\nCipher\Key Management Data\local folder before continuing to the next section.
Ensure you have properly created a Softcard or Operator Card Set (OCS) if you plan on using either of these to protect your AD FS keys. Refer to the applicable nShield User Guide for instructions.
Check the world status using nfkmcheck before continuing to the next section.
For a FIPS 140 Level 2 Security World, the output should resemble the following:
PS C:\> nfkmcheck
nfkmcheck: information: Module #1 Slot #0 Empty
nfkmcheck: everything seems to be in orderFor a FIPS 140 Level 3 Security World, the following output should resemble the following:
PS C:\> nfkmcheck
nfkmcheck: information: World requires administrator authorization
nfkmcheck: information: Module #1 Slot #0 Empty
nfkmcheck: everything seems to be in order| Ensure command prompt or PowerShell is launched as Administrator. |
Application key tokens
Application key tokens are an encrypted form of a Security World generated cryptographic key. These key tokens must not be mistaken for or regarded as being a Key in or of itself. The key is at all times obfuscated in this encrypted form and is only available for use as a cryptographic key when copied to the FIPS 140 Level 3 security boundary of a correctly configured nShield HSM.
| If you intend to use a web application proxy server, and your HSM must be configured for a FIPS 140 level 3 Security World, you should consider deploying a software-based SSL certificate. In level 3 mode, keys cannot be exported, which is required for configuring a WAP in front of the AD FS server. This guide does not cover deployment using a Web Application Proxy. |
Install and register the CNG provider
It is possible to use the CNG wizard to either load (reuse) an existing Security World instance or create a new instance. If you are creating a new Security World, see Installation Guide and User Guide for your HSM on the information required to define Security World parameters. The HSM must be properly configured before running the CNG installation wizard.
To confirm the HSM is available:
-
Open a CLI as Administrator. You must run cmd with elevated privileges. To do this, right-click the cmd icon and select Run as administrator.
-
Run the command:
enquiryServer: and Module #1: should be reported showing the serial number (in form eeee-ssss-nnnn) of the module and hardware status as OK (this can be found at the bottom of the section detailing information on the module #).
If you are using an existing Security World, you can check to make sure it is available by running the command nfkminfo. Look at the state line of the output it should be reported as initialized and usable. There should be no ! prefix. -
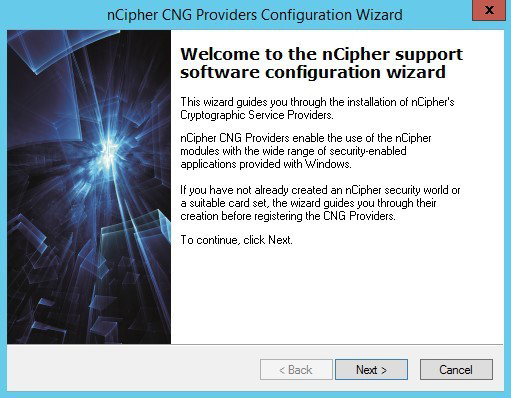
When the Security World software is operational, you must run the CNG install wizard to install and register the nShield Key Storage Provider (KSP). This can be performed via the CNG install wizard that can be found in the Start menu of the desktop > nCipher > CNG Configuration Wizard.
-
Select Start and look for the recently added nShield utilities, double-click the CNG configuration wizard. If the User Access Control prompt appears, select YES to continue.
-
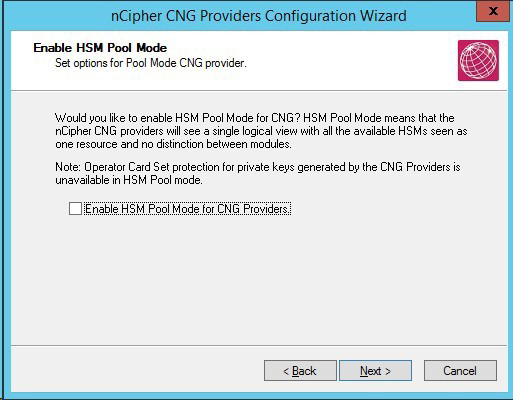
The Enable HSM Pool Mode screen prompts you to Enable HSM Pool Mode for CNG Providers. Leave the default value, make sure that the check box is clear, and select Next.
-
At the Initial Setup screen, your security world should have already been created or loaded in the section Create or Load a Security World. Choose Use the existing security world and select Next.
-
Make sure that the Set Module States screen, ensure module 1 shows both
operationalandusablethen select Next. -
At the Key Protection Setup screen choose Allow any protection method to be selected in the GUI when generating and select Next.
