Procedures
Install and configure Entrust KeyControl
To install and configure the Entrust KeyControl server cluster, see KeyControl Installation and Upgrade Guide. For information on configuring Entrust KeyControl as a KMIP server, see KeyControl KMIP Vault Overview.
Make sure the Entrust KeyControl Vault gets created and KMIP certificates are generated for Cohesity. These certificates are used in the configuration of the KMS described below.
Deploy Cohesity DataProtect
Deploy Cohesity DataProtect as described in the Cohesity user documentation: https://docs.cohesity.com/.
Create Cohesity client certificates in KeyControl
Before we can enable encryption, Cohesity and the KeyControl server must establish a mutual trust relationship. Client certificates are required to facilitate two-way KMIP communications between the KeyControl server and Cohesity. To perform this operation, create the certificate bundle as described in the Managing KMIP Client Certificates section of the Entrust KeyControl Admin Guide.
The configuration was tested using certificates without password protection. This client certificate is used to securely authenticate with the Entrust KeyControl server. After you create and download these certificates, you need to upload or import them into the Cohesity appliance.
-
Log in to the Entrust KeyControl server.
-
Select the Security icon, then select Client Certificates > +.
-
In the Create a New Client Certificate dialog, enter the Certificate Name and Expiration Date.
-
Leave the Password field blank.
This integration requires a password-less client certificate.
-
Select Create.
-
After the certificate has been created, select it, and select Action > Download Certificate.
-
This downloads a zip file that contains:
-
A
<cert_name>.pemfile that includes both the client certificate and private key.In our scenario this file is called
COHESITY.pem.The client certificate section of the
<cert_name>.pemfile includes the lines“-----BEGIN CERTIFICATE-----"and“-----END CERTIFICATE-----"and all text between them.The private key section of the
<cert_name>.pemfile includes the lines“-----BEGIN PRIVATE KEY-----"and“-----END PRIVATE KEY-----"and all text in between them. -
A
cacert.pemfile, which is the root certificate for the KMS cluster. It is always namedcacert.pem.
-
You will use these files in the Cohesity configuration.
Configure Cohesity for encryption with an external Key Management System
Configure the Cohesity cluster
This section assumes that you have not configured the Cohesity DataProtect cluster. If you have already configured this cluster, you can skip to Select the Key Management System.
-
Log in to the Cohesity Web UI:
-
Point your browser to the Cohesity Appliance IP Address.
-
Log into the Cohesity Web UI with the default username and password (admin/admin).
https://IP_ADDRESS.
-
-
On Virtual Edition Cluster Setup, select Get Started.
-
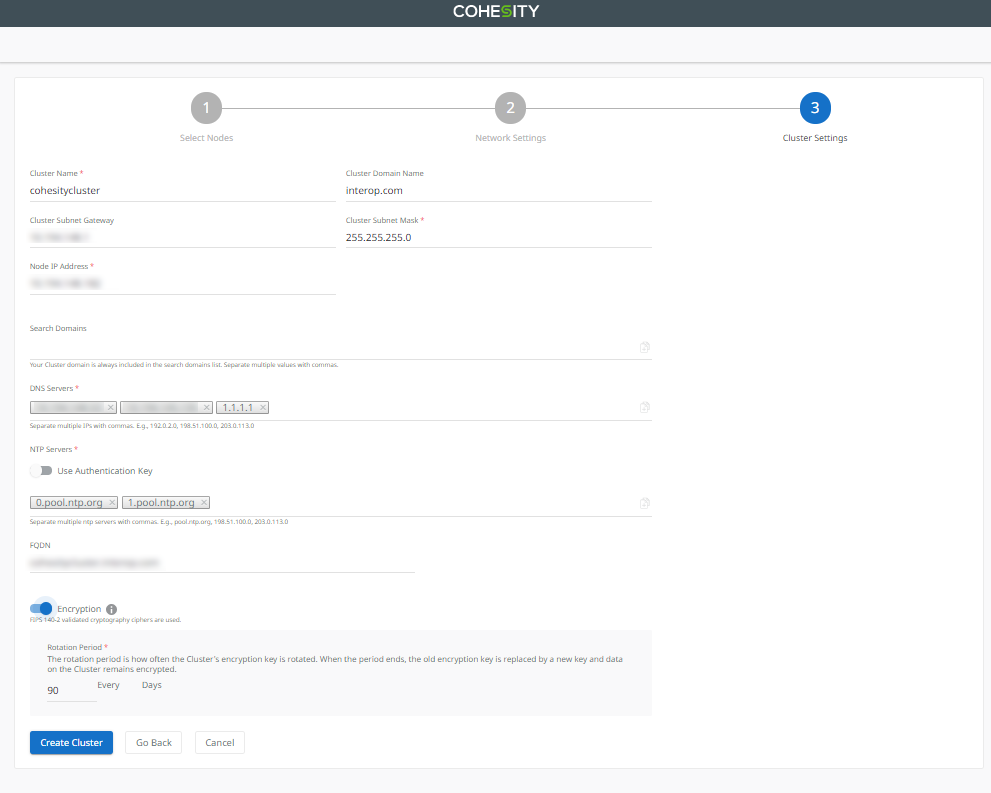
Enter cluster information.
