Database
General architecture
This chapter provides information about key storage. Security World keys and token data in the Web Services Option Pack environment are stored in a standalone database management system. The respective data is non-confidential data which exists and can be accessed outside the HSM.
The WSOP server accesses the database management system by using a database driver. The database driver depends on the database management system implementation.
The figure below is a high-level picture of the WSOP server and the database management system in which the database management system is implemented with MongoDB. The MongoDB driver allows the access of the WSOP server to the MongoDB database.
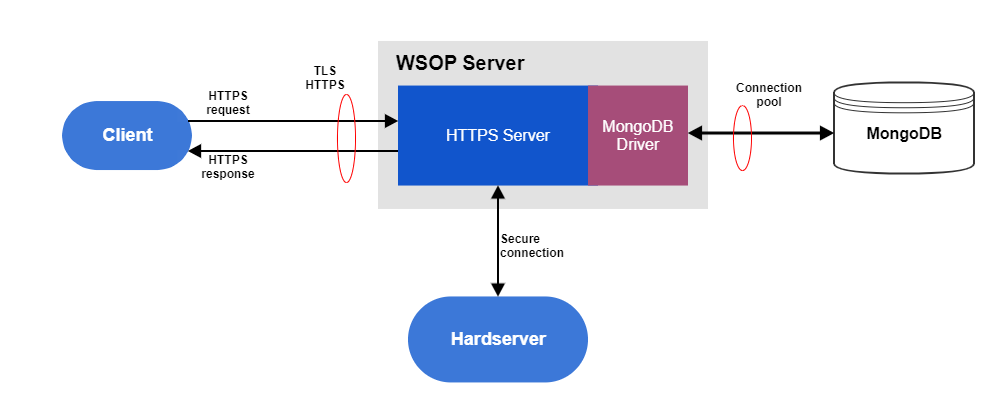
| Details about key properties and key management are provided in the Key Management with WSOP chapter. WSOP database configuration options are explained in the Database Configuration subchapter. |
Database type
Each Security World has one database management system.
The database type is specified in the WSOP server configuration file by the db field.
The name of the database and other database configuration options are also provided in the WSOP server configuration file.
MongoDB
When db field from WSOP configuration file type is set to mongodb, then database management system is implemented by using MongoDB.
MongoDB configuration options are also provided in the WSOP server configuration file under the mongodb section.
MongoDB stores Security World keys and token data in the following collections:
-
Keys
-
Groups
-
Domains
-
Softcards
User roles
MongoDB has the notion of roles, where each role has a defined set of allowed actions. A user of a MongoDB database can be given a role which then determines what the user can and cannot do to the data.
MongoDB comes with three built-in roles, namely cluster-administrator, database-administrator, and a database-user.
Give the WSOP server the database-user role. The WSOP server should only have the privileges necessary for it to function as a user of the MongoDB database.
To operate MongoDB, the WSOP server needs the following actions:
-
find
-
insert
-
remove
-
createIndex
-
update
The MongoDB administrator will configure the MongoDB database with the following actions and privileges for WSOP data-user role:
dbname = nshield-corecrypto
actions = ["find", "insert", "remove", "createIndex", "update"]
privileges=[
{"resource" : {"db" : dbname, "collection" : ""}, "actions" : actions},
]For details about MongoDB roles, see the MongoDB documentation: Role-based access control
Authentication methods
The WSOP MongoDB deployment supports the following authentication mechanisms to verify the identity of the WSOP server:
-
none
-
pwd
-
tls
The type of authentication is specified by auth_type option in the WSOP server configuration file in the database section using one of the following values: none, pwd, tls.
- none
-
No authentication. This option is used during development. It should not be used during production.
- pwd
-
Using username and password files for Salted Challenge Response Authentication Mechanism (SCRAM), MongoDB verifies the supplied WSOP server credentials against the MongoDB’s username, password, and authentication database. The
auth_username_fileandauth_password_fileoptions define the location of a secure file containing the username and passphrase to use for authentication. The value ofauth_sourceoption specifies the name of MongoDB’s authentication database. - tls
-
WSOP server can use tls X.509 certificates instead of usernames and passwords to authenticate to the MongoDB database. In this configuration the value of the
auth_typeoption in the WSOP server configuration file is set toX509. Also, in the same configuration file, the TLS must be enabled by settingdisable_tlstofalse.The Certificate Authority (CA) files to use for TLS are specified by the following options:
db_ca_file,db_cert_fileanddb_key_file.