-
At the Software Installation screen, select Next.
-
At the Finish registering the nCipher Providers screen, select Finish.
-
The nShield CNG providers will now be installed and the KSP will be registered. To confirm that the KSP has been successfully registered open either a CLI or PowerShell (right-click and Run as Administrator) and run the following command:
>cnglist.exe --list-providers PS C:\WINDOWS\system32> cnglist.exe --list-providers Microsoft Key Protection Provider Microsoft Passport Key Storage Provider Microsoft Platform Crypto Provider Microsoft Primitive Provider Microsoft Smart Card Key Storage Provider Microsoft Software Key Storage Provider Microsoft SSL Protocol Provider Windows Client Key Protection Provider nCipher Primitive Provider nCipher Security World Key Storage Provider PS C:\WINDOWS\system32>You should see the nCipher Security World key Storage Provider listed.
Install and register the CSP Provider
Run 64bit CSP install wizard through Start menu under Entrust nShield Security World.
-
On the start menu select Next.
-
Select Next on the Enable HSM Pool Mode Screen.
-
Select Next on the Initial Set Up Screen.
-
Select Next on the Set Module States Screen.
-
Select Module Protection.
-
Select Next on the Software Installation Screen.
-
Select Finish.
Ensure command prompt or PowerShell is launched as Administrator. -
Reboot the server.
AD FS Server: Request an SSL/TLS certificate for use on the AD FS server
The instructions in this section assume that all certificates for AD FS will be issued from an Enterprise Microsoft AD CS (CA) server within the Active Directory forest The certificate template to be used was previously configured in section AD FS Server: Create a TLS certificate template for use by AD FS. Configuring AD FS for use with a different CA product or an external PKI is not in scope of this integration guide.
Four keys/certificates will be created for use by AD FS. You can create all four of these keys/certificates before installing the AD FS role, so they will be ready for use in later sections. The critical parameters for these objects are as follows (tailor these for your environment), which will be referenced in the steps to follow:
| AD FS Token-Decrypting cert will later be modified to use CAPI. Module protection must be used for this specific certificate during this integration. |
| Protection | Crypto Provider | Common Name | Alternative Name(s) | Friendly Name |
|---|---|---|---|---|
Software |
RSA,Microsoft Software Key Storage Provider |
adfs.domain.com |
adfs.domain.com, certauth.adfs.domain.com |
AD FS TLS Software Key |
HSM |
RSA,nCipher Security World Key Storage Provider |
adfs.domain.com |
adfs.domain.com, certauth.adfs.domain.com |
AD FS TLS HSM Key |
HSM |
RSA,nCipher Security World Key Storage Provider |
AD FS Token-Signing Key |
N/A |
AD FS Token-Signing HSM Key |
HSM |
RSA,nCipher Security World Key Storage Provider |
AD FS Token-Decrypting Key |
N/A |
AD FS Token-Decrypting HSM Key |
Make sure the new certificate template is visible within the domain, run gpupdate to refresh the Group Policy before proceeding
Open a command prompt opened as Administrator and run gpupdate:
gpupdate /force
Updating Policy...
User Policy update has completed successfully.
Computer Policy update has completed successfully.If using Security World 13.6.8 with softcard protection, run the following command before continuing. Otherwise, certificate enrollment fails.
preload --reload-everything --softcard-name=<Softcard Name> pause-
On the AD FS server, open
certlm.mscusing theRuncommand or an administrator level command prompt. -
From the left-hand panel beneath Certificates-Local Computer, right-click the Personal folder, select All Tasks > Request New Certificate.
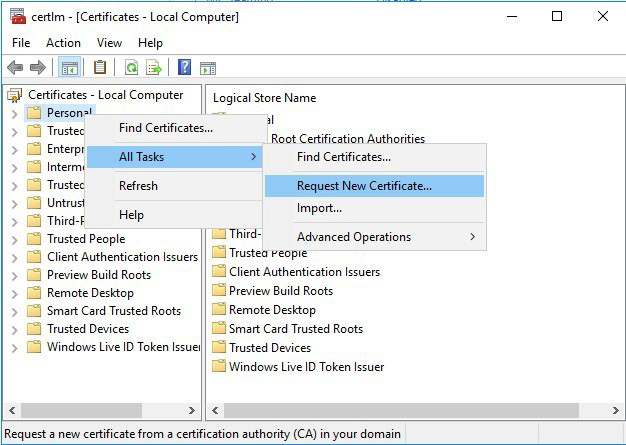
-
The Certificate Enrollment wizard will start, select Next.