-
In Cluster Name, enter the name of the cluster.
-
In Cluster Domain Name, enter the name of the domain.
-
In Cluster Subnet Gateway, enter the subnet gateway IP address.
-
In Cluster Subnet Mask, enter the subnet mask.
-
In Node IP Address, enter the node IP address.
-
In DNS Servers, enter the IP addresses for all required DNS servers. Separate DNS servers with commas. For example: 192.0.2.0, 198.51.100.0, 203.0.113.0
-
In NTP Servers, enter the IP addresses for all required NTP servers. Separate NTP servers with commas. For example: 0.pool.ntp.org, 1.pool.ntp.org
-
In FQDN, enter the full qualified domain name of the cluster.
-
Optionally, enable Encryption at the cluster level. If you enable encryption at the cluster level, all storage domains created in the cluster will be automatically encrypted with FIPS 140.2 validated cryptography ciphers. You must also set a Rotation Period for the cluster’s encryption key. At the end of each rotation period, the cluster encryption key is replaced, and all data remains encrypted.
If encryption is not enabled at the cluster level, you can enable encryption during the Storage Domain creation process if required.
-
-
Wait until the cluster setup completes.
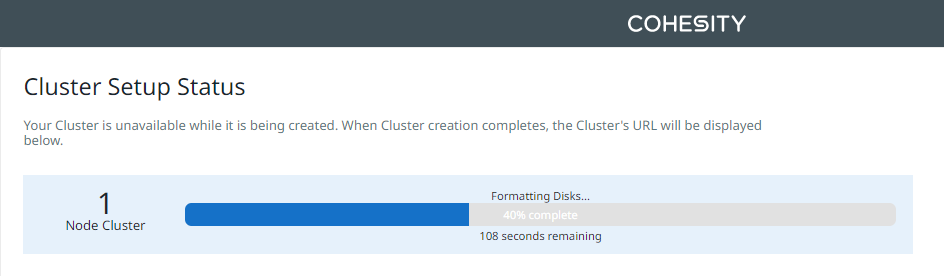
Once the setup is complete, wait a few minutes until the web services are restarted.
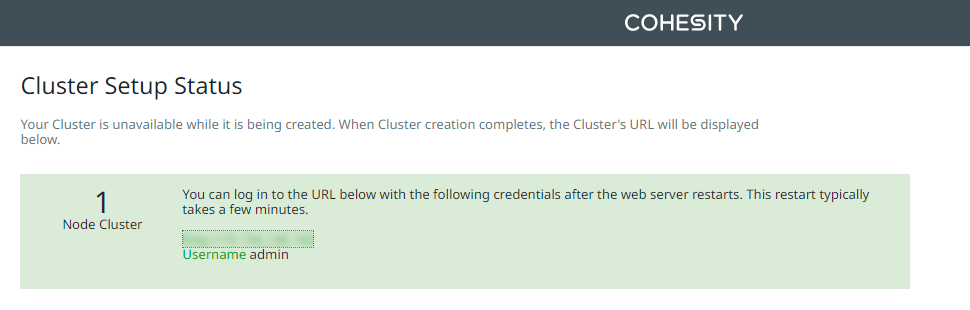
-
Log in again to the cluster.
-
Accept the End User License Agreement.
-
In Management Options, select either SaaS or On Prem.
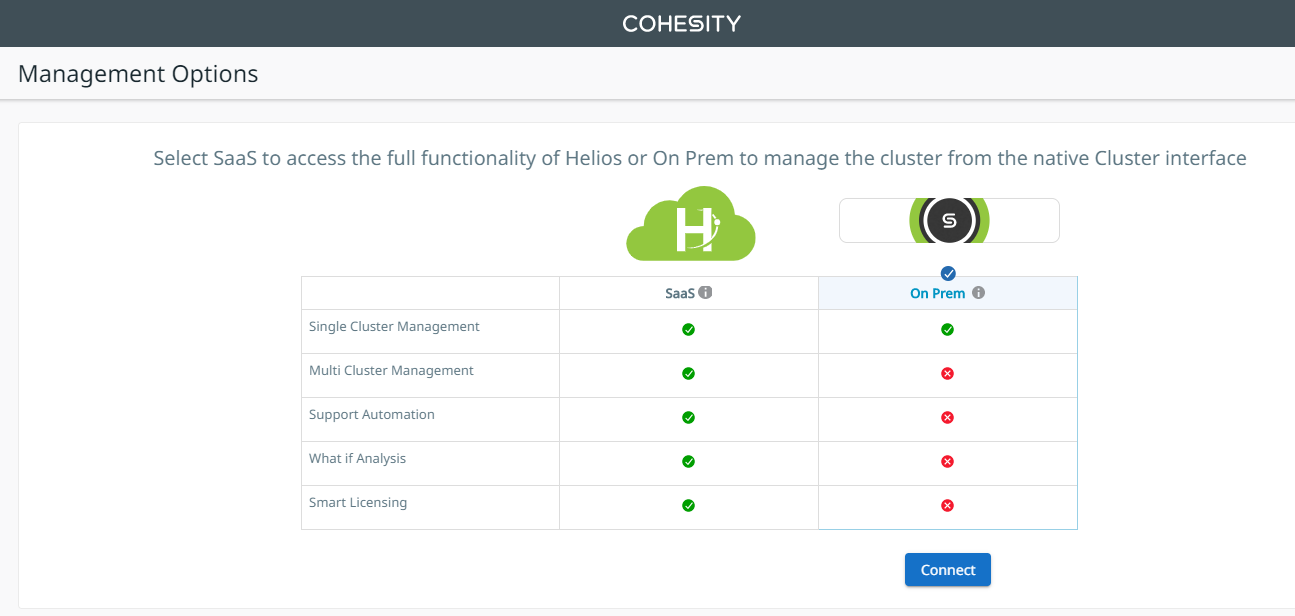
-
On Select preferred mode for licensing, select Helios licensing or manual licensing.
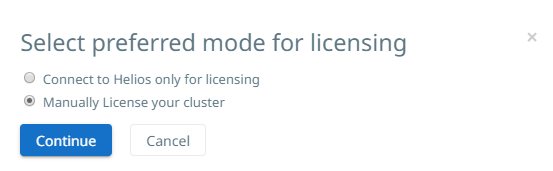
Obtain the license from your Cohesity account team or through Cohesity customer support.
-
Change the admin password.
The Cluster Dashboard appears. For example:
-
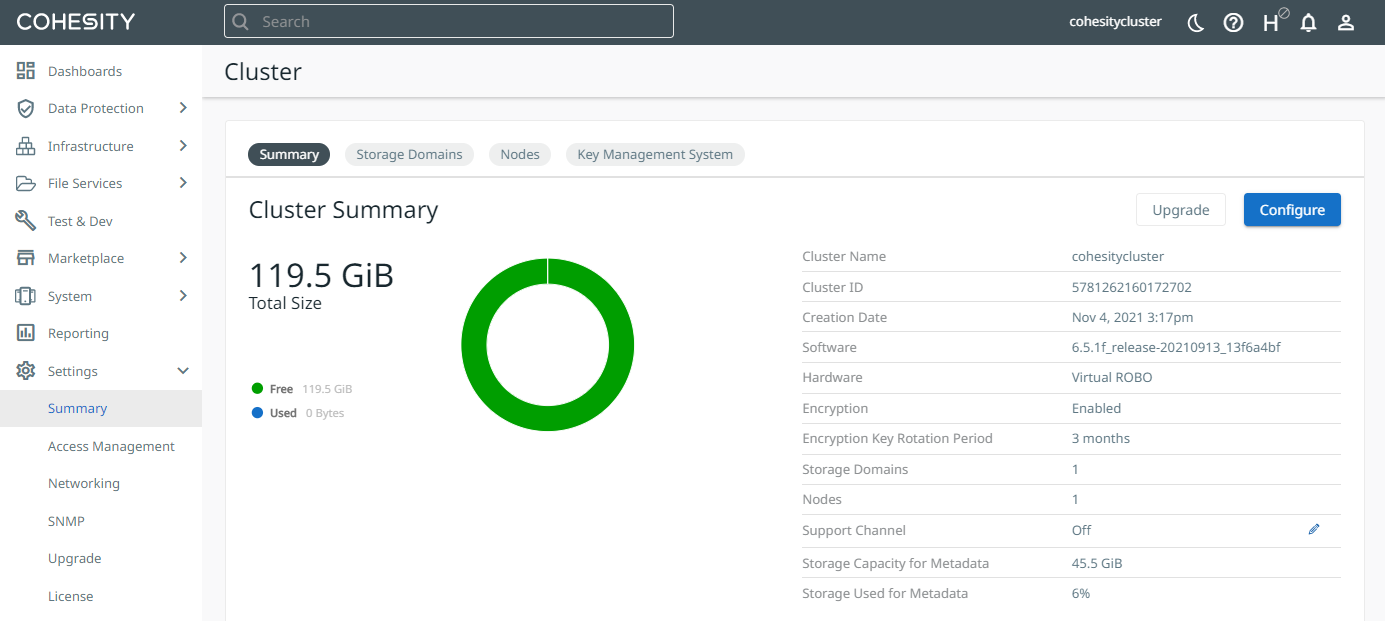
Select Settings > Summary in the left side bar to view the Cluster Summary. For example:
Select the Key Management System
-
Log in to the Cohesity cluster.