-
On the Select Certificate Enrollment Policy screen, select Next.
-
The Request Certificates window should display the recently created certificate template, select the link More information is required to enroll for this certificate. Click here to configure settings to continue.
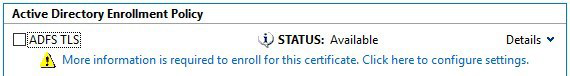
-
On the Certificate Properties window, in the Subject tab:
-
Under Subject Name, in Type choose Common Name.
-
In Value, enter the value from the Common Name field in the table at the beginning of this section.
-
Select Add.
-
Under Alternative name, in Type choose DNS.
-
In Value, enter the value from the Alternative Name field in the table at the beginning of this section. If there is no alternative name required as shown in the table, this step can be skipped. Select Add.
Repeat this process if more than one alternative name is required.
-
-
On the General tab, specify a sensible and recognizable name for the certificate.
-
Select the Private Key tab and expand the Cryptographic Service Provider and select the appropriate provider defined in the table at the beginning of the section. Make sure that only one provider is checked. Uncheck all of them except the one you need.
-
For a software-based key, choose RSA,Microsoft Software Key Storage Provider.
-
For an HSM-based key, choose RSA,nCipher Security World Key Storage Provider.
-
-
Select OK to close the Certificate Properties window.
-
On the Certificate Enrollment, Request Certificates window, check the box for the certificate just requested, and then select Enroll.
-
For HSM-based keys, the nCipher Key Storage Provider - Create Key wizard will appear.
-
At the Create new key screen, select Next.
-
At the Select a method to protect new key screen, select the desired key protection mechanism to use. For module, select Module protection and select Finish. For Softcard select Softcard protection and select Next.
-
At the Select token to protect key with screen select the appropriate Softcard from the list and select Finish.
-
When prompted for the passphrase (if required) enter it and select Finish.
-
-
For OCS select Operator Card Set protection and select Next.
-
At the Select token to protect key with screen select the appropriate OCS from the list and select Finish.
-
At the Loading "<OCS name>" screen, insert a card from the selected OCS.
-
When the OCS card has been read, if it has a passphrase, enter it now and select Next.
-
If using a k/n OCS with k>1, repeat to load other OCS cards until quorum is made.
-
After loading the required card(s), at the Card reading complete screen, select Finish.
-
The Certificate Installation Results window should show STATUS: Succeeded, select Finish.
Repeat these steps until all four certificates have been generated. -
Verify the new HSM keys:
-
Open a cmd window as Administrator and run
nfkminfo.exesimilar to the example below This will print the CNG key created via the Certificate template. The key will have been generated using the nShield Key Storage Provider. It is possible to use the key’sAppNameand itsIdentto show further details.Example:
PS C:\> nfkminfo -l OUTPUT: key_caping_machine--c4ce33928f457a19dd5a536a9038b55f02a2eaf1 `te-ADFSTLS-3ec97a8c-791a-4139-a0e6-ecbf1e185bd8` PS C:\> nfkminfo -k caping machine--c4ce33928f457a19dd5a536a9038b55f02a2eaf1 OUTPUT: Key AppName caping Ident machine--c4ce33928f457a19dd5a536a9038b55f02a2eaf1 BlobKA length 1052 name "te-ADFSTLS-3ec97a8c-791a-4139-a0e6-ecbf1e185bd8" hash 42b4875c0a2fc7af57fa8a904939c4a361c30ff9 recovery Enabled protection Module other flags PublicKey !SEEAppKey !NVMemBlob +0x0 gentime 2021-09-10 19:49:17 SEE integrity key NONE PS C:\> certutil -silent -store MY tq-ADFSKeys-9ad0688f-4686-4368-9586-95dc5a89c672 OUTPUT: Serial Number: 610000000d4ee2b718a2dd02ef00000000000d Issuer: CN=DOMAIN ENTERPRISE ROOT CA, DC=domain, DC=com NotBefore: 9/17/2021 10:07 PM NotAfter: 9/17/2023 10:17 PM Subject: CN=ADFS Token-Decrypting Key Non-root Certificate Template: ADFSKeys, ADFS Keys Cert Hash(sha1): dc36ce9322cc6be72acf6c073861105074d036cb Key Container = tq-ADFSKeys-9ad0688f-4686-4368-9586-95dc5a89c672 Provider = nCipher Security World Key Storage Provider Encryption test FAILED -
In the first output, copy the key hash for the next command, then verify the
Protectionfield for the proper protection type.Modulefor module protection,PassPhrasefor Sard protection, andCardSetfor OCS protection.The hash may not match the ones generated for your system. -
Save the name of the output of the second command for the last command.