-
Select Key Management System.
-
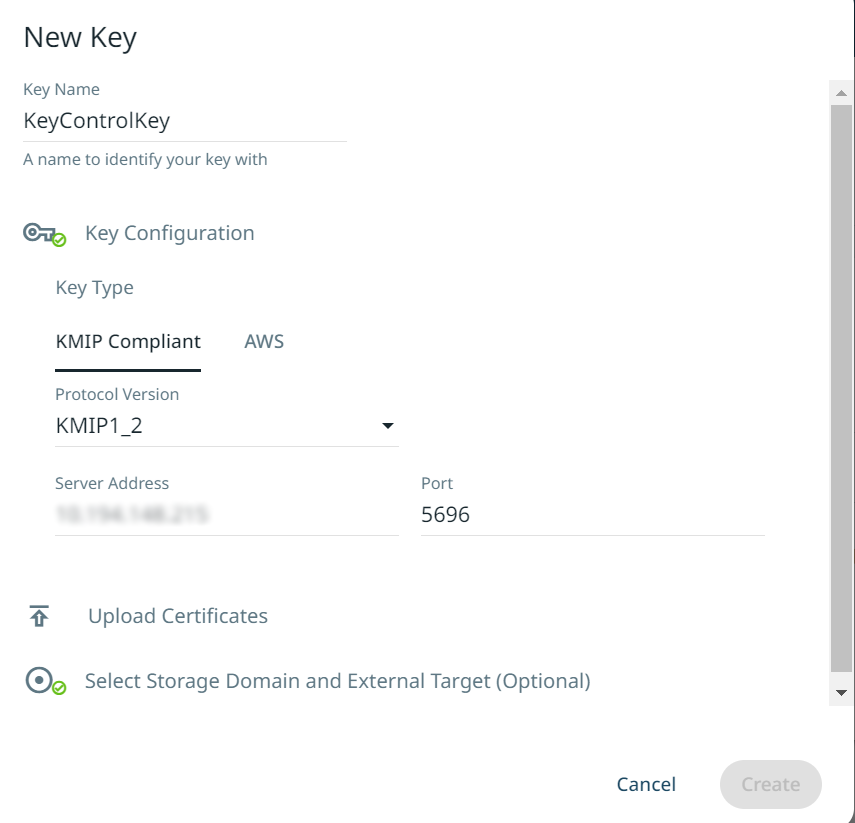
In Key Management System, create the external Key Management System by selecting Add New Key.
-
Expand Key Configuration:
-
In Key Type, select KMIP Compliant.
-
In Protocol Version, select the protocol version that Entrust KeyControl is configured to use. The KMIP version used in Cohesity must match the version used in Entrust KeyControl. Versions supported by Cohesity and KeyControl are KMIP1_1, KMIP1_2, and KMIP1_3.
-
In Server Address, enter the IP address of the KeyControl server.
-
In Port, enter 5696.
-
-
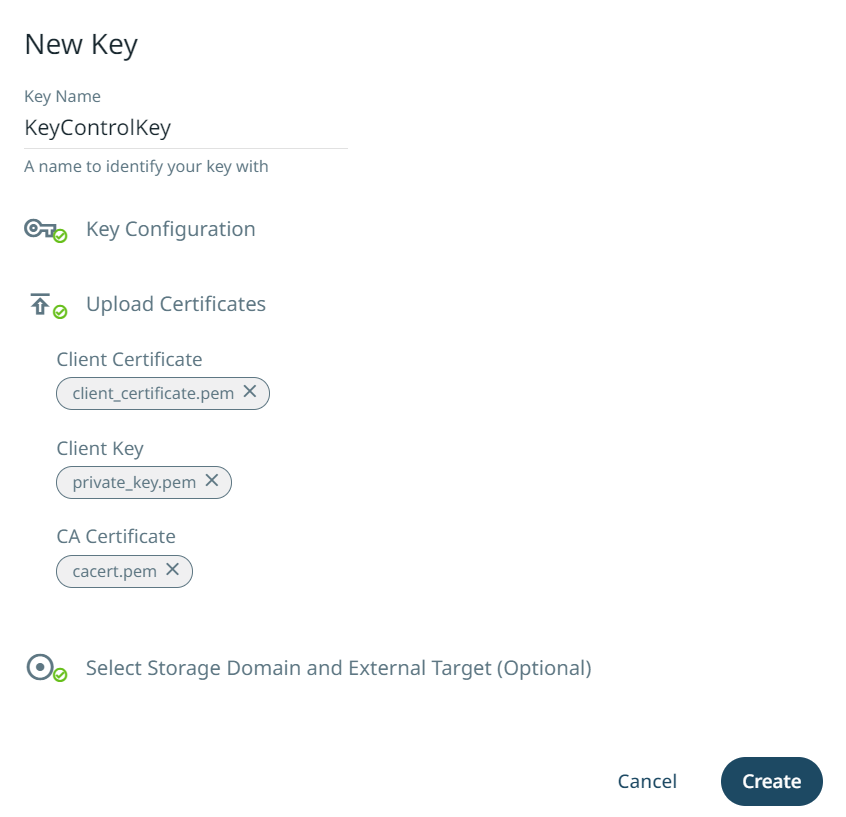
For the Certificates, expand Upload Certificates:
-
These will be the certificates created in KeyControl that have been downloaded before.