-
Verify the
Providerfield to ensure the proper Key Storage Provider has been used.
-
| Ensure command prompt or PowerShell is launched as Administrator. |
Install the AD FS server role
Perform the steps in this section on the AD FS server.
This can be done manually in the Server Manager.
-
Open Server Manager.
-
In Server Manager, navigate to Manage > Add Roles and Features.
-
On the Before you begin page (if it appears), select Next.
-
On the Select installation type page, select Role-based or feature-based installation, and then select Next.
-
On the Select destination server page, select Select a server from the server pool, verify that the target computer is selected, and then select Next.
-
On the Select server roles page, check the box for Active Directory Federation Services and select Next.
-
On the Select features page, select Next.
-
On the Active Directory Federation Service (AD FS) page, select Next.
-
Verify the information on the Confirm installation selections page then select Install.
Do not select the Restart the destination server automatically if required check box. -
On the Installation progress page, wait for everything to install correctly.
-
Once the installation has completed, select Close.
Configure the AD FS server
This step can be completed manually in the Server Manager.
-
In Server Manager, initiate post-deployment configuration for the AD FS role.
-
At the Welcome screen, select Create the first federation server in a federation server farm, select Next.
-
In the Connect to Active Directory Domain Services page, select the account you want to use to perform the configuration (the currently logged-on account if you have admin rights, which you will need to configure the role) then select Next.
-
On the Specify Service Properties window:
-
Select the appropriate SSL Certificate from the list. Choose the software-based TLS key previously generated, which should be first in the list. This will be replaced later with an HSM-based key. If you need to, select the View link to verify the certificate serial number (since both the software and HSM based credentials will be the FQDN of the AD FS service.
-
In Federation Service Name, ensure the same FQDN is shown (the first Alternative Name, the one that matches the certificate common name.
-
For Federation Service Display Name, enter a meaningful name for the AD FS service.
-
Select Next.
-
-
On the Specify Service Account page:
-
Select Use an existing domain user account or group Managed Service Account.
-
Select Select.
-
Enter the name of the gMSA account that was created on the domain controller.
-
Select Check Names, the account should be found.
-
Select OK.
-
Select Next.
-
-
On the Specify Configuration Database page, select Create a database on this server using Windows Internal Database, and then select Next.
-
On the Review Options page, verify your configuration selections then select Next.
-
On the Prerequisite Checks page, verify that all prerequisite checks completed successfully then select Configure.
-
On the Results page you should see a green tick against This server was successfully configured.
-
You may be informed that a machine restart is required.
-
Select Close to exit the configuration.
-
In Services, make sure to configure Active Directory Federation Services to start manually. If you are using OCS or Softcard protection for your AD FS integration with the HSM, some sort of manual interaction will be required to start the service.
At this point, the AD FS server should be restarted.
Once it has rebooted, sign in as Administrator.
Prepare the AD FS Keys for rollover
-
Ensure the AD FS service is stopped.
net stop adfssrv -
Ensure any existing preload cache is reset.
preload exit -
Remove the
NFAST_NFKM_TOKENSFILEcache (if it exists) by deleting the filec:\nfast_nfkm_tokensfile.del c:\nfast_nfkm_tokensfile -
Preload the keys into the HSM if necessary:
-
For module protected keys, go to the next step.
-
For Softcard protected keys:
preload --reload-everything --softcard-name=<Softcard Name> pause -
For OCS protected keys:
preload --reload-everything --cardset-name=<OCS Name> pauseThis preload command will intentionally pause until cancelled. You will cancel this in a later step.
-
-
In a separate PowerShell window, start the AD FS service.
net start adfssrv
| Ensure command prompt or PowerShell is launched as Administrator. |
Check and enable the AD FS install and sign-on page
The AD FS sign-on page is not enabled by default in Windows 2016 and later. To enable and allow verification of a successful installation, open a PowerShell CLI as Administrator and run the following command:
PS C:\Users\Administrator.DOMAIN> Set-AdfsProperties -EnableIdPInitiatedSignonPage $true-
Open Internet Explorer.
-
Add the AD FS server FQDN to the local intranet zone.
-
Add the web page to Trusted Sites:
-
Navigate to Internet Options > Security > Trusted Sites.
-
Select Sites.
-
In Add this website to the zone, the web site should be populated automatically. Select Add.
-
Select Close.
-
Select OK to close the Internet Options window.