-
Certificates must be in PEM format.
-
There should be two files:
COHESITY.pemandcacert.pem. -
Break up the
COHESITY.pemfile into two separate files. One file to contain the public key. The other file to contain the private key. -
In Client Certificate, select the public key file created from
COHESITY.pem. -
In Client Key, select the private key file created from
COHESITY.pem. -
In CA Certificate, select the
cacert.pemfile. -
For example, the
client_certificate.pemfile contains the public key from insideCOHESITY.pemfile.-----BEGIN CERTIFICATE----- MIIElTCCA32gAwIBAgIFAJ/aNcYwDQYJKoZIhvcNAQELBQAwVzELMAkGA1UEBhMC 3sYrq6XZjm3aZv8MnK6aroZFww5QWcwUQIEONThwOuQvP7FanSbIejEaqwk3LWlW . . . 8Uy4Xel5zMMjMrR5F1XLRDHaQa9ZSWUDmc9sPmzyvOe99LBz5EL+bCwlxYQ/7Wqn ugyrDuL7B62OpYmurGeaQ3Z7FfQnhkJmnA== -----END CERTIFICATE----- -
For example, the
private_key.pemfile contains the private key from insideCOHESITY.pemfile.-----BEGIN PRIVATE KEY----- MIIJQwIBADANBgkqhkiG9w0BAQEFAASCCS0wggkpAgEAAoICAQCjjmh5g0Z9vtWq lGL9ZMSLjnmRy9kOUsgb5YYyR48d89m32QfN6B5nO37p/OUzUp2b0k3WZ8uOWiRq . . . yo0CGhGw6Y0LTygoTdyE2mr+h665KEK0ew8lKuHPAGfwlL0cNSy4mgnwYGs8Xadb kkkVSC4PfxLD5zKJ4tpDapRP7oigv9Q= -----END PRIVATE KEY-----
-
-
Select Save to save the settings.
Create a Cohesity storage domain that uses KeyControl for encryption
If you already have a suitable storage domain that you want to use, Cohesity supports the migration of data from internal to external KMSs. To migrate a KMS instead of creating a new storage domain, see the Cohesity documentation: https://docs.cohesity.com/7_1_2/Web/UserGuide/Content/Dashboard/Admin/migrate-kms.htm
To create a new storage domain:
-
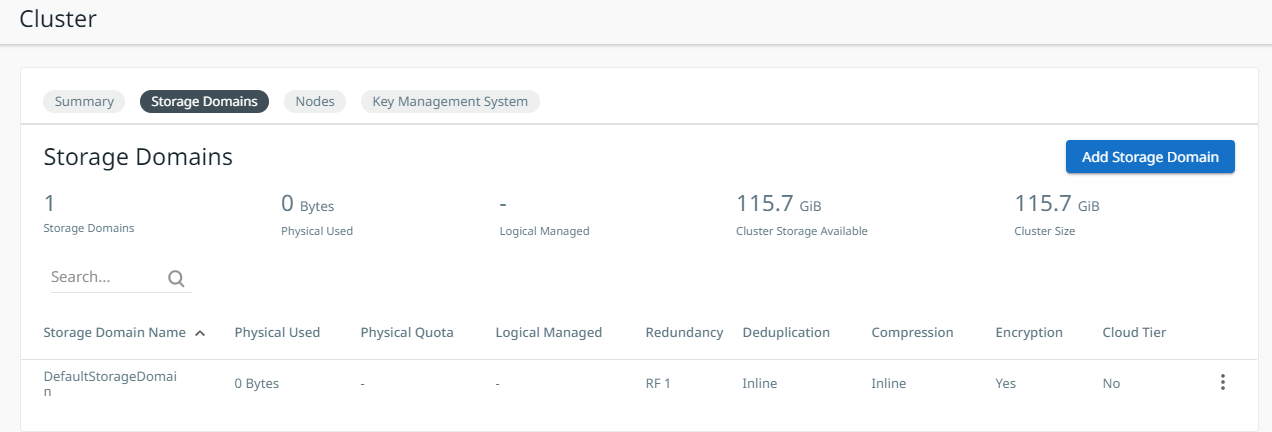
In Settings > Summary, select Storage Domains.