-
-
Navigate to https://adfs.domain.com/adfs/ls/idpinitiatedsignon.aspx (substitute your correct FQDN of the AD FS service).
-
You should see the AD FS sign in screen, enter your credentials to sign in AD FS.
-
You should also successfully be able to pull the AD FS configuration XML from https://adfs.domain.com/federationmetadata/2007-06/federationmetadata.xml.
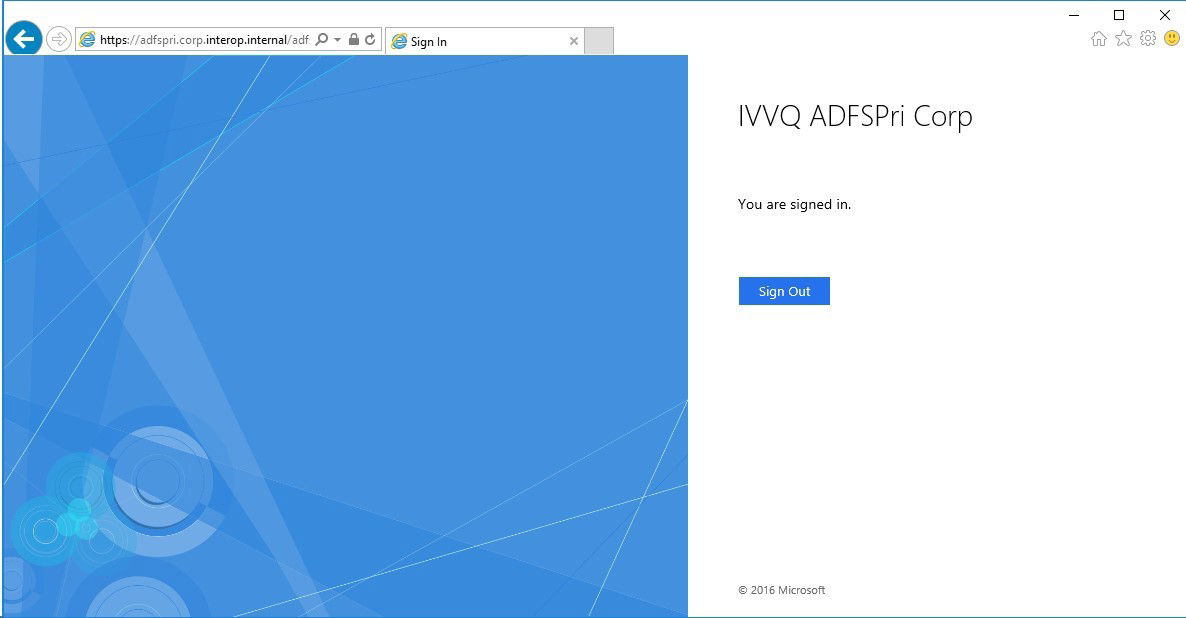
| Ensure command prompt or PowerShell is launched as Administrator. |
Configure AD FS to use the nShield HSM
Perform the steps in this section on the AD FS server.
| When using AD FS certificates that have keys protected by an HSM, they cannot automatically rollover when nearing expiration. As such, AD FS will not allow you to manually rollover certificates (in this case, from software-based keys to HSM-based keys) without first disabling the AutoCertificateRollover property. |
-
On the AD FS server, open a Powershell command prompt as Administrator.
-
Run the following command:
> Set-AdfsProperties -AutoCertificateRollover $false
| The Token-decryption and Token-signing certificates initially created by the AD FS role configuration are software-based and self-signed, and the initial TLS key was generated in software. This steps in this section will add new keys for Token-decryption, Token-signing, and TLS communication created earlier. Which improves the security of the solution. |
| For keys protected by Softcard or OCS, there should still be a preload session. |
Roll the AD FS Certificates from Default Objects to HSM Objects, this can be done manually on the AD FS Management Console.