-
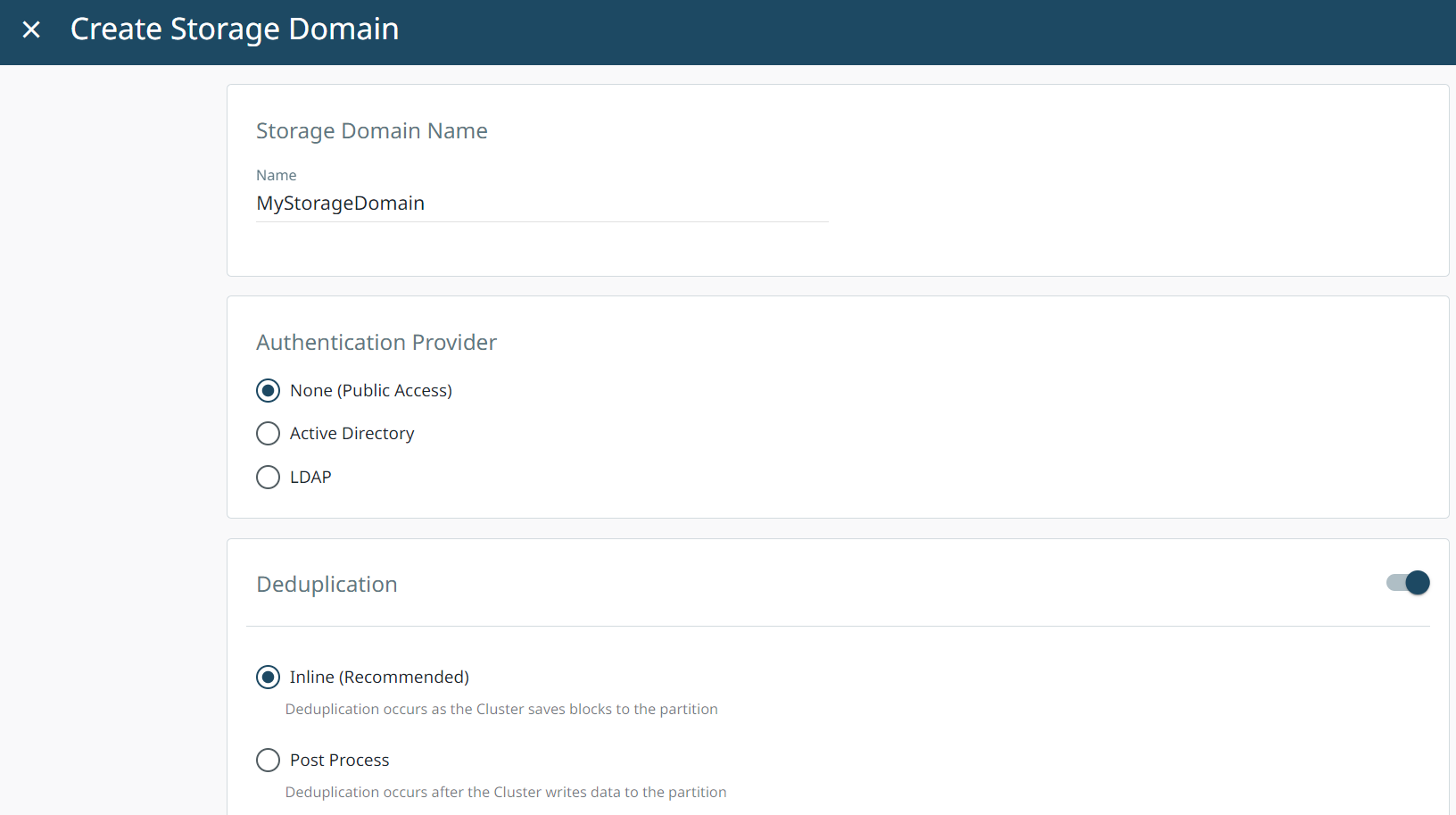
Select Create Storage Domain.
-
In Storage Domain Name, enter the Storage Domain Name.
-
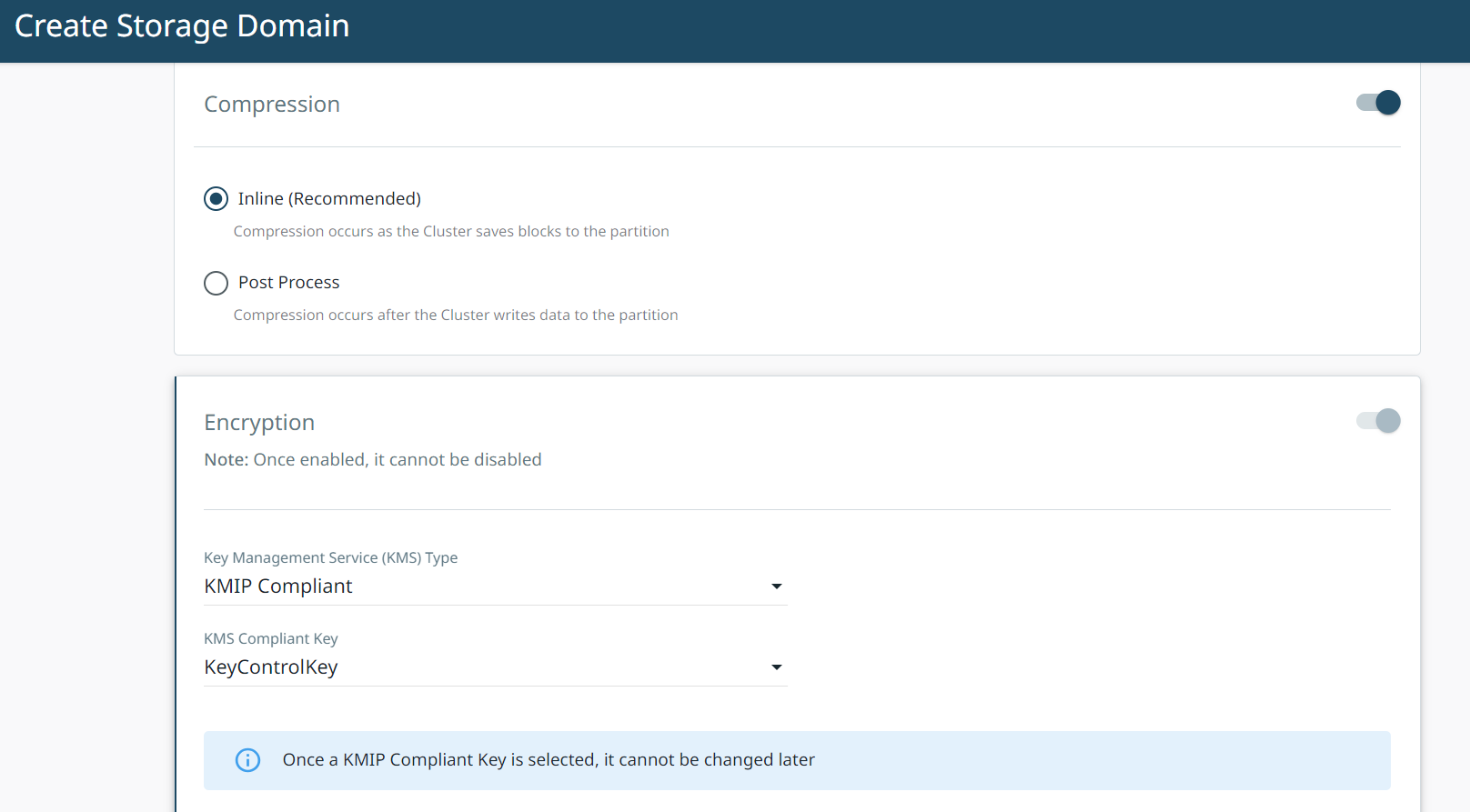
Select Encryption. This enables encryption at the cluster level.
-
In Key Management Service (KMS) Type, select KMIP Compliant from the drop down menu.
-
In KMS Compliant Key, select your recently created KeyControl Key from the drop down menu.
-
Fill out any other options required.
-
Select Create.
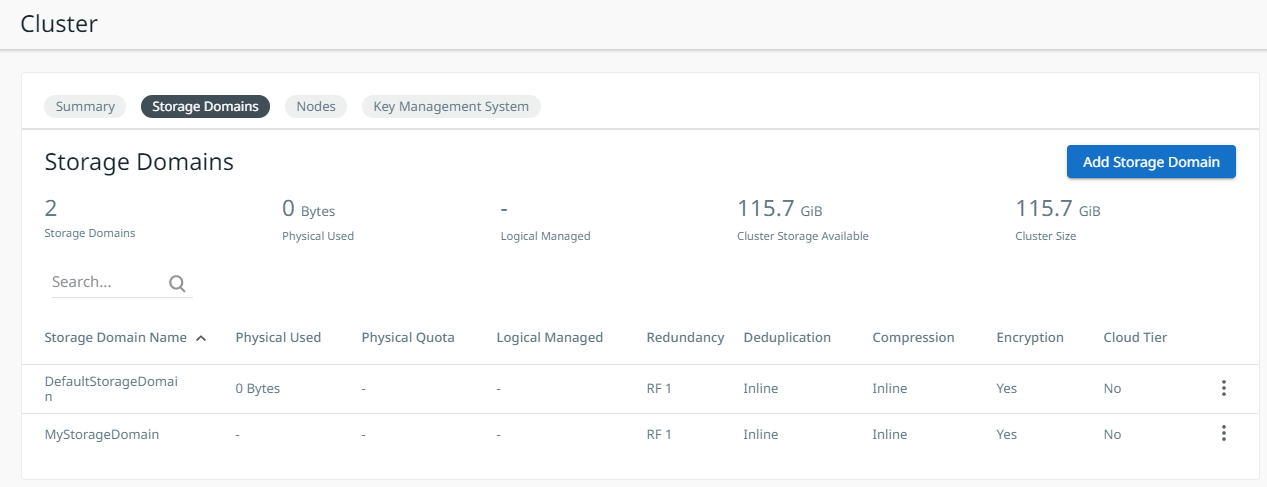
The new storage domain is created and added to the Storage Domains list.