-
Update the SSL Certificate object to use the new HSM-backed certificate/key in a PowerShell window running as Administrator:
For customers that installed the desired end-state SSL certificate during AD FS role configuration, there is no need to roll the SSL cert at this time. Skip to the next step (Service-Communications certificate). If you intend to use a Web Application Proxy (which is not covered in this guide), you may want to keep the SSL/TLS certificate as a software-protected key. Refer to Microsoft guidance for requirements to configure a Web Application Proxy. -
Get the current state of the certificate configuration:
Get-AdfsSslCertificate HostName PortNumber CertificateHash -------- ---------- --------------- adfs.domain.com 443 92E09233FF55F16A661AB417845C04FF3EC8F68E localhost 443 92E09233FF55F16A661AB417845C04FF3EC8F68E certauth.adfs.domain.com 443 92E09233FF55F16A661AB417845C04FF3EC8F68E -
Locate the certificate thumbprint of the new HSM-backed SSL key (locate the object with the nCipher Security World Key Storage Provider and capture its
Cert Hash(sha1)field for later use:certutil -silent -store my "adfs.domain.com" Serial Number: 610000000b29ee27dd2a24900c00000000000b Issuer: CN=DOMAIN ENTERPRISE ROOT CA, DC=domain, DC=com NotBefore: 9/17/2021 10:06 PM NotAfter: 9/17/2023 10:16 PM Subject: CN=adfs.domain.com Non-root Certificate Template: ADFSKeys, ADFS Keys Cert Hash(sha1): 6c4d3d71556303f42d5813d87836757a4a07f2ac Key Container = tq-ADFSKeys-8ca805b2-5e51-495f-a223-59d6fcf3c4db Provider = nCipher Security World Key Storage Provider Encryption test FAILED -
Set the certificate object to point to the new HSM-backed certificate:
Set-AdfsSslCertificate -Thumbprint 6c4d3d71556303f42d5813d87836757a4a07f2ac WARNING: PS0344: ADFS is configured to use Alternate TLS client binding. This command will not modify Alternate TLS client binding. If you want to modify Alternate TLS client binding too, please use the cmdlet 'Set-AdfsAlternateTlsClientBinding'. -
Get the updated state of the certificate configuration - notice how the
certauthobject did not change, and there is a new object at port49443:Get-AdfsSslCertificate HostName PortNumber CertificateHash -------- ---------- --------------- certauth.adfs.domain.com 443 92E09233FF55F16A661AB417845C04FF3EC8F68E localhost 443 6C4D3D71556303F42D5813D87836757A4A07F2AC adfs.domain.com 443 6C4D3D71556303F42D5813D87836757A4A07F2AC adfs.domain.com 49443 6C4D3D71556303F42D5813D87836757A4A07F2AC -
To correct the certauth object, update the alternate TLS client binding (ignore the warning):
Set-AdfsAlternateTlsClientBinding -Force $true -Member "certauth.adfs.domain.com" -Thumbprint "6c4d3d71556303f42d5813d87836757a4a07f2ac" Set-AdfsAlternateTlsClientBinding : PS0317: One or more of AD FS servers returned errors during execution of command 'Set-AdfsAlternateTlsClientBinding'. Error information: PS0316: AD FS Server: 'certauth.adfs.domain.com', Error: 'Connecting to remote server certauth.adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error occurred while using Kerberos authentication: Cannot find the computer certauth.adfs.domain.com. Verify that the computer exists on the network and that the name provided is spelled correctly. For more information, see the about_Remote_Troubleshooting Help topic.'. At line:1 char:1 + Set-AdfsAlternateTlsClientBinding -force $true -member "certauth.adfs ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : NotSpecified: (:) [Set-AdfsAlternateTlsClientBinding], RemoteException + FullyQualifiedErrorId : RuntimeException,Microsoft.IdentityServer.Management.Commands.SetAlternateTlsClientBinding -
Get the updated state of the certificate configuration (all the certificate hashes should match now):
Get-AdfsSslCertificate HostName PortNumber CertificateHash -------- ---------- --------------- certauth.adfs.domain.com 443 6C4D3D71556303F42D5813D87836757A4A07F2AC localhost 443 6C4D3D71556303F42D5813D87836757A4A07F2AC adfs.domain.com 443 6C4D3D71556303F42D5813D87836757A4A07F2AC adfs.domain.com 49443 6C4D3D71556303F42D5813D87836757A4A07F2AC -
Remove the new addition on port
49443:netsh http delete sslcert hostnameport=adfs.domain.com:49443 SSL Certificate successfully deleted -
Get the updated state of the certificate configuration (everything should look good now):
Get-AdfsSslCertificate HostName PortNumber CertificateHash -------- ---------- --------------- certauth.adfs.domain.com 443 6C4D3D71556303F42D5813D87836757A4A07F2AC localhost 443 6C4D3D71556303F42D5813D87836757A4A07F2AC adfs.domain.com 443 6C4D3D71556303F42D5813D87836757A4A07F2AC
-
Change the Token-Decrypting Certificate from CNG to CAPI
| CAPI certs are only supported with Module Protection during this integration. |
Microsoft only supports CAPI for the Token-Decrypt certificate, therefore we must edit it from using CNG to use CAPI:
-
Open a PowerShell as administrator, create a container for the ms capi (ncipher CSP) key:
cd "c:\program files\ncipher\nfast\bin"keytst -c -m adfstokendecrypt CSP being used: nCipher Enhanced Cryptographic Provider Container 'adfstokendecrypt' created -
List all of the containers:
csputils -U ALL -m File ID Container name Container owner DLL name S X ========= =================== =================== ========= = = cb551513e adfstokendecrypt MACHINE ncsp 1 container and 0 keys found. -
Find the container you just created by name and go to the left hand column and get the FILEID of that container.
-
To find your ADFS Token-Decrypting Key IDENT value, for example, key_caping-machine-IDENT, run:
nfkminfo -l Keys with module protection: key_caping_machine--0e29b54e36c1a2006981a7a8ca6234fd6cf15bed `te-ADFSTLS-dc716c04-87e1-417e-9ec6-5fb9928de1fc' key_caping_machine--2c21df63f288ed189ef4f1e6af9b781ae2c6c031 `te-ADFSTLS-1d0559b1-2759-4645-991c-8d7838097e6a' key_caping_machine--5d9f162dec839f3e4250af803fb0a81415359ed1 `te-ADFSTLS-9b36d23f-397a-48a2-adc4-f03888c145d9'The IDENT can additionally be located in the generated certificate file name located at C:\ProgramData\nCipher\Key Management Data\local. -
Now run the following command and type yes if prompted, see the next line for an example:
cspimport -i -k machine--IDENT -a caping FILEID exchange -
Now we have the key imported into the CSP container as a machine and exchange key.
-
Move the original ADFS Token-Decrypting Key key-caping-machine out of C:\ProgramData\nCipher\Key Management Data\local or else it will continue to use CNG. The new CAPI container and cloned key should remain in local.
-
Run the following command:
certutil -store my ================ Certificate 3 ================ Serial Number: 18000000047adbec8d4cc951f5000000000004 Issuer: CN=ADFSWIN2022-3, DC=interop, DC=local NotBefore: 7/30/2024 8:26 AM NotAfter: 7/30/2026 8:26 AM Subject: CN=ADFS Token-Decrypting Key Non-root Certificate Template: ADFSTLS, ADFS TLS Cert Hash(sha1): 03a19f17154193a70231c19dcdf64f91c496cf8e Key Container = te-ADFSTLS-d223bf5d-ab52-4753-a401-06f82de95711 Provider = nCipher Security World Key Storage Provider Private key is NOT exportable ERROR: Could not verify certificate public key against private key CertUtil: -store command completed successfully. -
Get the signing cert Serial Number from the above command and use it in the next command.
certutil -f -repairstore -csp "nCipher Enhanced Cryptographic Provider" my "18000000047adbec8d4cc951f5000000000004" . my "Personal" ================ Certificate 3 ================ Serial Number: 18000000047adbec8d4cc951f5000000000004 Issuer: CN=ADFSWIN2022-3, DC=interop, DC=local NotBefore: 7/30/2024 8:26 AM NotAfter: 7/30/2026 8:26 AM Subject: CN=ADFS Token-Decrypting Key Non-root Certificate Template: ADFSTLS, ADFS TLS Cert Hash(sha1): 03a19f17154193a70231c19dcdf64f91c496cf8e cbData: 14 ==> 40 Key Container = adfstokensign Provider = nCipher Enhanced Cryptographic Provider Private key is NOT exportable ERROR: Could not verify certificate public key against private key nCipher Enhanced Cryptographic Provider: KeySpec=1 AES256+RSAES_OAEP(RSA:AT_KEYEXCHANGE) test passed ================ Begin force NCrypt ================ Private key is NOT exportable ERROR: Could not verify certificate public key against private key nCipher Security World Key Storage Provider: KeySpec=0 AES256+RSAES_OAEP(RSA:CNG) test passed ---------------- End force NCrypt ---------------- CertUtil: -repairstore command completed successfully. -
Now the ADFS Decrypting Certificate is linked to the key in the MS CAPI nCipher provider.
-
For the Decryption Certificate you should see "Provider = nCipher Enhanced Cryptographic Provider" when you run the below command:
certutil -store my
Add HSM protected certificates to the AD FS server
-
Navigate to Start > Windows Administrative Tools > AD FS Management.
-
Expand the ADFS folder and navigate to Service > Certificates.
-
Update the Service-Communications object to use the new HSM-backed certificate/key:
-
Right-click on Certificates and select Set Service Communication Certificate.
-
In the Select a service communication certificate screen, select More Choices and select the newly created HSM-based TLS certificate. You may have named it as AD FS TLS HSM Key.
-
A dialog appears if the AD FS cannot determine the keyspec of the key. Select OK.
-
A warning will pop up advising you to make sure the private key is accessible for each AD FS server, select OK.
All AD FS services in the cluster must contain the same keys/certificates, so you will need to copy the HSM key(s) to other AD FS systems in the cluster, restore their CNG linkage, and configure AD FS with those key(s). The procedures for performing this are not in scope of this Integration Guide. -
The new certificate should be visible in the middle pane; you can double-click on the certificate to view its properties.
-
-
Update the Token-Decrypting object to use the new HSM-backed certificate/key:
-
Right-click on Certificates and select Add Token-Decrypting Certificate.
-
In the Select a token-decrypting certificate screen, select More Choices and select the newly created HSM-based token-decrypting certificate and select OK You may have named it as AD FS Token-Decrypting HSM Key.
-
A dialog appears if the AD FS cannot determine the keyspec of the key. Select OK.
-
A warning will pop up advising you to make sure the private key is accessible for each AD FS server, select OK.
All AD FS services in the cluster must contain the same keys/certificates, so you will need to copy the HSM key(s) to other AD FS systems in the cluster, restore their CNG linkage, and configure AD FS with those key(s). The procedures for performing this are not in scope of this Integration Guide. -
The new certificate should be visible in the middle pane; you can double-click on the certificate to view its properties.
-
In the middle pane, right-click on the new HSM token-decrypting certificate and select Set as Primary.
-
Do NOT delete the original certificate (yet), which should now be marked as Secondary.
-
-
Update the Token-Signing object to use the new HSM-backed certificate/key:
-
Right-click on Certificates and select Add Token-Signing Certificate.
-
In the Select a token-signing certificate screen, select More Choices and select the newly created HSM-based token-signing certificate and select OK. You may have named this as AD FS Token-Signing HSM Key.
-
A dialog appears if the AD FS cannot determine the keyspec of the key. Select OK.
-
A warning will pop up advising you to make sure the private key is accessible for each AD FS server, select OK.
All AD FS services in the cluster must contain the same keys/certificates, so you will need to copy the HSM key(s) to other AD FS systems in the cluster, restore their CNG linkage, and configure AD FS with those key(s). The procedures for performing this are not in scope of this Integration Guide. -
The new certificate should be visible in the middle pane; you can double-click on the certificate to view its properties.
-
In the middle pane, right-click on the new HSM token-signing certificate and select Set as Primary.
-
When warned about setting this certificate as primary, select Yes.
Setting a new token-signing certificate as primary could break trust relationships with relying parties that do not yet have the certificate. If this is an existing AD FS infrastructure, make sure you coordinate this activity prior to performing this step. -
Do NOT delete the original certificate (yet), which should now be marked as Secondary.
-
-
Close the AD FS Management Console.
At this point, restart the AD FS Service:
-
Stop the AD FS service:
net stop adfssrv -
If
preloadis still running inpausemode in another window, go back to that window and use[CTRL]-[C]to break the pause and return to the command prompt. -
Clear the preload state:
preload exit -
Remove the
NFAST_NFKM_TOKENSFILEcache:del c:\nfast_nfkm_tokensfile -
Verify the preload cache is clear:
nfkminfo -p <...snip all but last line...> No Pre-Loaded Objects
To restart AD FS, refer to the chosen HSM Key protection mechanism below for instructions:
-
For module protected HSM Keys:
-
Stop the AD FS service via the command prompt as follows:
net stop adfssrv -
Start the AD FS service via the command prompt as follows:
net start adfssrv
-
-
For Softcard protected HSM Keys:
-
Stop the AD FS service via command prompt as follows:
net stop adfssrv preload exit del c:\nfast_nfkm_tokensfile -
Start the AD FS service via command prompt as follows:
preload --reload-everything --softcard-name=<Softcard name> net start adfssrv
-
-
For OCS protected HSM Keys:
-
Stop the AD FS service via the command prompt as follows:
net stop adfssrv preload exit del c:\nfast_nfkm_tokensfile -
Start the AD FS service via command prompt as follows:
preload --reload-everything --cardset-name=<OCS Name> net start adfssrv
-
| Ensure command prompt or PowerShell is launched as Administrator. |
Test AD FS
Sign in to the AD FS web page (in the integration steps we used https://adfs.domain.com/adfs/ls/idpinitiatedsignon.aspx to ensure the service is working properly. The sign-in process should be successful.