Check KeyControl for Cohesity keys
Now that the Cohesity Storage Domain has been created, there should be new keys in KeyControl.
-
Log in to the KeyControl Vault server.
-
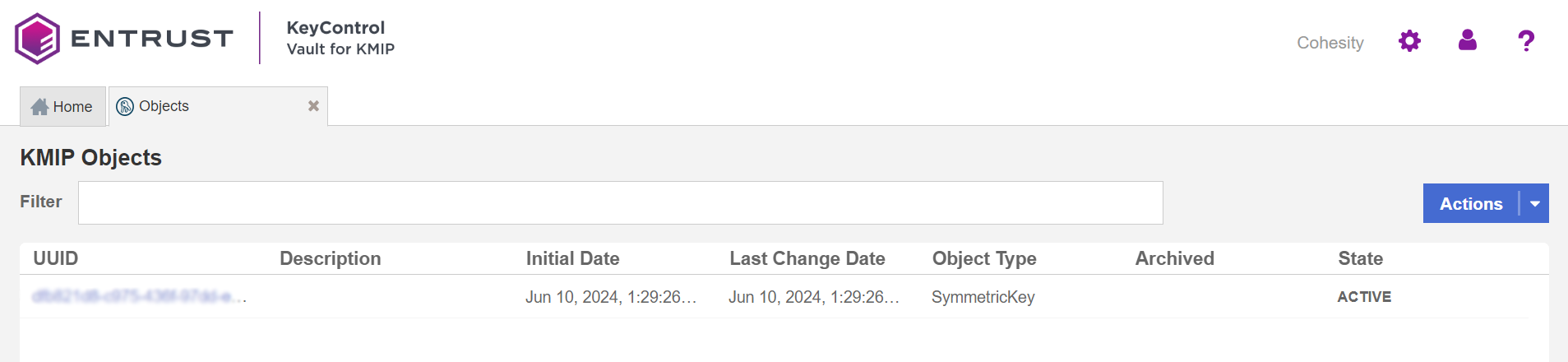
Select the Objects tab.
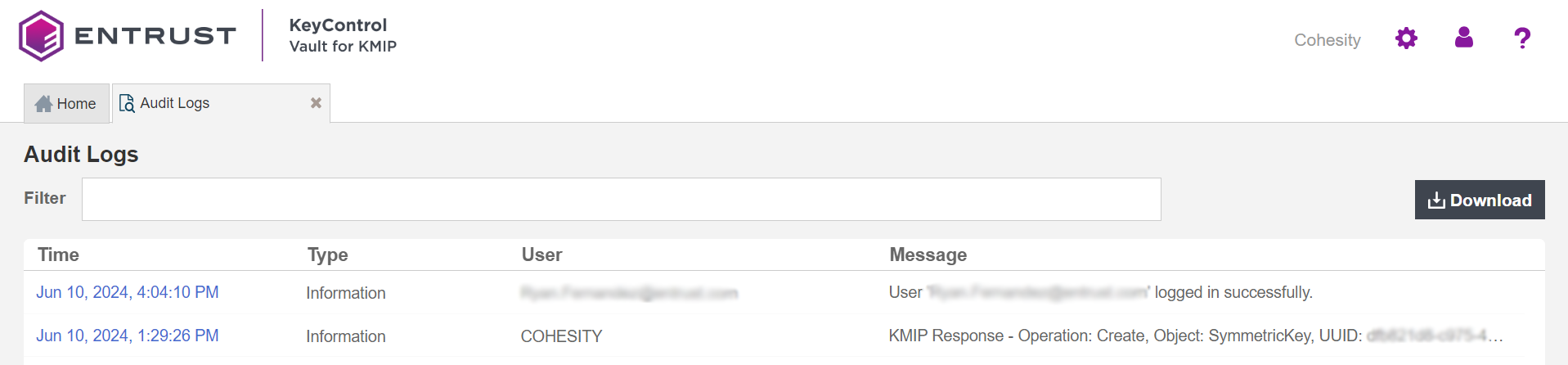
There should be new keys listed that were created when the storage domain was created in the Cohesity cluster. Select one of the keys and validate that it is from Cohesity by selecting the Custom Attributes tab. For example:
-
Select the Audit Logs page from the home screen on the KeyControl Vault page and validate the creation of keys when you created the storage domain in Cohesity. For example: